Protection and Security 1 Protection and Security Operating









































- Slides: 74

Protection and Security 1

Protection and Security • Operating system consists of a collection of objects, hardware or software • Each object has a unique name and can be accessed through a well-defined set of operations (hopefully) • Protection and security problem - ensure that each object is accessed correctly and only by those processes of authorized users that are allowed to do so 2

Protection and Security – cont. • OS designer faces challenge of creating a protection scheme that cannot be bypassed by any software that may be created in the future • Networking adds to the problem as it allows access to a computer and its resources without being in the same physical location • See next frame 3

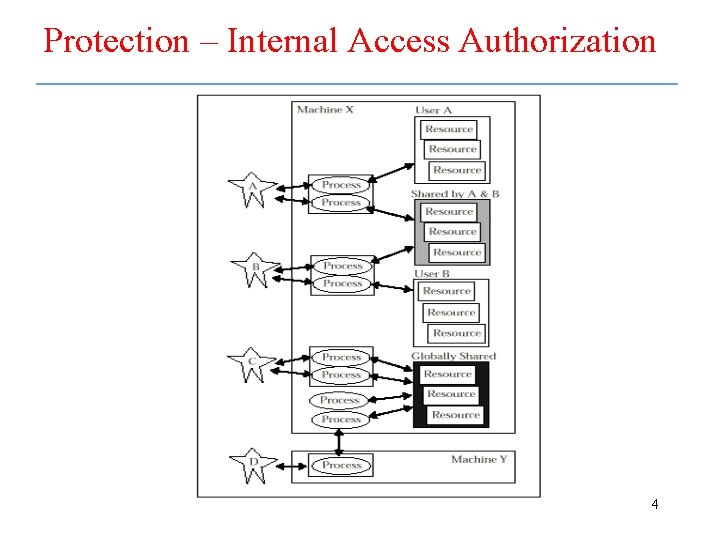
Protection – Internal Access Authorization 4

Policy vs. Mechanism • An organization’s security policy defines the rules for authorizing access to its computers and information resources – A particular strategy that dictates the way a mechanism is used to achieve specific goals • Protection mechanisms are tools for implementing the organization’s security policy 5

Policy & Mechanism • A security policy is a strategy that dictates the way a mechanism is used to achieve a specific goal – Accountants have access to payroll files – OS processes have access to the page table – Client process has access to information provided by a server • A protection mechanism is a set of components used to implement any one of different sets of strategies – Authentication – Authorization – Cryptography 6

Policy & Mechanism – cont. • Example - Computers in lab – Policy: can only be used by students registered for graduate classes – Mechanism: authentication via username and password; set up via class list and request – Policy: students may only have N bytes of storage space – Mechanism: establish a quota system on disk 7

Policy & Mechanism – cont. • The security policy specifies the ways resources should be shared among members of the organization and with members external to the organization • The mechanism is the specific steps and tools provided by the system to enforce the policy 8

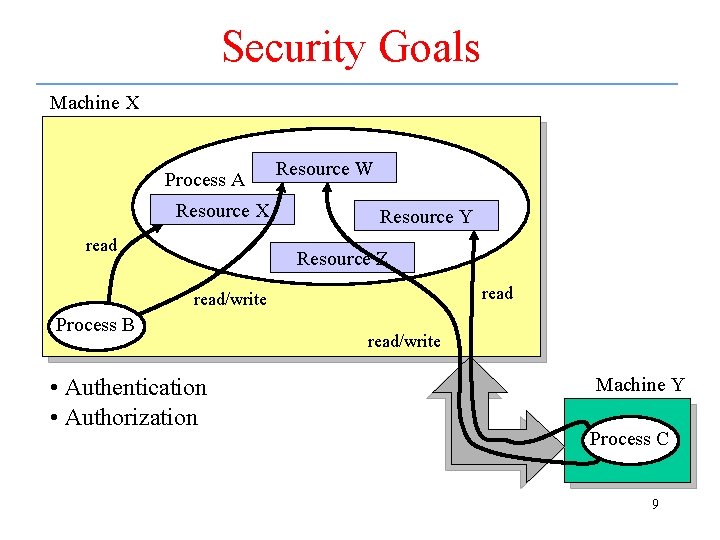
Security Goals Machine X Process A Resource X read Resource W Resource Y Resource Z read/write Process B • Authentication • Authorization read/write Machine Y Process C 9

Implementing Policy & Mechanism • Policies selected by system administrators – after the OS and protection mechanisms have been designed and implemented • OS designer must foresee all the policies that may be selected and implement the mechanisms accordingly • Very difficult task – usually handled by sending out patches as security holes are found 10

The Security Problem • Security must consider external environment of the system, and protect it from – unauthorized access. – malicious modification or destruction – accidental introduction of inconsistency. • Easier to protect against accidental than malicious misuse 11

Authentication Mechanisms • Basis of most protection mechanisms • Two types of authentication – External: verify the user • Usually username/password combination • May require two passwords or other identification – Internal: verify the process • Don’t allow one users process to appear to be that of another user • Network access accentuates the problem – Is the computer who it says it is? 12

