The following is intended to outline our general








- Slides: 47


The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle.

443

<Insert Picture Here> Kris Bhanushali Senior Solution Architect Oracle Corporation Oracle Database 11 g: Security and Regulatory Compliance

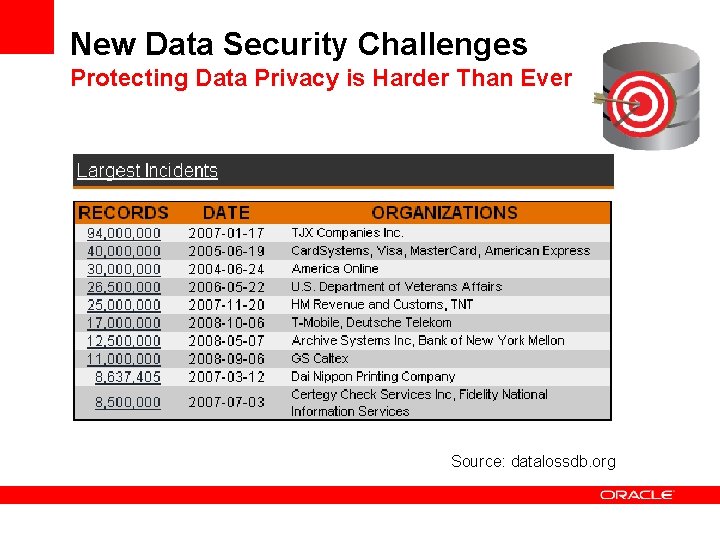
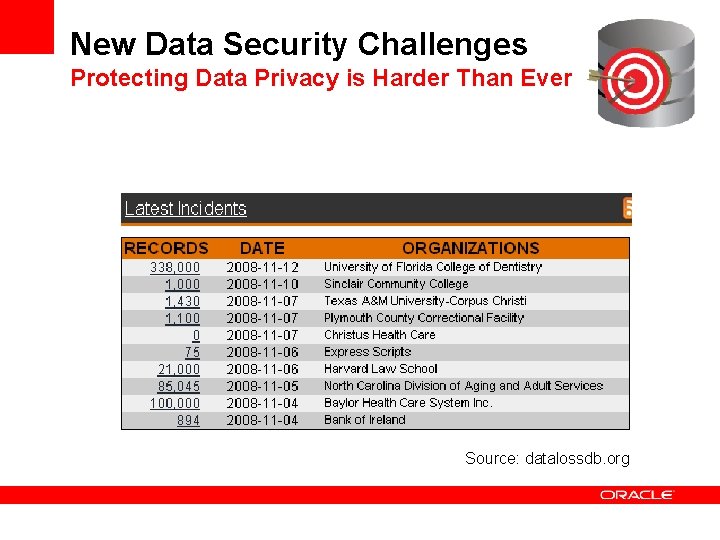
New Data Security Challenges Protecting Data Privacy is Harder Than Ever Source: datalossdb. org

New Data Security Challenges Protecting Data Privacy is Harder Than Ever Source: datalossdb. org

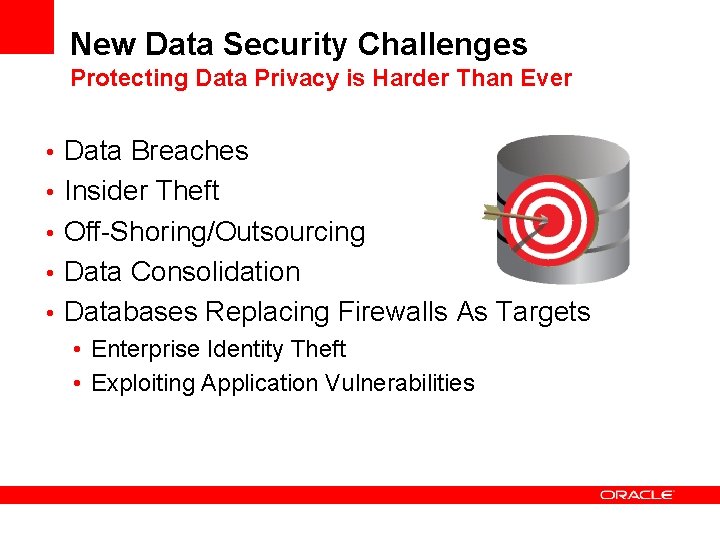
New Data Security Challenges Protecting Data Privacy is Harder Than Ever • Data Breaches • Insider Theft • Off-Shoring/Outsourcing • Data Consolidation • Databases Replacing Firewalls As Targets • Enterprise Identity Theft • Exploiting Application Vulnerabilities

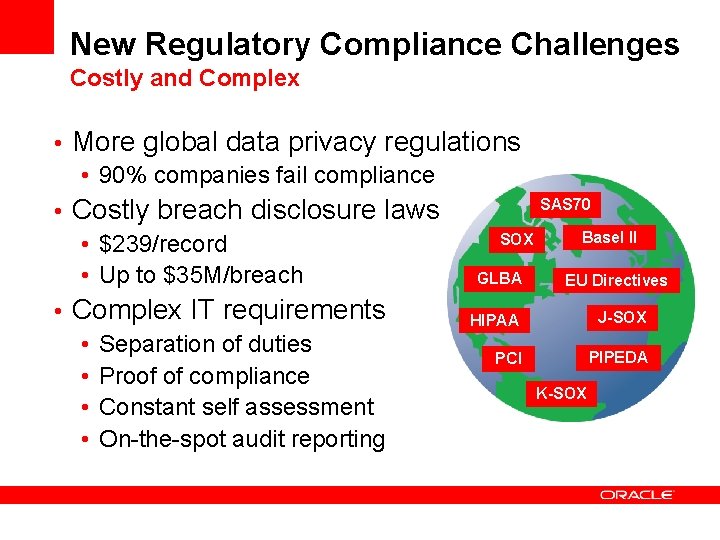
New Regulatory Compliance Challenges Costly and Complex • More global data privacy regulations • 90% companies fail compliance SAS 70 • Costly breach disclosure laws Basel II SOX • $239/record • Up to $35 M/breach GLBA EU Directives • Complex IT requirements J-SOX HIPAA • Separation of duties PIPEDA PCI • Proof of compliance K-SOX • Constant self assessment • On-the-spot audit reporting

Strategic Direction: Security Transparent to Your Applications • No changes required in applications • Secure data today and meet auditor’s changing reqmts • No expert security engineers needed • Provided • It is secure and fast • It is manageable, flexible, and easy-to-use • It is baked-in Regulations Policies Enforcement Audit

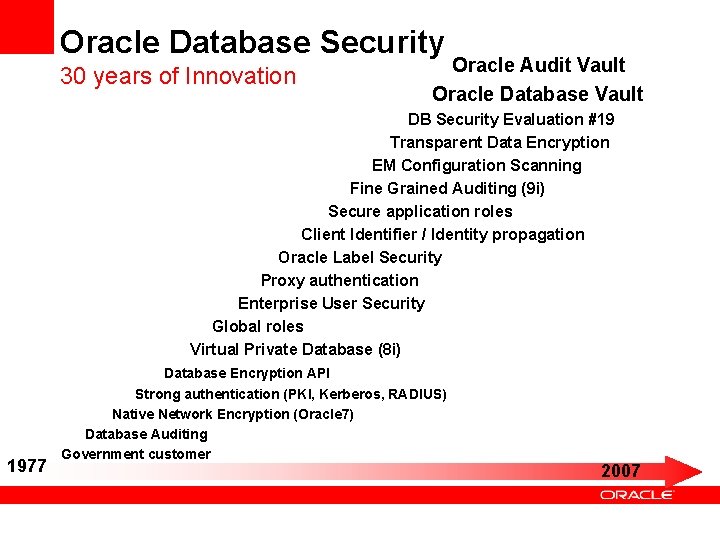
Oracle Database Security 30 years of Innovation Oracle Audit Vault Oracle Database Vault DB Security Evaluation #19 Transparent Data Encryption EM Configuration Scanning Fine Grained Auditing (9 i) Secure application roles Client Identifier / Identity propagation Oracle Label Security Proxy authentication Enterprise User Security Global roles Virtual Private Database (8 i) 1977 Database Encryption API Strong authentication (PKI, Kerberos, RADIUS) Native Network Encryption (Oracle 7) Database Auditing Government customer 2007

