Synchronization Chapter 5 Chapter Outline Clock Synchronization Physical











- Slides: 26

Synchronization Chapter 5

Chapter Outline • Clock Synchronization – Physical Clocks – Clock synchronization algorithms • Logical Clocks – Lamport’s logical clock – Vector clocks • Mutual Exclusion – – A centralized algorithm A decentralized algorithm A distributed algorithm A token ring algorithm • Election Algorithms – Bully algorithm – Ring algorithm

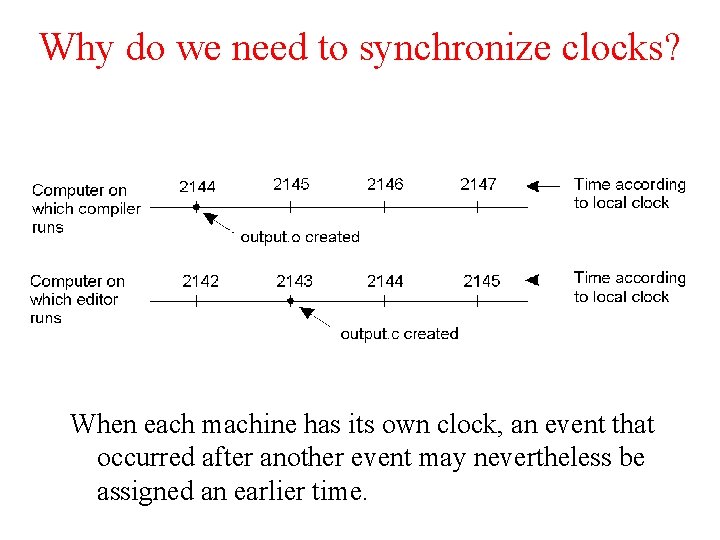
Why do we need to synchronize clocks? When each machine has its own clock, an event that occurred after another event may nevertheless be assigned an earlier time.

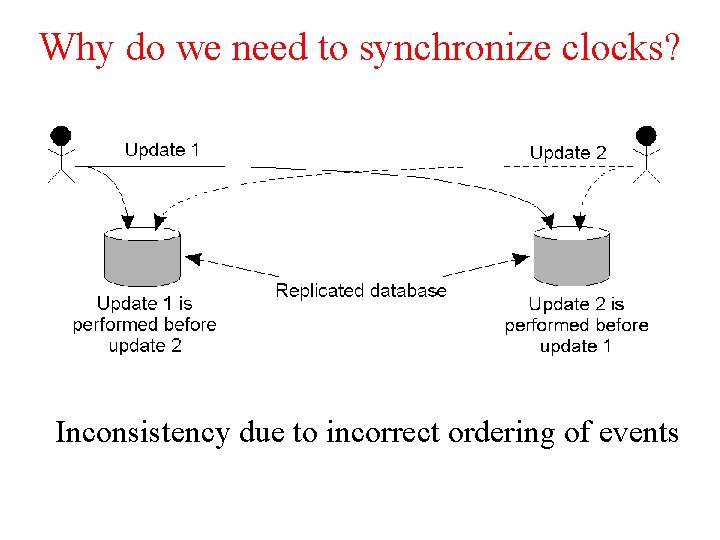
Why do we need to synchronize clocks? Inconsistency due to incorrect ordering of events

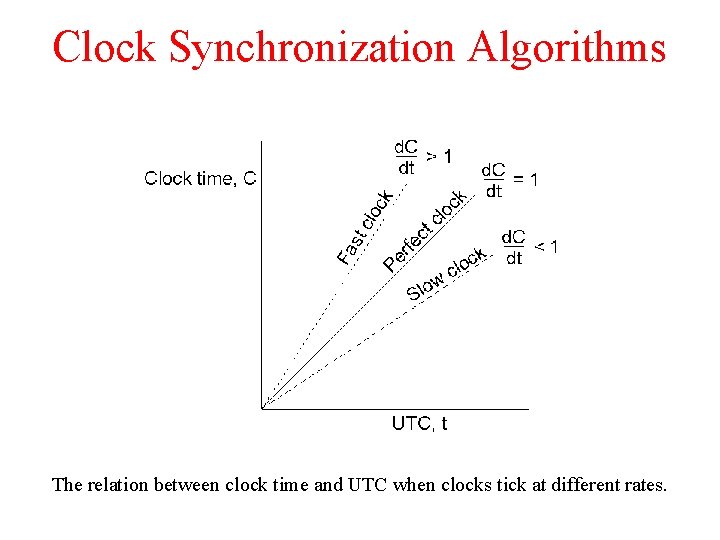
Clock Synchronization Algorithms The relation between clock time and UTC when clocks tick at different rates.

