Endpoint Encryption Evolution and Trends in Data Security







- Slides: 24

Endpoint Encryption: Evolution and Trends in Data Security Rob Mac. Intosh West Coast Sales Director Utimaco Safeware, Inc Company Confidential - Internal Use Only

Agenda u Data theft and loss u Analysis of Full Disk Encryption solutions w w Software OS HDD-based Chipset u Q&A Copyright © Utimaco Safeware, Inc 2

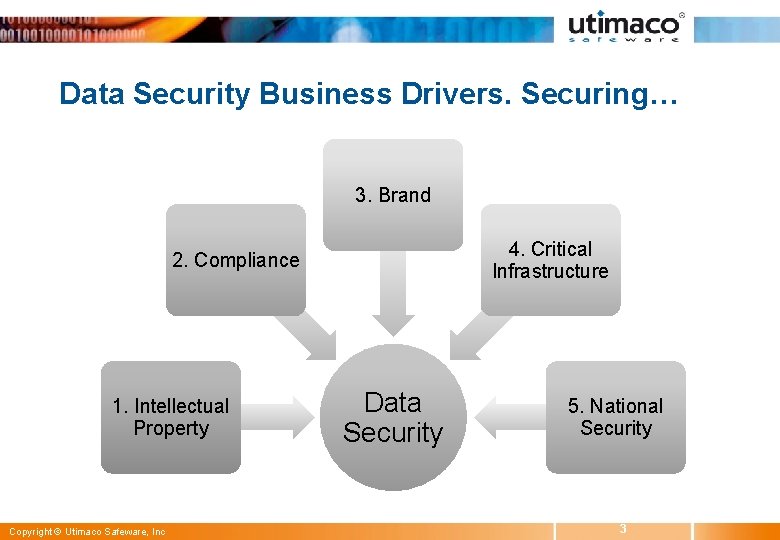
Data Security Business Drivers. Securing… 3. Brand 4. Critical Infrastructure 2. Compliance 1. Intellectual Property Copyright © Utimaco Safeware, Inc Data Security 5. National Security 3

Data Loss Or Theft Is Expensive Recent Surveys Say… Data Is The Target Laptop Theft • Top 3 threats (CSI Survey, 10/08) • Cost of Lost/Stolen record (Ponemon $4. 6 m / Company • Avg. intellectual property loss (CERIAS, “All Data Driven!” • Malware, Botnets, Cyber crime / warfare, Vo. IP/mobile device threats $202 Institute, 02/09) Purdue Univ. 01/09) (Georgia Tech Info. Sec Center, 10/08) Copyright © Utimaco Safeware, Inc 4

Compliance Regs. Mandate Data Security Protection Of Confidential and/or Private Data u Federal w GLBA, HIPAA, PCI u States: 44/50 require “Reasonable measures” w CA: Breach notification (personal, medical). Encryption exempt w OR: Similar to CA (personal). Fines for delayed disclose w WA: Similar to CA u States (“Specific measures”) w NV: Encrypt PII data in transit outside the enterprise w MA: Encrypt all personal information u Canada w PIPEDA: Protect personal info. – collected, used, disclosed. Technologies: e. g. , passwords, encryption 5 Copyright © Utimaco Safeware, Inc

Data Breach Headlines to be Avoided d? e t ep st c r te rs lo n i s me 007 X n J T tio usto 4, 2 a c ni on c er 2 om u m illi tob bc. c m o 4 m Oc msn c e r 9 on ww. r o t fo ted ce: w s a -In -Dat por Sour e -R Copyright © Utimaco Safeware, Inc n ide 5 24 M s Re. U. S 5 f o 00. org s d r ce 2 ghts o ec Sin cyri R a ata osed. priv D n xp ww li lio E e: w urc So 6 ts