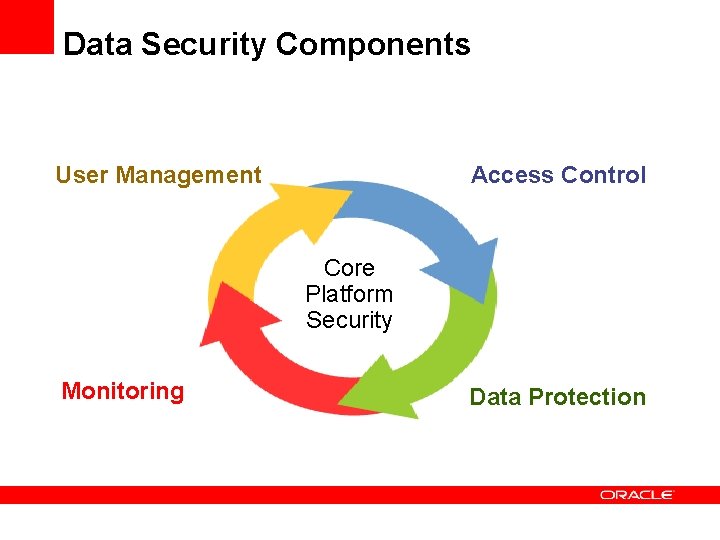
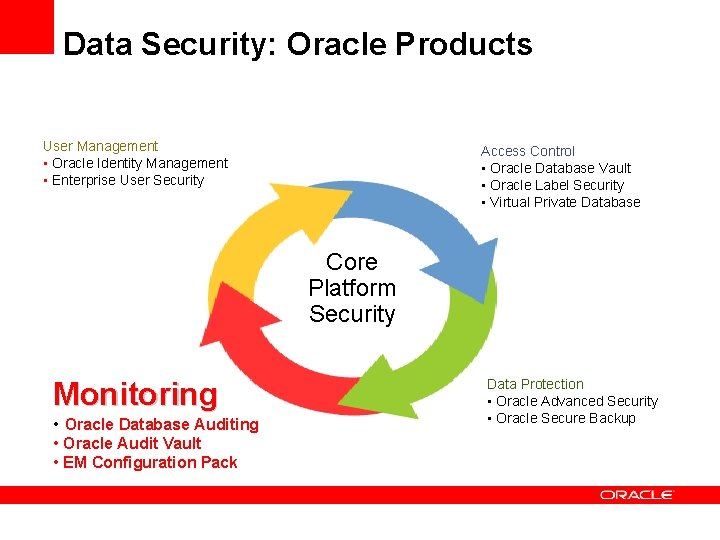
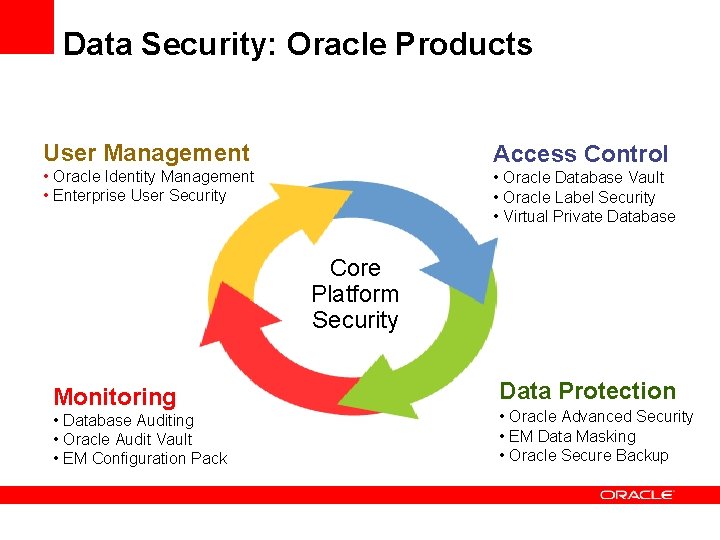
Data Security Components User Management Access Control Core Platform Security Monitoring Data Protection

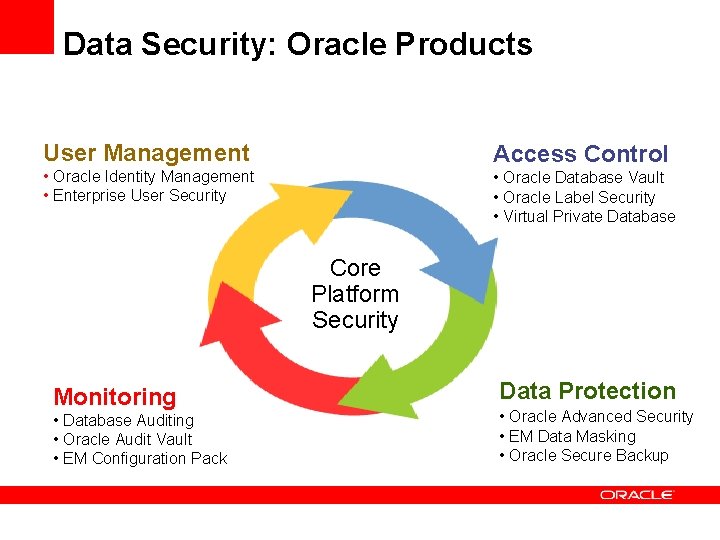
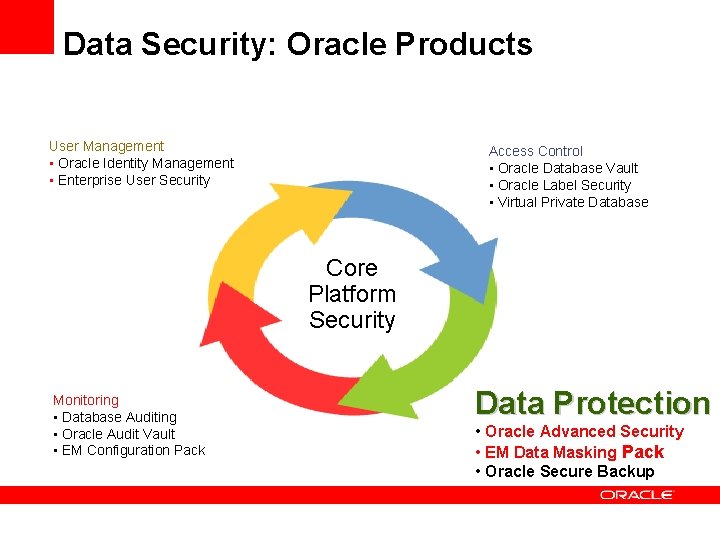
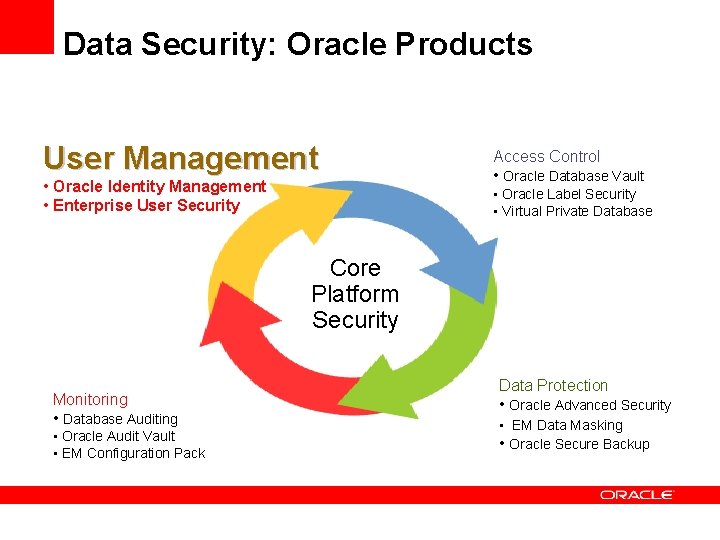
Data Security: Oracle Products User Management Access Control • Oracle Identity Management • Enterprise User Security • Oracle Database Vault • Oracle Label Security • Virtual Private Database Core Platform Security Monitoring • Database Auditing • Oracle Audit Vault • EM Configuration Pack Data Protection • Oracle Advanced Security • EM Data Masking • Oracle Secure Backup