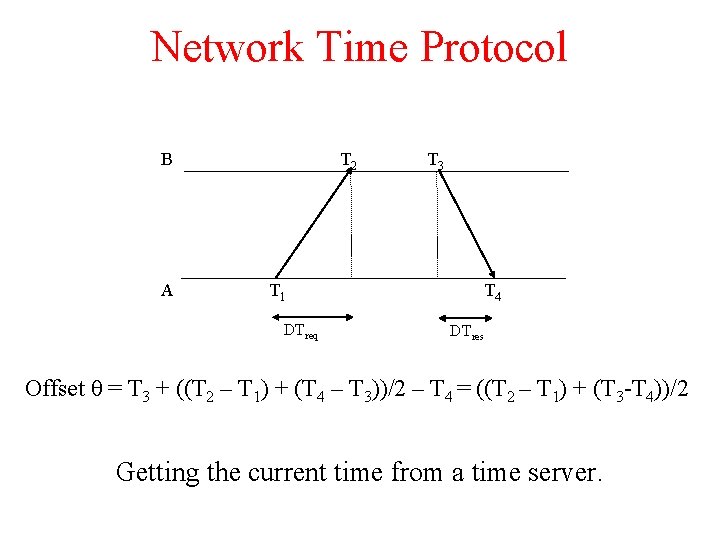
Network Time Protocol B A T 2 T 1 DTreq T 3 T 4 DTres Offset θ = T 3 + ((T 2 – T 1) + (T 4 – T 3))/2 – T 4 = ((T 2 – T 1) + (T 3 -T 4))/2 Getting the current time from a time server.

The Berkeley Algorithm a) b) c) The time daemon asks all the other machines for their clock values The machines answer The time daemon tells everyone how to adjust their clock

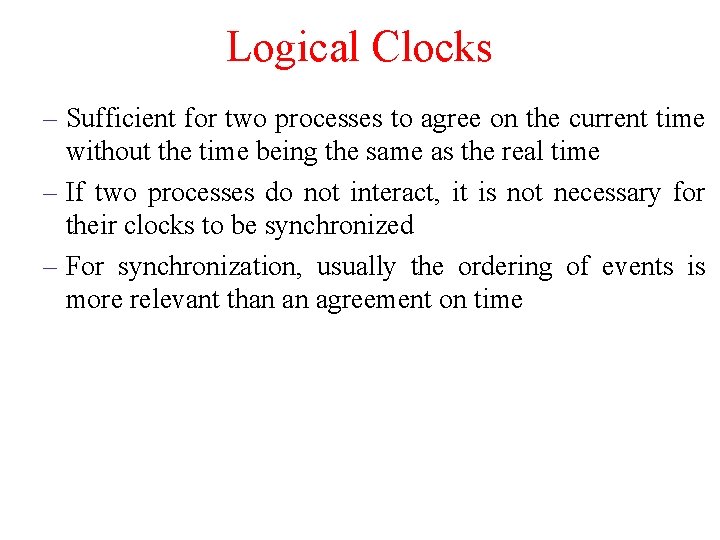
Logical Clocks – Sufficient for two processes to agree on the current time without the time being the same as the real time – If two processes do not interact, it is not necessary for their clocks to be synchronized – For synchronization, usually the ordering of events is more relevant than an agreement on time

Lamport’s Logical Clocks (1) – The events are logically ordered by defining a relation happens-before as follows: – If a and b are events in the same process, and a occurs before b, then a → b is true. – If a is the event of a message being sent by one process, and b is the event of the message being received by another process, then a →b is also true. – A message cannot be received before it is sent, or even at the same time it is sent.

