Security Related Research Projects at UCCS Network Research











- Slides: 31

Security Related Research Projects at UCCS Network Research Lab C. Edward Chow Department of Computer Science University of Colorado at Colorado Springs Security Research 2/7/2003 1 chow

Outline of the Talk n Brief Introduction to the Network/Protocol Research Lab at UCCS n Network security related research projects at UCCS Network/Protocol Research Lab n l Autonomous Anti-DDo. S Project l Secure Collective Defense Project l BGP/MPLS based VPN Project Discussion on Innerwall-UCCS Joint Research Project l STTR N 03 -T 010 TITLE: Intrusion Monitoring, Detection and Reporting Security Research 2/7/2003 2 chow

UCCS Network Research Lab n n Director: Dr. C. Edward Chow Graduate students: – John Bicknell/Steve Mc. Caughey/Anders Hansmat: Distributed Network Restoration/Network Survivability – Hekki Julkunen: Dynamic Packet Filter – Chandra Prakash: High Available Linux kernel-based Content Switch – Ganesh Godavari: Linux based Secure Web Switch – Angela Cearns: Autonomous Anti-DDo. S (A 2 D 2) Testbed – Longhua Li: IXP-based Content Switch – Yu Cai (Ph. D. research assistant): Multipath Routing – Jianhua Xie (Ph. D. ): Secure Storage Networks – Frank Watson: Content Switch for Email Security – Paul Fong: Wireless AODV Routing for sensor networks – Nirmala Belusu: Wireless Network Security PEAP vs. TTLS – David Wikinson/Sonali Patankar: Secure Collective Defense – Murthy Andukuri/Jing Wu: Enhanced BGP/MPLS-based VPN – Patricia Ferrao/Merlin Vincnet: Web-based Collaborative System Support Security Research 2/7/2003 3 chow

UCCS Network Lab Setup Gigabit fiber connection to UCCS backbone Switch/Firewall/Wireless AP: l HP 4000 switch; 4 Linksys/Dlink Switches. l Sonicwall Pro 300 Firewall l 8 Intel 7112 SSL accelerators; 4 7820 XML directors donated by Intel. l Cisco 1200 Aironet Dual Band Access Point and 350 client PC/PCI cards (both 802. 11 a and 802. 11 b cards). l Intel IXP 12 EB network processor evaluation board n Servers: Two Dell Power. Edge Servers. n Workstations/PCs: l 8 Dell PCs (3 Ghz-500 Mhz); 12 HP PCs (500 -233 Mhz) l 2 laptop PCs with Aironet 350 for mobile wireless l OS: Linux Redhat 8. 0; Window XP/2000 n n Security Research 2/7/2003 4 chow

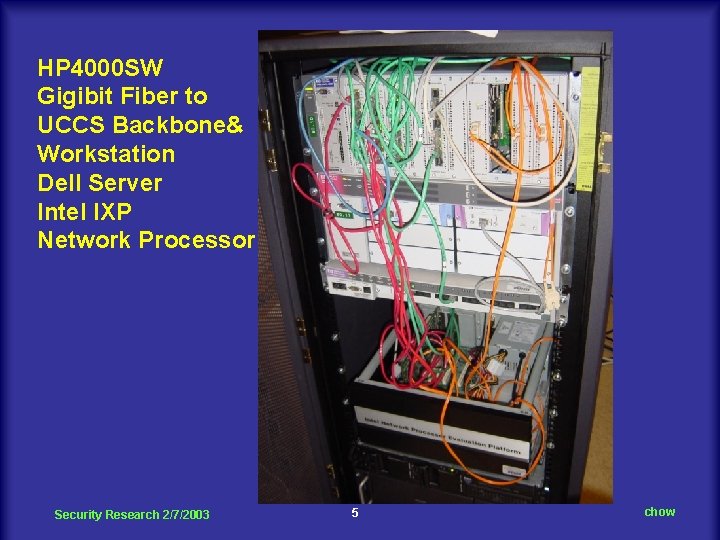
HP 4000 SW Gigibit Fiber to UCCS Backbone& Workstation Dell Server Intel IXP Network Processor Security Research 2/7/2003 5 chow

Intel 7110 SSL Accelerators n 7280 XML Director n Security Research 2/7/2003 6 chow