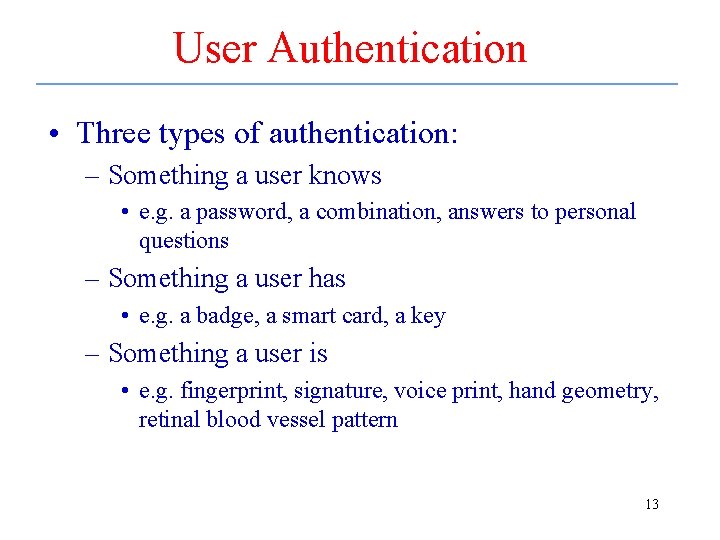
User Authentication • Three types of authentication: – Something a user knows • e. g. a password, a combination, answers to personal questions – Something a user has • e. g. a badge, a smart card, a key – Something a user is • e. g. fingerprint, signature, voice print, hand geometry, retinal blood vessel pattern 13

Authentication • User identity most often established through passwords, can be considered a special case of either keys or capabilities. • Passwords must be kept secret. – Frequent change of passwords. – Use of “non-guessable” passwords. – Log all invalid access attempts. • Encryption 14

User Authentication • Possible mechanisms – Recognize repeated login attempts • Disconnect after some threshold is reached • Disregard correct passwords after some threshold of failures has been reached • Make login process slow – handle computer generated attempts 15

Network Authentication • Need to be able to communicate between computers without significantly increasing the overhead involved • Most typical access is for file transport – Email – Messages – File downloading – Obtaining network services 16

Program Threats • Trojan Horse – Code segment that misuses its environment. – Exploits mechanisms for allowing programs written by users to be executed by other users. • Trap Door – Specific user identifier or password that circumvents normal security procedures. – Could be included in a compiler. 17

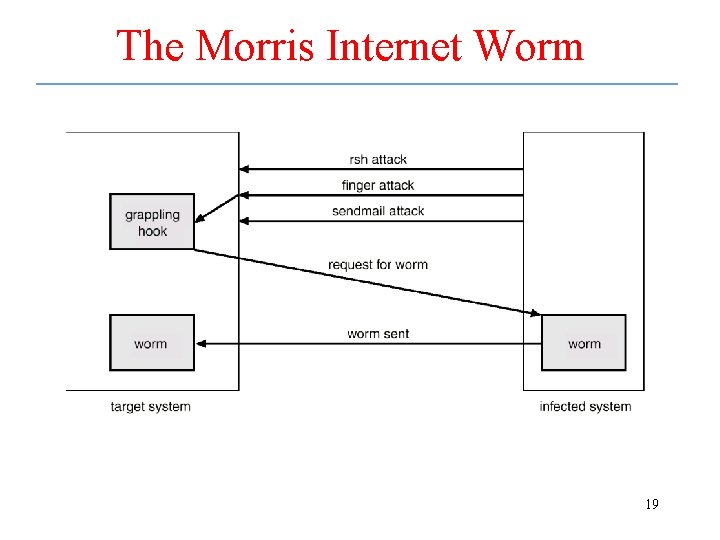
System Threats • Worms – use spawn mechanism; standalone program • Internet worm – Exploited UNIX networking features (remote access) and bugs in finger and sendmail programs. – Grappling hook program uploaded main worm program. • Viruses – fragment of code embedded in a legitimate program. – Mainly effect microcomputer systems. – Downloading viral programs from public bulletin boards or exchanging floppy disks containing an infection. – Safe computing. 18

The Morris Internet Worm 19

The confinement problem • How do we prevent a program from leaking information to others? • It is not as simple as preventing IPC and I/O • A covert channel is a hidden means of communication information – e. g. sending bits by manipulating the CPU load 20

Threat Monitoring • Check for suspicious patterns of activity – i. e. , several incorrect password attempts may signal password guessing. • Audit log – records the time, user, and type of all accesses to an object; useful for recovery from a violation and developing better security measures. • Scan the system periodically for security holes; done when the computer is relatively unused. 21

Threat Monitoring – cont. • Check for: – – – – Short or easy-to-guess passwords Unauthorized set-uid programs Unauthorized programs in system directories Unexpected long-running processes Improper directory protections Improper protections on system data files Dangerous entries in the program search path (Trojan horse) – Changes to system programs: monitor checksum values 22

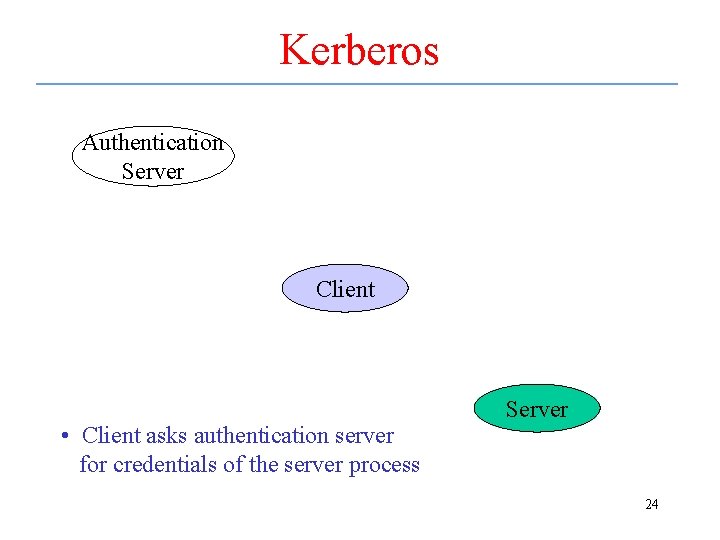
Kerberos Network Authentication • A set of network protocols used to authenticate access to a computer by a user at a different computer using an unsecure network • Assumes information over network could be tampered with • Does not assume OS on either machine is secure • Developed at MIT in 80’s; widely used 23

