Signcryption what why and how Yevgeniy Dodis New




![Prior Work • Initial study of signcryption [Zheng 97, …] – Main motivation efficiency Prior Work • Initial study of signcryption [Zheng 97, …] – Main motivation efficiency](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-5.jpg)
![Our Results I [ADR 02] • Formal definition(s) of signcryption – Multi-user vs. Two-user Our Results I [ADR 02] • Formal definition(s) of signcryption – Multi-user vs. Two-user](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-6.jpg)
![Our Results II [DFW 03] • More efficient parallel signcryption: Padding-based Parallel Signcryption (Pb. Our Results II [DFW 03] • More efficient parallel signcryption: Padding-based Parallel Signcryption (Pb.](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-7.jpg)
![Our Results III [DA 03] • General way to build signcryption on long messages Our Results III [DA 03] • General way to build signcryption on long messages](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-8.jpg)










- Slides: 40

Signcryption: what, why and how Yevgeniy Dodis New York University

Signature and Encryption • Most basic cryptographic tools • Signature: – Receiver is sure message came from sender – Provides Authentication • Encryption: – Only receiver can understand the message – Provides Privacy

Common Design Wisdom • Never mix things together • Make the design as modular as possible – Have freedom to design independent privacy and authentication components • When both are needed, combine known solutions – Encrypt-then-sign (Et. S): Sig(Enc(m)) – Sign-then-encrypt (St. E): Enc(Sig(m)) • But given both are needed so often, shall we define/design tailored solutions? Signcryption? ? ?

YES Signcryption as a Primitive? • Are we sure Et. S and St. E are “secure”? – NO, if we are not careful ! (yes, if we are) • Do we know exactly what we mean by “private authenticated communication”? – Definition is non-trivial ! • Maybe we can build significantly more efficient/secure solutions than Et. S/St. E? • Maybe we can in fact simplify protocol design by having this high-level primitive?
![Prior Work Initial study of signcryption Zheng 97 Main motivation efficiency Prior Work • Initial study of signcryption [Zheng 97, …] – Main motivation efficiency](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-5.jpg)
Prior Work • Initial study of signcryption [Zheng 97, …] – Main motivation efficiency – Security arguments: no formal definitions/proofs • Using authentication to go CPA->CCA – El. Gamal Encryption [TY 98, SJ 00] – Symmetric setting [BN 00, K 01, BR 00] • Authenticated Encryption (symmetric setting) – Definitions [KY 00, BN 00, BR 00] – Sequential Composition Et. A/At. E [BN 00, K 01] Called “good” if MAC helps CPA->CCA (justified but unnatural) – Encrypt/encipher-with-redundancy [AB 01, BR 00] – New Block Cipher Modes (RFC, IAPM, OCB, SNCBC, …)
![Our Results I ADR 02 Formal definitions of signcryption Multiuser vs Twouser Our Results I [ADR 02] • Formal definition(s) of signcryption – Multi-user vs. Two-user](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-6.jpg)
Our Results I [ADR 02] • Formal definition(s) of signcryption – Multi-user vs. Two-user setting – “Insider” vs. “Outsider” distinction • Et. S/St. E are secure if modeled properly… • Paradigm of parallel signcryption: – Performs expensive Enc and Sig in parallel – Commit-then-Encrypt-and-Sign (Ct. S&E) – Leads to fast On-line/Off-line Signcryption • Definitional inadequacy of CCA security
![Our Results II DFW 03 More efficient parallel signcryption Paddingbased Parallel Signcryption Pb Our Results II [DFW 03] • More efficient parallel signcryption: Padding-based Parallel Signcryption (Pb.](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-7.jpg)
Our Results II [DFW 03] • More efficient parallel signcryption: Padding-based Parallel Signcryption (Pb. PS) – Fully compatible with PKCS#1 standard • • Works with PSS-R, OAEP+ & other paddings Based on any TDP f (e. g. , RSA) Simple and flexible key management Same f can be used to both send & receive data… – Effortlessly supports associated data – Tight exact security and many more… • New notion: universal two-padding schemes – New padding: PSEP, hybrid of PSS-R & OAEP
![Our Results III DA 03 General way to build signcryption on long messages Our Results III [DA 03] • General way to build signcryption on long messages](https://slidetodoc.com/presentation_image_h2/81f7999fa7b5599176502cb136b5b68f/image-8.jpg)
Our Results III [DA 03] • General way to build signcryption on long messages from that on short messages – Very simple and efficient – Couple with Pb. PS very practical signcryption ! • Utilizes a new primitive of independent interest: Concealment • Strong version equivalent to CRHFs, weak version can be built from UOWHFs (and, thus, OWFs) • Remotely Keyed (Authenticated) Encryption – Formal definition and simple solution – Considerably simplifies/generalizes prior work

Defining Signcryption Ideal Functionality: Love from Alice ? Implementation: • Each player P publishes key pair (Sec. P, Pub. P) • To send m from sender S to receiver R – u = Sig. Enc(m; Sec. S, Pub. R); m = Ver. Dec(u; Pub. S, Sec. R)

Example: Et. S Love from Alice ? Alice But what if intervenes?