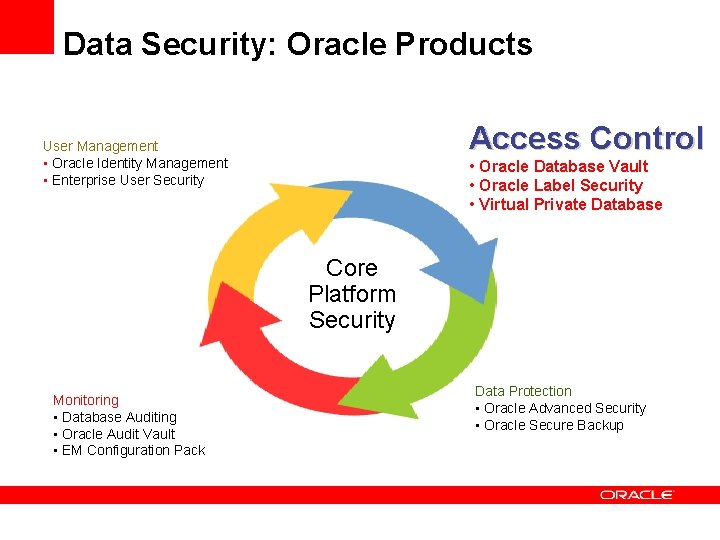
Data Security: Oracle Products Access Control User Management • Oracle Identity Management • Enterprise User Security • Oracle Database Vault • Oracle Label Security • Virtual Private Database Core Platform Security Monitoring • Database Auditing • Oracle Audit Vault • EM Configuration Pack Data Protection • Oracle Advanced Security • Oracle Secure Backup

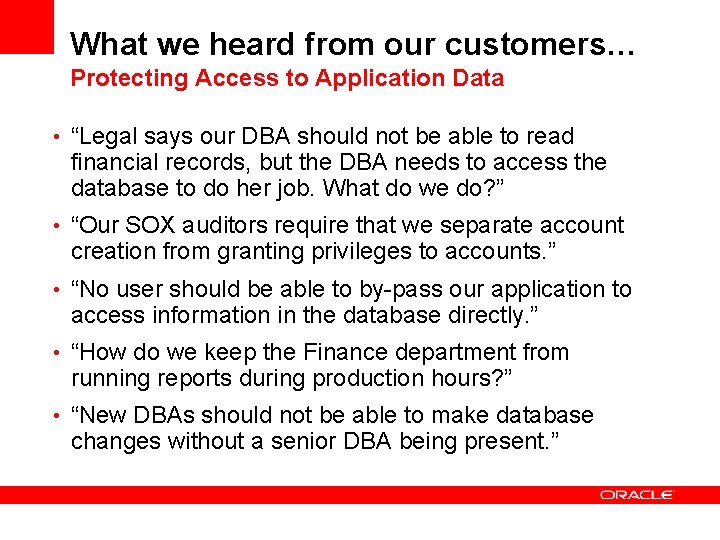
What we heard from our customers… Protecting Access to Application Data • “Legal says our DBA should not be able to read financial records, but the DBA needs to access the database to do her job. What do we do? ” • “Our SOX auditors require that we separate account creation from granting privileges to accounts. ” • “No user should be able to by-pass our application to access information in the database directly. ” • “How do we keep the Finance department from running reports during production hours? ” • “New DBAs should not be able to make database changes without a senior DBA being present. ”

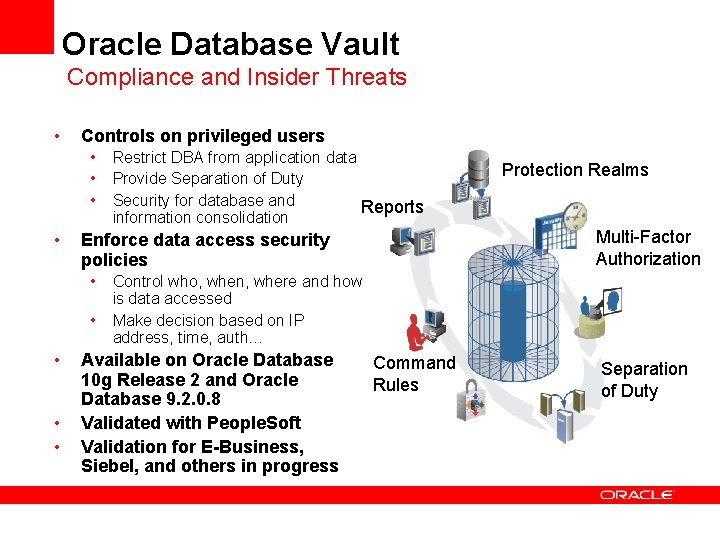
Oracle Database Vault Compliance and Insider Threats • Controls on privileged users • • Protection Realms Multi-Factor Authorization Enforce data access security policies • • Restrict DBA from application data Provide Separation of Duty Security for database and Reports information consolidation Control who, when, where and how is data accessed Make decision based on IP address, time, auth… Available on Oracle Database 10 g Release 2 and Oracle Database 9. 2. 0. 8 Validated with People. Soft Validation for E-Business, Siebel, and others in progress Command Rules Separation of Duty

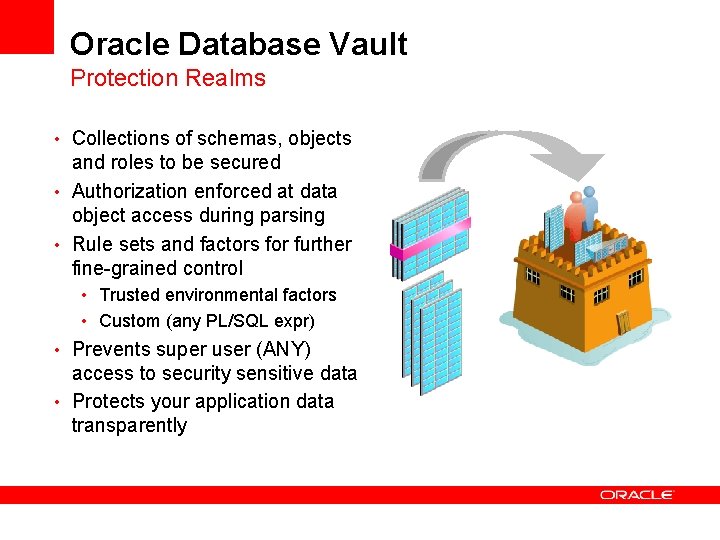
Oracle Database Vault Protection Realms • Collections of schemas, objects and roles to be secured • Authorization enforced at data object access during parsing • Rule sets and factors for further fine-grained control • Trusted environmental factors • Custom (any PL/SQL expr) • Prevents super user (ANY) access to security sensitive data • Protects your application data transparently