Kerberos Authentication Server Client • Client asks authentication server for credentials of the server process Server 24

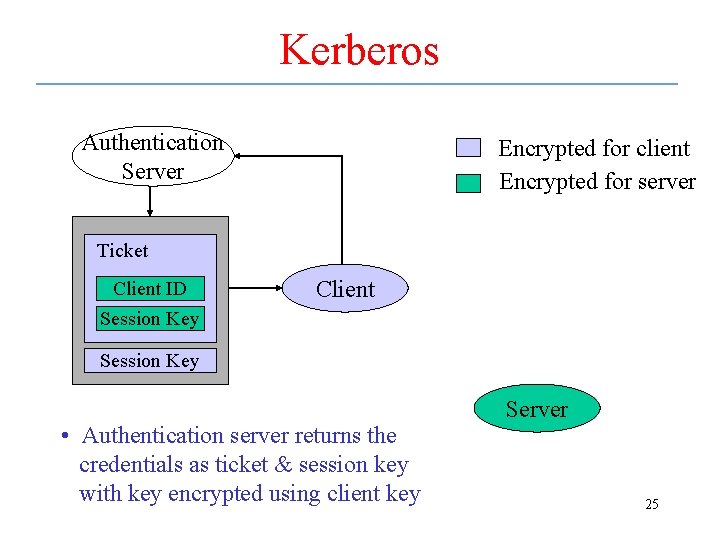
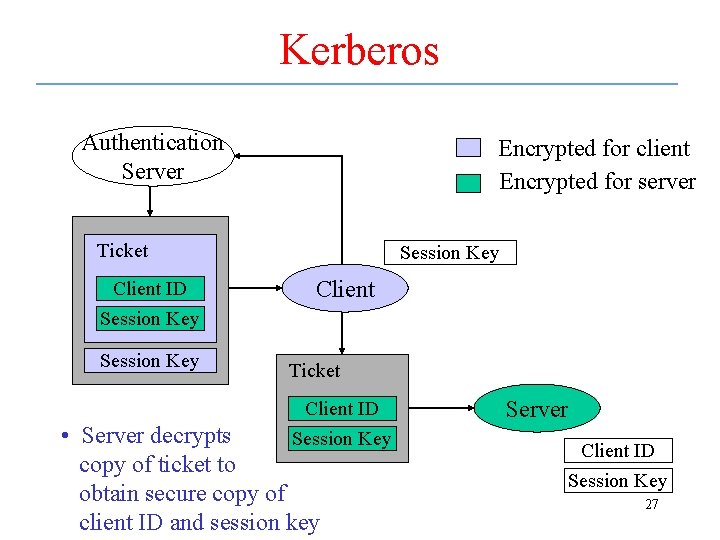
Kerberos Authentication Server Encrypted for client Encrypted for server Ticket Client ID Session Key Client Session Key • Authentication server returns the credentials as ticket & session key with key encrypted using client key Server 25

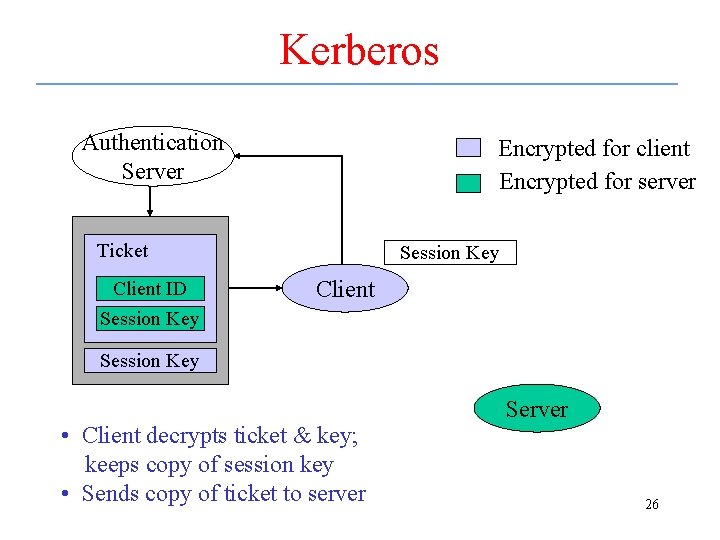
Kerberos Authentication Server Encrypted for client Encrypted for server Ticket Client ID Session Key Client Session Key • Client decrypts ticket & key; keeps copy of session key • Sends copy of ticket to server Server 26

Kerberos Authentication Server Encrypted for client Encrypted for server Ticket Client ID Session Key Client Ticket Client ID Session Key • Server decrypts copy of ticket to obtain secure copy of client ID and session key Server Client ID Session Key 27

Kerberos Authentication • Once these steps completed, client and server processes both have copy of session key and can begin secure communication • Authentication server MUST be trusted – It has copy of client’s ID, knows how to encrypt info that only client can decrypt, knows how to encrypt info that only server can decrypt, and can create unique session key 28

Authorization • Is this user/process allowed to access the resource under the current policy? • What type of access is allowable? – Read – Write – Execute – Append 29