Example: Et. S (cont) ? Alice Love from Ugly Moral Need to use identities from Alice? ? ? in multi-user setting! Both for syntax and constructions

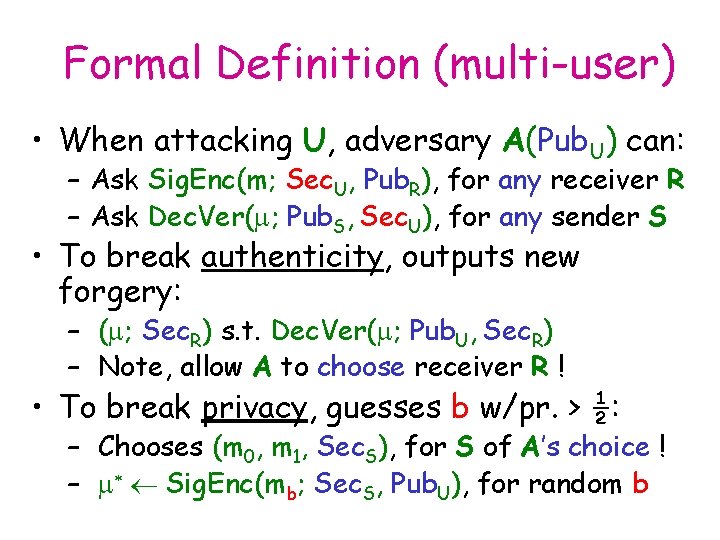
Formal Definition (multi-user) • When attacking U, adversary A(Pub. U) can: – Ask Sig. Enc(m; Sec. U, Pub. R), for any receiver R – Ask Dec. Ver(m; Pub. S, Sec. U), for any sender S • To break authenticity, outputs new forgery: – (m; Sec. R) s. t. Dec. Ver(m; Pub. U, Sec. R) – Note, allow A to choose receiver R ! • To break privacy, guesses b w/pr. > ½: – Chooses (m 0, m 1, Sec. S), for S of A’s choice ! – m* Sig. Enc(mb; Sec. S, Pub. U), for random b

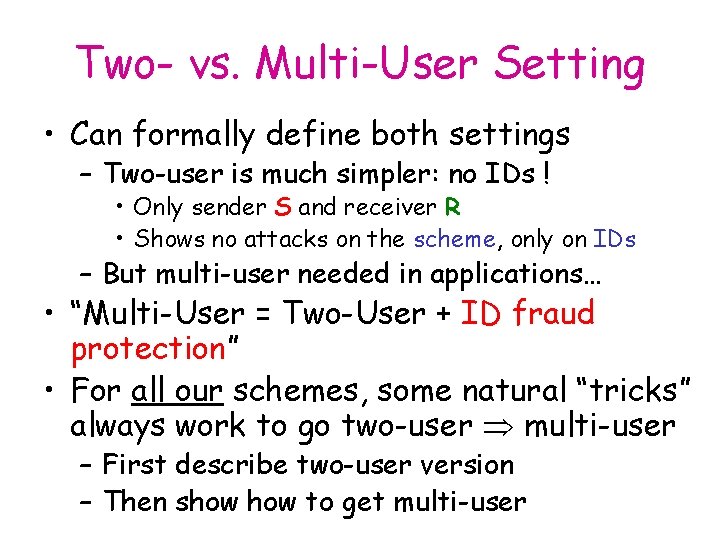
Two- vs. Multi-User Setting • Can formally define both settings – Two-user is much simpler: no IDs ! • Only sender S and receiver R • Shows no attacks on the scheme, only on IDs – But multi-user needed in applications… • “Multi-User = Two-User + ID fraud protection” • For all our schemes, some natural “tricks” always work to go two-user multi-user – First describe two-user version – Then show to get multi-user