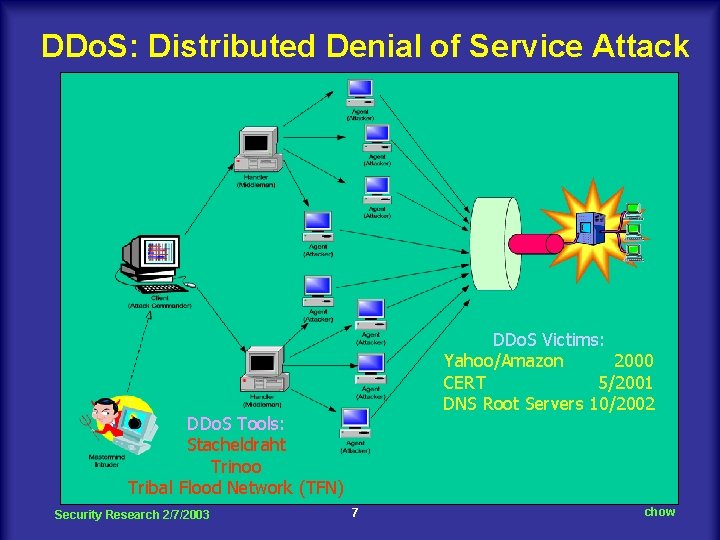
DDo. S: Distributed Denial of Service Attack DDo. S Victims: Yahoo/Amazon 2000 CERT 5/2001 DNS Root Servers 10/2002 DDo. S Tools: Stacheldraht Trinoo Tribal Flood Network (TFN) Security Research 2/7/2003 7 chow

How wide spread is DDo. S? n Research by Moore et al of University of California at San Diego, 2001. l 12, 805 Do. S in 3 -week period l Most of them are Home, small to medium sized organizations Security Research 2/7/2003 8 chow

Intrusion Related Research Areas Intrusion Prevention l General Security Policy l Ingress/Egress Filtering n Intrusion Detection l Anomaly Detection l Misuse Detection n Intrusion Response l Identification/Traceback/Pushback l Intrusion Tolerance n Security Research 2/7/2003 9 chow

Security Related Research Projects n Secure Content Switch n Autonomous Anti-DDo. S Project l Deal with Intrusion Detection and Handling; l Techniques: – IDS-Firewall Integration – Adaptive Firewall Rules – Easy to use/manage. n Secure Collective Defense Project l Deal with Intrusion Tolerance; How to tolerate the attack l Techniques (main idea Explore secure alternate paths for clients to come in) – Multiple Path Routing – Secure DNS extension: how to inform client DNS servers to add alternate new entries – Utilize a consortium of Proxy servers with IDS that hides the IP address of alternate gateways. n BGP/MPLS based VPN Project n Content Switch for Email Security Research 2/7/2003 10 chow

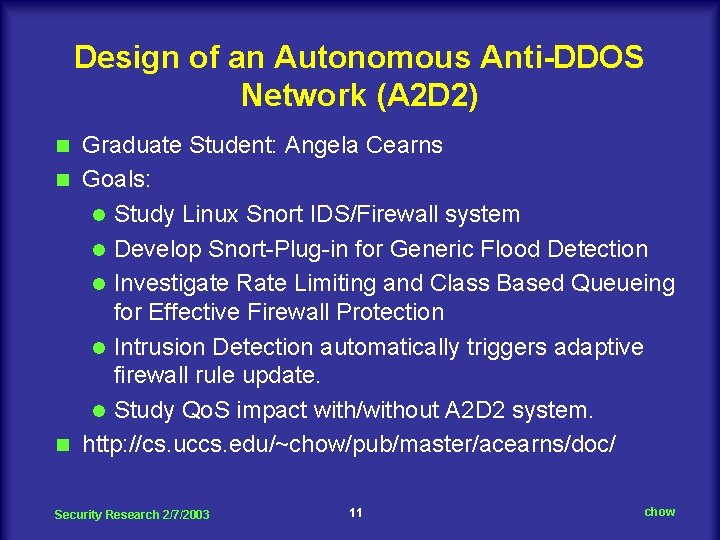
Design of an Autonomous Anti-DDOS Network (A 2 D 2) Graduate Student: Angela Cearns n Goals: l Study Linux Snort IDS/Firewall system l Develop Snort-Plug-in for Generic Flood Detection l Investigate Rate Limiting and Class Based Queueing for Effective Firewall Protection l Intrusion Detection automatically triggers adaptive firewall rule update. l Study Qo. S impact with/without A 2 D 2 system. n http: //cs. uccs. edu/~chow/pub/master/acearns/doc/ n Security Research 2/7/2003 11 chow