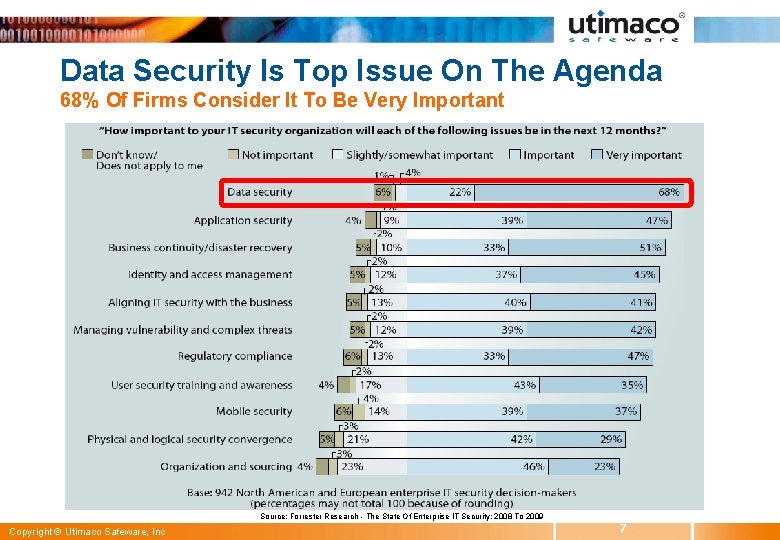
Data Security Is Top Issue On The Agenda 68% Of Firms Consider It To Be Very Important Source: Forrester Research - The State Of Enterprise IT Security: 2008 To 2009 Copyright © Utimaco Safeware, Inc 7

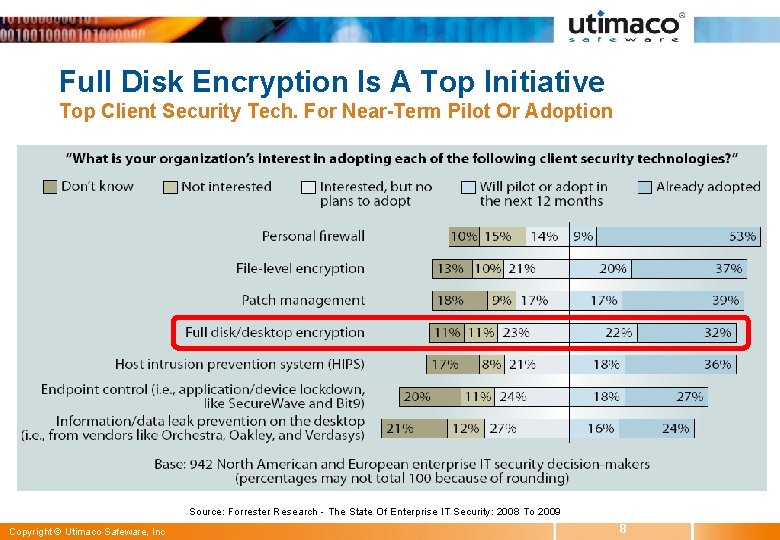
Full Disk Encryption Is A Top Initiative Top Client Security Tech. For Near-Term Pilot Or Adoption Source: Forrester Research - The State Of Enterprise IT Security: 2008 To 2009 Copyright © Utimaco Safeware, Inc 8

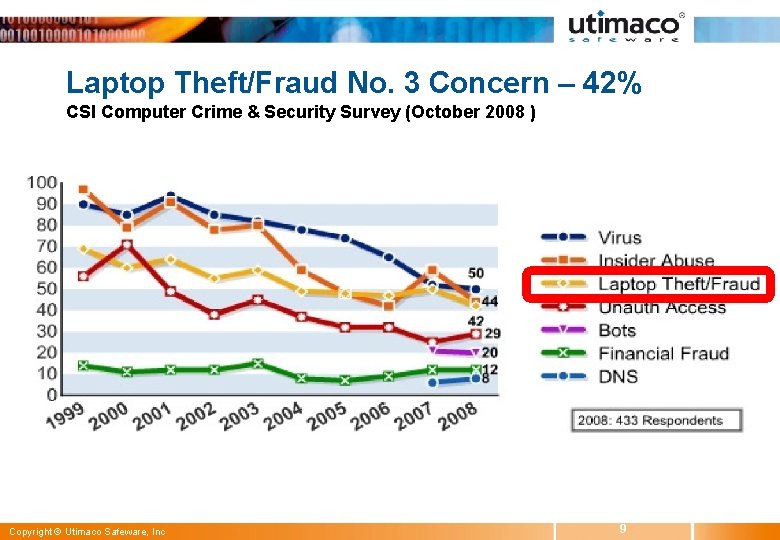
Laptop Theft/Fraud No. 3 Concern – 42% CSI Computer Crime & Security Survey (October 2008 ) Copyright © Utimaco Safeware, Inc 9

