Redefining Endpoint Security Agenda 1 Environment and Endpoint








- Slides: 27

Redefining Endpoint Security

Agenda 1 Environment and Endpoint Challenges 2 Symantec Endpoint Protection 3 Entitlement/Deployment/Migration 4 Symantec Network Access Control 5 Available Now 2

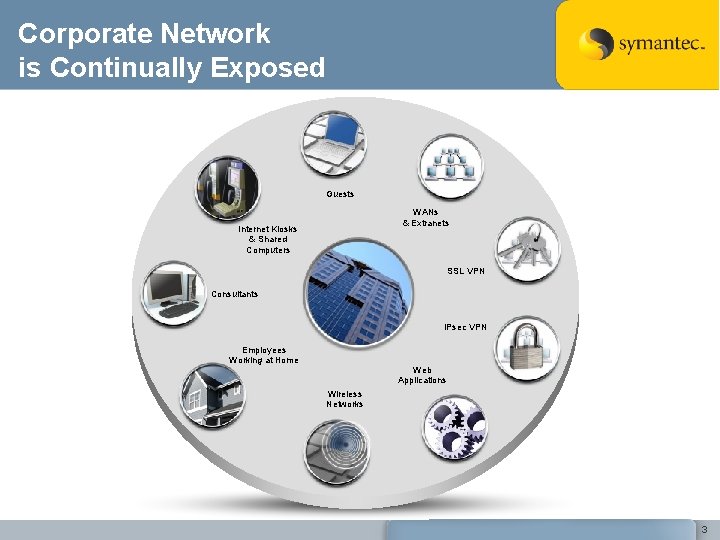
Corporate Network is Continually Exposed Guests WANs & Extranets Internet Kiosks & Shared Computers SSL VPN Consultants IPsec VPN Employees Working at Home Web Applications Wireless Networks 3

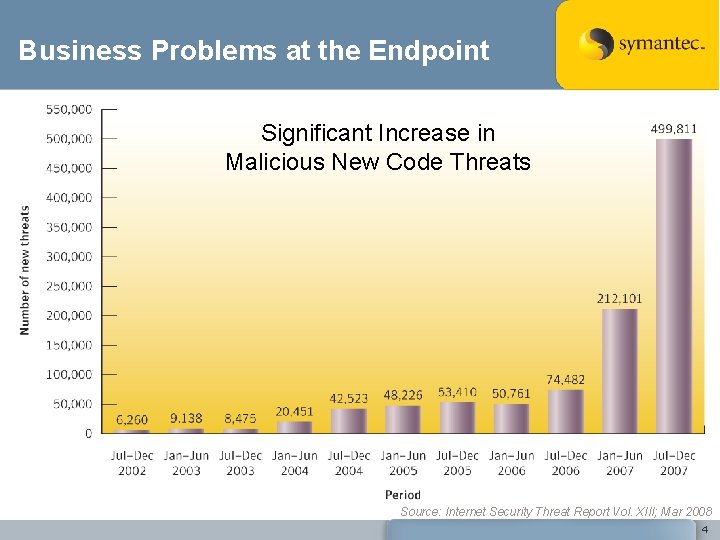
Business Problems at the Endpoint • Endpoint management costs Significant are increasing – Increase in Malicious New Code Threats Cost of downtime impacts both productivity and revenue, productivity hit largest in enterprise – Costs to acquire, manage and administer point products are increasing, as well as the demand on system resources • Complexity is increasing as well – Complexity and resources needed to manage disparate endpoint protection technologies are inefficient and time consuming • Growing number of known and unknown threats – Stealth-based and silent attacks are increasing, so there is a need for antivirus to do much more Source: Internet Security Threat Report Vol. XIII; Mar 2008 4

Changes in the Threat Landscape From Hackers… To Thieves Fame motivated Financially motivated Noisy and highly visible Silent Indiscriminate Highly targeted Few named variants Overwhelming variants 5