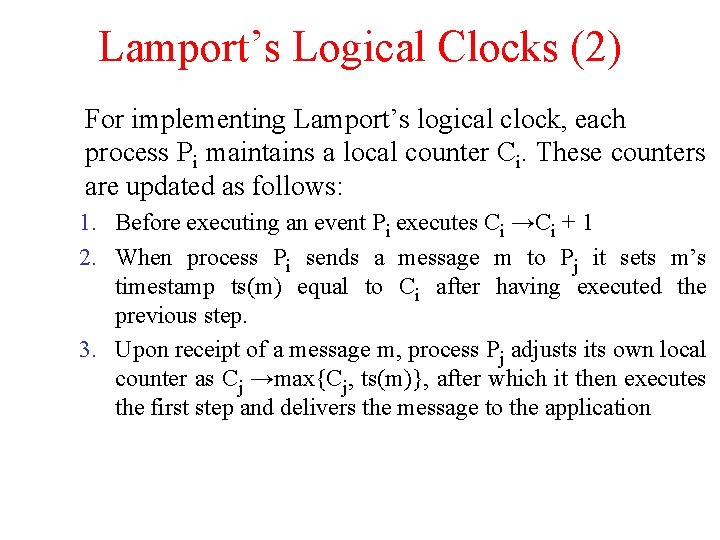
Lamport’s Logical Clocks (2) For implementing Lamport’s logical clock, each process Pi maintains a local counter Ci. These counters are updated as follows: 1. Before executing an event Pi executes Ci →Ci + 1 2. When process Pi sends a message m to Pj it sets m’s timestamp ts(m) equal to Ci after having executed the previous step. 3. Upon receipt of a message m, process Pj adjusts its own local counter as Cj →max{Cj, ts(m)}, after which it then executes the first step and delivers the message to the application

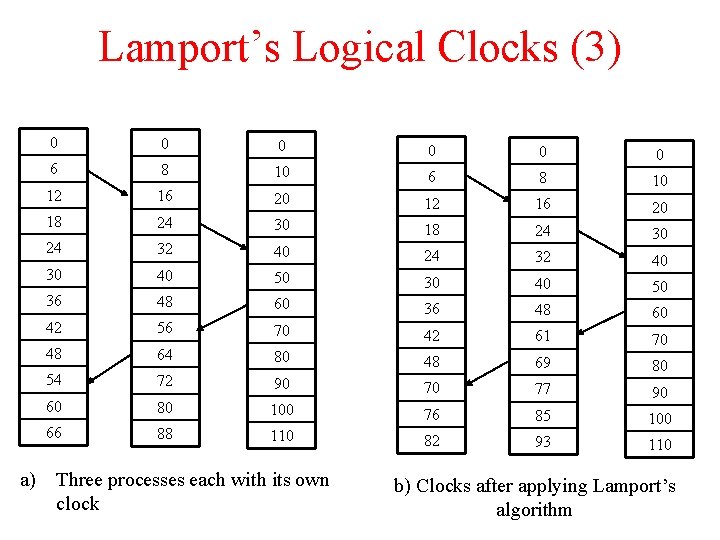
Lamport’s Logical Clocks (3) 0 0 6 0 8 10 0 6 12 8 16 20 10 12 18 16 24 30 20 18 24 24 32 40 30 24 30 32 40 50 40 30 36 40 48 60 50 36 42 48 56 70 60 42 48 61 64 80 70 48 54 69 72 90 80 70 60 77 80 100 90 76 66 85 88 110 100 82 93 110 a) Three processes each with its own clock b) Clocks after applying Lamport’s algorithm

Example: Totally-Ordered Multicasting Updating a replicated database and leaving it in an inconsistent state.

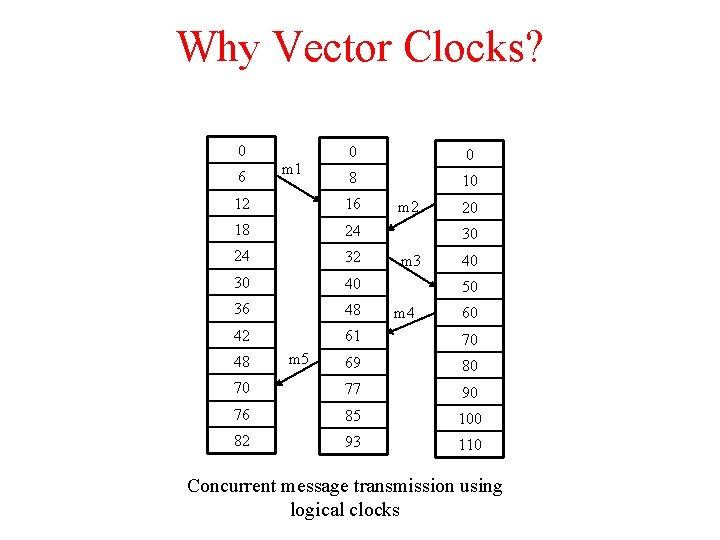
Why Vector Clocks? 0 6 m 1 0 0 8 10 12 16 18 24 24 32 30 40 36 48 42 61 70 69 80 70 77 90 76 85 100 82 93 110 48 m 5 m 2 20 30 m 3 40 50 m 4 60 Concurrent message transmission using logical clocks

Vector Clocks (1) – Vector clocks capture causality – A vector clock VC(a) assigned to an event a has the property that if VC(a) < VC(b) for some event b, then event a is known to causally precede b. – Vector clocks are implemented by letting each process Pi maintain a vector VCi With the following properties: – VCi[i] is the number of events that have occurred so far at Pi. – If VCi[j] = k then Pi knows that k events have occurred at Pj.

