Reverse Engineering Dept of ICT MIT Manipal Reverse




![References [1] P. Aiken. Data Reverse Engineering: Slaying the Legacy Dragon. Mc. Graw- Hill. References [1] P. Aiken. Data Reverse Engineering: Slaying the Legacy Dragon. Mc. Graw- Hill.](https://slidetodoc.com/presentation_image_h2/e31dd75f9f7c47f9ef15211a538a8247/image-18.jpg)

- Slides: 19

Reverse Engineering Dept. of I&CT, MIT, Manipal

Reverse Engineering Aspects To Be Covered • Introduction to reverse engineering. • Comparison between reverse and forward engineering. • Reverse engineering process. • Approaches for reverse engineering. • Other areas of application. • Legal issues. Dept. of I&CT, MIT, Manipal

Reverse Engineering Introduction • What is Reverse Engineering ? The process of analyzing a system to (i) identify the system's components and their inter-relationships and (ii) to create representation of the system in another form. • Also called as “going backwards through development cycle. ” Dept. of I&CT, MIT, Manipal

Reverse Engineering Objectives 1. Re-documentation A process to derive the design or speciation of a system from its source code. 2. Design Recovery Design recovery aims at recreating design abstractions from the source code, existing documentation, experts' knowledge and any other source of information. Dept. of I&CT, MIT, Manipal

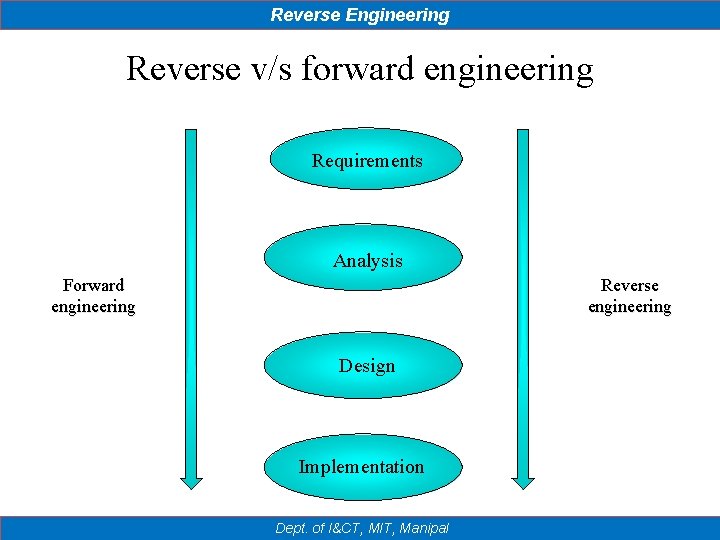
Reverse Engineering Reverse v/s forward engineering Requirements Analysis Forward engineering Reverse engineering Design Implementation Dept. of I&CT, MIT, Manipal

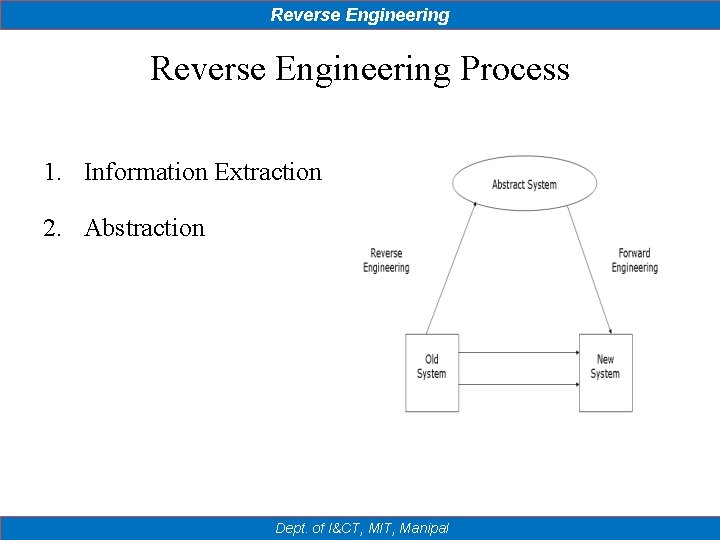
Reverse Engineering Process 1. Information Extraction 2. Abstraction Dept. of I&CT, MIT, Manipal

