Protection and Security Andy Wang Operating Systems COP






























- Slides: 42

Protection and Security Andy Wang Operating Systems COP 4610 / CGS 5765

Definitions n Security: policy of authorizing accesses ¡ n Prevents intentional misuses of a system Protection: the actual mechanisms implemented to enforce the specialized policy ¡ Prevents either accidental or intentional misuses

Security Goals n n n Data confidentiality: secret data remains secret Data integrity: unauthorized users should not be able to modify data System availability: nobody can make a system unusable

Security Components n n n Authentication determines who the user is Authorization determines who is allowed to do what Enforcement makes it so people can do only what they are allowed to do

Authentication n The most common approach: passwords ¡ n If I know the secret, the machine can assume that I’m the user Problems: 1. Password storage 2. Poor passwords

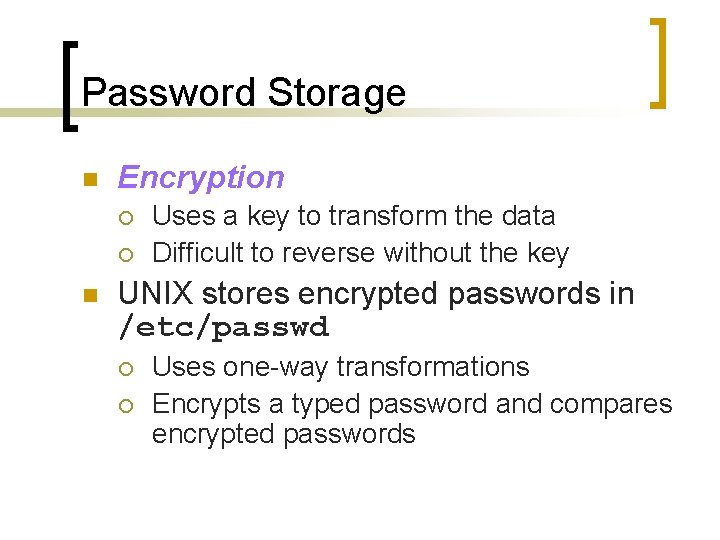
Password Storage n Encryption ¡ ¡ n Uses a key to transform the data Difficult to reverse without the key UNIX stores encrypted passwords in /etc/passwd ¡ ¡ Uses one-way transformations Encrypts a typed password and compares encrypted passwords

Poor Passwords n Short passwords ¡ n Easy to crack Long passwords ¡ Tend to be written down somewhere

Original UNIX n n Required only lower-case, 5 -lettered passwords 265 or 1 million combinations ¡ ¡ In 1975, it would take one day to crack one password Today, we can go through all those combinations < 1 second

Partial Solutions n n Extend password with a unique number Require more complex passwords ¡ ¡ ¡ 6 letters of upper, lower cases, numbers, and special characters 706 or 100 billion combinations Unfortunately, people still pick common words

Partial Solutions n n Delay every login by 1 second Assign very long passwords ¡ ¡ Give everyone a calculator (ATM card) Requires a physical theft to steal the password

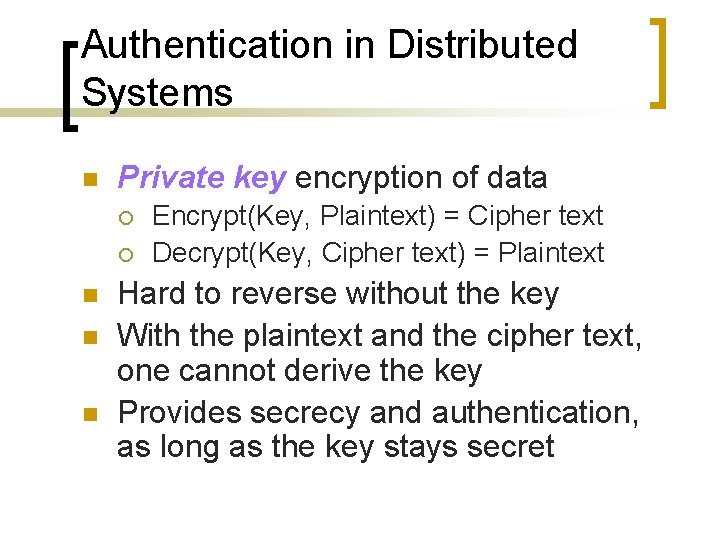
Authentication in Distributed Systems n Private key encryption of data ¡ ¡ n n n Encrypt(Key, Plaintext) = Cipher text Decrypt(Key, Cipher text) = Plaintext Hard to reverse without the key With the plaintext and the cipher text, one cannot derive the key Provides secrecy and authentication, as long as the key stays secret