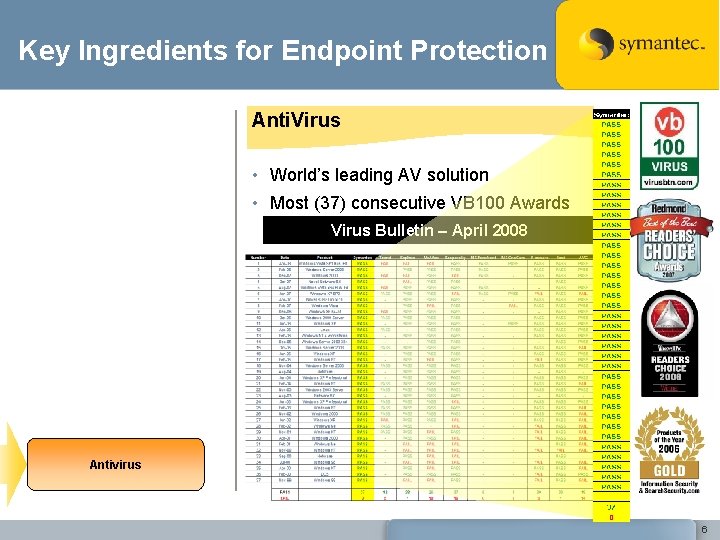
Key Ingredients for Endpoint Protection Anti. Virus • World’s leading AV solution • Most (37) consecutive VB 100 Awards Virus Bulletin – April 2008 Antivirus 6

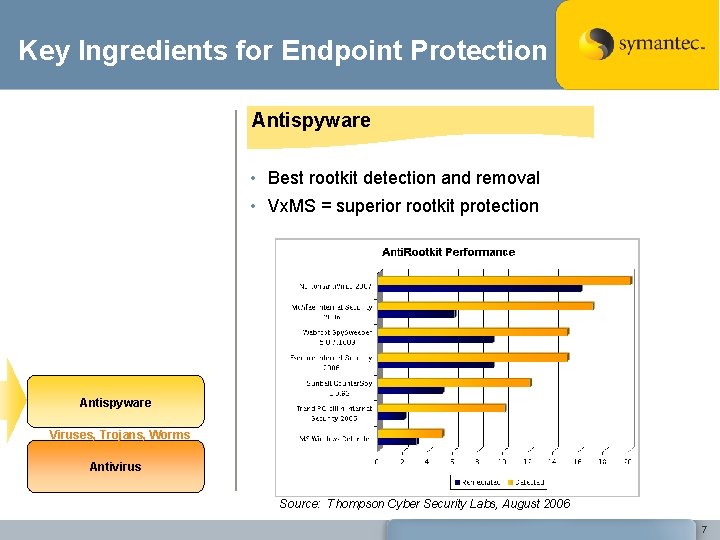
Key Ingredients for Endpoint Protection Antispyware • Best rootkit detection and removal • Vx. MS = superior rootkit protection Antispyware Viruses, Trojans, Worms Antivirus Source: Thompson Cyber Security Labs, August 2006 7

Key Ingredients for Endpoint Protection Firewall • Industry leading endpoint firewall technology • Gartner MQ “Leader” – 4 consecutive years • Rules based FW can dynamically adjust port settings to block threats from spreading Firewall Spyware, Rootkits Antispyware Viruses, Trojans, Worms Antivirus 8

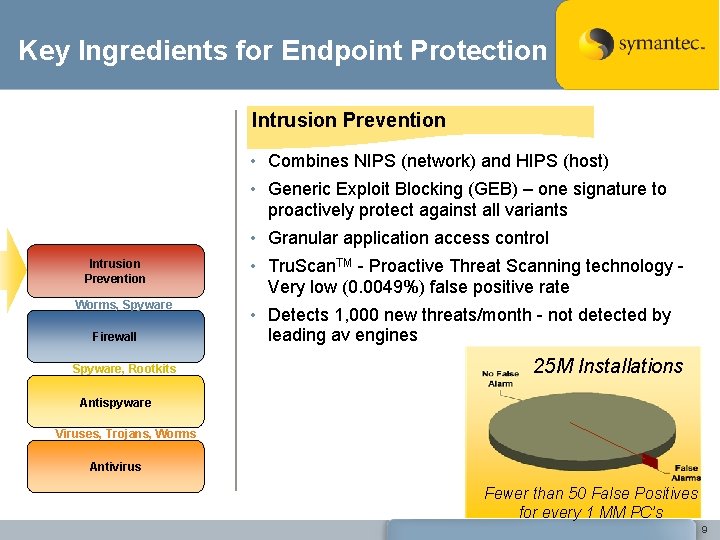
Key Ingredients for Endpoint Protection Intrusion Prevention • Combines NIPS (network) and HIPS (host) • Generic Exploit Blocking (GEB) – one signature to proactively protect against all variants • Granular application access control Intrusion Prevention Worms, Spyware Firewall Spyware, Rootkits • Tru. Scan. TM - Proactive Threat Scanning technology Very low (0. 0049%) false positive rate • Detects 1, 000 new threats/month - not detected by leading av engines 25 M Installations Antispyware Viruses, Trojans, Worms Antivirus Fewer than 50 False Positives for every 1 MM PC’s 9