Reverse Engineering Use Of Reverse Engineering • Transforming obsolete products into useful ones by adapting them to new systems and platforms. • Some features of the system needs to be refined out. • It can be use if there is no adequate documentation of the original design. • Investigating and correcting errors and limitations in existing programs. • Studying the design principles of a product as part of an education in engineering. • Understanding how a product works. Dept. of I&CT, MIT, Manipal

Reverse Engineering Approaches To Reverse Engineering • White Box Analysis • Black Box Analysis • Gray Box Analysis Dept. of I&CT, MIT, Manipal

Reverse Engineering White Box Analysis • Involves analysis of source code. • For e. g. decompiling a binary code to get the source code is a kind of white box analysis. • Effective for finding programming and implementation errors in software. Dept. of I&CT, MIT, Manipal

Reverse Engineering Black Box Analysis • Black box analysis refers to analyzing a running program by probing it with various inputs. • This can be used to test for the security issues of the system. Dept. of I&CT, MIT, Manipal

Reverse Engineering Gray Box Analysis • Gray box analysis combines white box techniques with black box input testing. • A good example of a simple gray box analysis is running a target program within a debugger and then supplying particular sets of inputs to the program. Dept. of I&CT, MIT, Manipal

Reverse Engineering Code Reverse Engineering • Reverse engineering focuses at reverse engineering at code level. • For reverse engineering code is a reliable source of information. • Limitation : the code does not contain all the information that is needed. Dept. of I&CT, MIT, Manipal

Reverse Engineering Data Reverse Engineering • Data reverse engineering tackles the question of what information is stored and how this information can be used. • Data reverse engineering techniques can also be used to assess the overall quality of software systems. • Consists of 2 main activities : 1. Data Analysis 2. Conceptual Abstraction Dept. of I&CT, MIT, Manipal

Reverse Engineering Data Analysis • The analysis activity aims to recover an up-to-date logical data model that is structurally complete and semantically annotated. • Computer-aided reverse engineering tools can be used for data analysis. Dept. of I&CT, MIT, Manipal

Reverse Engineering Conceptual Abstraction • Conceptual abstraction aims to map the logical data model derived from data analysis to an equivalent conceptual design. • ER-Diagrams or Object Oriented data models can be used to represent the design. • Several tools support data abstraction but has following limitations : 1. Iteration 2. Bidirectional Mapping Process 3. Research Direction Dept. of I&CT, MIT, Manipal

Reverse Engineering Reverse engineering can also be used for • Military applications • Mechanical Devices Dept. of I&CT, MIT, Manipal

Reverse Engineering Legal Issues • Reverse engineering has been held a legitimate form of discovery. • The law regarding reverse engineering in the computer software and hardware context is less clear due to : 1. Anti reverse engineering licensing provisions. 2. Prohibition on the circumvention of technologies embedded within protection measures. Dept. of I&CT, MIT, Manipal
![References 1 P Aiken Data Reverse Engineering Slaying the Legacy Dragon Mc Graw Hill References [1] P. Aiken. Data Reverse Engineering: Slaying the Legacy Dragon. Mc. Graw- Hill.](https://slidetodoc.com/presentation_image_h2/e31dd75f9f7c47f9ef15211a538a8247/image-18.jpg)
References [1] P. Aiken. Data Reverse Engineering: Slaying the Legacy Dragon. Mc. Graw- Hill. [2] http: //www. jenkins. eu/articles/reverse-engineering. asp [3] http : //www. en. wikipedia. org/wiki/Reverse. Engineering [4] http: //www. chillingeects. org/reverse/faq. cgi

THANK YOU