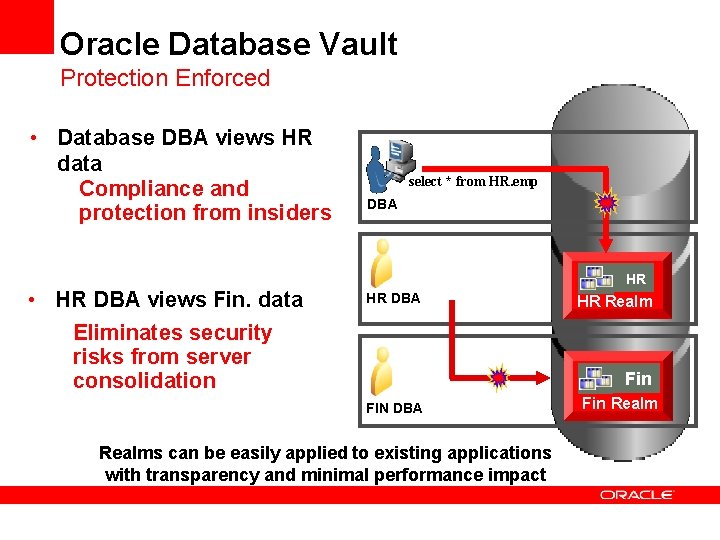
Oracle Database Vault Protection Enforced • Database DBA views HR data Compliance and protection from insiders • HR DBA views Fin. data Eliminates security risks from server consolidation select * from HR. emp DBA HR HR HR DBA HR Realm Fin FIN DBA Realms can be easily applied to existing applications with transparency and minimal performance impact Fin Realm

What we heard from our customers… Data Classification • “We want to restrict access to data in our database on a • • need to know basis. ” “We want to label our customer accounts to assign highvalue accounts to strategic account managers. ” “We want to consolidate sensitive information in a single database for better business intelligence but we need to compartmentalize access. ” “We need to apply labels to our data to comply with HIPAA. ” “We want to label our international accounts so we can assign to local managers and not violate data privacy regulations. ”

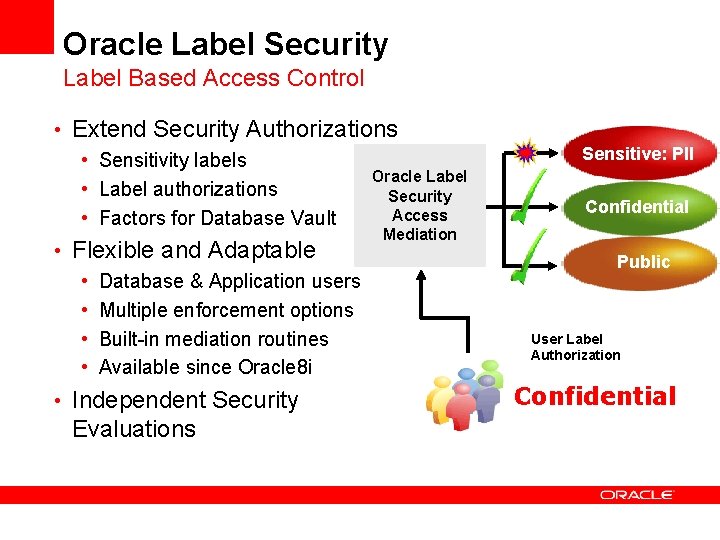
Oracle Label Security Label Based Access Control • Extend Security Authorizations • Sensitivity labels Oracle Label • Label authorizations Security Access • Factors for Database Vault • Flexible and Adaptable • Database & Application users • Multiple enforcement options • Built-in mediation routines • Available since Oracle 8 i • Independent Security Evaluations Sensitive: PII Confidential Mediation Public User Label Authorization Confidential

Oracle Label Security Manageability • Comprehensive API Available • Integrated with Oracle Identity Management

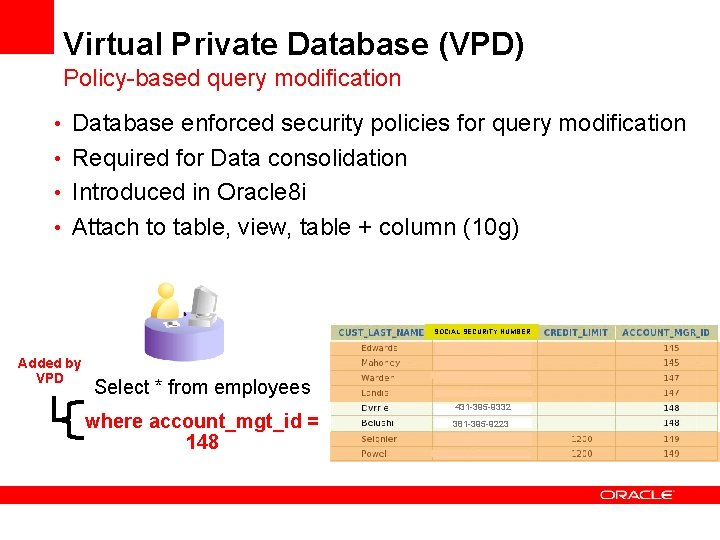
Virtual Private Database (VPD) Policy-based query modification • Database enforced security policies for query modification • Required for Data consolidation • Introduced in Oracle 8 i • Attach to table, view, table + column (10 g) SOCIAL SECURITY NUMBER Added by VPD Select * from employees where account_mgt_id = 148 431 -395 -9332 381 -395 -9223

Data Security: Oracle Products User Management • Oracle Identity Management • Enterprise User Security Access Control • Oracle Database Vault • Oracle Label Security • Virtual Private Database Core Platform Security Monitoring • Database Auditing • Oracle Audit Vault • EM Configuration Pack Data Protection • Oracle Advanced Security • EM Data Masking Pack • Oracle Secure Backup

What we heard from our customers… Protecting Data-at-Rest • “Our PCI auditors say we have to encrypt credit card data. ” • “We need to encrypt personal identity information to comply with EU Data Privacy but cannot change our applications. ” • “We want to manage medical images in our database but they have to be encrypted for HIPAA compliance. ” • “We don’t want users with operating system file ‘read’ access to be able to walk away with our database. ” • “We send back-up tapes off-site and need to make sure they are secure even if off-site facility is compromised. ”