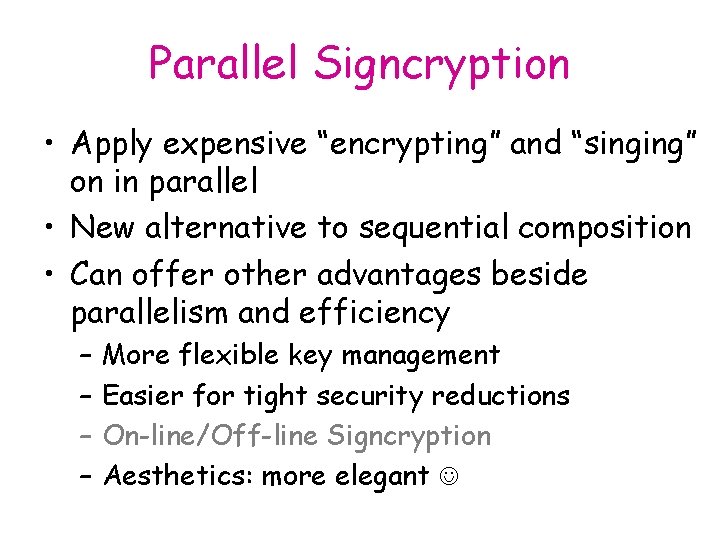
Parallel Signcryption • Apply expensive “encrypting” and “singing” on in parallel • New alternative to sequential composition • Can offer other advantages beside parallelism and efficiency – – More flexible key management Easier for tight security reductions On-line/Off-line Signcryption Aesthetics: more elegant

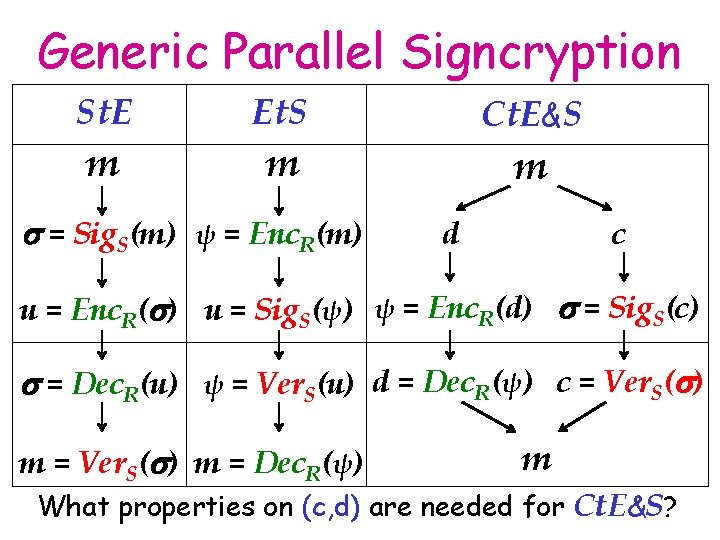
Generic Parallel Signcryption St. E m Et. S Ct. E&S m s = Sig. S(m) ψ = Enc. R(m) m d c u = Enc. R(s) u = Sig. S(ψ) ψ = Enc. R(d) s = Sig. S(c) s = Dec. R(u) ψ = Ver. S(u) d = Dec. R(ψ) c = Ver. S(s) m = Dec. R(ψ) m What properties on (c, d) are needed for Ct. E&S?

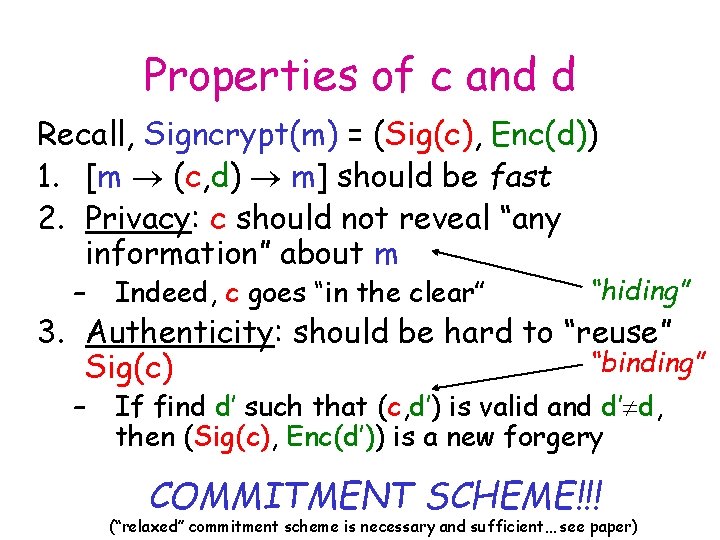
Properties of c and d Recall, Signcrypt(m) = (Sig(c), Enc(d)) 1. [m (c, d) m] should be fast 2. Privacy: c should not reveal “any information” about m “hiding” – Indeed, c goes “in the clear” – If find d’ such that (c, d’) is valid and d’ d, then (Sig(c), Enc(d’)) is a new forgery 3. Authenticity: should be hard to “reuse” “binding” Sig(c) COMMITMENT SCHEME!!! (“relaxed” commitment scheme is necessary and sufficient… see paper)

Improving Generic Approach • Need IND-CCA Enc and s. UF-CMA Sig – Expensive • What if implement in RO model? – Say, PSS for Sig, OAEP/OAEP+ for Enc… • Wasteful, need to “pad” twice ! – – – Poor exact security Poor message bandwidth Less efficient Need to store two independent keys Aesthetics: inelegant • Can we do (much) better? YES!