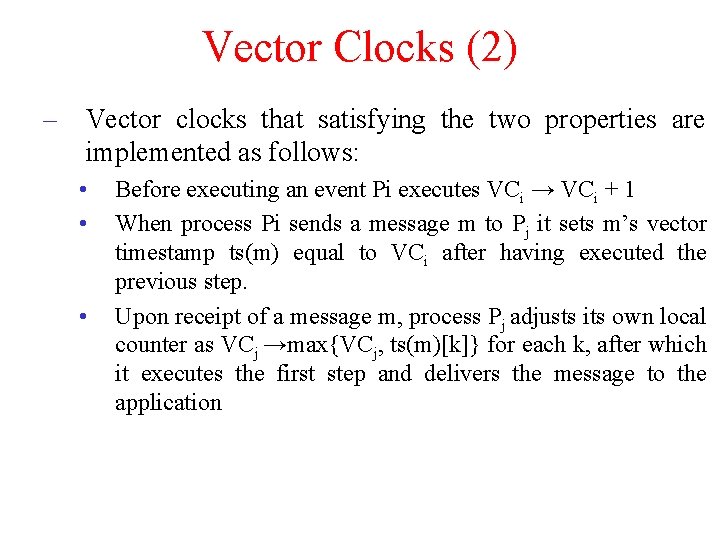
Vector Clocks (2) – Vector clocks that satisfying the two properties are implemented as follows: • • • Before executing an event Pi executes VCi → VCi + 1 When process Pi sends a message m to Pj it sets m’s vector timestamp ts(m) equal to VCi after having executed the previous step. Upon receipt of a message m, process Pj adjusts its own local counter as VCj →max{VCj, ts(m)[k]} for each k, after which it executes the first step and delivers the message to the application

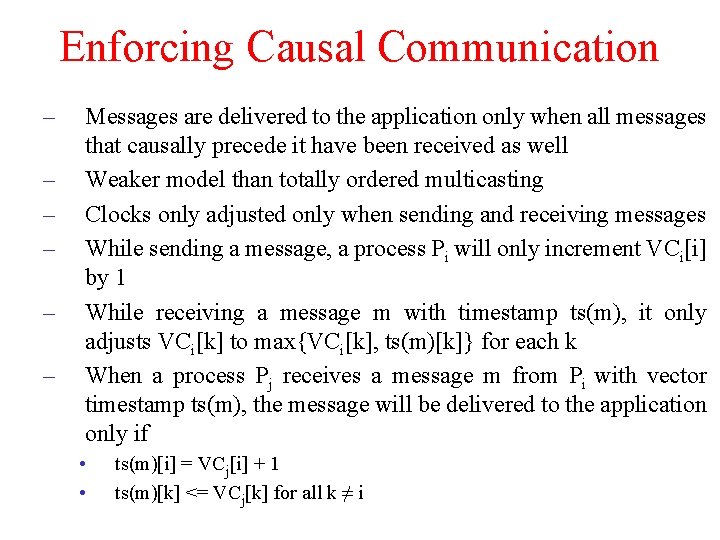
Enforcing Causal Communication – – – Messages are delivered to the application only when all messages that causally precede it have been received as well Weaker model than totally ordered multicasting Clocks only adjusted only when sending and receiving messages While sending a message, a process Pi will only increment VCi[i] by 1 While receiving a message m with timestamp ts(m), it only adjusts VCi[k] to max{VCi[k], ts(m)[k]} for each k When a process Pj receives a message m from Pi with vector timestamp ts(m), the message will be delivered to the application only if • • ts(m)[i] = VCj[i] + 1 ts(m)[k] <= VCj[k] for all k ≠ i