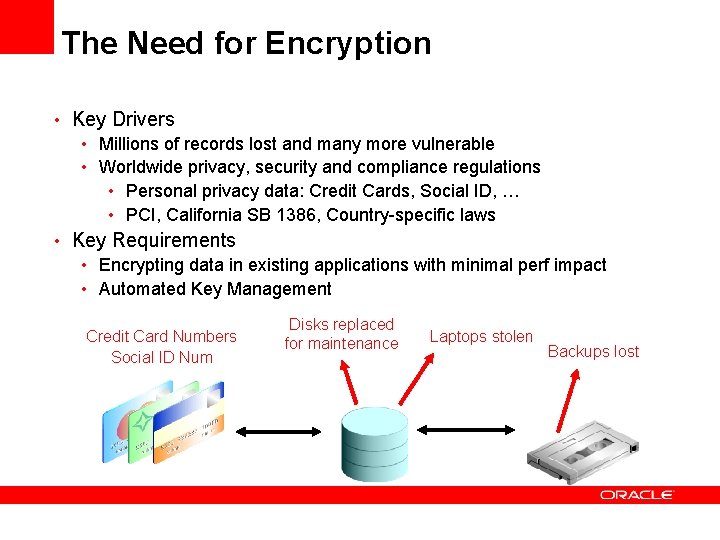
The Need for Encryption • Key Drivers • Millions of records lost and many more vulnerable • Worldwide privacy, security and compliance regulations • Personal privacy data: Credit Cards, Social ID, … • PCI, California SB 1386, Country-specific laws • Key Requirements • Encrypting data in existing applications with minimal perf impact • Automated Key Management Credit Card Numbers Social ID Num Disks replaced for maintenance Laptops stolen Backups lost

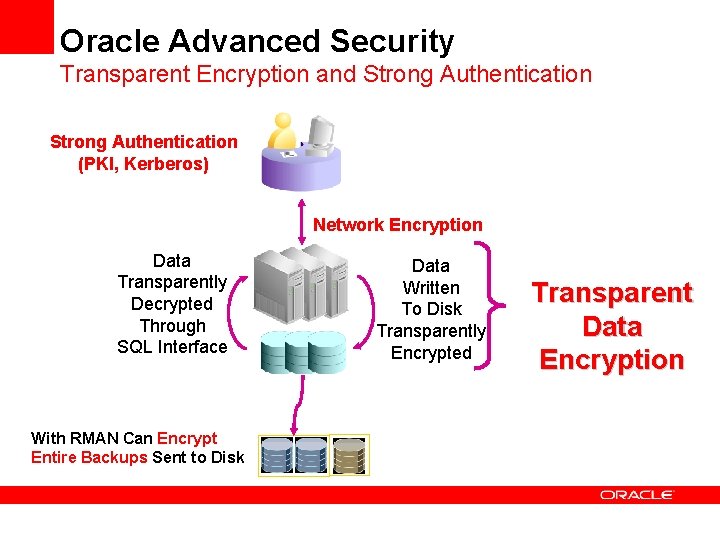
Oracle Advanced Security Transparent Encryption and Strong Authentication (PKI, Kerberos) Network Encryption Data Transparently Decrypted Through SQL Interface With RMAN Can Encrypt Entire Backups Sent to Disk Data Written To Disk Transparently Encrypted Transparent Data Encryption

Transparent Data Encryption Manageability for Column TDE

Oracle Advanced Security Oracle Database 11 g Enhancements • Tablespace Encryption • SECUREFILE LOB encryption • Hardware Security Module (HSM) Integration • Generate, store and manage master key in an external device • Works with Standard PKCS #11 compliant hardware devices

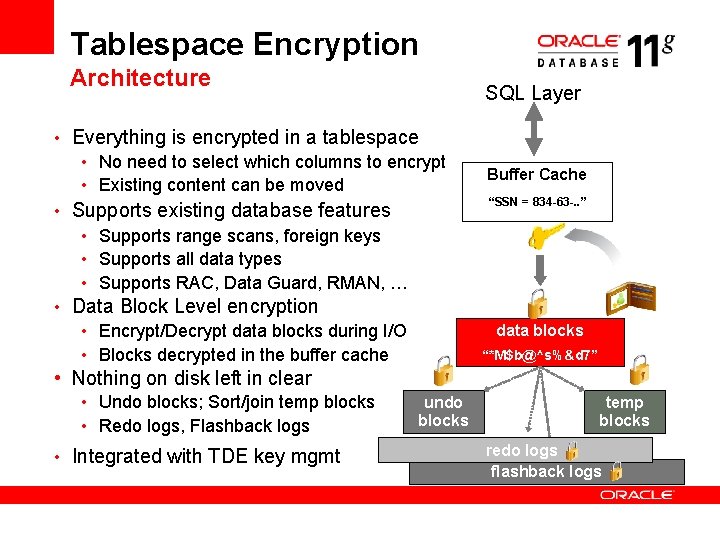
Tablespace Encryption Architecture SQL Layer • Everything is encrypted in a tablespace • No need to select which columns to encrypt • Existing content can be moved • Supports existing database features • Supports range scans, foreign keys • Supports all data types • Supports RAC, Data Guard, RMAN, … • Data Block Level encryption • Encrypt/Decrypt data blocks during I/O • Blocks decrypted in the buffer cache Buffer Cache “SSN = 834 -63 -. . ” data blocks “*M$b@^s%&d 7” • Nothing on disk left in clear • Undo blocks; Sort/join temp blocks • Redo logs, Flashback logs • Integrated with TDE key mgmt undo blocks temp blocks redo logs flashback logs

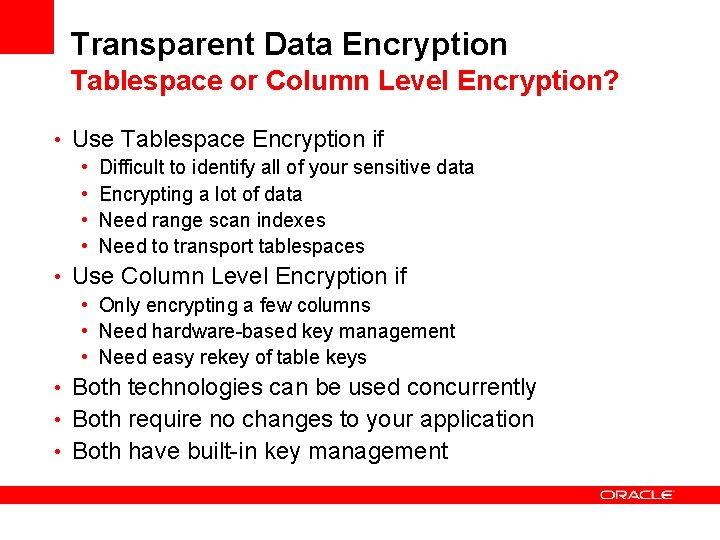
Transparent Data Encryption Tablespace or Column Level Encryption? • Use Tablespace Encryption if • Difficult to identify all of your sensitive data • Encrypting a lot of data • Need range scan indexes • Need to transport tablespaces • Use Column Level Encryption if • Only encrypting a few columns • Need hardware-based key management • Need easy rekey of table keys • Both technologies can be used concurrently • Both require no changes to your application • Both have built-in key management

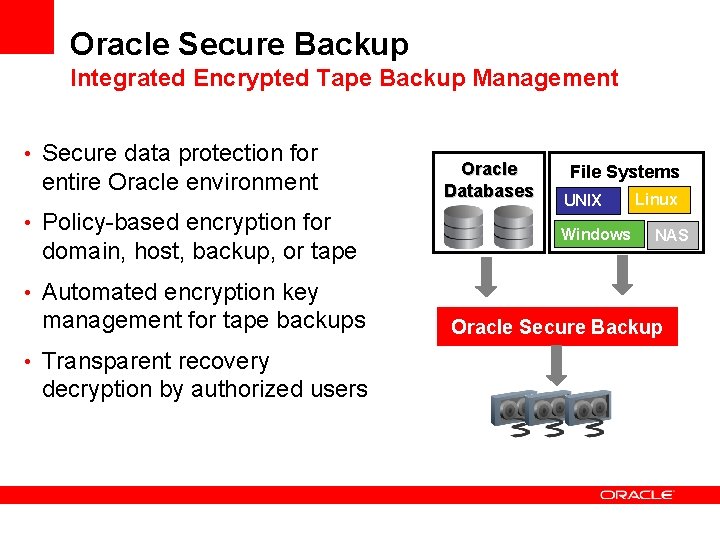
Oracle Secure Backup Integrated Encrypted Tape Backup Management • Secure data protection for entire Oracle environment • Policy-based encryption for domain, host, backup, or tape Oracle Databases File Systems UNIX Windows Linux NAS • Automated encryption key management for tape backups • Transparent recovery decryption by authorized users Oracle Secure Backup

