Suing Spammers for Fun and Profit Serge Egelman














- Slides: 30

Suing Spammers for Fun and Profit Serge Egelman CMU Usable Privacy and Security Laboratory http: //cups. cmu. edu/

“Two years from now, spam will be solved” -Bill Gates, February 24 th, 2004 • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

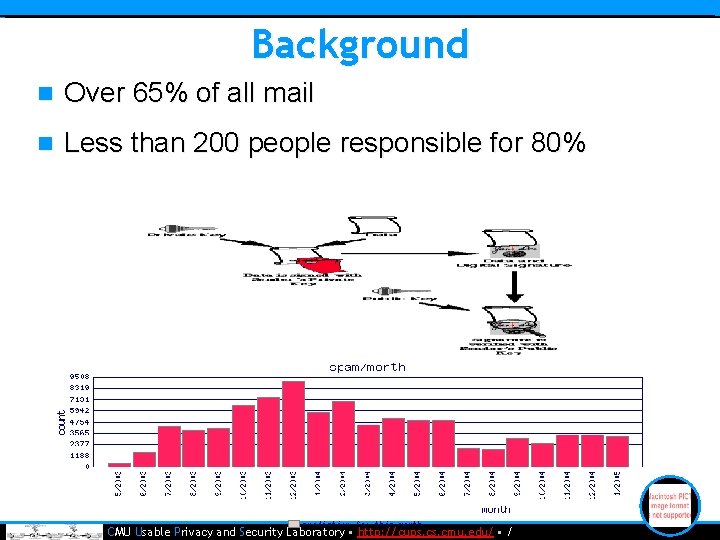
Background n Over 65% of all mail n Less than 200 people responsible for 80% • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Statistics • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Statistics • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Background n It’s cheap! n Wider audience n Profit guaranteed n Little work involved • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Background n Address harvesting • Web pages • Forums • USENET n Dictionary attacks n Purchased lists n No way out • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Profile of a Spammer n Alan Ralsky • 20 Computers § 190 Servers § 650, 000 messages/hour § 250 millions addresses § $500 for every million messages • Convicted Felon § 1992 Securities fraud § 1994 Insurance fraud • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Technical Means n Text recognition n Black hole lists n Statistical modeling • Neural networks n Cryptography • Digital signatures • Payment schemes • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Asymmetric Cryptography Example • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Digital Signature Example • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

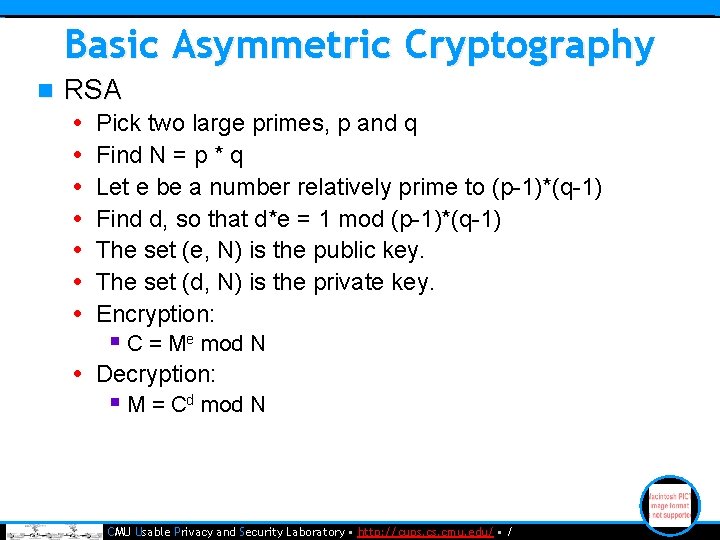
Basic Asymmetric Cryptography n RSA • Pick two large primes, p and q • Find N = p * q • Let e be a number relatively prime to (p-1)*(q-1) • Find d, so that d*e = 1 mod (p-1)*(q-1) • The set (e, N) is the public key. • The set (d, N) is the private key. • Encryption: § C = Me mod N • Decryption: § M = Cd mod N • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