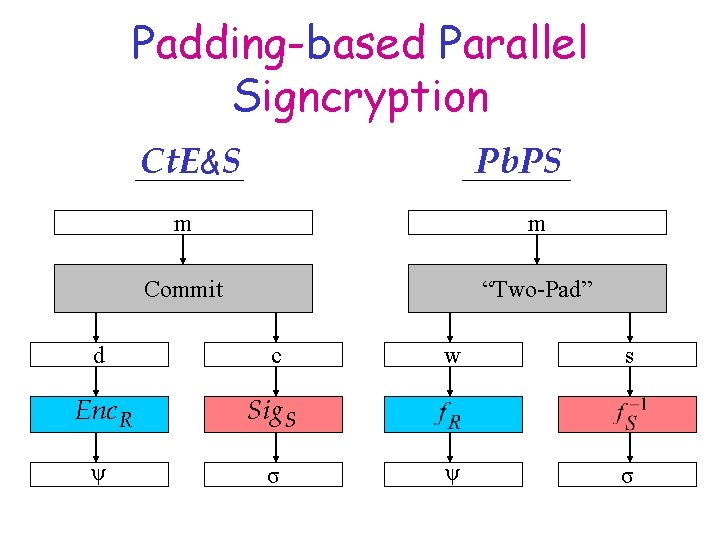
Padding-based Parallel Signcryption Ct. E&S Pb. PS m m Commit “Two-Pad” d c Enc. R Sig. S ψ σ w s ψ σ

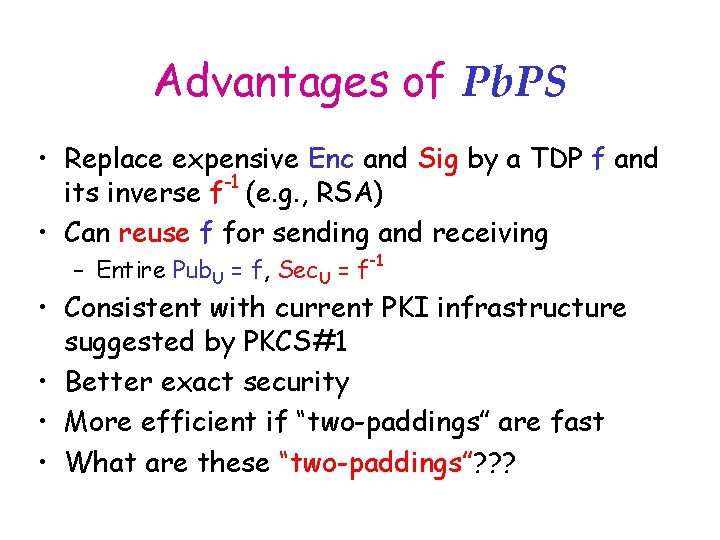
Advantages of Pb. PS • Replace expensive Enc and Sig by a TDP f and -1 its inverse f (e. g. , RSA) • Can reuse f for sending and receiving – Entire Pub. U = f, Sec. U = f-1 • Consistent with current PKI infrastructure suggested by PKCS#1 • Better exact security • More efficient if “two-paddings” are fast • What are these “two-paddings”? ? ?

Universal Two-Paddings • Invertible Pad(m) (w, s) s. t. for any TDP f – [f(w), s] is IND-CCA-secure encryption – [w, f– 1(s)] is s. UF-CMA-secure signature – In fact, holds even if reuse the same f for both signature and encryption • Lemma: if Pad is universal two-padding, – 1 then [f. R(w), f. S (s)] is a secure signcryption in the two-user setting – Later extend to multi-user setting

Two-Padding Results • Note: must use Random Oracle Model as use TDPs • Give a wide variety of universal two-paddings: – Old: PSS-R, OAEP+, SAP (“scramble all padding”) – New: many, most notably PSEP (mix of PSS-R & OAEP) • All are special cases of one general construction! – In particular, found generalization of most padding schemes commonly used for plain signature/encryption

