Tactic 1 Adopt Least Privilege Zaid Arafeh Clare














- Slides: 22

Tactic 1: Adopt Least Privilege Zaid Arafeh, Clare Kearney Microsoft Services Cybersecurity Source: Engineering journal - 'The White Star liner Titanic', vol. 91.

• Part I: Understanding Tier-0 • Part II: Minimizing Privilege


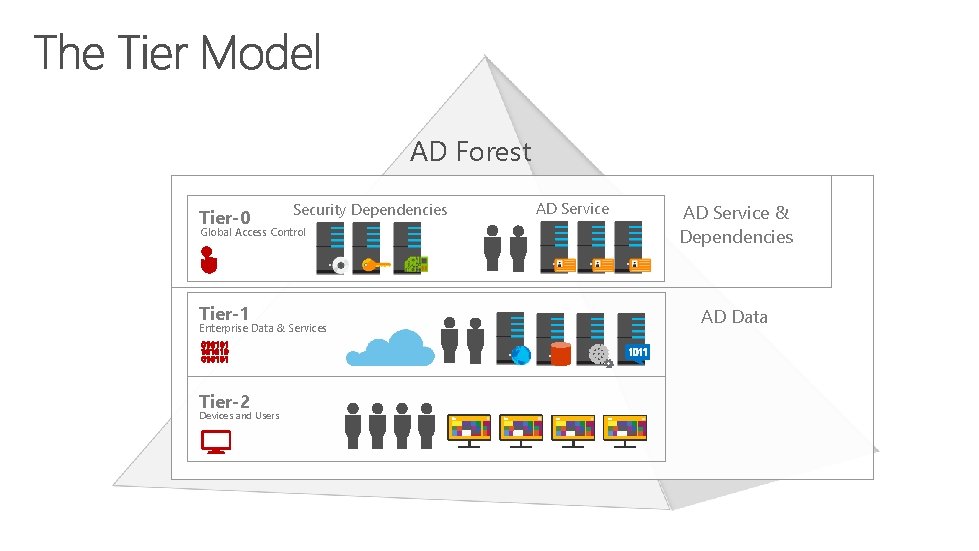
AD Forest Tier-0 Security Dependencies Global Access Control Tier-1 Enterprise Data & Services Tier-2 Devices and Users AD Service & Dependencies AD Data