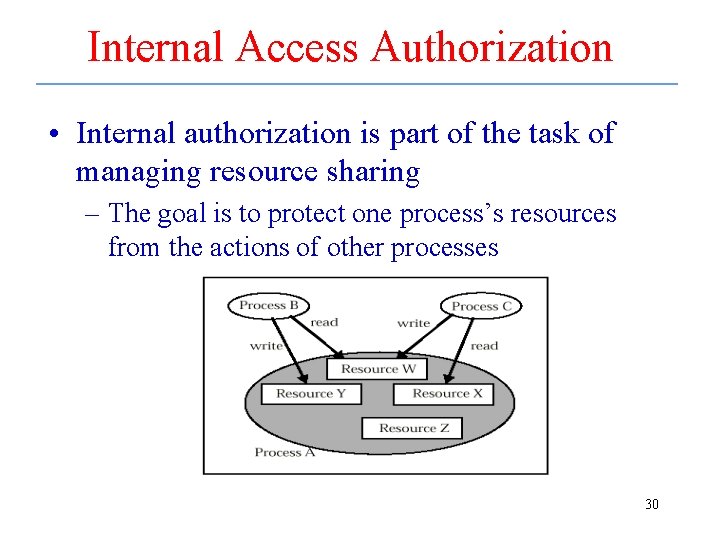
Internal Access Authorization • Internal authorization is part of the task of managing resource sharing – The goal is to protect one process’s resources from the actions of other processes 30

Protection Problems • Sharing parameters – Process calls procedure in another process’s address space, which then modifies parameters, so that when original process regains control, variables in its address space have been changed • Confinement – Contain all rights to resources so that they do not propagate outside some chosen set of processes 31

Protection Problems – cont. • Allocating rights – A process provides another process with specific rights to use its resources; should be a temporary allocation; but what if 2 nd process passes those rights on to other processes without knowledge or permission of original process (the owner of the resource) • Trojan horse – Special case of allocating rights: client process invokes a service program which then takes advantage of the client’s process rights 32

Lampson’s Protection Model • Active parts (e. g. , processes or threads) – Act on behalf of users – Operate in different protection domains • The set of rights a process has at any given time – Subject is a process executing in a specific domain • Passive parts are called objects – Correspond to resources – NOTE: not related to OOP terminology 33

Model • Want mechanism to implement different security policies for subjects to access objects – Many different policies must be possible – Policy may change over time 34

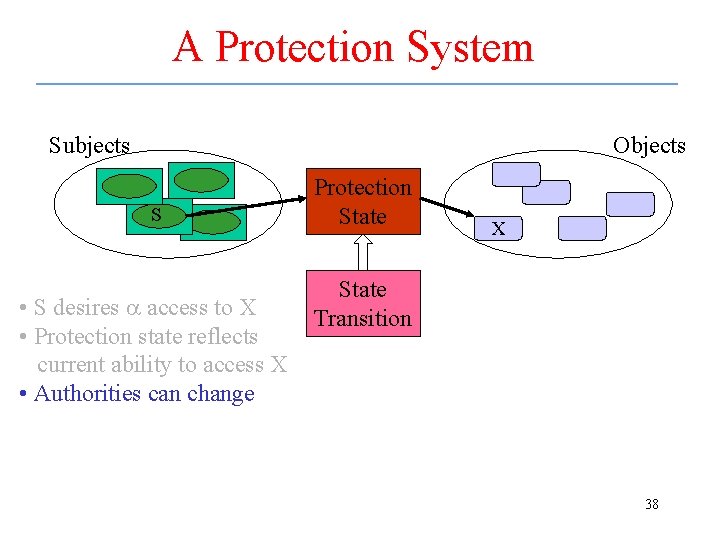
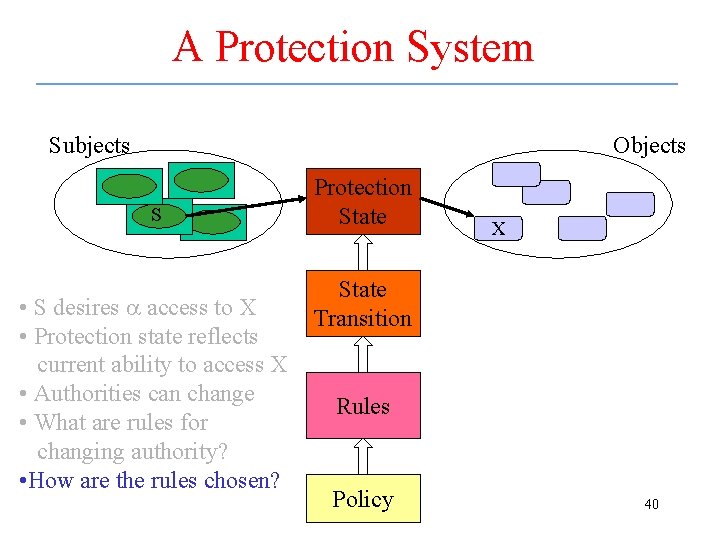
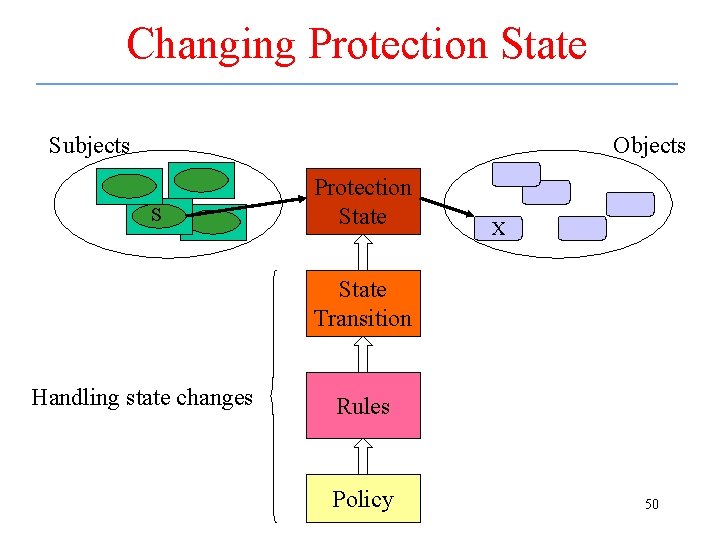
Protection System • Composed of – Set of objects – Set of subjects – Set of rules specifying protection policy • Represents accessibility of objects by subjects • Guarantees that the protection state is checked for each access of an object by a subject 35