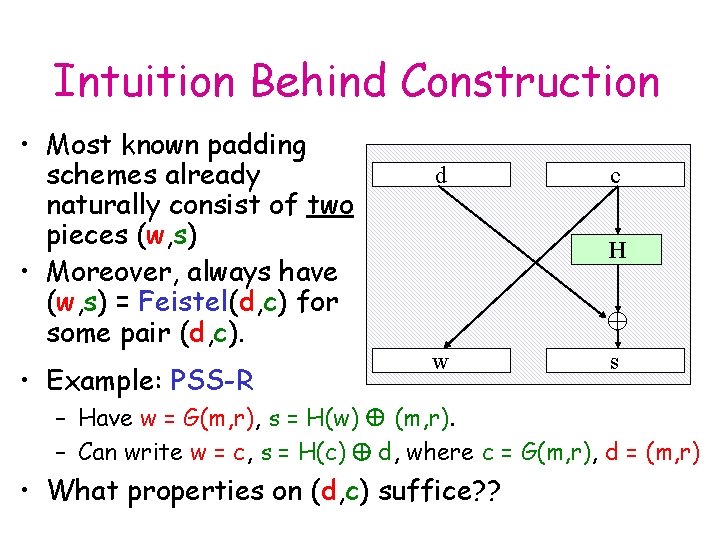
Intuition Behind Construction • Most known padding schemes already naturally consist of two pieces (w, s) • Moreover, always have (w, s) = Feistel(d, c) for some pair (d, c). • Example: PSS-R d c H w s – Have w = G(m, r), s = H(w) (m, r). – Can write w = c, s = H(c) d, where c = G(m, r), d = (m, r) • What properties on (d, c) suffice? ?

Extractable Commitment Given by two properties: 1. (Strong) Hiding: c(m) looks random, for any m - usually holds anyway for any natural commitment 2. Extractability: using some “trapdoor” T, can find d from c. - • There is Extract(c, T) d procedure s. t. for any A: Pr[ (c, d) valid & Extract(c, T) d | (c, d) A ] = negl. In the RO model, trapdoor T = RO queries made by A Note: extractability implies strong binding – Hard to find (c, d, d’) s. t. (c, d), (c, d’) are valid and d d’

Feistel Two-Paddings • Theorem: If Commit(m) (c, d) is an extractable commitment then Pad(m) = (w = c, s = H(c) d) is a universal two-padding scheme • Note: we will see that all natural commitments in the RO model are anyway extractable • Thus, essentially show that applying one round of Feistel to a pair (c, d) good for Ct. E&S, get a twopadding (w, s) good Pb. PS ! – Feistel allows to replace expensive Enc and Sig by a TDP f and its inverse f-1 (e. g. , RSA)

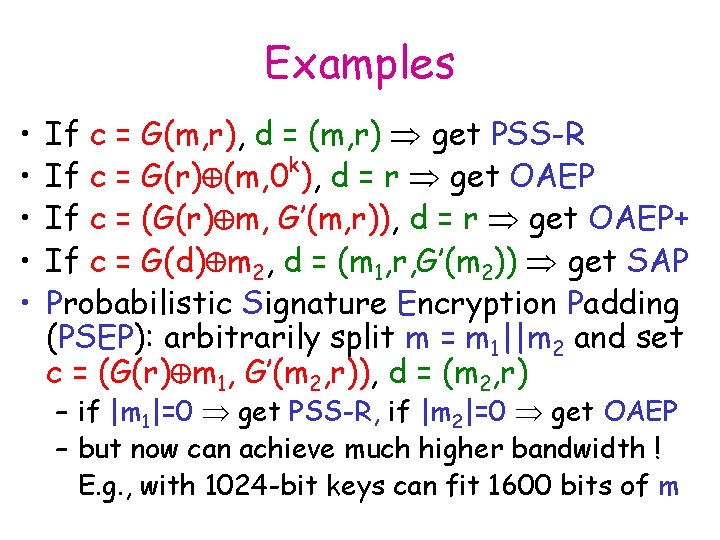
Examples • • • If c = G(m, r), d = (m, r) get PSS-R If c = G(r) (m, 0 k), d = r get OAEP If c = (G(r) m, G’(m, r)), d = r get OAEP+ If c = G(d) m 2, d = (m 1, r, G’(m 2)) get SAP Probabilistic Signature Encryption Padding (PSEP): arbitrarily split m = m 1||m 2 and set c = (G(r) m 1, G’(m 2, r)), d = (m 2, r) – if |m 1|=0 get PSS-R, if |m 2|=0 get OAEP – but now can achieve much higher bandwidth ! E. g. , with 1024 -bit keys can fit 1600 bits of m