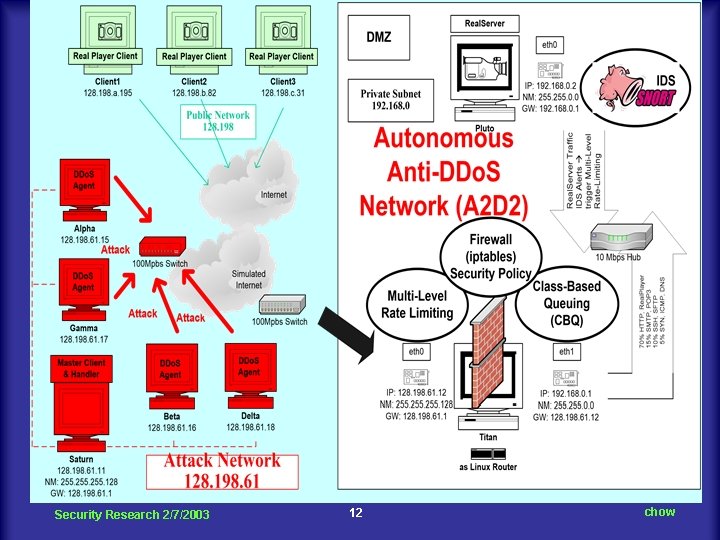
Security Research 2/7/2003 12 chow

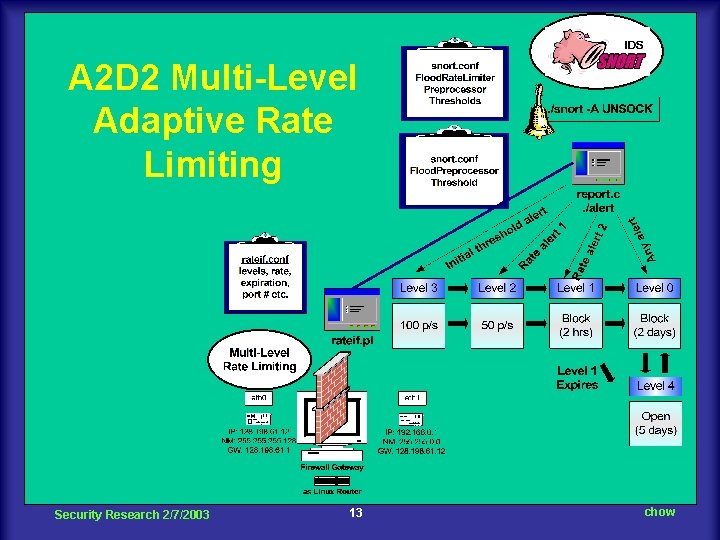
A 2 D 2 Multi-Level Adaptive Rate Limiting Security Research 2/7/2003 13 chow

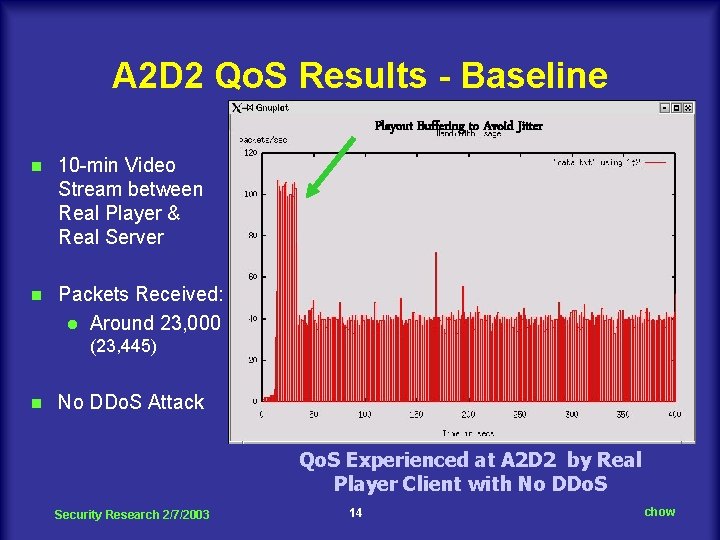
A 2 D 2 Qo. S Results - Baseline Playout Buffering to Avoid Jitter n 10 -min Video Stream between Real Player & Real Server n Packets Received: l Around 23, 000 (23, 445) n No DDo. S Attack Qo. S Experienced at A 2 D 2 by Real Player Client with No DDo. S Security Research 2/7/2003 14 chow