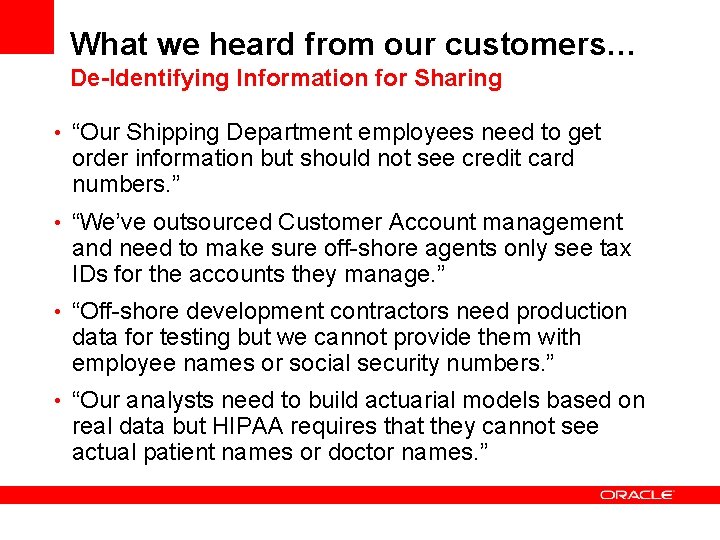
What we heard from our customers… De-Identifying Information for Sharing • “Our Shipping Department employees need to get order information but should not see credit card numbers. ” • “We’ve outsourced Customer Account management and need to make sure off-shore agents only see tax IDs for the accounts they manage. ” • “Off-shore development contractors need production data for testing but we cannot provide them with employee names or social security numbers. ” • “Our analysts need to build actuarial models based on real data but HIPAA requires that they cannot see actual patient names or doctor names. ”

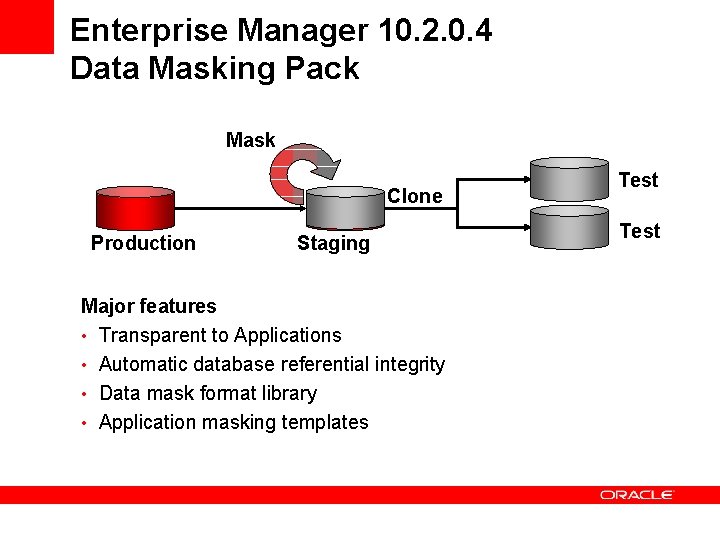
Enterprise Manager 10. 2. 0. 4 Data Masking Pack Mask Clone Production Staging Major features • Transparent to Applications • Automatic database referential integrity • Data mask format library • Application masking templates Test

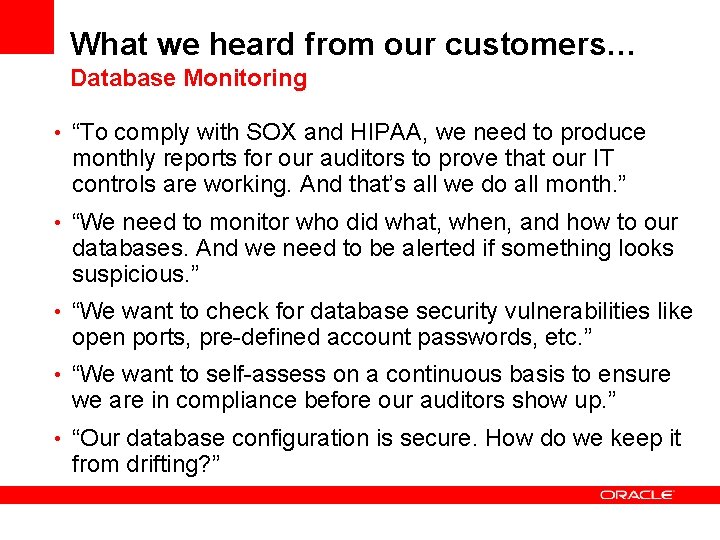
What we heard from our customers… Database Monitoring • “To comply with SOX and HIPAA, we need to produce monthly reports for our auditors to prove that our IT controls are working. And that’s all we do all month. ” • “We need to monitor who did what, when, and how to our databases. And we need to be alerted if something looks suspicious. ” • “We want to check for database security vulnerabilities like open ports, pre-defined account passwords, etc. ” • “We want to self-assess on a continuous basis to ensure we are in compliance before our auditors show up. ” • “Our database configuration is secure. How do we keep it from drifting? ”

Data Security: Oracle Products User Management • Oracle Identity Management • Enterprise User Security Access Control • Oracle Database Vault • Oracle Label Security • Virtual Private Database Core Platform Security Monitoring • Oracle Database Auditing • Oracle Audit Vault • EM Configuration Pack Data Protection • Oracle Advanced Security • Oracle Secure Backup

Auditing in the Oracle Database Robust, Flexible, and High Fidelity Audit • Industry’s most advanced • Robust auditing since Oracle 7 (1993) • What to audit: • Audit statement, privileges, statement event, failure or success, user -level, schema-object privilege, SYS auditing • Fine grained auditing for condition/policy based auditing (2001) • Flexible format: tables, SYSLOG, Windows event viewer • Storage: Audit tables, OS files, syslog • Use by customers today in nearly all markets • Finance • Healthcare • Government