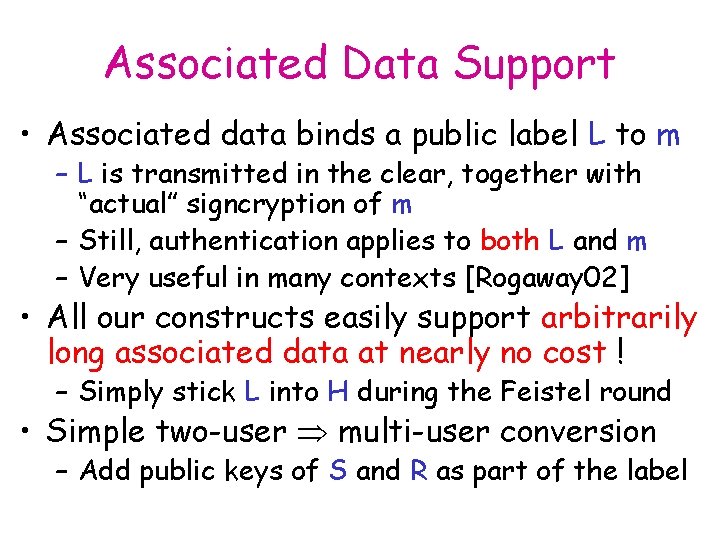
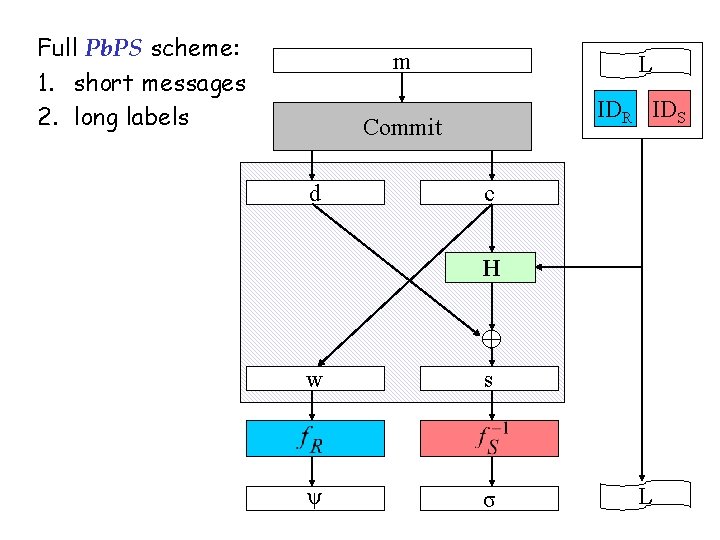
Associated Data Support • Associated data binds a public label L to m – L is transmitted in the clear, together with “actual” signcryption of m – Still, authentication applies to both L and m – Very useful in many contexts [Rogaway 02] • All our constructs easily support arbitrarily long associated data at nearly no cost ! – Simply stick L into H during the Feistel round • Simple two-user multi-user conversion – Add public keys of S and R as part of the label

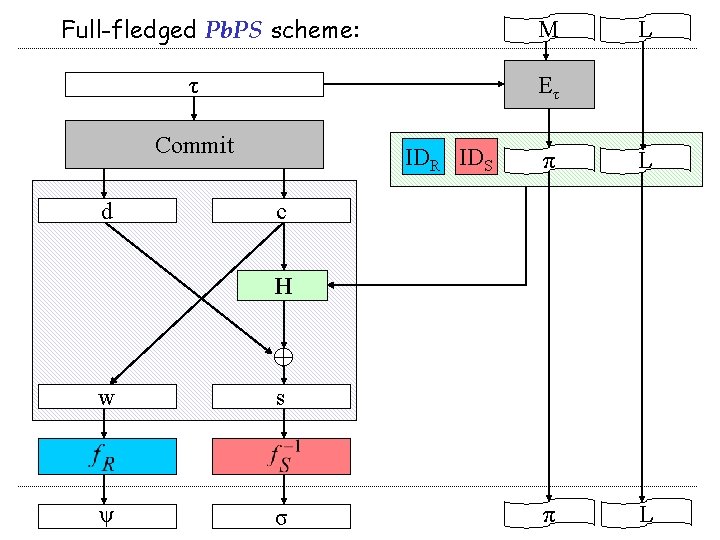
Full Pb. PS scheme: 1. short messages 2. long labels m L IDR IDS Commit d c H w s ψ σ L

Signcrypting Long Messages • Main Question: given good signcryption SC on short messages m, how to signcryption arbitrarily long messages M? • Approach: transform M (b, h) and set SC*(M) = (SC(b), h) – (note: want to have |b| << |M| ) • Sub-Question: what transformations T are needed to make SC* secure? • Answer: concealments !