How to distribute the keys? n Authentication server ¡ Keeps a list of keys

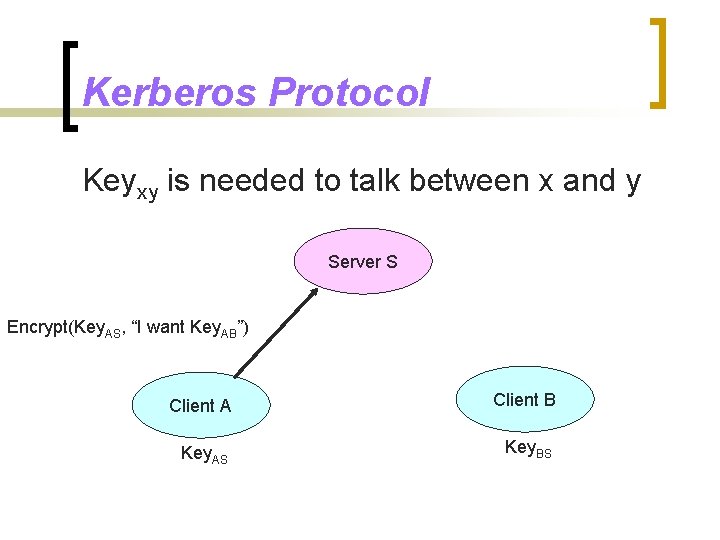
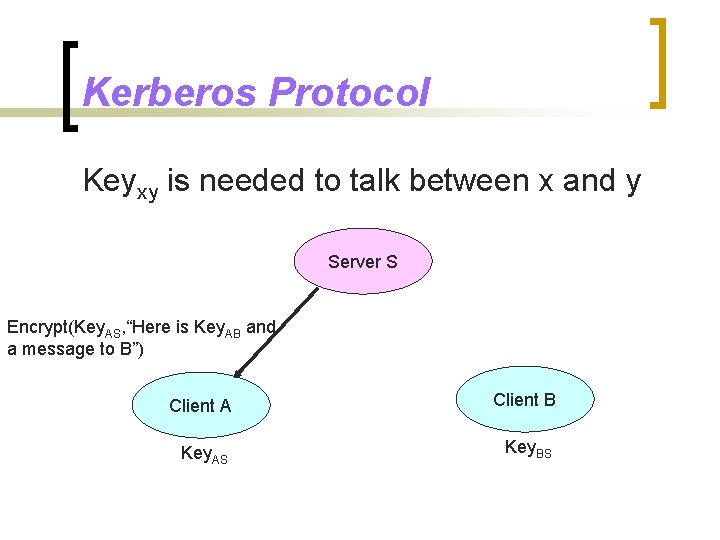
Kerberos Protocol Keyxy is needed to talk between x and y Server S Encrypt(Key. AS, “I want Key. AB”) Client A Client B Key. AS Key. BS

Kerberos Protocol Keyxy is needed to talk between x and y Server S Encrypt(Key. AS, “Here is Key. AB and a message to B”) Client A Client B Key. AS Key. BS

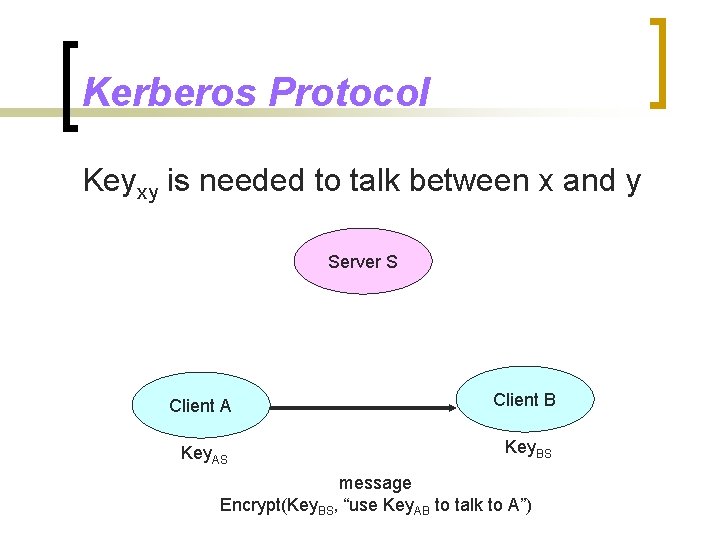
Kerberos Protocol Keyxy is needed to talk between x and y Server S Client A Client B Key. AS Key. BS message Encrypt(Key. BS, “use Key. AB to talk to A”)