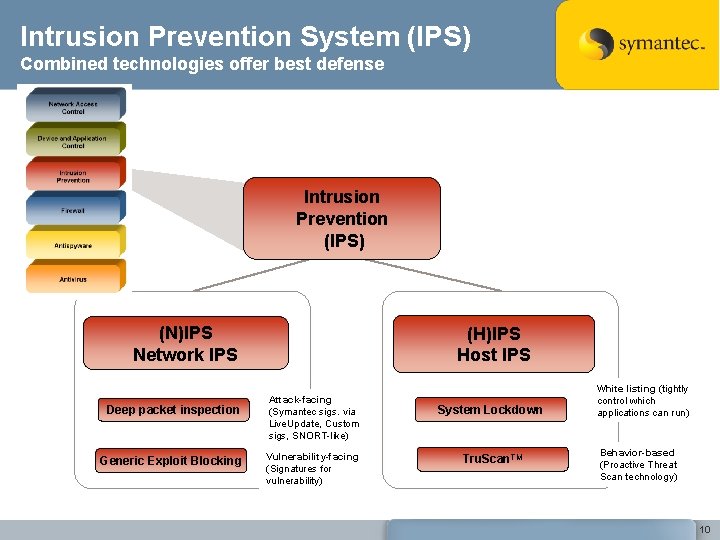
Intrusion Prevention System (IPS) Combined technologies offer best defense Intrusion Prevention (IPS) (N)IPS Network IPS Deep packet inspection Generic Exploit Blocking (H)IPS Host IPS Attack-facing (Symantec sigs. via Live. Update, Custom sigs, SNORT-like) Vulnerability-facing (Signatures for vulnerability) System Lockdown Tru. Scan. TM White listing (tightly control which applications can run) Behavior-based (Proactive Threat Scan technology) 10

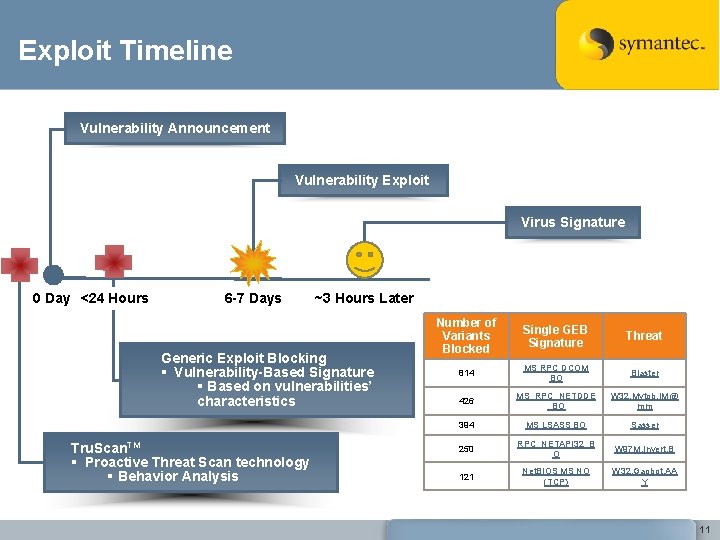
Exploit Timeline Vulnerability Announcement Vulnerability Exploit Virus Signature 0 Day <24 Hours 6 -7 Days ~3 Hours Later Generic Exploit Blocking § Vulnerability-Based Signature § Based on vulnerabilities’ characteristics Tru. Scan. TM § Proactive Threat Scan technology § Behavior Analysis Number of Variants Blocked Single GEB Signature Threat 814 MS RPC DCOM BO Blaster 426 MS_RPC_NETDDE _BO W 32. Mytob. IM@ mm 394 MS LSASS BO Sasser 250 RPC_NETAPI 32_B O W 97 M. Invert. B 121 Net. BIOS MS NO (TCP) W 32. Gaobot. AA Y 11