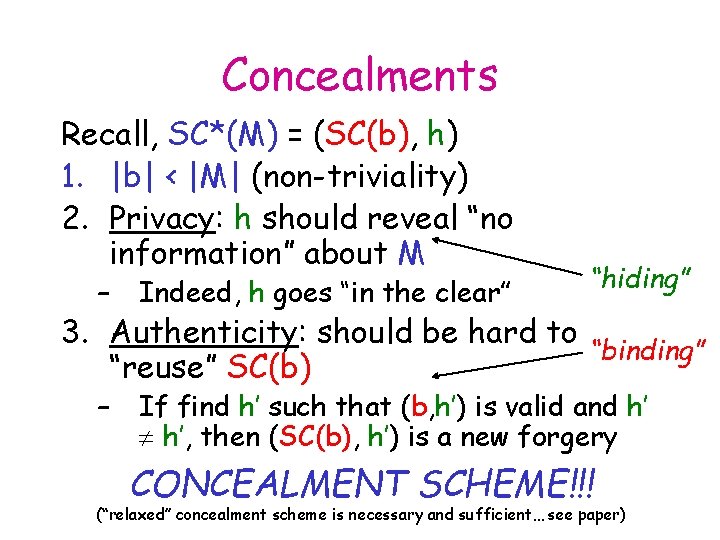
Concealments Recall, SC*(M) = (SC(b), h) 1. |b| < |M| (non-triviality) 2. Privacy: h should reveal “no information” about M “hiding” – Indeed, h goes “in the clear” – If find h’ such that (b, h’) is valid and h’ h’, then (SC(b), h’) is a new forgery 3. Authenticity: should be hard to “binding” “reuse” SC(b) COMMITMENT SCHEME!!! CONCEALMENT (“relaxed” concealment scheme is necessary and sufficient… see paper)

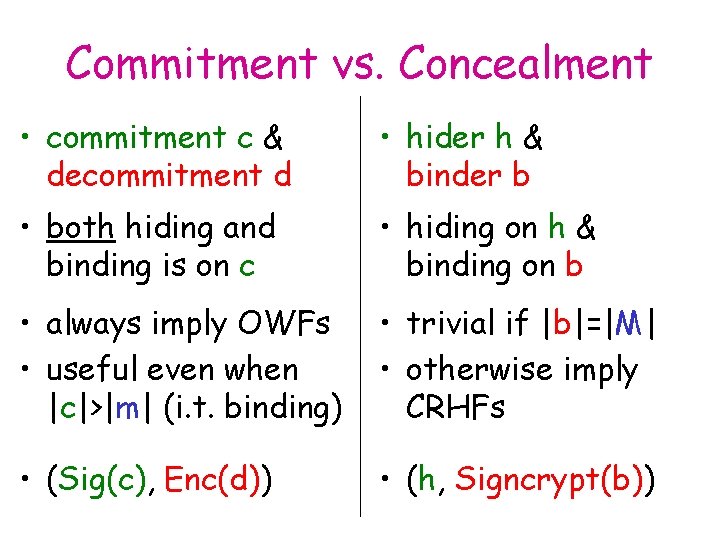
Commitment vs. Concealment • commitment c & decommitment d • hider h & binder b • both hiding and binding is on c • hiding on h & binding on b • always imply OWFs • useful even when |c|>|m| (i. t. binding) • trivial if |b|=|M| • otherwise imply CRHFs • (Sig(c), Enc(d)) • (h, Signcrypt(b))

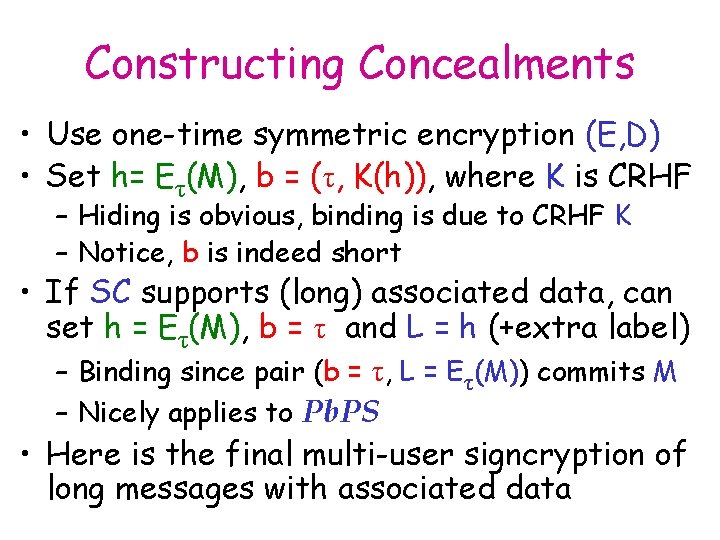
Constructing Concealments • Use one-time symmetric encryption (E, D) • Set h= Eτ(M), b = (τ, K(h)), where K is CRHF – Hiding is obvious, binding is due to CRHF K – Notice, b is indeed short • If SC supports (long) associated data, can set h = Eτ(M), b = τ and L = h (+extra label) – Binding since pair (b = τ, L = Eτ(M)) commits M – Nicely applies to Pb. PS • Here is the final multi-user signcryption of long messages with associated data