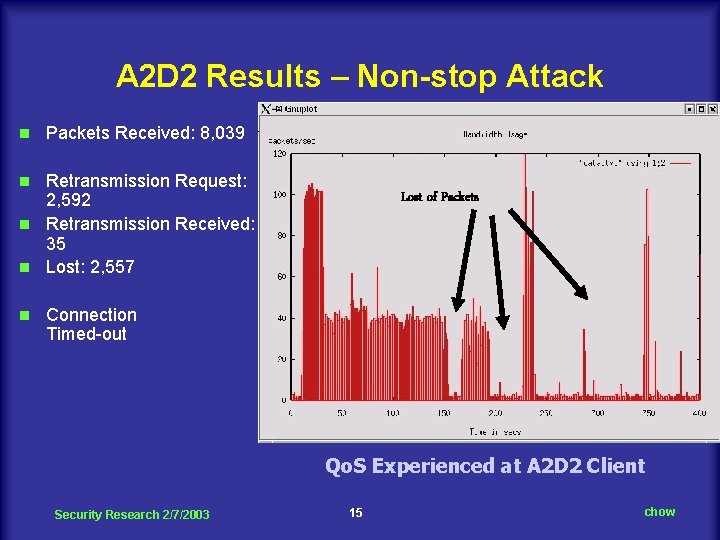
A 2 D 2 Results – Non-stop Attack n Packets Received: 8, 039 Retransmission Request: 2, 592 n Retransmission Received: 35 n Lost: 2, 557 n n Lost of Packets Connection Timed-out Qo. S Experienced at A 2 D 2 Client Security Research 2/7/2003 15 chow

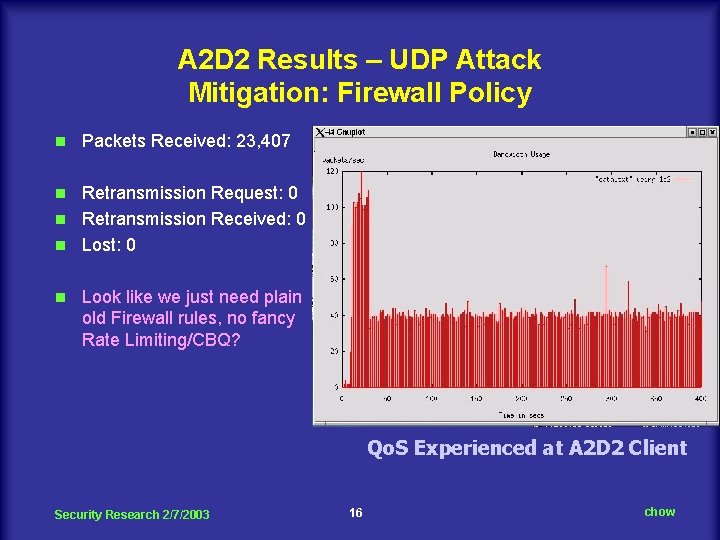
A 2 D 2 Results – UDP Attack Mitigation: Firewall Policy n Packets Received: 23, 407 Retransmission Request: 0 n Retransmission Received: 0 n Lost: 0 n n Look like we just need plain old Firewall rules, no fancy Rate Limiting/CBQ? Qo. S Experienced at A 2 D 2 Client Security Research 2/7/2003 16 chow

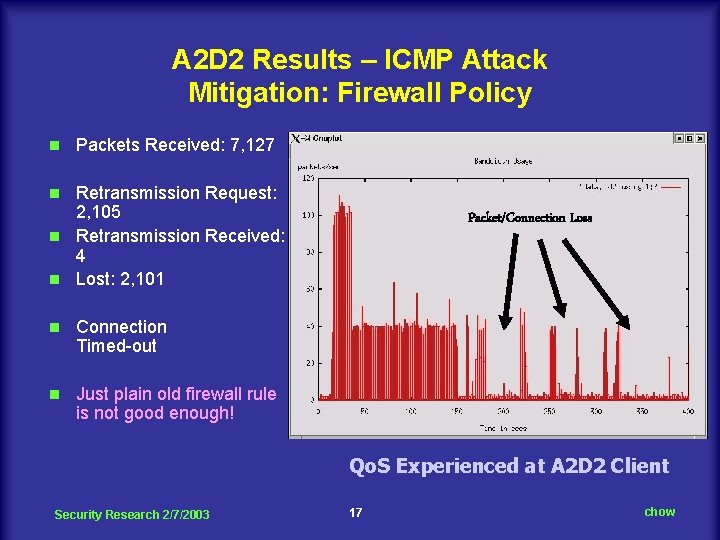
A 2 D 2 Results – ICMP Attack Mitigation: Firewall Policy n Packets Received: 7, 127 Retransmission Request: 2, 105 n Retransmission Received: 4 n Lost: 2, 101 n n Connection Timed-out n Just plain old firewall rule is not good enough! Packet/Connection Loss Qo. S Experienced at A 2 D 2 Client Security Research 2/7/2003 17 chow