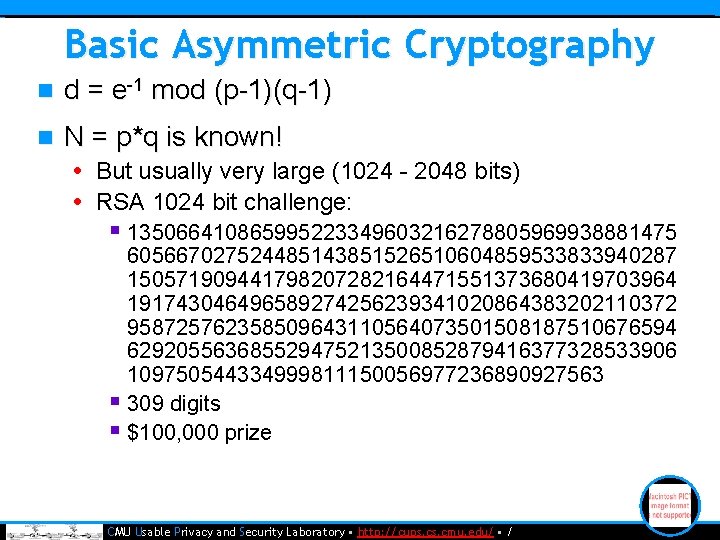
Basic Asymmetric Cryptography n d = e-1 mod (p-1)(q-1) n N = p*q is known! • But usually very large (1024 - 2048 bits) • RSA 1024 bit challenge: § 135066410865995223349603216278805969938881475 605667027524485143851526510604859533833940287 150571909441798207282164471551373680419703964 191743046496589274256239341020864383202110372 958725762358509643110564073501508187510676594 629205563685529475213500852879416377328533906 109750544334999811150056977236890927563 § 309 digits § $100, 000 prize • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

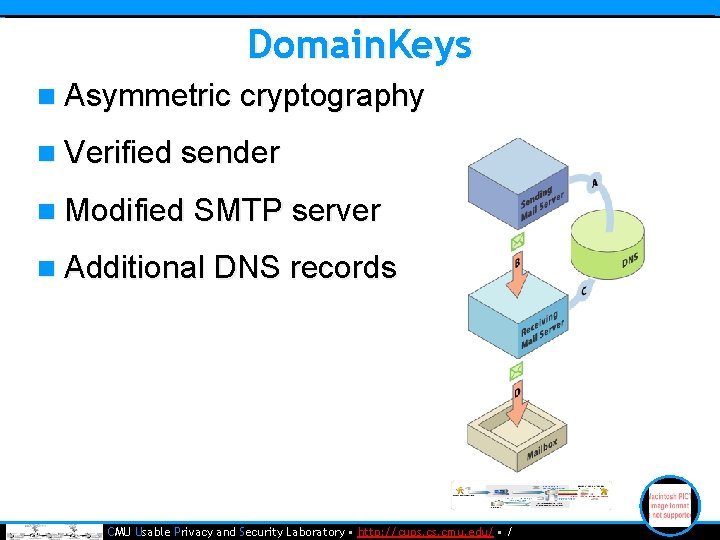
Domain. Keys n Asymmetric cryptography n Verified sender n Modified SMTP server n Additional DNS records • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Spam. Assassin n Multiple tests • Around 300 n Statistical modeling n Scoring • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Example Domain. Key-Signature: a=rsa-sha 1; q=dns; c=nofws; s=beta; d=gmail. com; h=received: message-id: date: from: replyto: subject: mime-version: content-type: content-transferencoding; b=ARBy. WZ 8/yk 5 cm 8 Ew/t. JZ 5 Uykez. QZkm/f. ZUV 6 Wkd 0 RAb 46 slx. Gg 8 TRQ 91 Dc 2 yi 8 ZIhb. Vz 1 TOc 94 Qe. RGg. HOfv. ALEtjqe. IA 1 L 1 z 3 y. Vt. Ta+4 BJG 4+oqi Ts. Ticz+b. I 2 h. Pd. Gl. GFRixb. Sshslvoyc 3 Fa. ISIICMx 7 Hlcq. CN/wmi. G 4 Q 0 uub 4= From: Matthew Eaton <mattheweaton@gmail. com> Reply-To: Matthew Eaton <mattheweaton@gmail. com> To: serge@guanotronic. com Subject: test from gmail X-Spam-Status: No, hits=-4. 9 required=5. 0 tests=BAYES_00 autolearn=no version=2. 63 X-Spam-Checker-Version: Spam. Assassin 2. 63 (2004 -01 -11) on jabba. geek. haus • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Sender Policy Framework n Prevents forgery n Requires DNS record n Recipient confirms sender n Open standard • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Graylisting n Whitelist maintained n Other mail temporarily rejected n Spammers might give up n Mail delivery delayed n Spammers will adapt • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

