Reverse Engineering Shaochun Xu Computer Science University of












- Slides: 29

Reverse Engineering Shaochun Xu Computer Science University of Windsor

Contents b b b What is Reverse Engineering (RE)? Why do we need Reverse Engineering? Scope and Tasks of Reverse Engineering Different Approaches RE tools Conclusions

What is Reverse Engineering ? b You • • have an unexpected case: You finished one course project using Java Your program runs OK But, by accident, you delete the java file How to hand in your project?

What is Reverse Engineering ? b You • • have an unexpected case: You finished one course project using Java Your program runs OK But, by accident, you delete the java file How to hand in your project? b Reverse Engineering

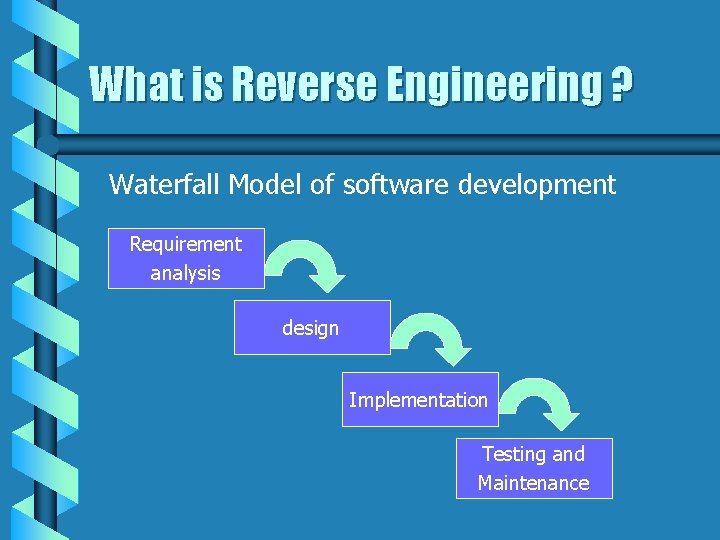
What is Reverse Engineering ? Waterfall Model of software development Requirement analysis design Implementation Testing and Maintenance

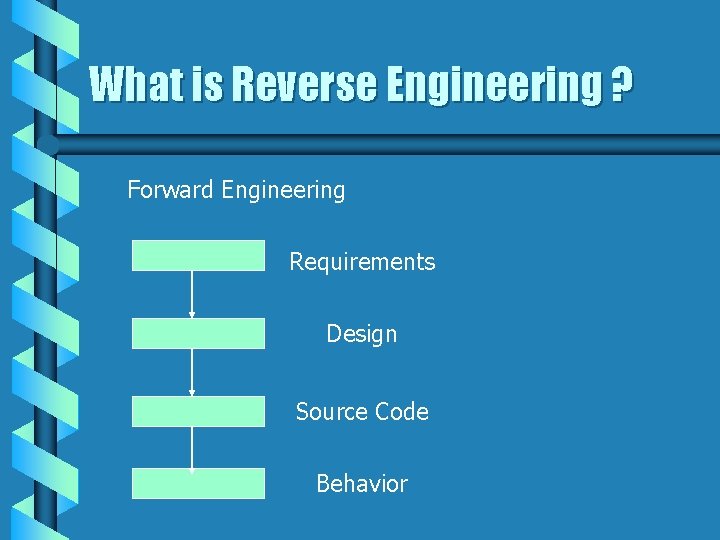
What is Reverse Engineering ? Forward Engineering Requirements Design Source Code Behavior

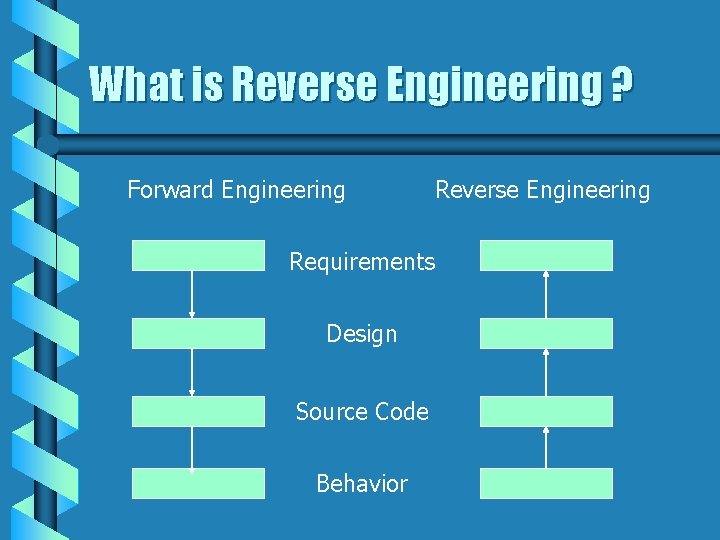
What is Reverse Engineering ? Forward Engineering Reverse Engineering Requirements Design Source Code Behavior