Additional Details n Expiration timestamp for a key ¡ n Checksum for an encrypted message ¡ n Prevents a machine from replaying messages (e. g. , “deposit $100”) Prevents modifications to a message (e. g. , “deposit $1000”) Key. AS and Key. BS are renewed periodically to reduce their exposures

Public Key Encryption n n Separates authentication from secrecy Involves a public key and private key ¡ ¡ Encrypt(Keypublic, plaintext) = cipher text Decrypt(Keyprivate, cipher text) = plaintext Encrypt(Keyprivate, plaintext) = cipher text Decrypt(Keypublic, cipher text) = plaintext

Public Key Encryption n Idea: ¡ ¡ Private key is kept secret Public key is advertised

Public Key Encryption n Encrypt(Keymy_public, “Hi, Andy”) ¡ n Anyone can create it, but only I can read it (secrecy) Encrypt(Keymy_private, “I’m Andy”) ¡ Everyone can read it, but only I can create it (authentication)

Public Key Encryption n Encrypt(Keyyour_public, Encrypt(Keymy_private, “I know your secret”)) ¡ Only I can create it, and only you can read it

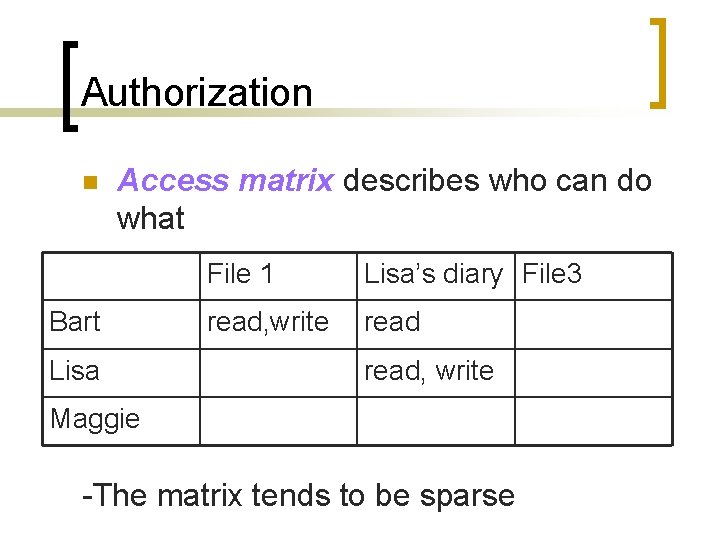
Authorization n Access matrix describes who can do what Bart Lisa File 1 Lisa’s diary File 3 read, write Maggie -The matrix tends to be sparse

Access Control List n n Stores all permissions for all users with each object Analogy: a guard in front of a door ¡ n Checks for a list of people allowed to enter UNIX: permission of each file is specified according to its owner, group, and the world

Capability List n n Stores all objects a process can touch Analogy: Keys ¡ n A key owner has the right of entry Example: page tables ¡ Each process has a list of pages that it can access

Access Control List vs. Capability List n Access control list (commonly used) ¡ ¡ n Easy to know who can access the object Hard to know which objects a user can access Capability list ¡ ¡ A user knows the list of objects to access Hard to know who can access an object n More difficult to revoke capabilities

Enforcement n n n Enforcer programs check passwords, access control lists, and so on… In UNIX, enforcers are run as superuser If there is a bug, you are hosed!

The State of the World in Security n Authentication ¡ ¡ n Authorization ¡ ¡ n Poor passwords Nobody encrypts emails Coarse-grained access control list Often turned off for sharing Enforcement ¡ Buggy operating systems

Classes of Security Problems n Eavesdropping is the listener approach ¡ ¡ n Tap into the Ethernet and see everything Countermeasure: pressurized cabled Abuse of privilege ¡ If the superuser is evil, there is nothing you can do

Classes of Security Problems n Imposter breaks into the system by pretending to be someone else ¡ ¡ Recorded voice and facial image Countermeasure: behavioral monitoring to look for suspicious activities n Overwriting the boot block

Classes of Security Problems n A Trojan horse is a seemingly innocent program that performs an unexpected function ¡ Countermeasure: integrity checking n Periodically, check binaries against their checksums