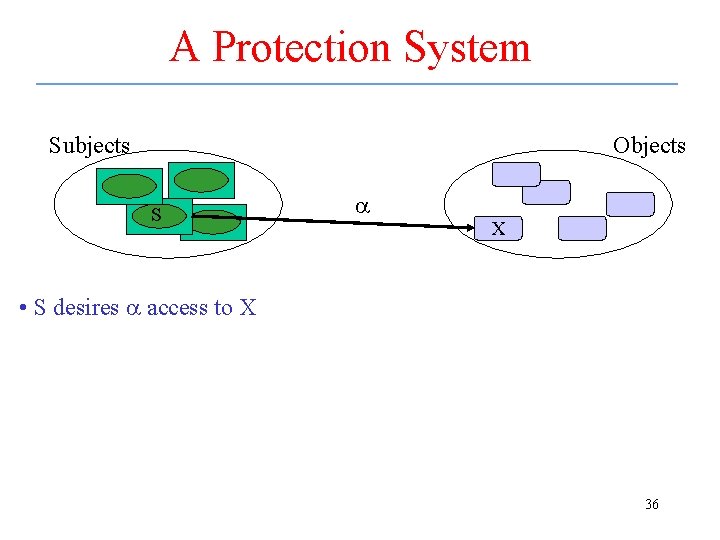
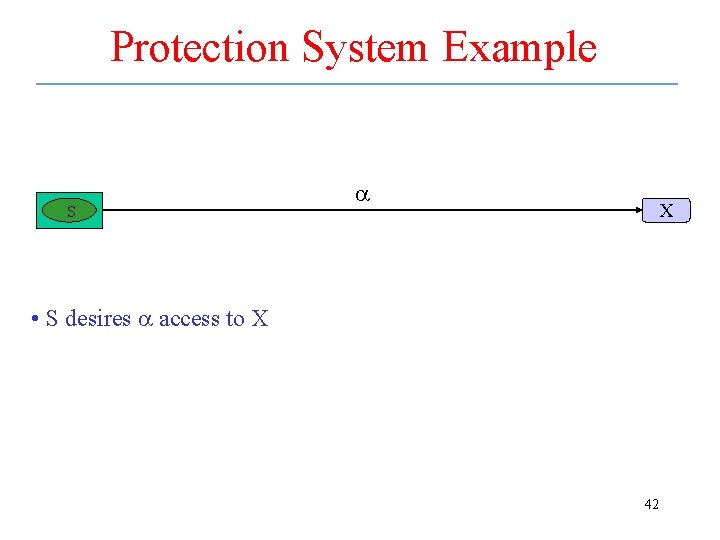
A Protection System Subjects Objects S a X • S desires a access to X 36

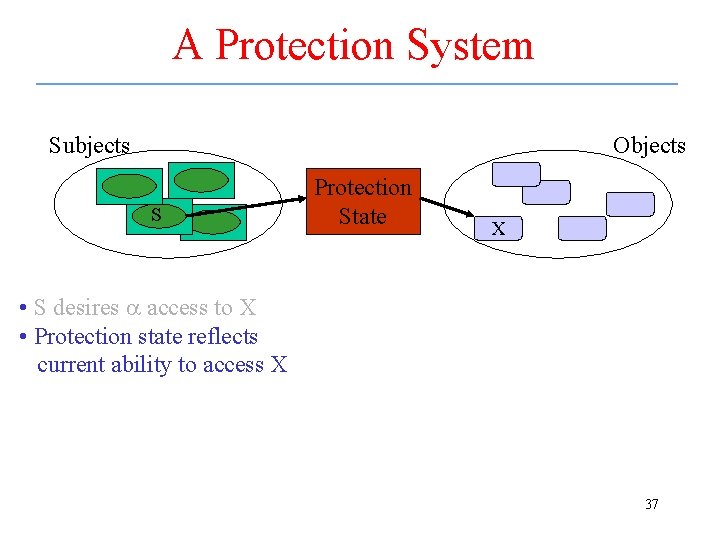
A Protection System Subjects Objects S Protection State X • S desires a access to X • Protection state reflects current ability to access X 37

A Protection System Subjects Objects S • S desires a access to X • Protection state reflects current ability to access X • Authorities can change Protection State X State Transition 38

A Protection System Subjects Objects S • S desires a access to X • Protection state reflects current ability to access X • Authorities can change • What are rules for changing authority? Protection State X State Transition Rules 39

A Protection System Subjects Objects S • S desires a access to X • Protection state reflects current ability to access X • Authorities can change • What are rules for changing authority? • How are the rules chosen? Protection State X State Transition Rules Policy 40