Full-fledged Pb. PS scheme: M τ Eτ Commit d L IDR IDS π L c H w s ψ σ

Conclusions • Formally defined signcryption – importance of IDs, multi-user security, … • Parallel Signcryption & its advantages – generic Ct. S&E paradigm – big improvement: Pb. PS • Two-padding schemes – general Feistel construction from commitments – get many old padding (PSS-R, OAEP, …) + new (PSEP) • Concealment Primitive: define, construct + apps • Full-fledged signcryption of long messages – flexibility, efficiency, simplicity, generality, security – consistent with existent standards/PKI

Thank you ? end Alice





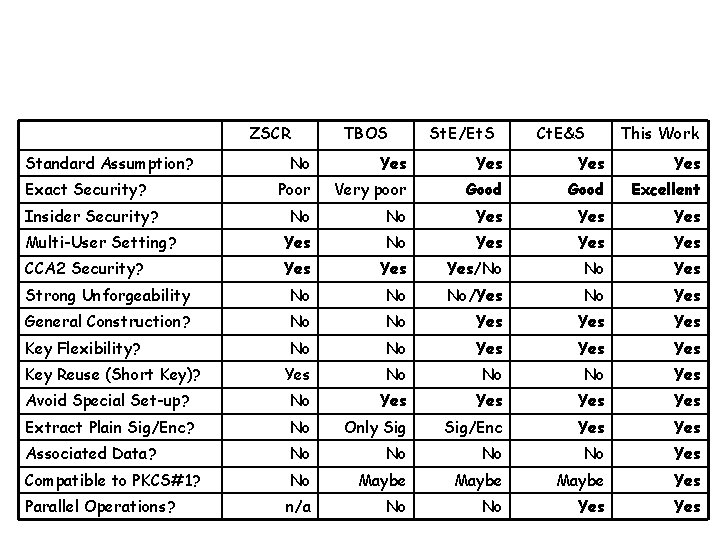
ZSCR Standard Assumption? TBOS St. E/Et. S Ct. E&S This Work No Yes Yes Poor Very poor Good Excellent No No Yes Yes Multi-User Setting? Yes No Yes Yes CCA 2 Security? Yes Yes/No No Yes Strong Unforgeability No No No/Yes No Yes General Construction? No No Yes Yes Key Flexibility? No No Yes Yes No No No Yes Avoid Special Set-up? No Yes Yes Extract Plain Sig/Enc? No Only Sig/Enc Yes Associated Data? No No Yes Compatible to PKCS#1? No Maybe Yes Parallel Operations? n/a No No Yes Exact Security? Insider Security? Key Reuse (Short Key)?

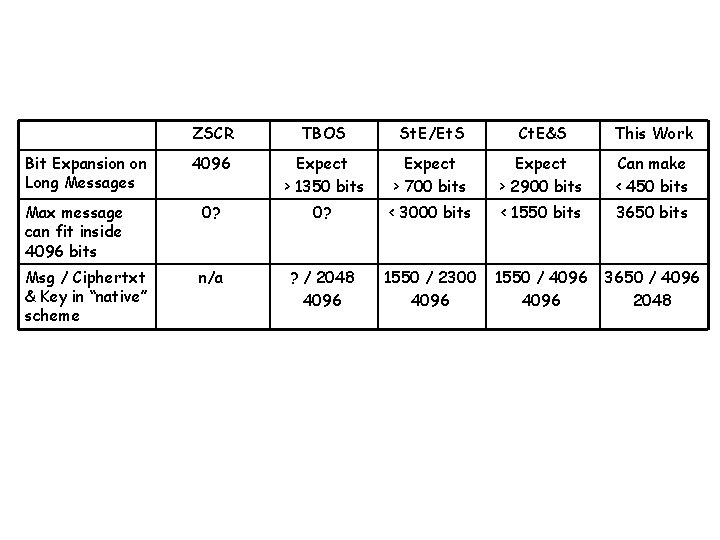
ZSCR TBOS St. E/Et. S Ct. E&S This Work 4096 Expect > 1350 bits Expect > 700 bits Expect > 2900 bits Can make < 450 bits Max message can fit inside 4096 bits 0? < 3000 bits < 1550 bits 3650 bits Msg / Ciphertxt & Key in “native” scheme n/a ? / 2048 4096 1550 / 2300 4096 1550 / 4096 3650 / 4096 2048 Bit Expansion on Long Messages