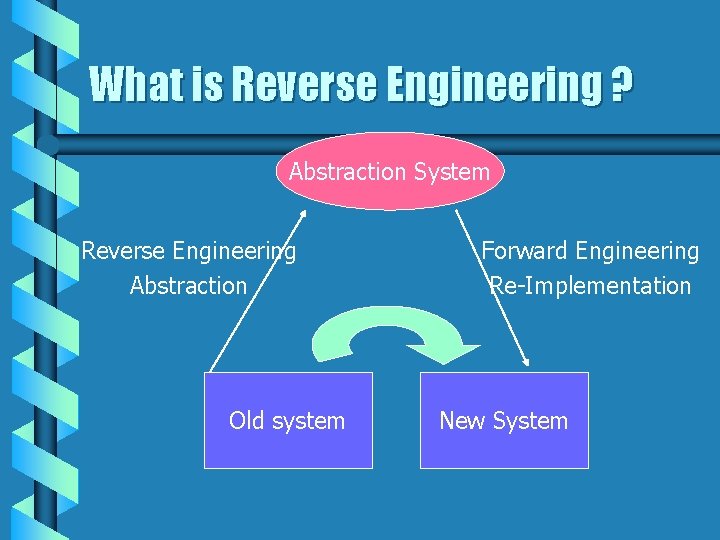
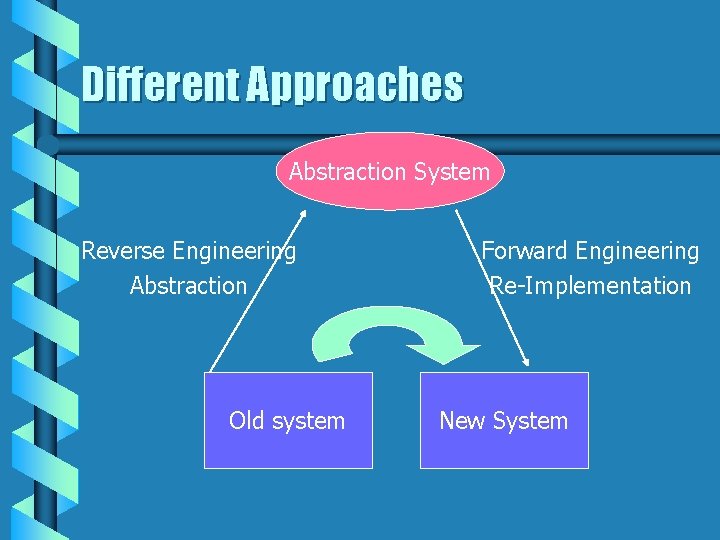
What is Reverse Engineering ? Abstraction System Reverse Engineering Abstraction Old system Forward Engineering Re-Implementation New System

What is Reverse Engineering? b RE encompasses any activity that is done to determine how a product works, to learn the ideas and technology that were used in developing that product. b RE can be done at many levels b RE generally belongs to Software Maintenance

The Early Days of RE b Law of Software Revolution (Lehman, 1980) b Fundamental strategies for program comprehension (Brooks, 1983) b Taxonomy of Reverse Engineering (Chikofsky&Cross, 1990) b WCRE (Working Conference on R. E. , 1990) b IWPC (Int. Workshop on Program Comprehension)

Why do we need RE ? b Recovery of lost information • providing proper system documentation b Assisting with maintenance • identification of side effects and anomalies b Migration to another hw/sw platform b Facilitating software reuse

Why do we need RE ? b Benefits • • maintenance cost savings quality improvements competitive advantages software reuse facilitation