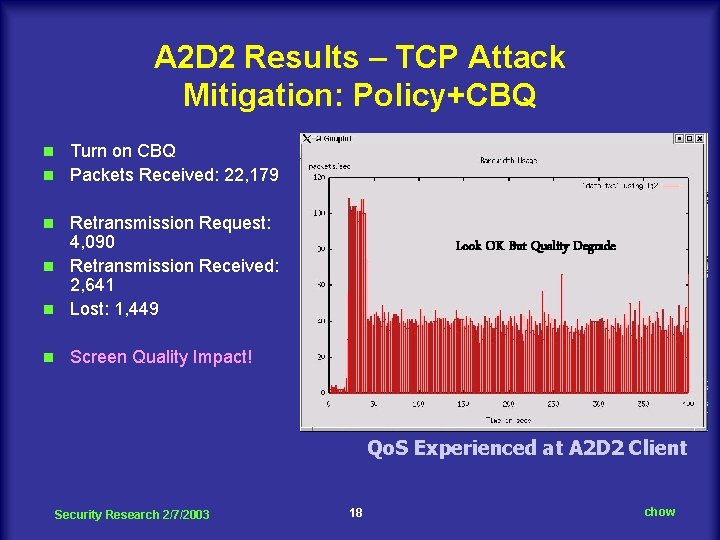
A 2 D 2 Results – TCP Attack Mitigation: Policy+CBQ Turn on CBQ n Packets Received: 22, 179 n Retransmission Request: 4, 090 n Retransmission Received: 2, 641 n Lost: 1, 449 n n Look OK But Quality Degrade Screen Quality Impact! Qo. S Experienced at A 2 D 2 Client Security Research 2/7/2003 18 chow

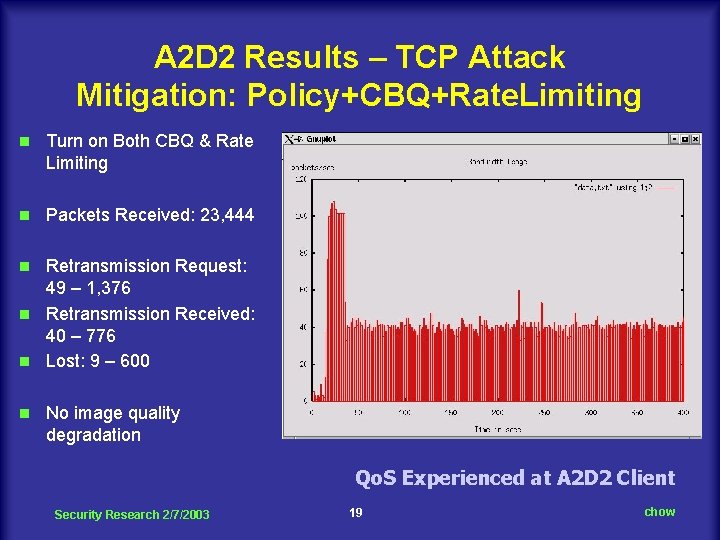
A 2 D 2 Results – TCP Attack Mitigation: Policy+CBQ+Rate. Limiting n Turn on Both CBQ & Rate Limiting n Packets Received: 23, 444 Retransmission Request: 49 – 1, 376 n Retransmission Received: 40 – 776 n Lost: 9 – 600 n n No image quality degradation Qo. S Experienced at A 2 D 2 Client Security Research 2/7/2003 19 chow

A 2 D 2 Future Works n n n Extend to include IDIP/Pushback Precise Anomaly Detection Improve Firewall/IDS Processing Speed Scalability Issues l Tests with More Services Types l Tests with Heavy Client Traffic Volume Fault Tolerant (Multiple Firewall Devices) Alternate Routing Security Research 2/7/2003 20 chow

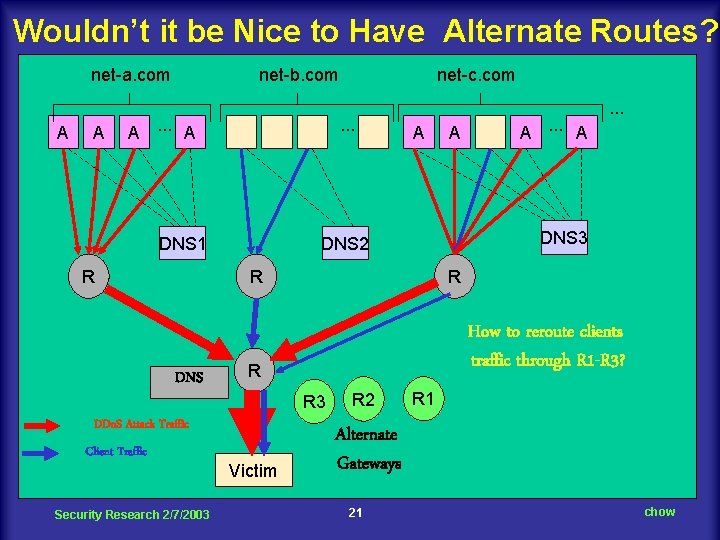
Wouldn’t it be Nice to Have Alternate Routes? net-a. com A A net-b. com A. . . A . . . DNS 1 R net-c. com A Client Traffic Security Research 2/7/2003 R How to reroute clients traffic through R 1 -R 3? R R 3 DDo. S Attack Traffic Victim A. . . A DNS 3 DNS 2 R DNS A . . . R 2 R 1 Alternate Gateways 21 chow