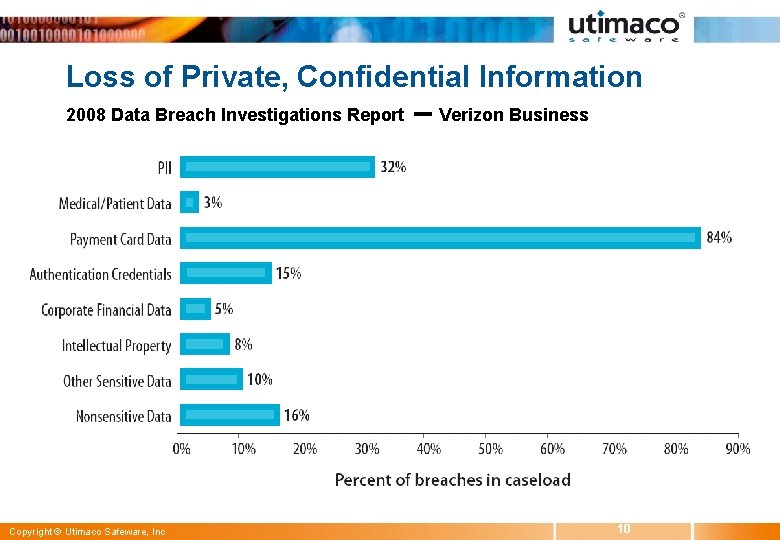
Loss of Private, Confidential Information 2008 Data Breach Investigations Report Copyright © Utimaco Safeware, Inc -- Verizon Business 10

Data Security Solution Requirements Utimaco Customer Surveys…Encryption, And More… 1. Define security roles and responsibilities 2. Enforce consistent polices 3. Provide transparent security to end-users 4. Enable secure data sharing and recovery 5. Allow easy deployment and administration 6. Facilitate quick, on-demand audits Copyright © Utimaco Safeware, Inc 11

Full Disk Encryption (FDE) For Laptops, Desktops and Servers u Encrypts and secures all data on HDD u Enforces pre-boot authentication for users u Secure protection: Power-off, hibernation w Confidentiality of IP w Protection of privacy w Compliance w/ policy & regulations Copyright © Utimaco Safeware, Inc 12

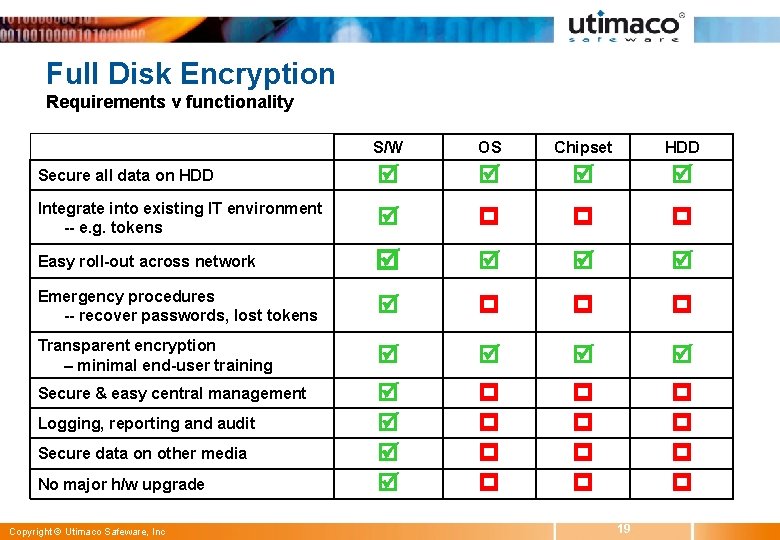
FDE Requirements Protect all data on HDD Integrate into existing IT environment (e. g. , tokens) Easy roll-out across enterprise Emergency procedures -- forgotten passwords, lost tokens Transparent encryption, minimal end-user training Easy central management Logging, reporting and audit Copyright © Utimaco Safeware, Inc 13

Existing and Emerging FDE Solutions u S/W based w Early 1990 s w e. g. Utimaco / Safe. Guard u O/S based w November 2006 w e. g. Microsoft / Bit. Locker™ Drive Encryption u Self-encrypting HDDs w 2006 w e. g. Seagate Momentus 5400 FDE. 2 u PC board Chipset-based w Not yet released Copyright © Utimaco Safeware, Inc 14

