Secret sharing using Lagrange interpolation polynomial i TEM





- Slides: 14

Secret sharing using Lagrange interpolation polynomial i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

Secret sharing • Suppose that 1234 is the code to the safe of a bank. • For safety reason, the rule is that the safe cannot be open by a single person, but by two together. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

Secret sharing: first solution • As a first solution, we split the code into two parts 12 and 34 and give one part to clerk A and the second to clerk B. • Problem: each clerk has only two digits to guess for the secret code, making it easer for them to find the secret. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

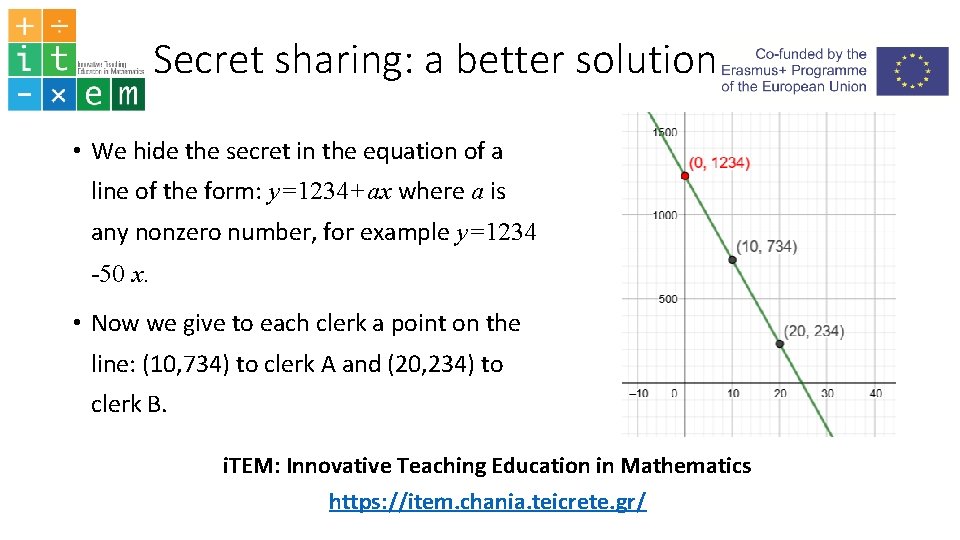
Secret sharing: a better solution • We hide the secret in the equation of a line of the form: y=1234+ax where a is any nonzero number, for example y=1234 -50 x. • Now we give to each clerk a point on the line: (10, 734) to clerk A and (20, 234) to clerk B. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

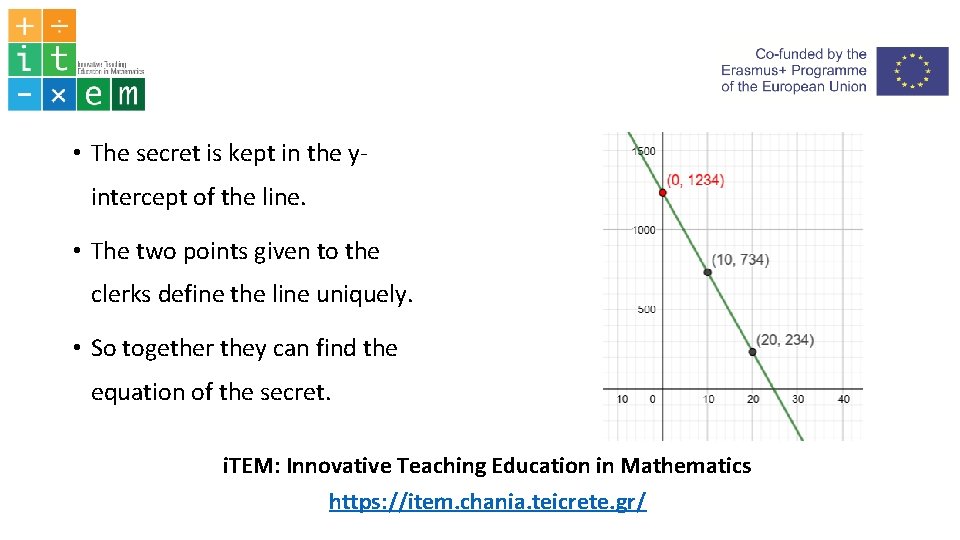
• The secret is kept in the y intercept of the line. • The two points given to the clerks define the line uniquely. • So together they can find the equation of the secret. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