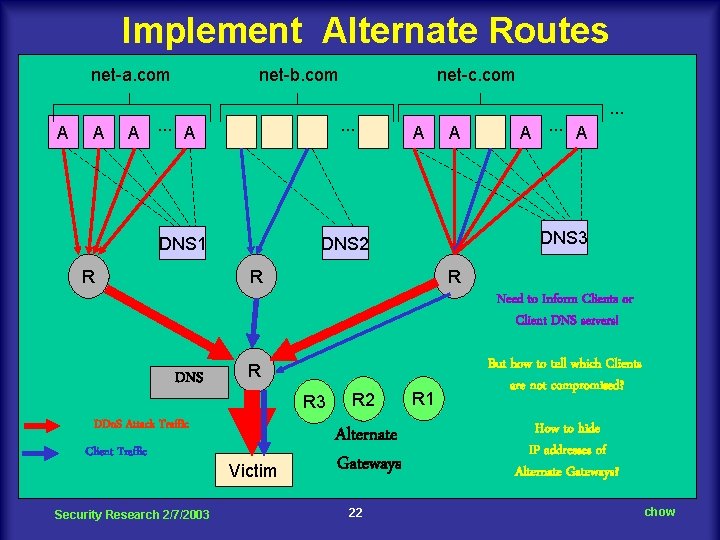
Implement Alternate Routes net-a. com A A net-b. com A. . . A . . . DNS 1 R net-c. com A A A. . . A . . . DNS 3 DNS 2 R R Need to Inform Clients or Client DNS servers! DNS R R 3 DDo. S Attack Traffic Client Traffic Security Research 2/7/2003 Victim R 2 Alternate Gateways 22 R 1 But how to tell which Clients are not compromised? How to hide IP addresses of Alternate Gateways? chow

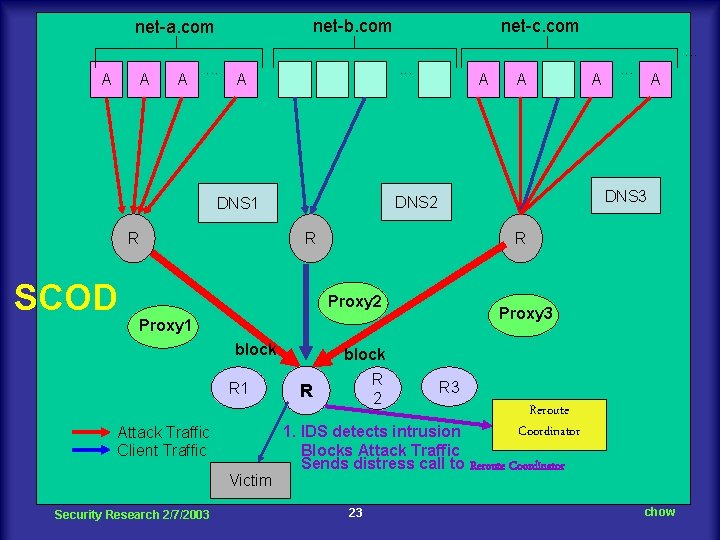
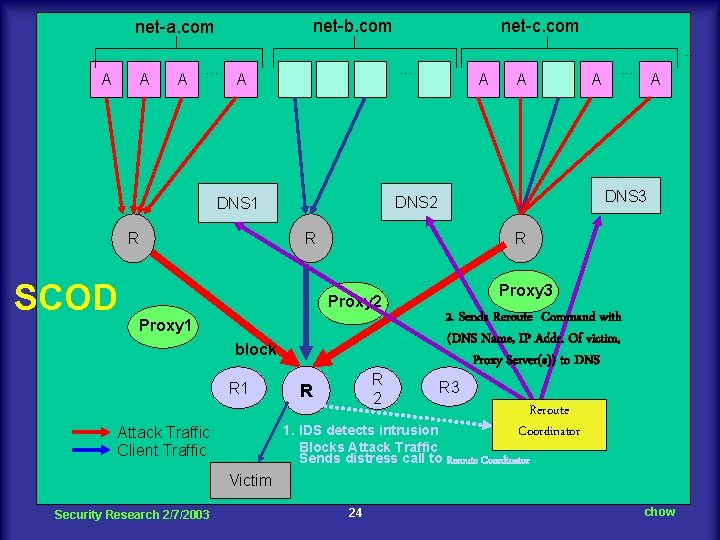
net-b. com net-a. com net-c. com. . . A A A . . . A SCOD Victim Security Research 2/7/2003 A Proxy 3 Proxy 1 Attack Traffic Client Traffic . . . R Proxy 2 block A DNS 3 R R 1 A DNS 2 DNS 1 R A block R 2 R R 3 Reroute Coordinator 1. IDS detects intrusion Blocks Attack Traffic Sends distress call to Reroute Coordinator 23 chow