Classes of Security Problems n Salami attack builds up an attack, one -bit at a time ¡ ¡ Example: send partial pennies to a bank account Countermeasure: code reviews

Classes of Security Problems n Logic bombs: a programmer may secretly insert a piece of code into the production system ¡ ¡ ¡ A programmer feeds the system password periodically If the programmer is fired, the logic bomb goes off Countermeasure: code reviews

Classes of Security Problems n Denial-of-service attacks aim to reduce system availability ¡ ¡ A handful of machines can flood a victim machine to disrupt its normal use Countermeasure: open

Pentagon Traffic Analysis n Before the 1991 Persian Gulf War ¡ Foreign intelligence tried to predict the starting date of the war time

Pentagon Traffic Analysis n So much for the element of surprise…

Tenex n n Used to be the most popular system at universities before UNIX Thought to be very secure

Tenex n Source code for the password check: for (j = 0; j < 8; j++) { if (input[j] != pw[j]) { // go to error; } } n Need to go through 2568 combinations

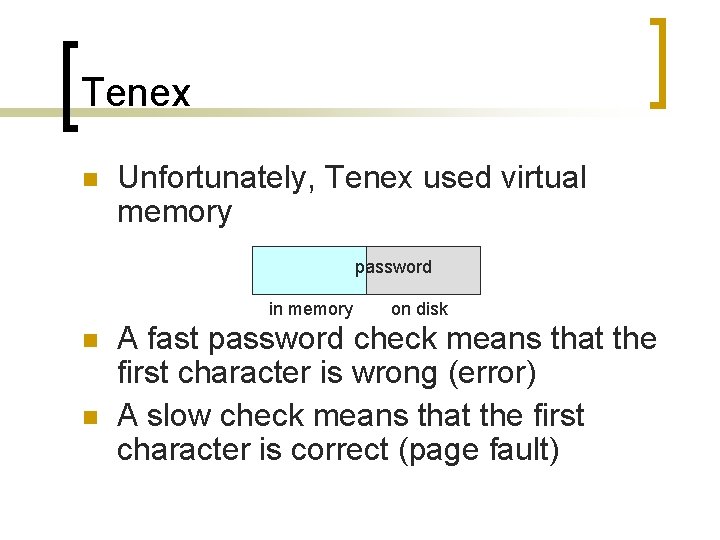
Tenex n Unfortunately, Tenex used virtual memory password in memory n n on disk A fast password check means that the first character is wrong (error) A slow check means that the first character is correct (page fault)

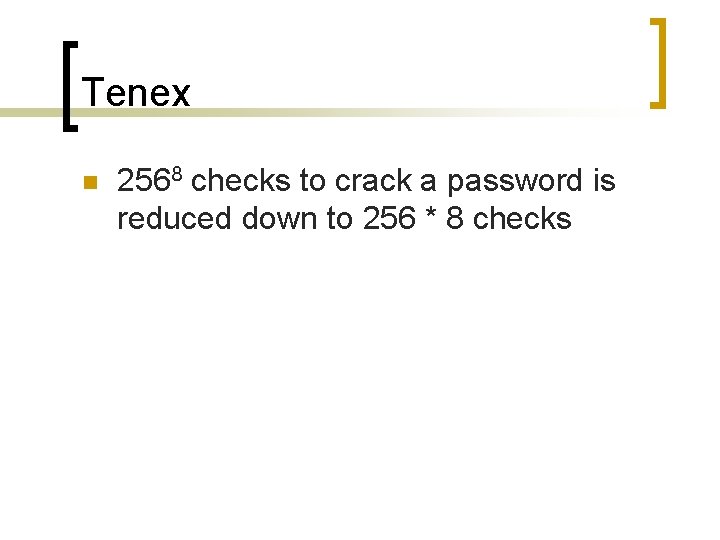
Tenex n 2568 checks to crack a password is reduced down to 256 * 8 checks

The Internet Worm n n In 1988, a Cornell graduate student, RTM, released a worm into the Internet The worm used three attacks ¡ ¡ ¡ rsh fingerd sendmail

The Internet Worm n Some machines trust other machines, the use of rsh was sufficient to get into a remote machine without authentication

The Internet Worm n finger command did not check the input buffer size ¡ finger name@location ¡ Overflow the buffer Overwrite the return address of a procedure Jump and execute a shell (under root privilege) ¡ ¡

The Internet Worm n sendmail allowed the worm to mail a copy of the code and get it executed n The worm was caught due to multiple infections ¡ People noticed the high CPU load