Tru. Scan. TM - Proactive Threat Scan Detects 1, 000 threats/month not detected by top 5 leading antivirus engines • 6 months testing with Norton consumer technology • Very low false positive rate (0. 004%) • Fewer than 50 False Positives for every 1 M computers • No set up or configuration required 12

Key Ingredients for Endpoint Protection Device and Application Control • Prevents data leakage Device and Application Control 0 -day, Key Logging Intrusion Prevention • Restrict Access to devices (USB keys, Back-up drives) • Whitelisting – allow only “trusted” applications to run Worms, Spyware Firewall Spyware, Rootkits Antispyware Viruses, Trojans, Worms Antivirus s sticks drive y e l r C b o ova lly. FD mem i m e S e l r. b 2 o W 3 mova lf ont e e r s t i s t ge pying ry sticks next o s c • tar i y e b o devic reads USB mem e p h t s • hen as w h s c n u u s ally r omputer c i t a ac tom • au nected to con 13

Key Ingredient for Endpoint Compliance Network Access Control • Comes ready for Network Access Control – add on Device and Application Control • Agent is included, no extra agent deployment • Simply license SNAC Enforcement Intrusion Prevention Firewall Antispyware Antivirus 14

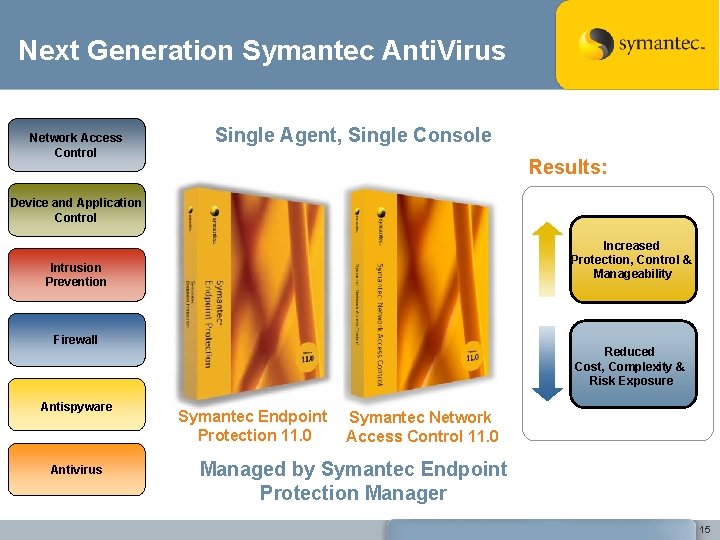
Next Generation Symantec Anti. Virus Network Access Control Single Agent, Single Console Results: Device and Application Control Increased Protection, Control & Manageability Intrusion Prevention Firewall Antispyware Antivirus Reduced Cost, Complexity & Risk Exposure Symantec Endpoint Protection 11. 0 Symantec Network Access Control 11. 0 Managed by Symantec Endpoint Protection Manager 15

Beta Customer Value Data • Single console – Customers will reduce management hours by 75% • Security Related Reporting – One customer expects to save 97% of the hours on weekly security related reporting • Application Control – One customer: • will eliminate nearly $800, 000 in cost of servers currently being used to maintain performance and sufficient drive space because of music downloading – Another: • anticipates recovering over $2. 0 million from network outages caused by unauthorized peer to peer applications 16

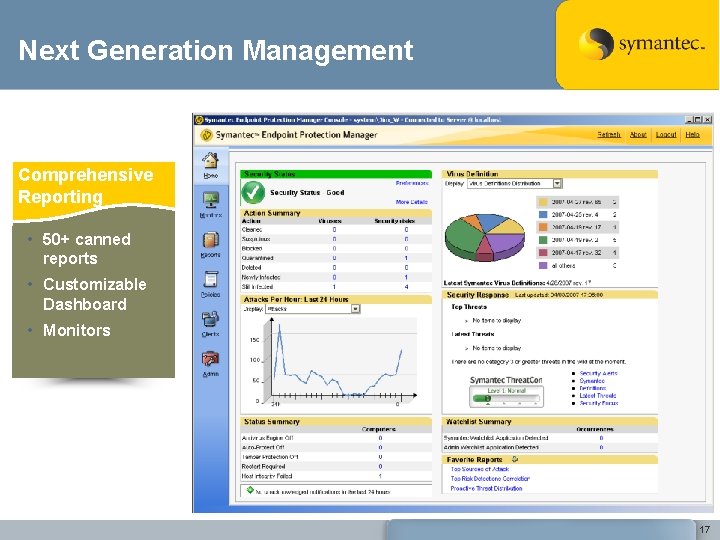
Next Generation Management Comprehensive Reporting • 50+ canned reports • Customizable Dashboard • Monitors 17