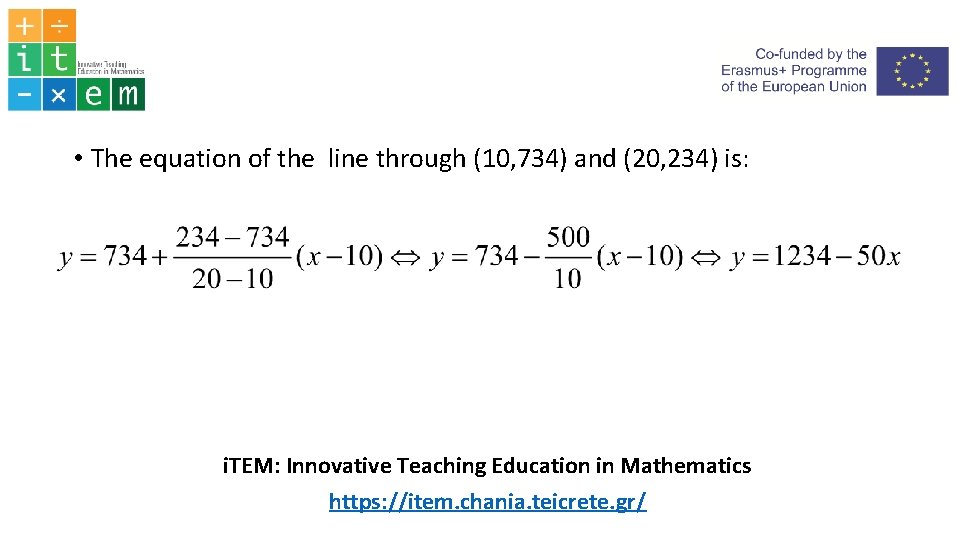
• The equation of the line through (10, 734) and (20, 234) is: i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

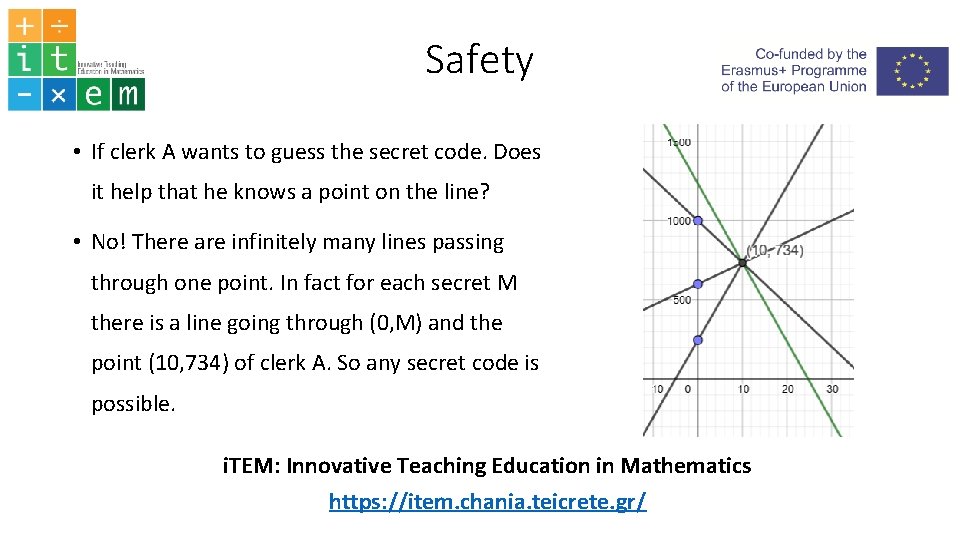
Safety • If clerk A wants to guess the secret code. Does it help that he knows a point on the line? • No! There are infinitely many lines passing through one point. In fact for each secret M there is a line going through (0, M) and the point (10, 734) of clerk A. So any secret code is possible. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

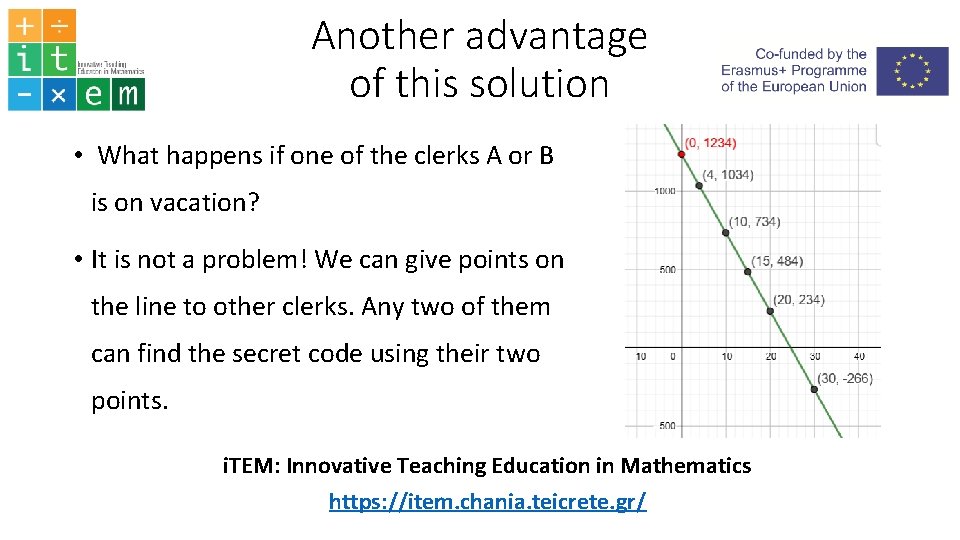
Another advantage of this solution • What happens if one of the clerks A or B is on vacation? • It is not a problem! We can give points on the line to other clerks. Any two of them can find the secret code using their two points. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

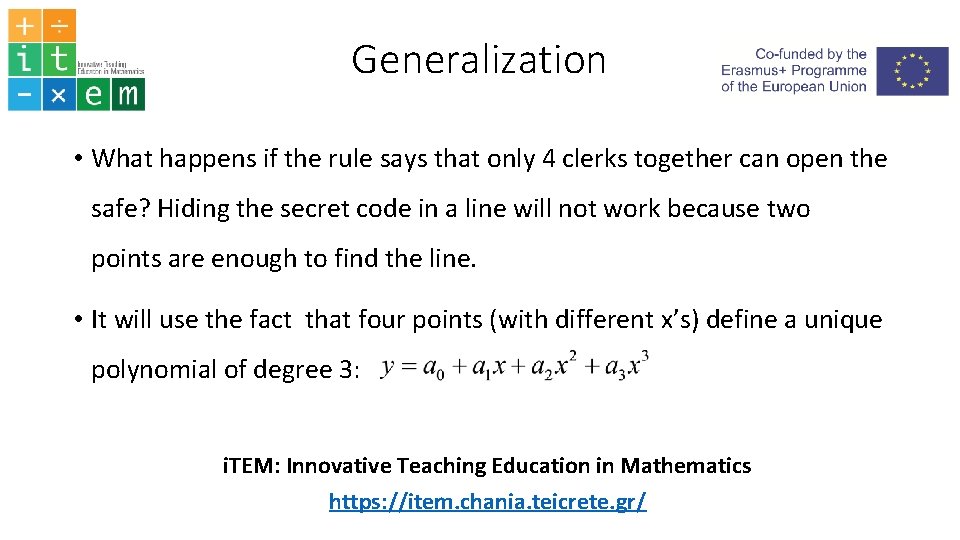
Generalization • What happens if the rule says that only 4 clerks together can open the safe? Hiding the secret code in a line will not work because two points are enough to find the line. • It will use the fact that four points (with different x’s) define a unique polynomial of degree 3: i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

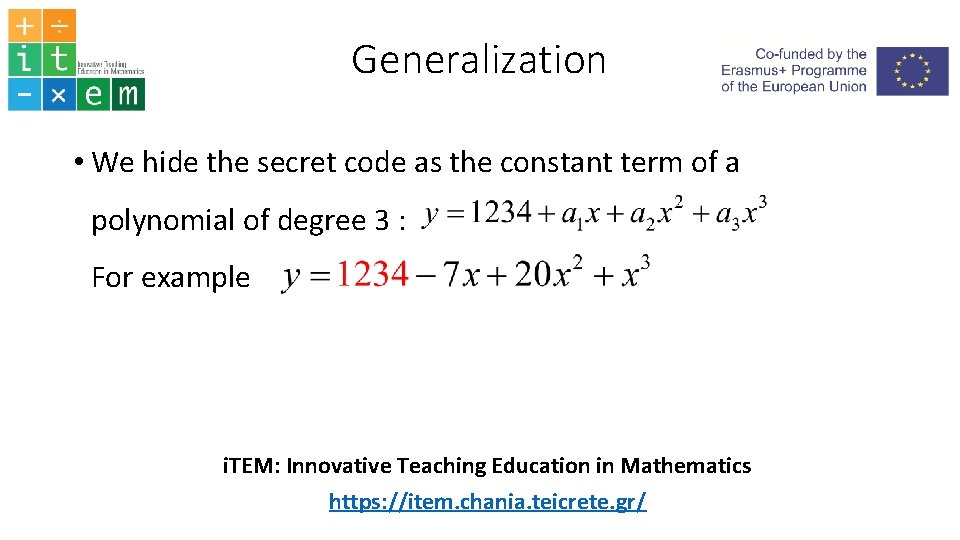
Generalization • We hide the secret code as the constant term of a polynomial of degree 3 : For example i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

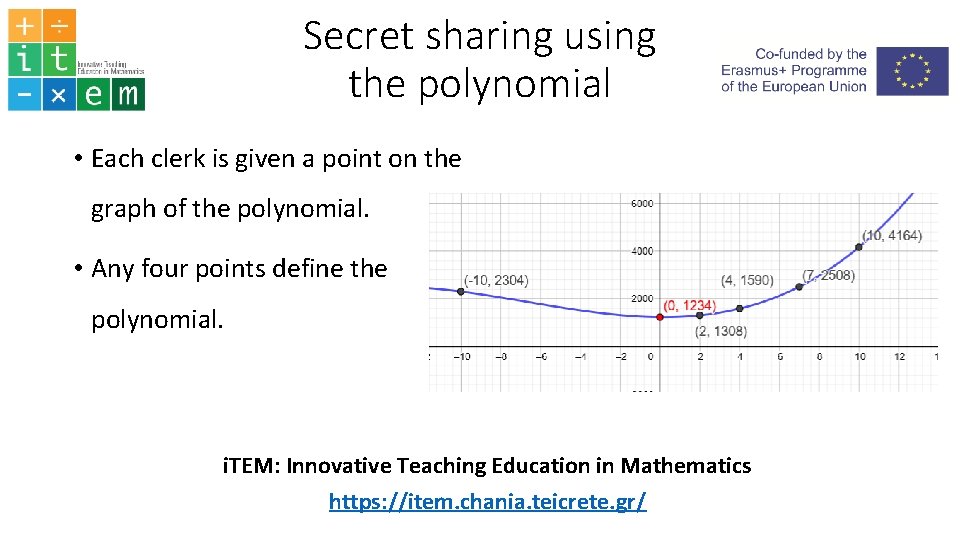
Secret sharing using the polynomial • Each clerk is given a point on the graph of the polynomial. • Any four points define the polynomial. i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

Find the secret • How is it possible to find the polynomial using 4 points? • Using the Lagrange’s interpolation formula which we will learn about in the course! i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

• This method for secret sharing is a well known cryptographic protocol due to Adi Shamir (Weizman Institute). In ryptography, the polynomial if defined with coefficient in where p is a prime number. • Shamir, Adi (1979), "How to share a secret", Communications of the ACM, 22 (11): 612– 613 i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/

"The European Commission support for the production of this publication does not constitute an endorsement of the contents which reflects the views only of the authors, and the Commission cannot be held responsi ble for any use which may be made of the information contained therein. " i. TEM: Innovative Teaching Education in Mathematics https: //item. chania. teicrete. gr/