Difficulties of Reverse Engineering b Gap between problem /solution domain b Gap between concrete and abstract b Gap between coherency/disintegration b Gap between hierarchical/associational

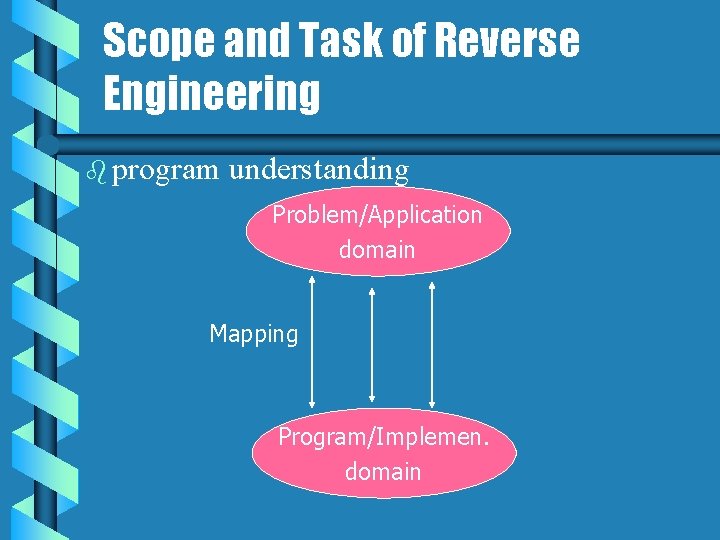
Scope and Task of Reverse Engineering b program understanding Problem/Application domain Mapping Program/Implemen. domain

Scope and Task of Reverse Engineering b Redocumentation and/or document generation b Recovery of design approach and design details at any level of abstraction b Identifying reusable components and components that need restructuring b Recovering business rules b Understanding high-level system description.

Discovery of Abstraction b Discovery of abstraction in large system • maintenance purpose • evolution purpose • reengineering purpose

Levels of abstractions b Application • Application concepts, business rule, policies b Function • Logical and functional specification, non-functional requirement b Structure • Data and control flow, dependency graphs • Structure and subsystem charts • Architectures b Implementation • Symbol tables, source text

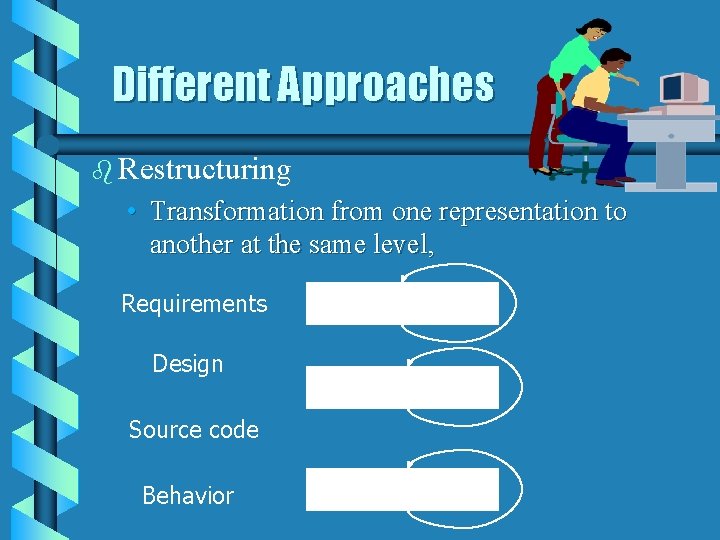
Different Approaches b Restructuring • Transformation from one representation to another at the same level, Requirements Design Source code Behavior