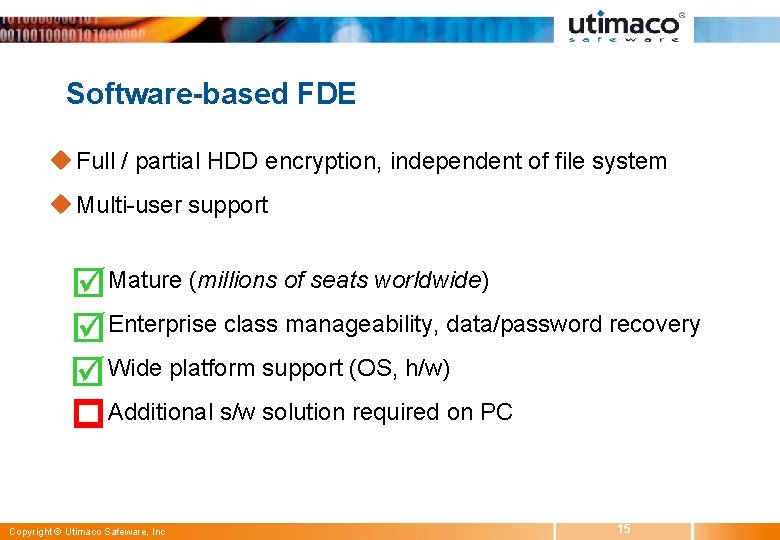
Software-based FDE u Full / partial HDD encryption, independent of file system u Multi-user support w Mature (millions of seats worldwide) w Enterprise class manageability, data/password recovery w Wide platform support (OS, h/w) w Additional s/w solution required on PC Copyright © Utimaco Safeware, Inc 15

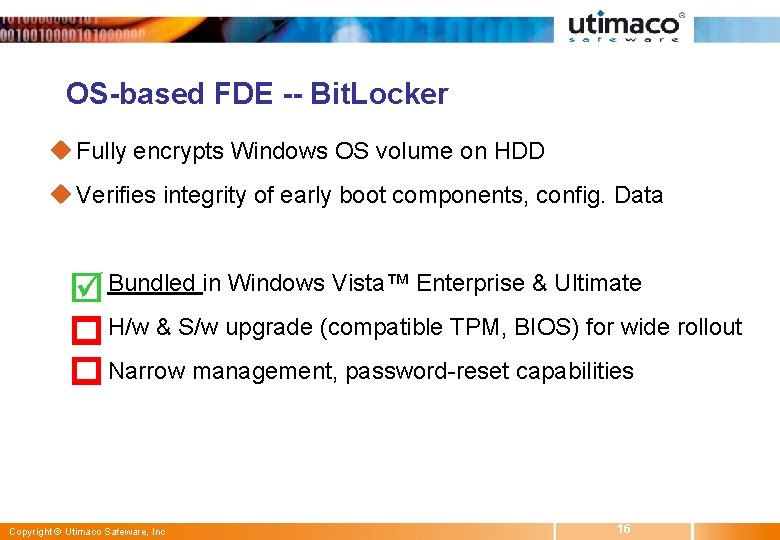
OS-based FDE -- Bit. Locker u Fully encrypts Windows OS volume on HDD u Verifies integrity of early boot components, config. Data w Bundled in Windows Vista™ Enterprise & Ultimate w H/w & S/w upgrade (compatible TPM, BIOS) for wide rollout w Narrow management, password-reset capabilities Copyright © Utimaco Safeware, Inc 16

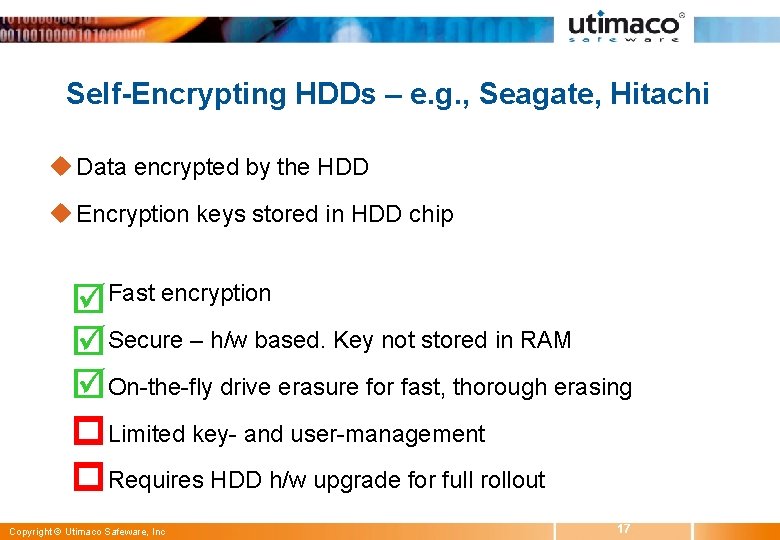
Self-Encrypting HDDs – e. g. , Seagate, Hitachi u Data encrypted by the HDD u Encryption keys stored in HDD chip w Fast encryption w Secure – h/w based. Key not stored in RAM w On-the-fly drive erasure for fast, thorough erasing w Limited key- and user-management w Requires HDD h/w upgrade for full rollout Copyright © Utimaco Safeware, Inc 17