net-b. com net-a. com net-c. com. . . A A A . . . A SCOD Proxy 1 block Victim Security Research 2/7/2003 . . . A R Proxy 2 Attack Traffic Client Traffic A DNS 3 R R 1 A DNS 2 DNS 1 R A R 2 R Proxy 3 2. Sends Reroute Command with (DNS Name, IP Addr. Of victim, Proxy Server(s)) to DNS R 3 Reroute Coordinator 1. IDS detects intrusion Blocks Attack Traffic Sends distress call to Reroute Coordinator 24 chow

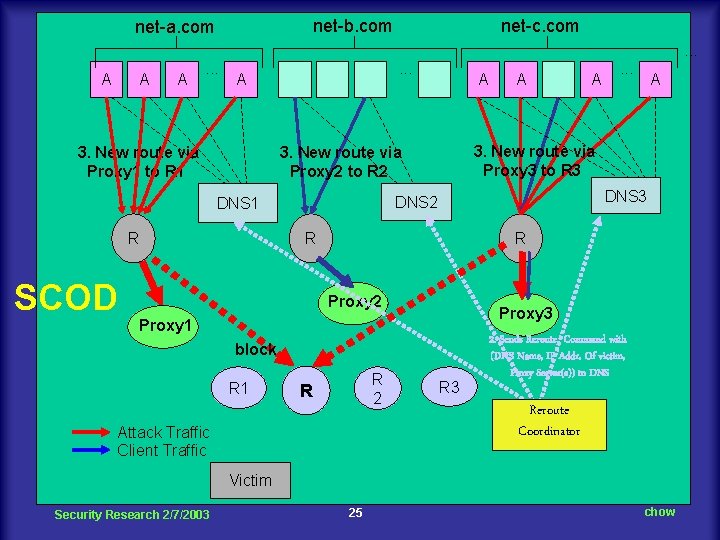
net-b. com net-a. com net-c. com. . . A A A . . . A 3. New route via Proxy 1 to R 1 R A . . . A DNS 3 DNS 2 R R Proxy 2 Proxy 3 Proxy 1 block R 1 A 3. New route via Proxy 3 to R 3 3. New route via Proxy 2 to R 2 DNS 1 SCOD A R 2 R Attack Traffic Client Traffic R 3 2. Sends Reroute Command with (DNS Name, IP Addr. Of victim, Proxy Server(s)) to DNS Reroute Coordinator Victim Security Research 2/7/2003 25 chow

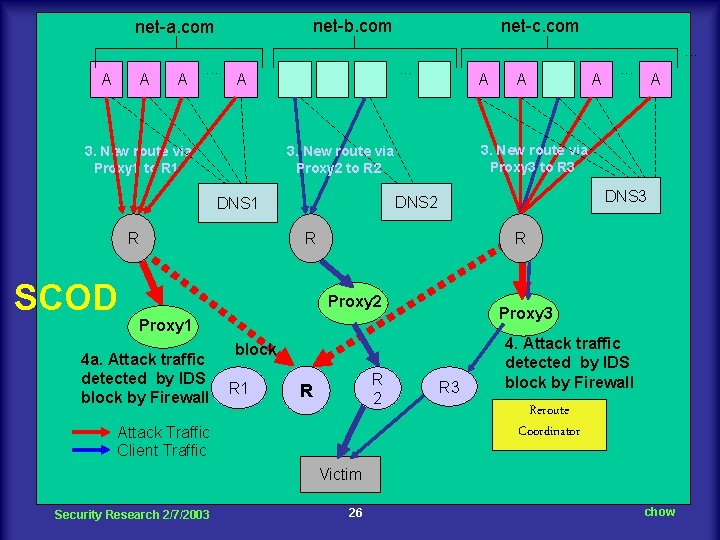
net-b. com net-a. com net-c. com. . . A A A . . . A 3. New route via Proxy 1 to R 1 R R . . . A R Proxy 3 Proxy 1 block R 1 A DNS 3 DNS 2 Proxy 2 4 a. Attack traffic detected by IDS block by Firewall A 3. New route via Proxy 3 to R 3 3. New route via Proxy 2 to R 2 DNS 1 SCOD A R 2 R Attack Traffic Client Traffic R 3 4. Attack traffic detected by IDS block by Firewall Reroute Coordinator Victim Security Research 2/7/2003 26 chow

