Secret Image Sharing with Steganography and Authentication Authors








- Slides: 11

Secret Image Sharing with Steganography and Authentication Authors: Chang-Chou Lin, Wen-Hsiang Tsai Source: The Journal of System and Software, Volume: 73, Issue: 3, Nov. -Dec. , 2004, PP. 405 -414 Speaker: Nan-I Wu (吳男益) Date: 2004/12/017 1

Introduction • The proposed method based on a (k, n)-threshold scheme with the additional capabilities of steganography and authentication. • Steganography is different from visual cryptography schemes. • The fragile image watermarking is adopted for image authentication during the secret sharing process. • The proposed scheme as a whole offers a high secure and effective mechanism for secret image sharing that is not found in existing secret image sharing methods. 2



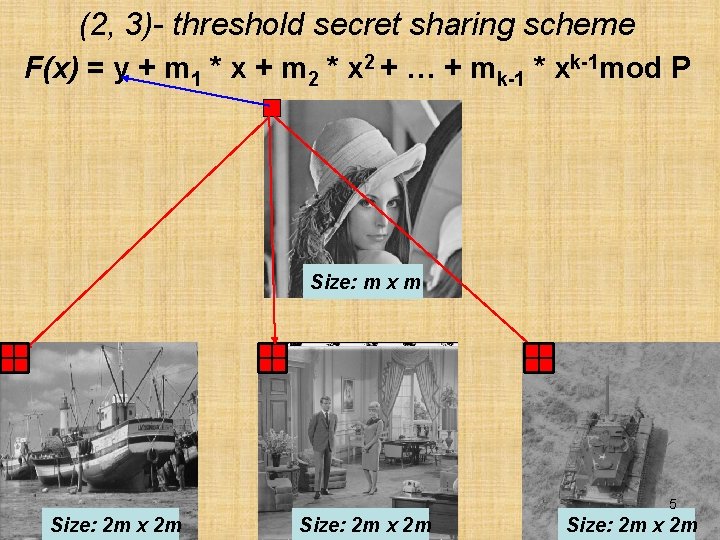
(2, 3)- threshold secret sharing scheme F(x) = y + m 1 * x + m 2 * x 2 + … + mk-1 * xk-1 mod P Size: m x m 5 Size: 2 m x 2 m


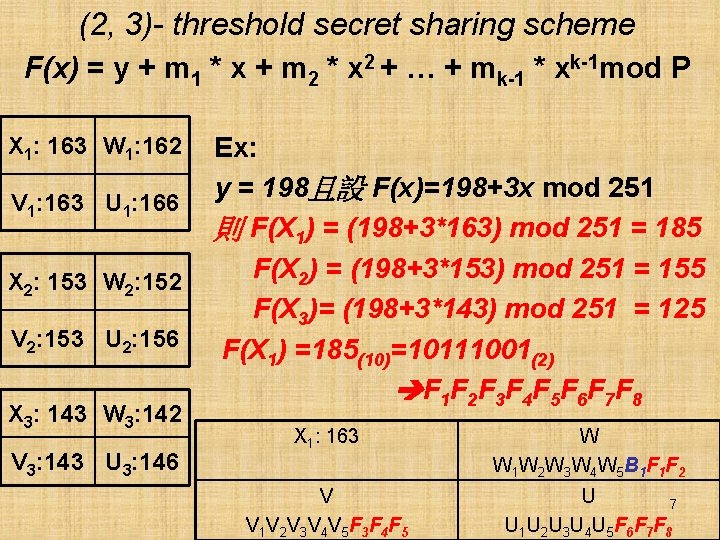
(2, 3)- threshold secret sharing scheme F(x) = y + m 1 * x + m 2 * x 2 + … + mk-1 * xk-1 mod P X 1: 163 W 1: 162 V 1: 163 U 1: 166 X 2: 153 W 2: 152 V 2: 153 U 2: 156 X 3: 143 W 3: 142 V 3: 143 U 3: 146 Ex: y = 198且設 F(x)=198+3 x mod 251 則 F(X 1) = (198+3*163) mod 251 = 185 F(X 2) = (198+3*153) mod 251 = 155 F(X 3)= (198+3*143) mod 251 = 125 F(X 1) =185(10)=10111001(2) F 1 F 2 F 3 F 4 F 5 F 6 F 7 F 8 X 1: 163 W W 1 W 2 W 3 W 4 W 5 B 1 F 2 V V 1 V 2 V 3 V 4 V 5 F 3 F 4 F 5 U 7 U 1 U 2 U 3 U 4 U 5 F 6 F 7 F 8

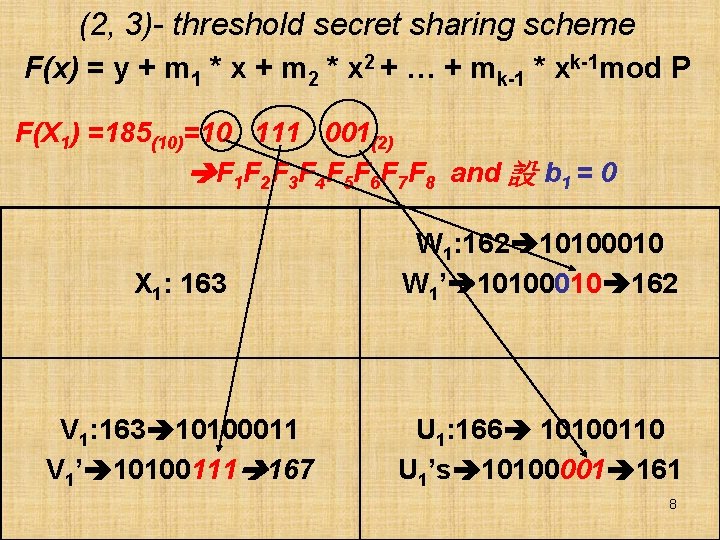
(2, 3)- threshold secret sharing scheme F(x) = y + m 1 * x + m 2 * x 2 + … + mk-1 * xk-1 mod P F(X 1) =185(10)=10 111 001(2) F 1 F 2 F 3 F 4 F 5 F 6 F 7 F 8 and 設 b 1 = 0 X 1: 163 W 1: 162 10100010 W 1’ 10100010 162 V 1: 163 10100011 V 1’ 10100111 167 U 1: 166 10100110 U 1’s 10100001 161 8

Recovery Algorithm (163, 185), (153, 155), (143, 125) Ex 1: (163, 185), (153, 155) 設 F(x)=ax+y mod 251 F(163) = (a*163+y) mod 251 =185 F(153) = (a*153+y) mod 251 =155 解聯立 得 a=3, y=198 Ex 2: (163, 185), (143, 125) F(163) = (a*163+y) mod 251 =185 F(143) = (a*143+y) mod 251 =125 解聯立 得 a=3, y=198 9

Experimental Results (The PSNR of stego-image about 39. 2 d. B) 10

Conclusions • The proposed scheme has three levels of security protection. (1) the (k, n)-threshold function is adopted. (2) data hiding technique is employed. (3) has the capability of authentication. 11