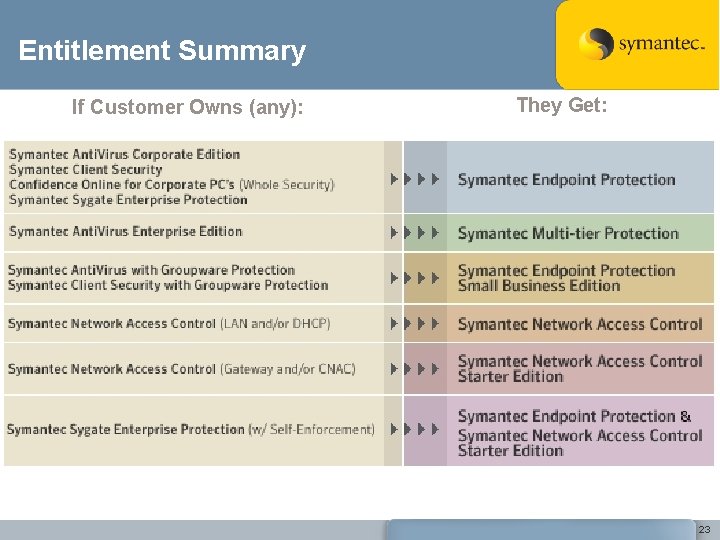
Entitlement Summary If Customer Owns (any): They Get: 23

Endpoint Bundles/ Multi-Product Packages • Symantec™ Multi-tier Protection 11. 0 – Unmatched protection for endpoints, multiplatform network environments and mail servers and gateways. – Includes: • Symantec Endpoint Protection 11. 0 • Symantec Anti. Virus for Macintosh & Linux • Symantec Mail Security for SMTP, Domino & MS Exchange • Symantec™ Endpoint Protection Small Business Edition 11. 0 – A simple and cost-effective solution designed to safeguard business assets through Symantec's trusted protection – Includes: • Symantec Endpoint Protection 11. 0 • Symantec Mail Security for MS Exchange 24

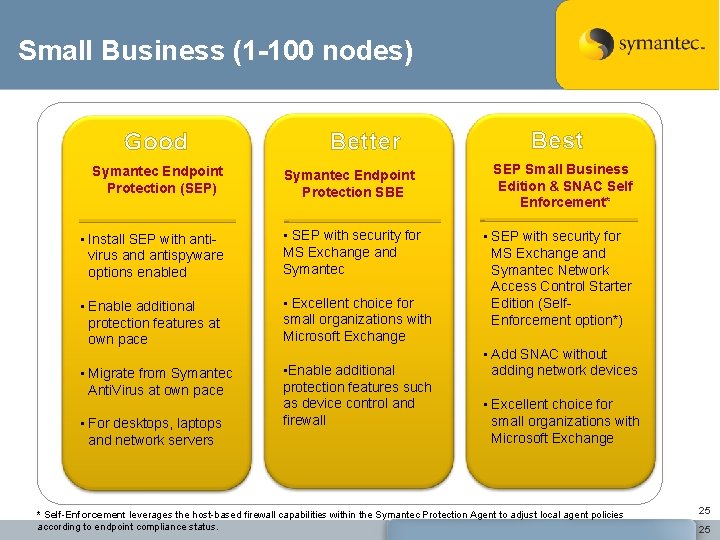
Small Business (1 -100 nodes) Good Symantec Endpoint Protection (SEP) Better Symantec Endpoint Protection SBE • Install SEP with antivirus and antispyware options enabled • SEP with security for MS Exchange and Symantec • Enable additional protection features at own pace • Excellent choice for small organizations with Microsoft Exchange • Migrate from Symantec Anti. Virus at own pace • Enable additional protection features such as device control and firewall • For desktops, laptops and network servers Best SEP Small Business Edition & SNAC Self Enforcement* • SEP with security for MS Exchange and Symantec Network Access Control Starter Edition (Self. Enforcement option*) • Add SNAC without adding network devices • Excellent choice for small organizations with Microsoft Exchange * Self-Enforcement leverages the host-based firewall capabilities within the Symantec Protection Agent to adjust local agent policies according to endpoint compliance status. 25 25