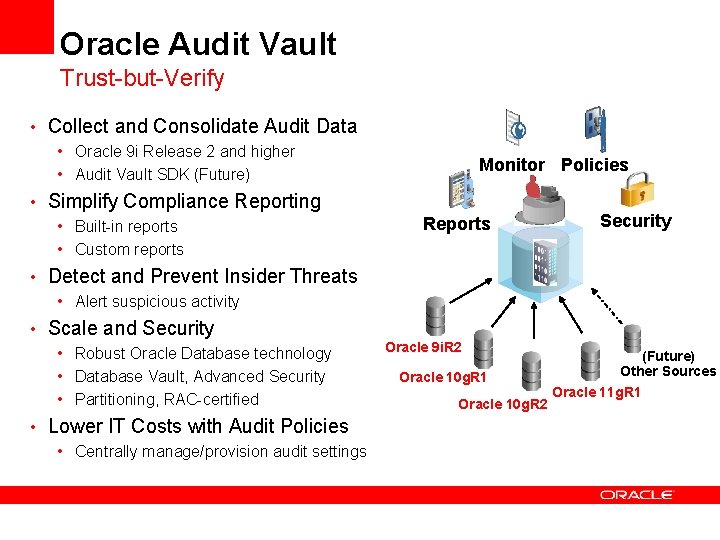
Oracle Audit Vault Trust-but-Verify • Collect and Consolidate Audit Data • Oracle 9 i Release 2 and higher • Audit Vault SDK (Future) Monitor Policies • Simplify Compliance Reporting • Built-in reports • Custom reports Reports Security • Detect and Prevent Insider Threats • Alert suspicious activity • Scale and Security • Robust Oracle Database technology • Database Vault, Advanced Security • Partitioning, RAC-certified • Lower IT Costs with Audit Policies • Centrally manage/provision audit settings Oracle 9 i. R 2 Oracle 10 g. R 1 Oracle 10 g. R 2 (Future) Other Sources Oracle 11 g. R 1

Audit Vault Reports Audit Assessments & Custom Reports • Out-of-the-box reports • Privileged user activity • Role grants • DDL activity • Login/logout • Access to sensitive data • User-defined reports • What privileged users did on the financial database? • What user ‘A’ did across multiple databases? • Who accessed sensitive data? • Custom reports • Oracle BI Publisher, Application Express, or 3 rd party tools

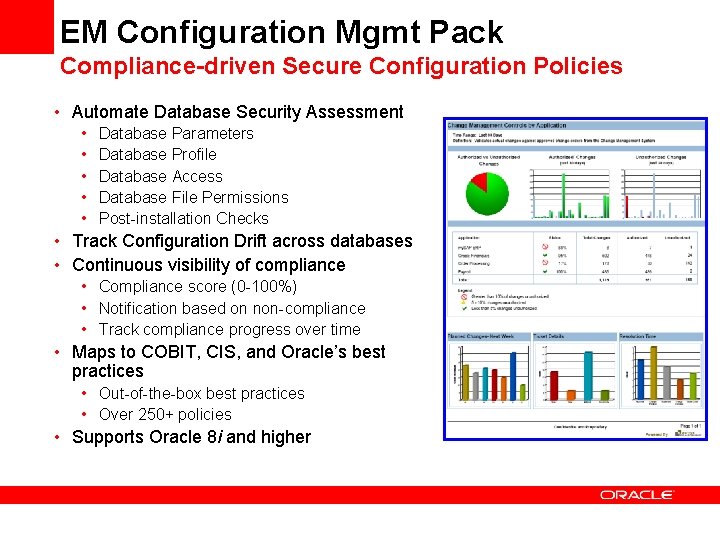
EM Configuration Mgmt Pack Compliance-driven Secure Configuration Policies • Automate Database Security Assessment • Database Parameters • Database Profile • Database Access • Database File Permissions • Post-installation Checks • Track Configuration Drift across databases • Continuous visibility of compliance • Compliance score (0 -100%) • Notification based on non-compliance • Track compliance progress over time • Maps to COBIT, CIS, and Oracle’s best practices • Out-of-the-box best practices • Over 250+ policies • Supports Oracle 8 i and higher

Data Security: Oracle Products User Management • Oracle Identity Management • Enterprise User Security Access Control • Oracle Database Vault • Oracle Label Security • Virtual Private Database Core Platform Security Monitoring • Database Auditing • Oracle Audit Vault • EM Configuration Pack Data Protection • Oracle Advanced Security • EM Data Masking • Oracle Secure Backup

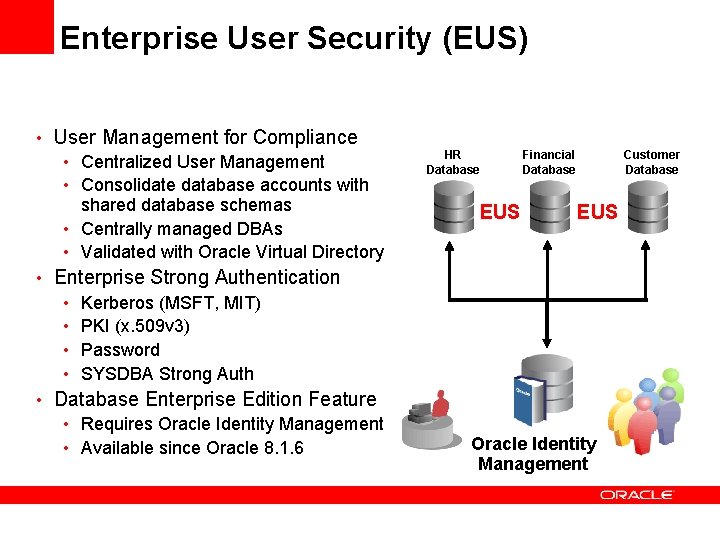
Enterprise User Security (EUS) • User Management for Compliance • Centralized User Management • Consolidate database accounts with shared database schemas • Centrally managed DBAs • Validated with Oracle Virtual Directory • Enterprise Strong Authentication • Kerberos (MSFT, MIT) • PKI (x. 509 v 3) • Password • SYSDBA Strong Auth • Database Enterprise Edition Feature • Requires Oracle Identity Management • Available since Oracle 8. 1. 6 HR Database EUS Financial Database Customer Database EUS Oracle Identity Management

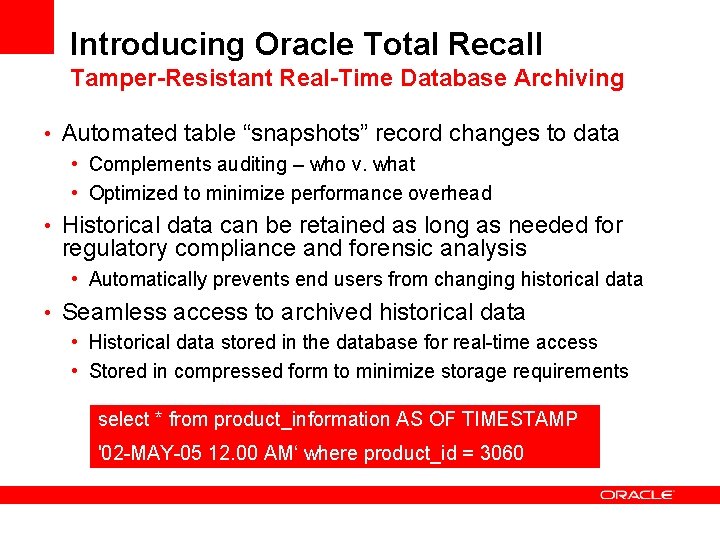
Introducing Oracle Total Recall Tamper-Resistant Real-Time Database Archiving • Automated table “snapshots” record changes to data • Complements auditing – who v. what • Optimized to minimize performance overhead • Historical data can be retained as long as needed for regulatory compliance and forensic analysis • Automatically prevents end users from changing historical data • Seamless access to archived historical data • Historical data stored in the database for real-time access • Stored in compressed form to minimize storage requirements select * from product_information AS OF TIMESTAMP '02 -MAY-05 12. 00 AM‘ where product_id = 3060