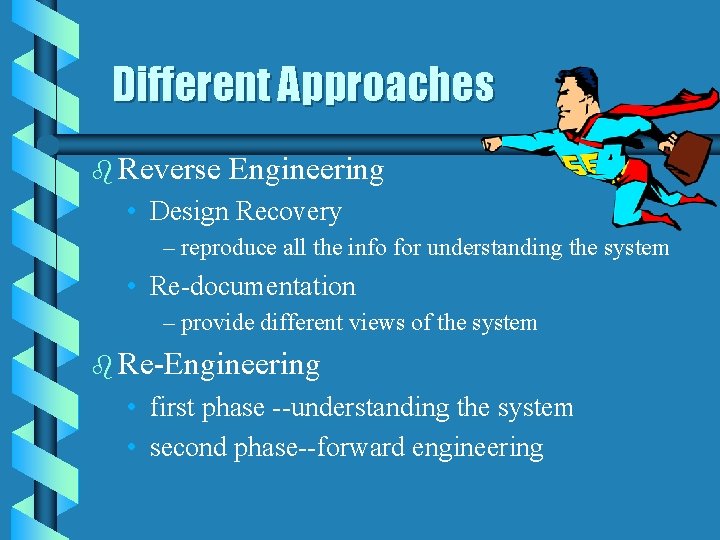
Different Approaches b Reverse Engineering • Design Recovery – reproduce all the info for understanding the system • Re-documentation – provide different views of the system b Re-Engineering • first phase --understanding the system • second phase--forward engineering

Different Approaches Abstraction System Reverse Engineering Abstraction Old system Forward Engineering Re-Implementation New System

Reverse Engineering Tools b Analysis Tools b Browsers b Object Server b Task Oriented Tools

Example--Java Decompiler b How to recover bytecode from. class file under Unix/Win with JDK? % javap -c <filename> % javap -help (to see the options) b Java Decompilers • ”Class. Cracker” http: //www. pcug. org. au/~mayon/ • “De. Cafe Pro" from De. Cafe, France at http: //decafe. hypermart. net/index. htm • “Source. Again" from Ahpah corp at http: //www. ahpah. com

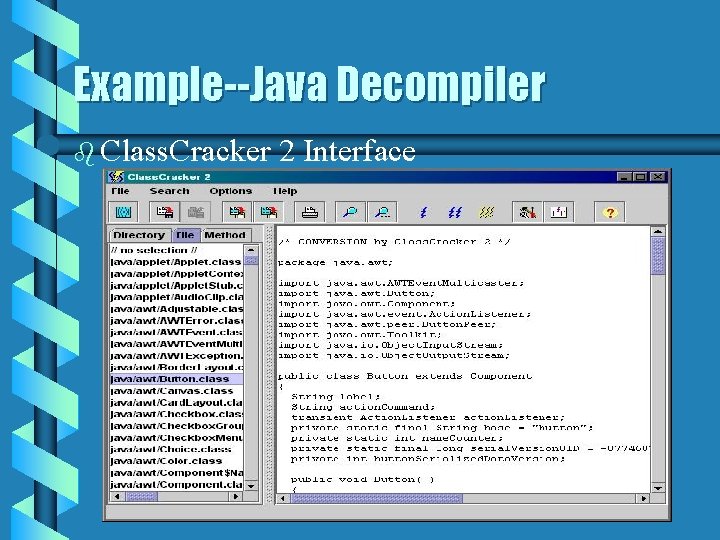
Example--Java Decompiler b Class. Cracker 2 Interface

Example--Java Decompiler b Components of Class. Cracker 2 • Java decompiler – retrieves Java source code from Java class files • Java disassembler – produces Java Assembly Code • A Java class file viewer – displays Java class file structures.

Example--Java Decompiler b Features of Class. Cracker 2 • User visual interface. • Can decompile class files within zip or jar files. • Conversion mode (JAVA, JASM or JDUMP) is selectable • A Batc Mode allows multiple class files to be decompiled simultaneously • more…. . .

Example--Java Decompiler b Class. Cracker 2 System Requirements • All platform (Window/Linus/Unix) • JDK /JRE b Do not believe it? • From my. Class_origin. class ==>my. Class. java • % javac my. Class. java (==>my. Class. class) • % diff my. Class. class my. Class_origin. class

Example--Java Decompiler b Class. Cracker 2. 0 --want to try it? • Free download at http: //www. pcug. org. au/~mayon/classcracker/ ccgetdemo. html • Only first three methods are decoded. b Bridge 1. 0 ---Free • http: //www. geocities. com/Silicon. Valley/Brid ge/8617/jad. html

Conclusions b Reverse Engineering is a new research area among software maintenance b RE includes activities of understanding the system and recovery info from system b Program understanding is the most important subset of Reverse Engineering b Discovery of abstraction is key issue

Questions ?