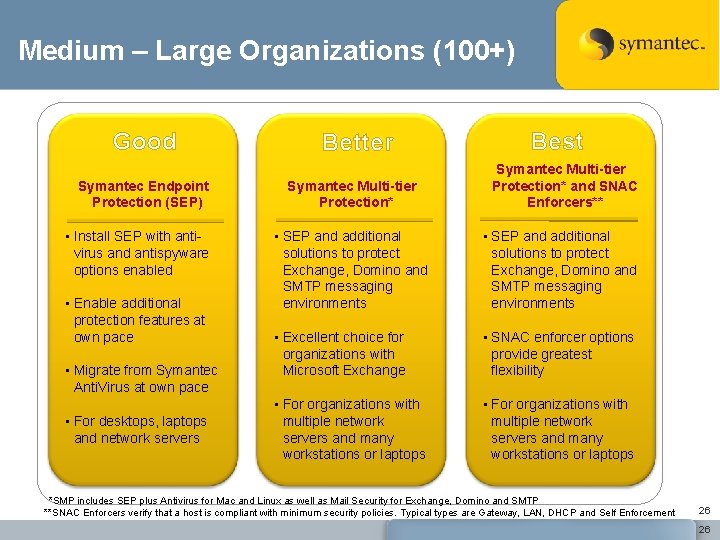
Medium – Large Organizations (100+) Good Symantec Endpoint Protection (SEP) • Install SEP with antivirus and antispyware options enabled • Enable additional protection features at own pace • Migrate from Symantec Anti. Virus at own pace • For desktops, laptops and network servers Better Symantec Multi-tier Protection* Best Symantec Multi-tier Protection* and SNAC Enforcers** • SEP and additional solutions to protect Exchange, Domino and SMTP messaging environments • Excellent choice for organizations with Microsoft Exchange • SNAC enforcer options provide greatest flexibility • For organizations with multiple network servers and many workstations or laptops *SMP includes SEP plus Antivirus for Mac and Linux as well as Mail Security for Exchange, Domino and SMTP **SNAC Enforcers verify that a host is compliant with minimum security policies. Typical types are Gateway, LAN, DHCP and Self Enforcement 26 26

Migration Made Easy Overview • What is it? – A free tool to help customers migrate to Symantec Endpoint Protection – “Symantec Integrated Component” Product offered with pre-configures templates to remove previously installed solutions • Symantec • Competitive • Where do I get and When? – Download now at http: //www. altiris. com/download. aspx – Altiris Client Management Suite 30 Day Trial available today • Who can use this? – Any customer or partner may leverage the Symantec Endpoint Protection Integrated Component, but we recommend that customers consider that they are deploying the Altiris management platform. 27

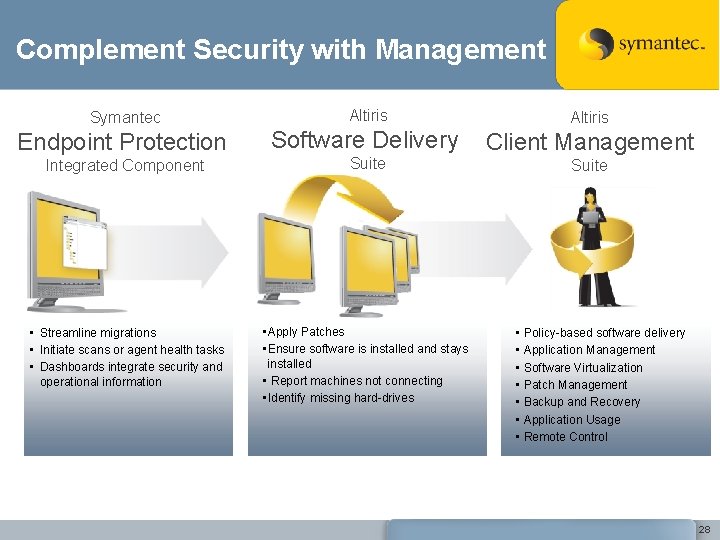
Complement Security with Management Symantec Altiris Endpoint Protection Software Delivery Client Management Integrated Component Suite • Streamline migrations • Initiate scans or agent health tasks • Dashboards integrate security and operational information • Apply Patches • Ensure software is installed and stays installed • Report machines not connecting • Identify missing hard-drives • Policy-based software delivery • Application Management • Software Virtualization • Patch Management • Backup and Recovery • Application Usage • Remote Control 28