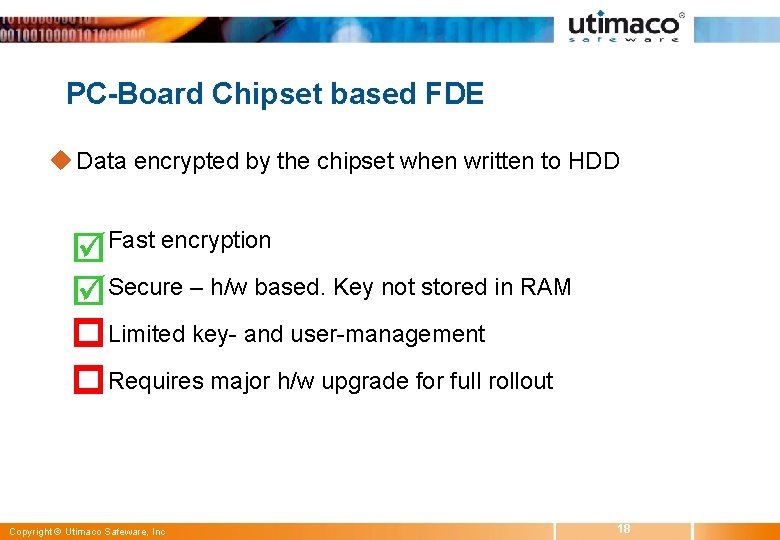
PC-Board Chipset based FDE u Data encrypted by the chipset when written to HDD w Fast encryption w Secure – h/w based. Key not stored in RAM w Limited key- and user-management w Requires major h/w upgrade for full rollout Copyright © Utimaco Safeware, Inc 18

Full Disk Encryption Requirements v functionality S/W OS Chipset HDD Secure all data on HDD Integrate into existing IT environment -- e. g. tokens Easy roll-out across network Emergency procedures -- recover passwords, lost tokens Transparent encryption – minimal end-user training Secure & easy central management Logging, reporting and audit Secure data on other media No major h/w upgrade Copyright © Utimaco Safeware, Inc 19

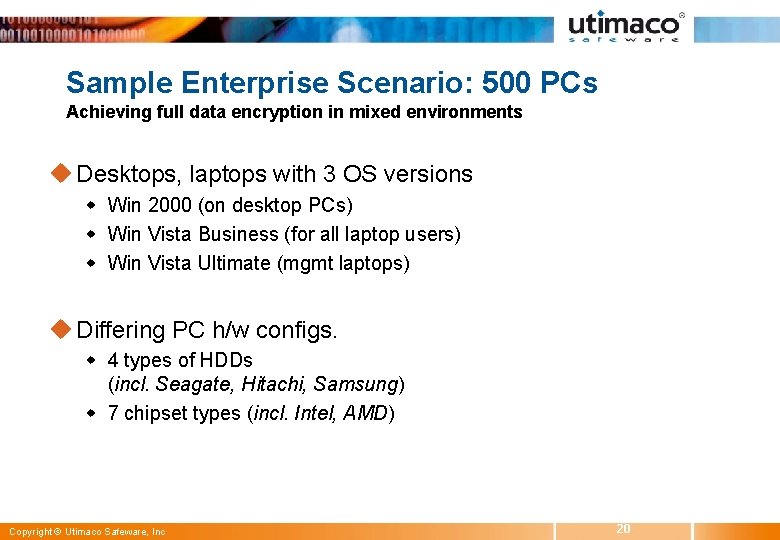
Sample Enterprise Scenario: 500 PCs Achieving full data encryption in mixed environments u Desktops, laptops with 3 OS versions w Win 2000 (on desktop PCs) w Win Vista Business (for all laptop users) w Win Vista Ultimate (mgmt laptops) u Differing PC h/w configs. w 4 types of HDDs (incl. Seagate, Hitachi, Samsung) w 7 chipset types (incl. Intel, AMD) Copyright © Utimaco Safeware, Inc 20