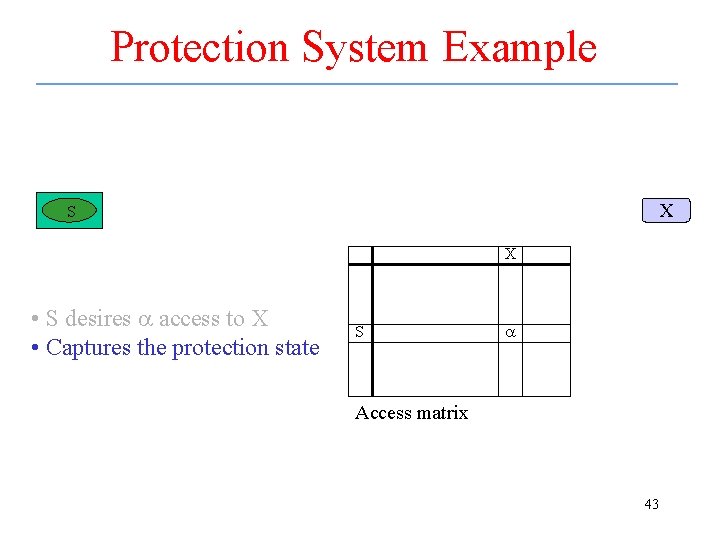
Access Matrix • The protection state can be represented using an access matrix – An access matrix A has one row for each subject and one column for each object • Note: subjects are also objects (processes controlling processes) – Each entry A[S, X] is a set that describes the access rights held by subject S to object X • Access authentication – If subject S initiates type a access to X then if a A[S, X], the access is valid. If a A[S, X], the access is invalid. 41

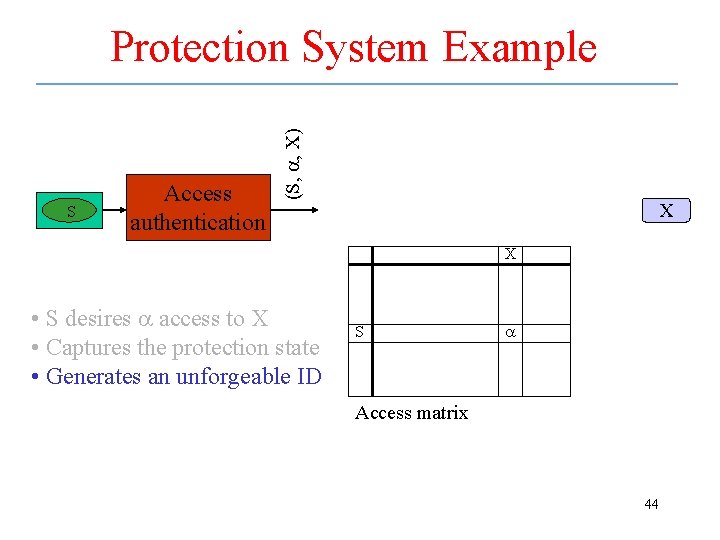
Protection System Example S a X • S desires a access to X 42

Protection System Example X S X • S desires a access to X • Captures the protection state S a Access matrix 43

S Access authentication (S, a, X) Protection System Example X X • S desires a access to X • Captures the protection state • Generates an unforgeable ID S a Access matrix 44

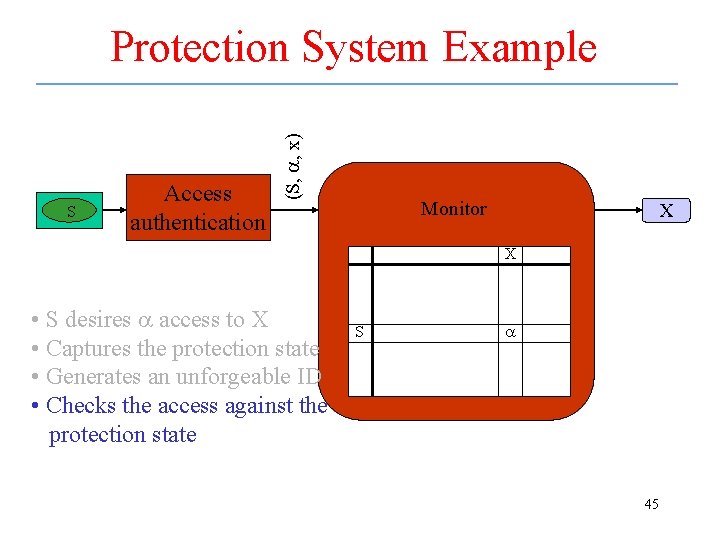
S Access authentication (S, a, x) Protection System Example Monitor X X • S desires a access to X • Captures the protection state • Generates an unforgeable ID • Checks the access against the protection state S a 45

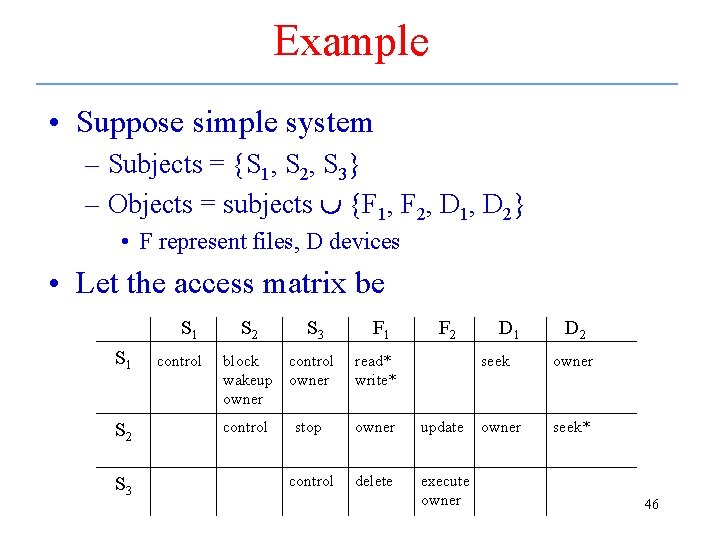
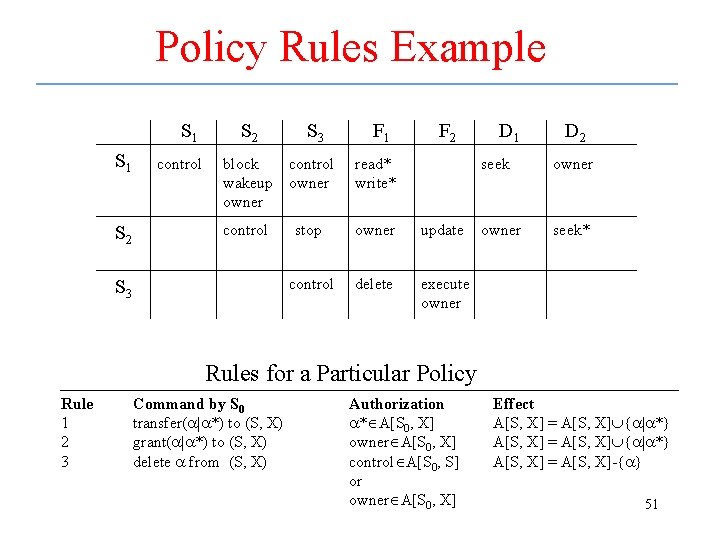
Example • Suppose simple system – Subjects = {S 1, S 2, S 3} – Objects = subjects {F 1, F 2, D 1, D 2} • F represent files, D devices • Let the access matrix be S 1 S 2 S 3 control S 2 S 3 F 1 F 2 block wakeup owner control owner read* write* control stop owner update control delete execute owner D 1 D 2 seek owner seek* 46