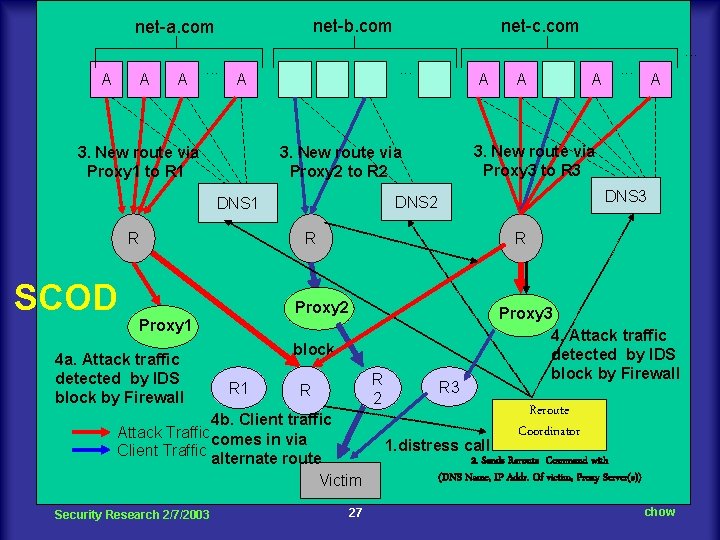
net-b. com net-a. com net-c. com. . . A A A . . . A 3. New route via Proxy 1 to R 1 R R block R 2 R 4 b. Client traffic Attack Traffic comes in via Client Traffic alternate route Victim Security Research 2/7/2003 . . . A R Proxy 1 R 1 A DNS 3 DNS 2 Proxy 2 4 a. Attack traffic detected by IDS block by Firewall A 3. New route via Proxy 3 to R 3 3. New route via Proxy 2 to R 2 DNS 1 SCOD A 27 R 3 1. distress call Proxy 3 4. Attack traffic detected by IDS block by Firewall Reroute Coordinator 2. Sends Reroute Command with (DNS Name, IP Addr. Of victim, Proxy Server(s)) chow

Secure Collective Defense n Main Idea Explore secure alternate paths for clients to come in; Utilize geographically separated proxy servers. n Goal: n l Provide secure alternate routes l Hide IP addresses of alternate gateways Techniques: l Multiple Path Routing l Secure DNS extension: how to inform client DNS servers to add alternate new entries (Not your normal DNS name/IP address mapping entry). l Utilize a consortium of Proxy servers with IDS that hides the IP address of alternate gateways. l How to partition clients to come at different proxy servers? may help identify the attacker! l How clients use the new DNS entries and route traffic through proxy server? Use Sock protocol, modify resolver library? Security Research 2/7/2003 28 chow

New UCCS IA Degree/Certificate Master of Engineering Degree in Information Assurance n Certificate in Information Assurance (offered to Peterson AFB through NISSC) l Computer Networks; Fundamental of Security; Cryptography; Advanced System Security Design n Security Research 2/7/2003 29 chow

New CS 691 Course on Advanced System Security Design n n n Use Matt Bishop new Computer Security Text Spring 2003: With one class at UCCS; one at Peterson AFB. Enhanced by Demo/Hand-on exercises at Distribute Security Lab of Northorp Grumman. Integrate security research results into course material such as A 2 D 2, Secure Collective Defense, MPLS-VPN projects. Invite speakers from Industry such as Innerwall and AFA? Looking for potential joint exercises with other institutions such as AFA, Northorp Grumman, Innerwall. Security Research 2/7/2003 30 chow

Joint Research/Development Effort n STTR N 03 -T 010 TITLE: Intrusion Monitoring, Detection and Reporting n Penetration Analysis/Testing projects? n Intrusion Detection/Handling projects? n Other Cyberwarfare related projects? n Security Forum organized by Dean Haefner/Dr. Ayen n Security Seminar Series with CITTI funding support l Look for Speakers (suggestion? ) Security Research 2/7/2003 31 chow