Challenges with Emerging Solutions 1. Emergency procedures – password recovery, lost tokens 2. Integrate w/ existing IT environment: AD, PKI, tokens 3. Central Administration & key management w w Using existing definitions (e. g. users, keys, roles) Separation of duties 4. Limited logs and reports for audits 5. Securing data stored on other media: encryption of w w w Removable media (incl. USB sticks, CD/DVD) Files stored on servers, Emails Copyright © Utimaco Safeware, Inc 21

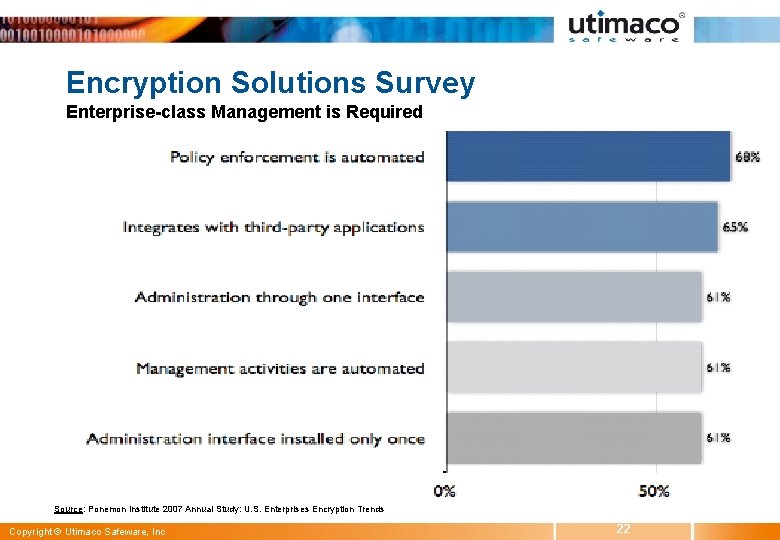
Encryption Solutions Survey Enterprise-class Management is Required Source: Ponemon Institute 2007 Annual Study: U. S. Enterprises Encryption Trends Copyright © Utimaco Safeware, Inc 22

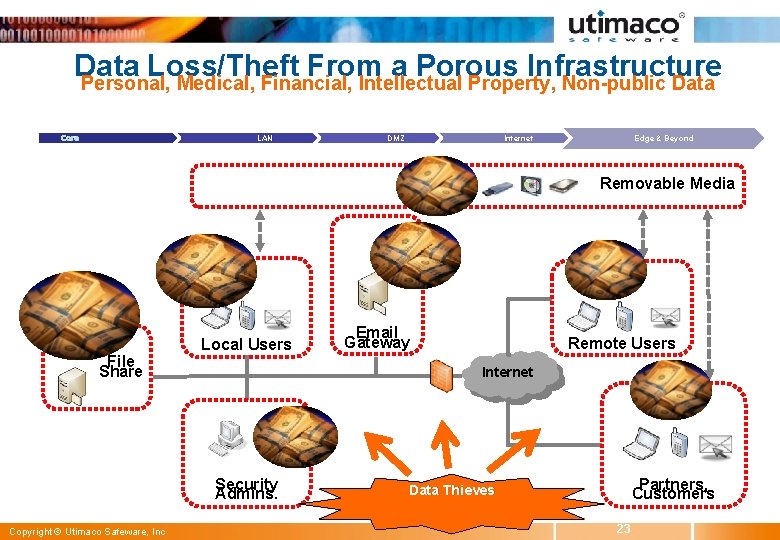
Data Loss/Theft From a Porous Infrastructure Personal, Medical, Financial, Intellectual Property, Non-public Data Core LAN DMZ Edge & Beyond Internet Removable Media Central Management Server File Share Email gateway Local Users Gateway Remote Users Internet Security Admins. Copyright © Utimaco Safeware, Inc Email Encryption Email Partners, Customers Data Thieves 23

Thank you. Q & A Rob Mac. Intosh robert. macintosh@utimaco. com 480 -726 -0020 Copyright © Utimaco Safeware, Inc 24