Example – cont. • The * is called a copy flag • It allows the process to transfer an access right to another process 47

Example – cont. • If S 2 attempts to update access to F 2 – It initiates access – Causing protection system to create record of form (S 2, update, F 2) – Record given to monitor for F 2 – Monitor checks access table – Since access is valid, S 2 is allowed to update F 2 48

Example – cont. • If S 2 attempts execute access to F 2 – It initiates access – Causing protection system to create record of form (S 2, execute, F 2) – Record given to monitor for F 2 – Monitor checks access table – Since access is invalid, S 2 is not allowed to execute F 2 – Violation is reported to OS 49

Changing Protection State Subjects Objects S Protection State X State Transition Handling state changes Rules Policy 50

Policy Rules Example S 1 S 2 control S 2 S 3 block wakeup owner control owner read* write* control stop owner update control delete execute owner S 3 F 1 F 2 D 1 D 2 seek owner seek* Rules for a Particular Policy Rule 1 2 3 Command by S 0 transfer(a|a*) to (S, X) grant(a|a*) to (S, X) delete a from (S, X) Authorization a* A[S 0, X] owner A[S 0, X] control A[S 0, S] or owner A[S 0, X] Effect A[S, X] = A[S, X] {a|a*} A[S, X] = A[S, X]-{a} 51

Policy Rules Example • The policy rules determine who controls the propagation of the various types of access • Access may be – Transferred: process must have copy flag for right – Granted: process must be owner of object » Don’t need copy flag – Deleted: process must own or control object • Example: rule 1 determines what rights can be transferred from one process to another • Command: transfer(a|a*) to (S, X) • Authorization: a* A[S 0, X] – S 1 can transfer read or read* access to S 2 or S 3 for F 1 because S 1 has the copy flag set 52

Protection State • The copy flag and rules are designed to prevent indiscriminate propagation of access rights among subjects • Right can only be propagated when owner transfers copy flag to another subject – Subject may then transfer right with or without copy flag – This transfer may be nondestructive (first subject keeps access) or destructive (first subject loses access) 53

Results of Rules • These rules (along with a few others) define a protection system that addresses the problems mentioned earlier: – Masquerading: subject must be authenticated and given unforgeable signature – Confinement and allocating rights: rights are restricted to a designated set of subjects • An untrusted subsystem must be memoryless (confined with respect to its ability to retain information or leak it to other subjects) 54

Results of Rules – cont. – Sharing of parameters: allow only indirect access to objects by untrusted subjects • Create gatekeeper subject to protect object from unwanted accesses by untrusted subjects – Trojan horses: problem caused by process assuming rights of another while acting on its behalf • this model distinguishes between two processes using the same rights on different subjects • Many rule sets may solve problem for specific policies, but don’t guarantee solution independent of policy 55

Cost of Protection Mechanisms • Basic protection model requires that each resource access be passed through a monitor before request can be granted • This may introduce a substantial performance cost • Need to decide if performance hit is justified • If information MUST be secure, the cost of performance is not an issue 56

Implementing Internal Authorization • Protection model describes logical set of components that can be used – What implementations are cost effective? – How can an access matrix be implemented efficiently? • Need to consider – Access matrix not only possible representation – Access matrix must be secured; only read and written by selected processes – Goal is to route all accesses through protection monitor – Protection system should be able to authenticate the source of each request – Monitor must be protected process to implement the rules • Must not be possible for other subjects to compromise monitor 57

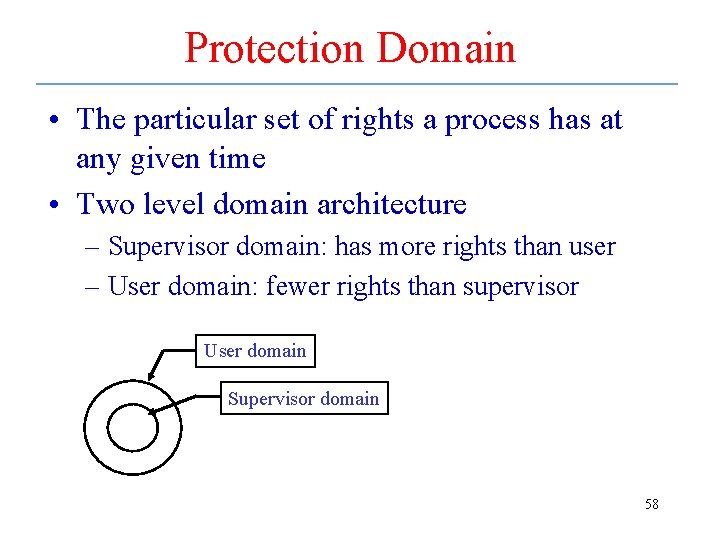
Protection Domain • The particular set of rights a process has at any given time • Two level domain architecture – Supervisor domain: has more rights than user – User domain: fewer rights than supervisor User domain Supervisor domain 58