The Hunt n Contact Info • URLs • Email Addresses n WHOIS/DNS n USENET • news. admin. net-abuse. email n Databases: • Spews. org • Spamhaus. org • Open. RBL. org • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Legal Means n Foreign spam, local companies n One weak federal law n 35 State laws (as of 2003) n A few heuristics: • Forged headers • “ADV” subject line • Misleading subject • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Telecommunications Consumer Protection Act n The TCPA (U. S. C 47 § 227): • "equipment which has the capacity to transcribe text or images (or both) from an electronic signal received over a regular telephone line onto paper. “ • $500 or $1500 fine per message n Mark Reinertson v. Sears Roebuck • Michigan small claims • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Telecommunications Consumer Protection Act n Erie. Net, Inc. v. Velocity. Net, Inc. • US Court of Appeals, 3 rd Circuit, No. 97 -3562 • September 25, 1998 n “it is my hope that the States will make it as easy as possible for consumers to bring such actions, preferably in small claims court. ” –Senator Hollings n “The question, therefore, is whether Congress has provided for federal court jurisdiction over consumer suits under the TCPA. ” n U. S. C. 28 § 1331: The district courts shall have original jurisdiction of all civil actions arising under the Constitution, laws, or treaties of the United States • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

The CAN-SPAM Act 15 U. S. C. § 7702 n Requirements: • Deceptive Subjects • Falsified Headers • Valid Return Address • Opt-Out n Enforcement: • FTC • States • ISPs n Do-Not-Email List n Bounty Hunters n Sender: “a person who initiates such a message and whose product, service, or Internet web site is advertised or promoted by the message. ” n Preemption • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Virginia Laws n The VA Computer Crimes Act (18. 2 -§ 152) • Forged headers • $10/message or $25, 000/day • AOL and Verizon n Verizon v. Ralsky: $37 M n AOL v. Moore: $10 M n U. S. C. 28 § 1332: The district courts shall have original jurisdiction of all civil actions where the matter in controversy exceeds the sum or value of $75, 000, exclusive of interest and costs, and is between citizens of different States. • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Pennsylvania Laws n The Unsolicited Telecommunications Advertisement Act (73 § 2250) n Illegal activities: • Forged addresses • Misleading information • Lack of opt-out n Only enforced by AG and ISPs • $10/message for ISPs • 10% from AG • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /


Small Claims Court n Court summons: $30 -80 n Maximum claim: $8000 n Winning by default because the spammer didn’t bother to show up: Priceless • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

So you’ve won a judgment… n Domesticate the judgment n Summons to Answer Interrogatories n Writ of Fieri Facias n Garnishment Summons • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Criminal Penalties n You’ve got jail! • 1 year • 3 years: § $5, 000 profit § >2, 500 in 24 hours § >25, 000 in a month § >250, 000 in a year • 5 years for second offense • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /

Questions? • CMU Usable Privacy and Security Laboratory • http: //cups. cmu. edu/ • /
 Aaron egelman
Aaron egelman Smash the stack for fun and profit
Smash the stack for fun and profit Aleph one smashing the stack for fun and profit
Aleph one smashing the stack for fun and profit Smash the stack for fun and profit
Smash the stack for fun and profit Profit
Profit Economic profit vs accounting profit
Economic profit vs accounting profit Post acquisition profit is which profit
Post acquisition profit is which profit Serge delfos
Serge delfos Edmond vidal et sa femme
Edmond vidal et sa femme Serge rozenberg
Serge rozenberg Serge abiteboul
Serge abiteboul Serge rubinstein
Serge rubinstein Serge kreiker
Serge kreiker Bambou (chanteuse)
Bambou (chanteuse) Serge lama je voudrais tant que tu sois là
Serge lama je voudrais tant que tu sois là Robert
Robert Ecusson sdmis
Ecusson sdmis Serge faure
Serge faure Je voudrais tant que tu sois la verlaine
Je voudrais tant que tu sois la verlaine Serge dezutter
Serge dezutter Serge hanna
Serge hanna Serge djama
Serge djama Serge duarte
Serge duarte Duite tissage
Duite tissage Serge hanna
Serge hanna Serge duarte
Serge duarte Hypoinsulinisme
Hypoinsulinisme Rue de seine paris
Rue de seine paris Serge hanna
Serge hanna Serge bard proviseur
Serge bard proviseur Serge tisseron
Serge tisseron