Migration Assistance online http: //www. symantec. com/enterprise/support/endpointsecurity/migrate/index. jsp 29

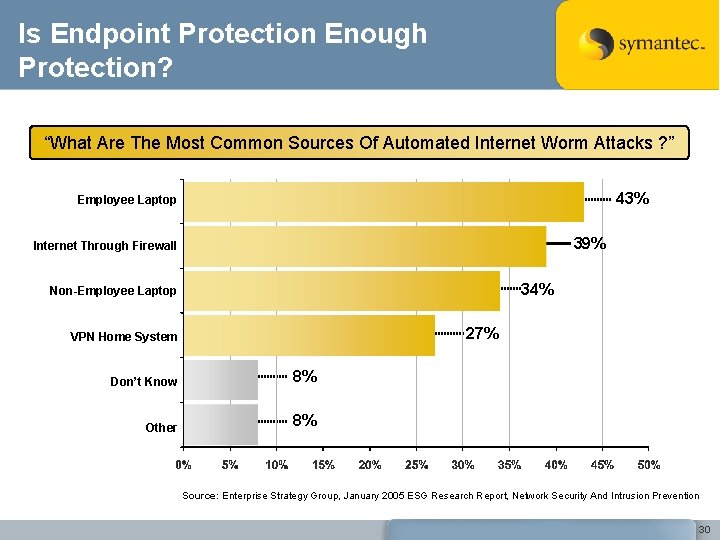
Is Endpoint Protection Enough Protection? “What Are The Most Common Sources Of Automated Internet Worm Attacks ? ” 43% Employee Laptop 39% Internet Through Firewall 34% Non-Employee Laptop 27% VPN Home System Don’t Know 8% Other 8% Source: Enterprise Strategy Group, January 2005 ESG Research Report, Network Security And Intrusion Prevention 30

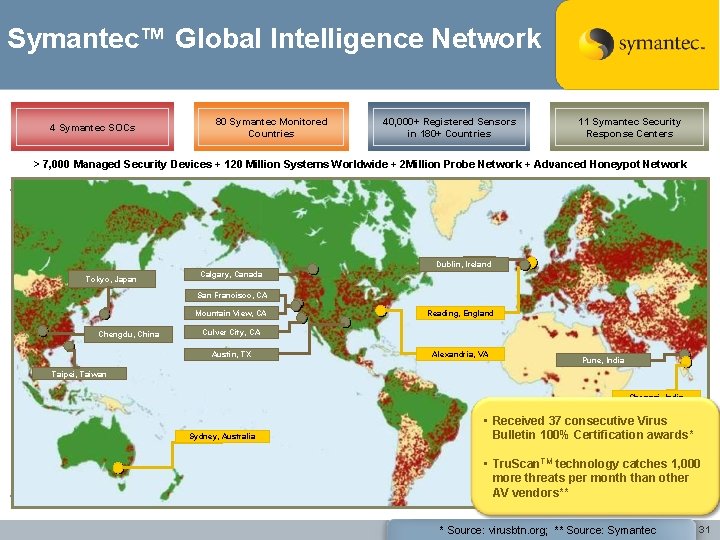
Symantec™ Global Intelligence Network 4 Symantec SOCs 80 Symantec Monitored Countries 40, 000+ Registered Sensors in 180+ Countries 11 Symantec Security Response Centers > 7, 000 Managed Security Devices + 120 Million Systems Worldwide + 2 Million Probe Network + Advanced Honeypot Network Dublin, Ireland Tokyo, Japan Calgary, Canada San Francisco, CA Mountain View, CA Chengdu, China Reading, England Culver City, CA Austin, TX Alexandria, VA Pune, India Taipei, Taiwan Chennai, India Sydney, Australia • Received 37 consecutive Virus Bulletin 100% Certification awards* • Tru. Scan. TM technology catches 1, 000 more threats per month than other AV vendors** * Source: virusbtn. org; ** Source: Symantec 31

Thank You! Copyright © 2007 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice.