Rootkits This presentation is an amalgam of presentations


















- Slides: 27

Rootkits This presentation is an amalgam of presentations by Mark Michael, Randy Marchany and Ed Skoudis. I have edited and added material. Dr. Stephen C. Hayne

Traditional Root. Kits n n Replaces key system components Less detectable than application-level Trojan Horse Backdoors Traditionally focused on UNIX systems, but NOW on Windows… Root access is required initially

Traditional Root. Kits n On Windows systems… n n Root. Kits Replace Dynamic Link Libraries or alters the system in other ways On UNIX systems… n Root. Kits replace /bin/login with a backdoor version of /bin/login

Traditional Root. Kits n n n When an attacker enters the backdoor password access is given to the system Backdoor password still works if other passwords are changed Login is not recorded in log files for the backdoor user

Traditional Root. Kits n Some other programs replaced: n du - shows free disk space n n find - finds files n n Hides attacker’s files ifconfig - shows status of interfaces n n Root. Kits hides space used by attacking tools masks promiscuous mode ls - shows contents of directories n Hides attacker’s files

Traditional Root. Kits n “Original” Linux Root. Kit 5 (lrk 5) n n n written by Lord Somer one of the most full-featured Root. Kits includes Trojan versions of the following: n chfn, chsh, crontab, du, find, ifconfig, inetd, killall, login, ls, netstat, passwd, pidof, ps, rshd, syslogd, tcpd, top, sshd, and su

Defending against Traditional Root. Kits n Remember root-level access is needed to install a Root. Kit… n n n Use “echo *” command to look for changes Get a program to scan /bin/login and see if it has been corrupted Use a File Integrity Checker such as Tripwire n Save hashes on read-only media

Tripwire n n n Available from www. tripwire. org First of the file integrity checkers Unix and Windows versions available n n Network capable versions available Useful in finding trojan programs

Tripwire n n n Generates a “signature” for each file based on checksums and other characteristics. These signatures are stored in a database file that should be kept offline. This is the baseline.

Security Configuration Management n Video – Open Source n Video – Enterprise NIST 800 -171

Tripwire n Advantages n n Security Issues n n n Simple interface, good choice of crypto hash functions, good all-around tool How to protect DBs…? Need to protect tripwire executables? Disadvantages n Kernel mod attacks, initial config takes quite some time to customize, no network security

Kernel-Level Root. Kits n n Trojan Horse becomes the Kernel Most difficult to detect Gives the attacker complete control of the underlying system Nothing on the system can be trusted

Kernel-Level Root. Kits n n Most common feature is execution redirection Instead of changing other programs to hide files, the kernel hides them Kernel may also hide processes that are running Port usage is often masked

Kernel-Level Root. Kits n Some early Kernel-level Root. Kits are: n n Knark (Linux) Adore (Linux) Plasmoid’s Solaris Loadable Kernel Module (Solaris) The Windows NT kernel-level Root. Kit (Windows)

Kernel-Level Root. Kits n Implemented with Loadable Kernel Modules (LKM) n n n LKM is used to extend the capabilities of the system only for some UNIX systems LKM makes it easy! To install the Knark Root. Kit type: n n “insmod knark. o, ” no reboot necessary

KNARK Background n n Written by Creed Released in 1999 Versions exist for Linux 2. 2 and 2. 4 kernels Very popular in ‘script kiddie’ community

KNARK Capabilities n n n n Hide/Unhide files or directories Hide TCP/UDP connections Execution Redirection Unauthenticated privilege escalation via the rootme program within knark Ability to change UID/GID of a running process Unauthenticated, privileged remote execution daemon Kill – 31 to hide a running process

Installing KNARK n KNARK IS installed as a Loadable Kernel Module (LKM) n n n System must have LKM enabled in order to be able to load KNARK Can be defeated if LKM is disabled, HOWEVER, updating system becomes much more complicated The KNARK rootkit has an additional LKM module to hide the presence of KNARK from the insmod (installed module) command.