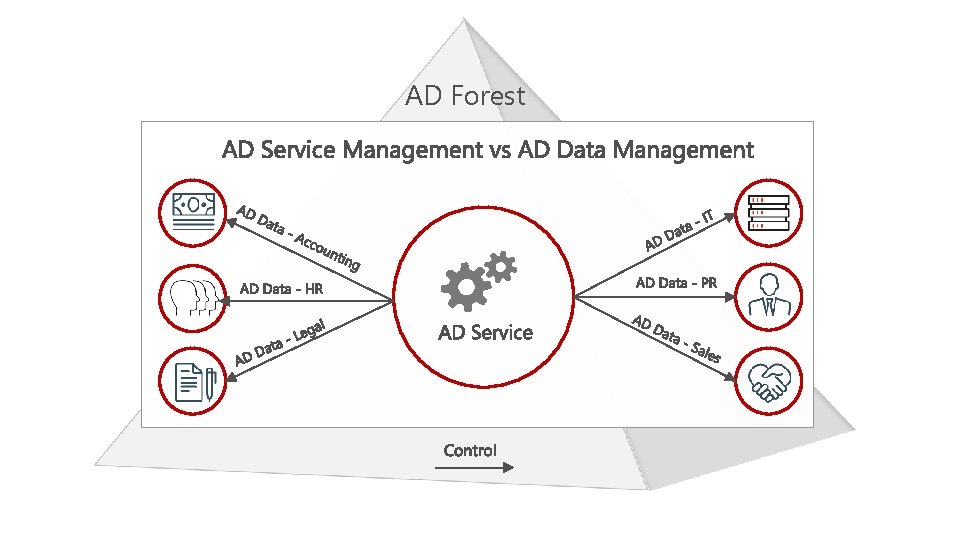
AD Forest


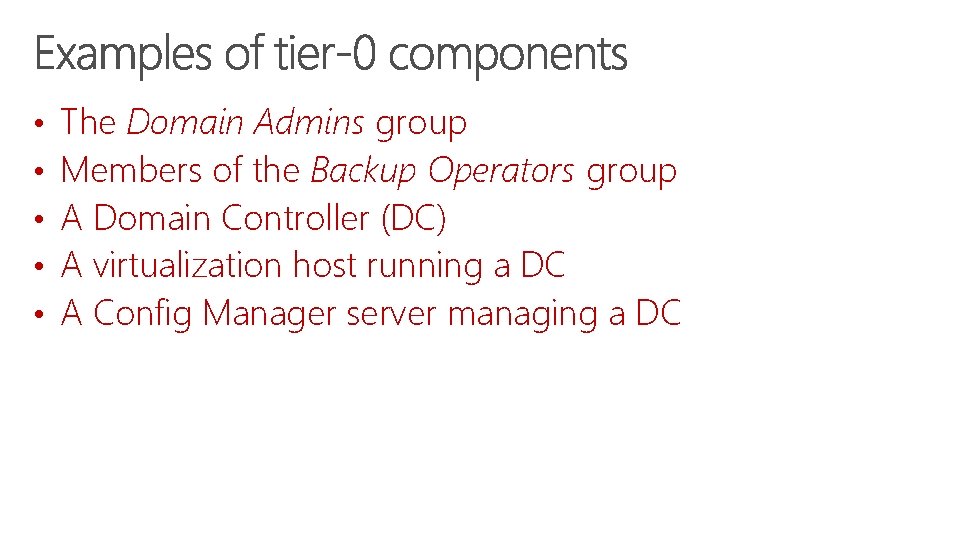
• • • The Domain Admins group Members of the Backup Operators group A Domain Controller (DC) A virtualization host running a DC A Config Manager server managing a DC

Napoléon Bonaparte 1769 - 1821

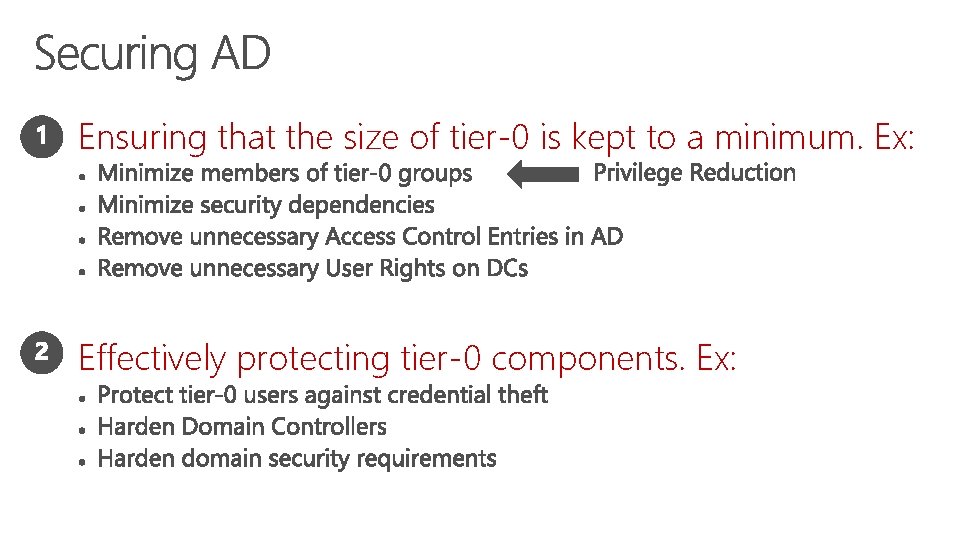
• Ensuring that the size of tier-0 is kept to a minimum. Ex: • Effectively protecting tier-0 components. Ex:

AND TREAT THEM AS SUCH


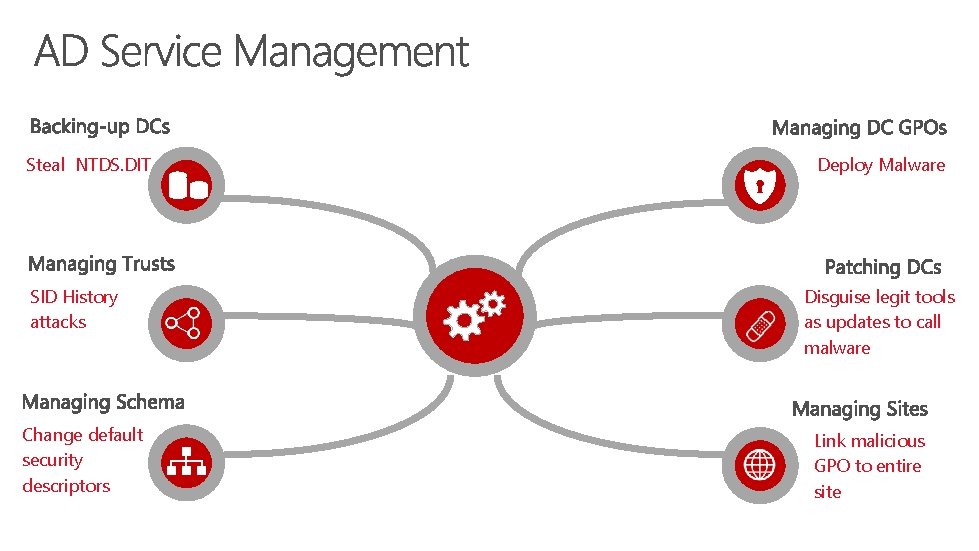
Steal NTDS. DIT SID History attacks Change default security descriptors Deploy Malware Disguise legit tools as updates to call malware Link malicious GPO to entire site


• For Built-in Tier-0 Groups • For resource management • For tier management • For service accounts

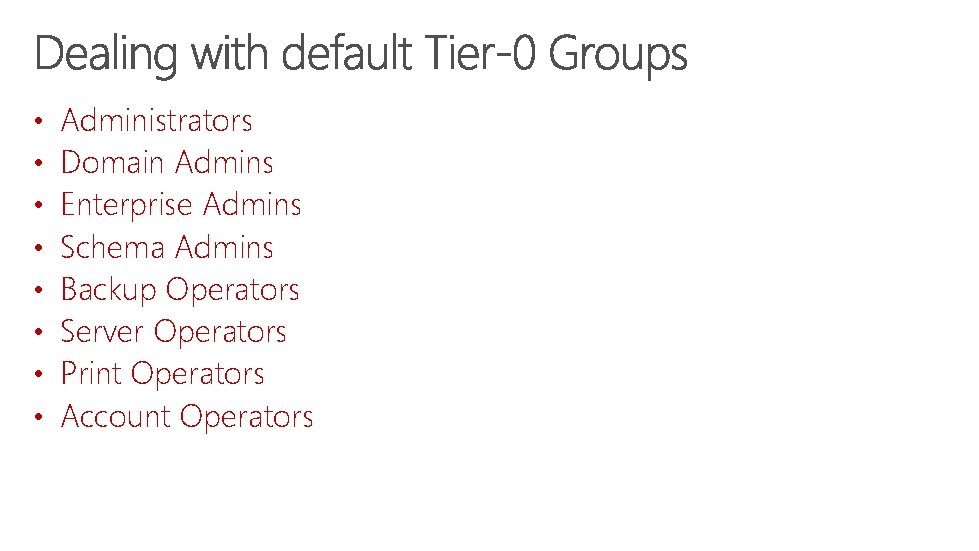
• • Administrators Domain Admins Enterprise Admins Schema Admins Backup Operators Server Operators Print Operators Account Operators



• Minimize privileged group membership • Configure alerting on privileged groups

• Tactic #2: Protect Privileged Identities

• AD ACL Scanner Tool by Robin Granberg • Active Directory Group Descriptions • Need help from Microsoft Services Cybersecurity? Cyber. RFI@microsoft. com

 Zaid arafeh
Zaid arafeh Zaid arafeh
Zaid arafeh Secure architecture principles isolation and less
Secure architecture principles isolation and less Least privilege security design principle
Least privilege security design principle Ambo university
Ambo university Least privilege security design principle
Least privilege security design principle Principle of least privilege
Principle of least privilege Why did chevron adopt bpi
Why did chevron adopt bpi Adopt uskids
Adopt uskids Chapter 5 section 1 cultures of the mountains and the sea
Chapter 5 section 1 cultures of the mountains and the sea Steps of remedial teaching
Steps of remedial teaching What policy did the qing adopt regarding foreign trade?
What policy did the qing adopt regarding foreign trade? Zaid mansuri
Zaid mansuri Dr omar zaid
Dr omar zaid Dr zaid malik
Dr zaid malik Robert zaid
Robert zaid Azza ouled zaid
Azza ouled zaid Yasmin ayoubi
Yasmin ayoubi Conclusion of artificial intelligence
Conclusion of artificial intelligence Zaid admani
Zaid admani Tactic rh
Tactic rh Hardball tactics are designed to
Hardball tactics are designed to Simple tactic
Simple tactic