<Insert Picture Here> Leveraging Oracle Database Security for PCI and SOX

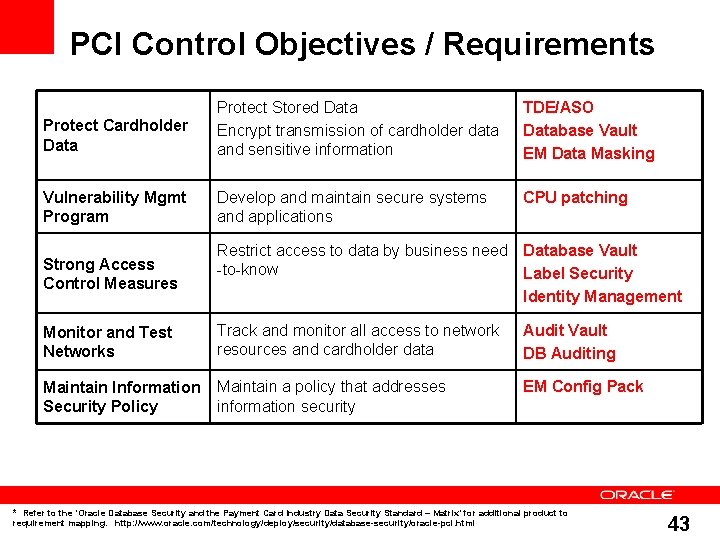
PCI Control Objectives / Requirements Protect Cardholder Data Protect Stored Data Encrypt transmission of cardholder data and sensitive information TDE/ASO Database Vault EM Data Masking Vulnerability Mgmt Program Develop and maintain secure systems and applications CPU patching Strong Access Control Measures Restrict access to data by business need Database Vault -to-know Label Security Identity Management Monitor and Test Networks Track and monitor all access to network resources and cardholder data Audit Vault DB Auditing Maintain Information Security Policy Maintain a policy that addresses information security EM Config Pack * Refer to the ‘Oracle Database Security and the Payment Card Industry Data Security Standard – Matrix’ for additional product to requirement mapping. http: //www. oracle. com/technology/deploy/security/database-security/oracle-pci. html 43

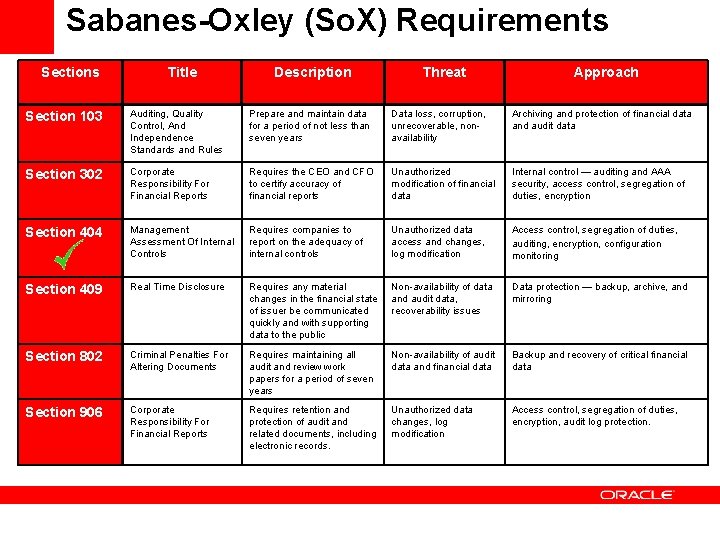
Sabanes-Oxley (So. X) Requirements Sections Title Description Threat Approach Section 103 Auditing, Quality Control, And Independence Standards and Rules Prepare and maintain data for a period of not less than seven years Data loss, corruption, unrecoverable, nonavailability Archiving and protection of financial data and audit data Section 302 Corporate Responsibility For Financial Reports Requires the CEO and CFO to certify accuracy of financial reports Unauthorized modification of financial data Internal control — auditing and AAA security, access control, segregation of duties, encryption Section 404 Management Assessment Of Internal Controls Requires companies to report on the adequacy of internal controls Unauthorized data access and changes, log modification Access control, segregation of duties, auditing, encryption, configuration monitoring Section 409 Real Time Disclosure Requires any material changes in the financial state of issuer be communicated quickly and with supporting data to the public Non-availability of data and audit data, recoverability issues Data protection — backup, archive, and mirroring Section 802 Criminal Penalties For Altering Documents Requires maintaining all audit and review work papers for a period of seven years Non-availability of audit data and financial data Backup and recovery of critical financial data Section 906 Corporate Responsibility For Financial Reports Requires retention and protection of audit and related documents, including electronic records. Unauthorized data changes, log modification Access control, segregation of duties, encryption, audit log protection.

Data Security: Oracle Products User Management Access Control • Oracle Identity Management • Enterprise User Security • Oracle Database Vault • Oracle Label Security • Virtual Private Database Core Platform Security Monitoring • Database Auditing • Oracle Audit Vault • EM Configuration Pack Data Protection • Oracle Advanced Security • EM Data Masking • Oracle Secure Backup

Learn More Technology Overview • Visit: oracle. com/security View Whitepapers and webinars Technical Information, Demos, Software • Visit OTN: otn. oracle. com -> products -> database -> security and compliance • PCI matrix • Step by step examples for Database Vault, Transparent Data Encryption and more

 Quotation sandwich
Quotation sandwich Thinking affects our language which then affects our
Thinking affects our language which then affects our Our census our future
Our census our future Longing for peace our world is troubled
Longing for peace our world is troubled Our life is what our thoughts make it
Our life is what our thoughts make it We bow our hearts we bend our knees
We bow our hearts we bend our knees Our census our future
Our census our future Our life is what our thoughts make it
Our life is what our thoughts make it Money is our madness
Money is our madness Our awareness of ourselves and our environment
Our awareness of ourselves and our environment Awareness of ourselves and our environment
Awareness of ourselves and our environment God our father christ our brother
God our father christ our brother Our future is in our hands quotes
Our future is in our hands quotes Awareness of ourselves and our environment is
Awareness of ourselves and our environment is Our awareness of ourselves and our environment
Our awareness of ourselves and our environment Balance in hair design
Balance in hair design Move in a circular or semi-circular direction
Move in a circular or semi-circular direction It has 4-5 inches finely tapered blades
It has 4-5 inches finely tapered blades A humorous scene or speech intended to lighten the mood
A humorous scene or speech intended to lighten the mood What is intended benefit
What is intended benefit It simulate or animate some features of intended system.
It simulate or animate some features of intended system. Fuses and circuit breakers are intended primarily for the
Fuses and circuit breakers are intended primarily for the Intended curriculum
Intended curriculum Usability specification in hci
Usability specification in hci Bdm tasmania
Bdm tasmania Who is the intended audience for this text
Who is the intended audience for this text Intended outcome
Intended outcome It is the intended height of the function?
It is the intended height of the function? In her statement (lines 53-54) miss nightingale intended to
In her statement (lines 53-54) miss nightingale intended to Most inhalants are actually intended to be _______________
Most inhalants are actually intended to be _______________ Hippo document analysis example
Hippo document analysis example Direct and indirect voluntariness
Direct and indirect voluntariness Intended audience of the declaration of independence
Intended audience of the declaration of independence Fuses and circuit breakers are intended primarily for the
Fuses and circuit breakers are intended primarily for the What is the destructive event or prank the virus delivers
What is the destructive event or prank the virus delivers Who was the intended audience
Who was the intended audience The poster was intended to
The poster was intended to The great gatsby vocabulary chapter 2
The great gatsby vocabulary chapter 2 The antis creed
The antis creed Xml
Xml Intended message
Intended message Intended audience
Intended audience Composition is the arrangement of
Composition is the arrangement of A humorous scene or speech intended to lighten the mood
A humorous scene or speech intended to lighten the mood Which core capability makes it possible
Which core capability makes it possible Intended audience
Intended audience Complications of hydrocephalus
Complications of hydrocephalus Intended audience
Intended audience