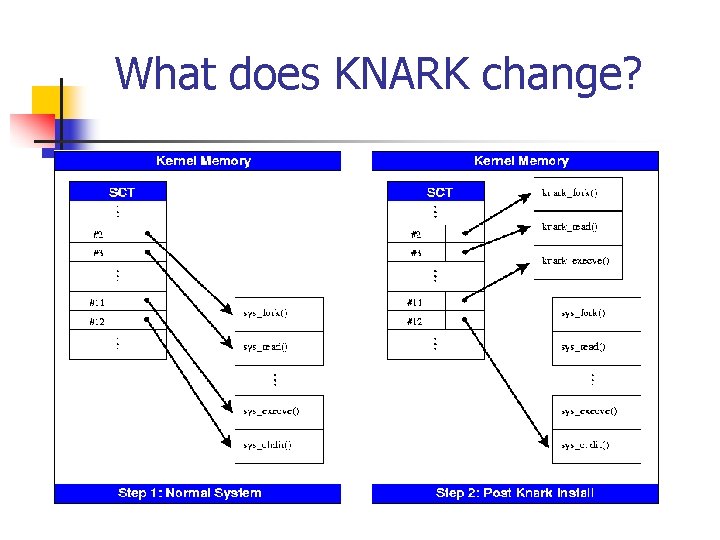
What does KNARK Change? n n KNARK modifies the system call table (sys_call_table) within kernel memory by redirecting some system calls (sys_read, sys_getdents) to malicous system calls written by CREED. These new malicious system calls function as normal except in certain circumstances.

What does KNARK change?

What does KNARK Change? n n Can no longer trust the output of the system calls? Very difficult to detect rootkits such as KNARK using conventional methods n n System utility files (ls, ps) are not modified Kernel Output to system utility files IS modified.

Detecting KNARK n Cyptographic Checksums of system utilities will NOT change when KNARK is installed n n May be possible to take cryptographic checksum of selected region of kernel in order to detect rootkit modification of kernel (St. Michael) Can detect presence of KNARK type rootkits by examining sys_call_table

Detecting KNARK n The file /boot/System. map is created when system is initially compiled n n n /boot/System. map contains correct address of kernel system calls /boot/system map can be archived or retrieved from a known good system for comparison Must have Superuser (ROOT) privilege in order to read /dev/kmem (kernel memory)

Detecting KNARK using the kern_check program n n Developed by Samhain labs GPL (‘free’) software Compares /boot/System. map file against the system call table in kernel memory Will not work against later versions of Red Hat Linux 2. 4 or the Linux 2. 6 kernel

KNARK Summary n n KNARK is a very powerful tool that was very popular with ‘script kiddies’ Very difficult to detect with conventional methods Can no longer trust system output once kernel is compromised Other kernel rootkits can defeat kern_check program (Suck. IT)

Rootkit Summary n n Prevent hackers from gaining root access in order to prevent rootkits from being installed Must check systems on a periodic basis for rootkit exploits Current advice for a rootkitted system: Wipe out files and re-install operating system. Is it possible to re-establish trust on a Rootkited System?

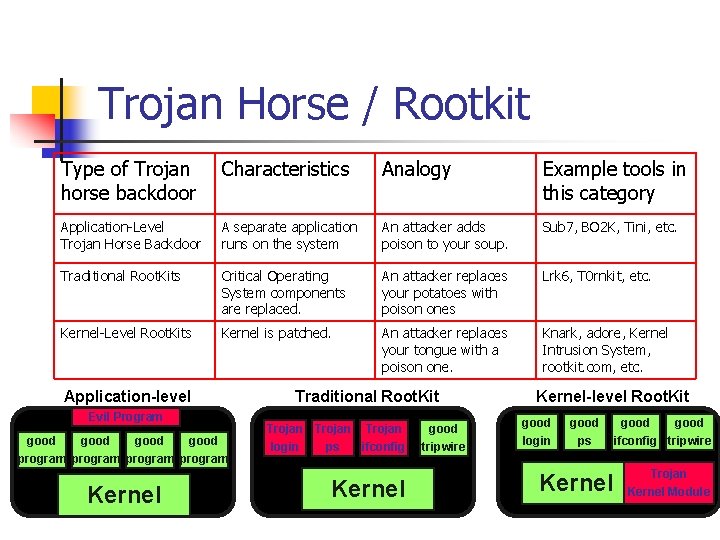
Trojan Horse / Rootkit Type of Trojan horse backdoor Characteristics Analogy Example tools in this category Application-Level Trojan Horse Backdoor A separate application runs on the system An attacker adds poison to your soup. Sub 7, BO 2 K, Tini, etc. Traditional Root. Kits Critical Operating System components are replaced. An attacker replaces your potatoes with poison ones Lrk 6, T 0 rnkit, etc. Kernel-Level Root. Kits Kernel is patched. An attacker replaces your tongue with a poison one. Knark, adore, Kernel Intrusion System, rootkit. com, etc. Application-level Evil Program good program Kernel Traditional Root. Kit Trojan login ps Trojan good ifconfig tripwire Kernel-level Root. Kit good login ps Kernel good ifconfig tripwire Trojan Kernel Module