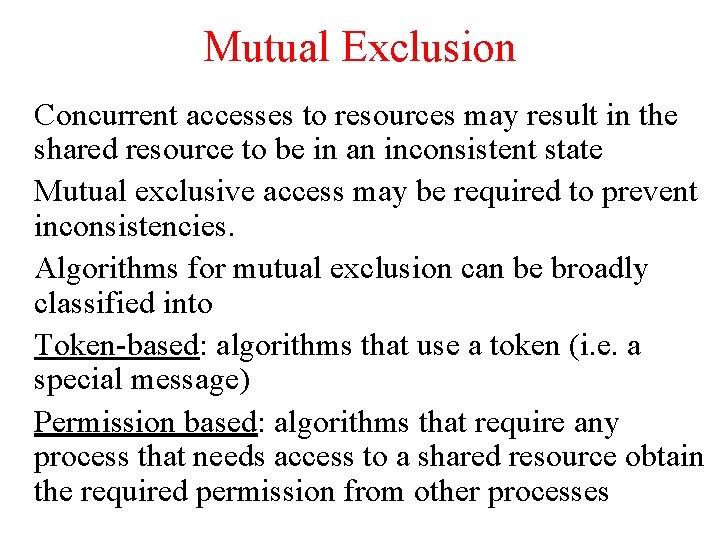
Mutual Exclusion Concurrent accesses to resources may result in the shared resource to be in an inconsistent state Mutual exclusive access may be required to prevent inconsistencies. Algorithms for mutual exclusion can be broadly classified into Token-based: algorithms that use a token (i. e. a special message) Permission based: algorithms that require any process that needs access to a shared resource obtain the required permission from other processes

A Centralized Algorithm a) b) c) Process 1 asks the coordinator for permission to enter a critical region. Permission is granted Process 2 then asks permission to enter the same critical region. The coordinator does not reply. When process 1 exits the critical region, it tells the coordinator, when then replies to 2

A decentralized Algorithm Assumptions: – Each resource is replicated n times. – Every replica has its own coordinator for controlling concurrent access. – When a coordinator crashes it recovers but would have forgotten the vote it gave before it crashed When a process wants to access the resource, it will simply need to get a majority vote from m > n/2 coordinators.

A Distributed Algorithm a) b) c) Two processes want to enter the same critical region at the same moment. Process 0 has the lowest timestamp, so it wins. When process 0 is done, it sends an OK also, so 2 can now enter the critical region.

A Token Ring Algorithm a) An unordered group of processes on a network. b) A logical ring constructed in software.

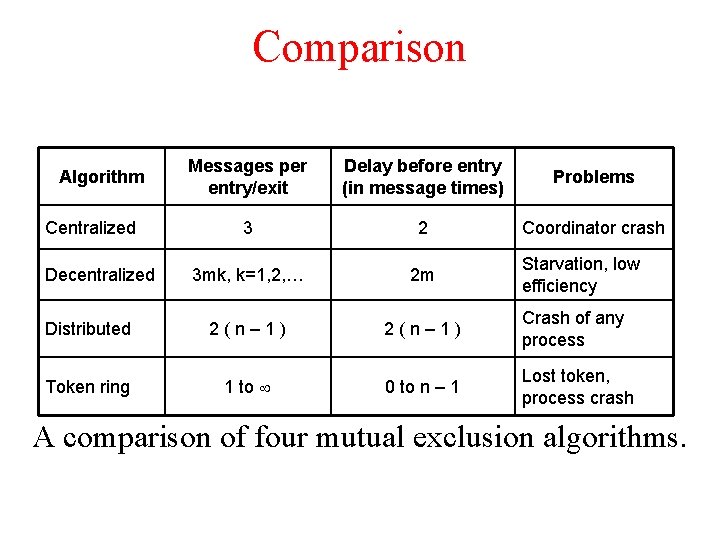
Comparison Messages per entry/exit Delay before entry (in message times) Problems 3 2 Coordinator crash 3 mk, k=1, 2, … 2 m Distributed 2(n– 1) Crash of any process Token ring 1 to 0 to n – 1 Lost token, process crash Algorithm Centralized Decentralized Starvation, low efficiency A comparison of four mutual exclusion algorithms.

The Bully Algorithm (1) The bully election algorithm a) Process 4 holds an election b) Process 5 and 6 respond, telling 4 to stop c) Now 5 and 6 each hold an election

Bully Algorithm (2) d) e) Process 6 tells 5 to stop Process 6 wins and tells everyone

A Ring Algorithm Election algorithm using a ring.

References Lecture slides of Distributed Systems principles and paradigms by Andrew Tannenbaum and Van Steen, Prentice Hall India, 2002.