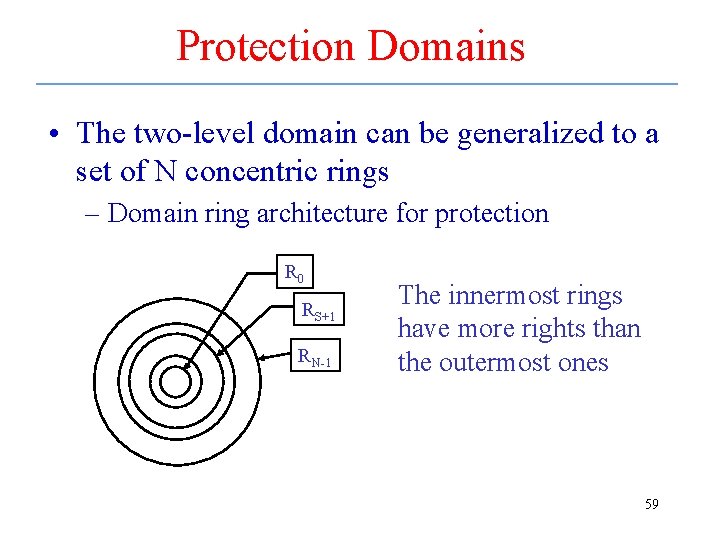
Protection Domains • The two-level domain can be generalized to a set of N concentric rings – Domain ring architecture for protection R 0 RS+1 RN-1 The innermost rings have more rights than the outermost ones 59

Protection Domains – cont. • Inner rings have higher authority – Ring 0 corresponds to supervisor mode – Rings 1 to S have decreasing protection, and are used to implement the OS – Rings S+1 to N-1 have decreasing protection, and are used to implement applications • Lampson model uses processes and domains -- how is a domain implemented? – Supervisor/user hardware mode bit – Software extensions -- rings 60

Protection Domains – cont. • Ring crossing is a domain change • Inner ring crossing rights amplification – Specific gates for crossing – Protected by an authentication mechanism • Outer ring crossing uses less-protected objects – No authentication – Need a return path – Used in Multics and Intel 80386 (& above) hardware 61

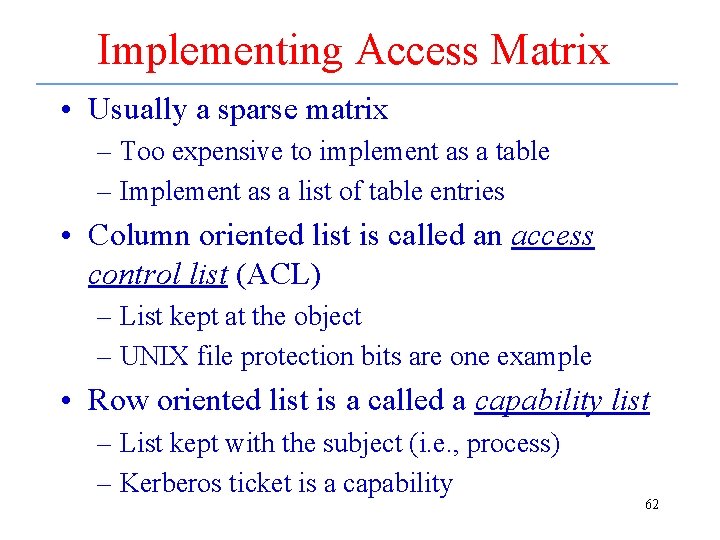
Implementing Access Matrix • Usually a sparse matrix – Too expensive to implement as a table – Implement as a list of table entries • Column oriented list is called an access control list (ACL) – List kept at the object – UNIX file protection bits are one example • Row oriented list is a called a capability list – List kept with the subject (i. e. , process) – Kerberos ticket is a capability 62

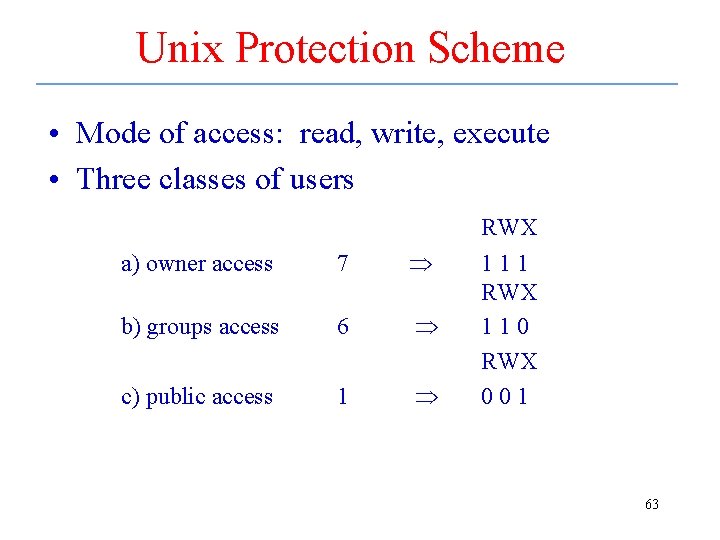
Unix Protection Scheme • Mode of access: read, write, execute • Three classes of users RWX a) owner access 7 b) groups access 6 c) public access 1 111 RWX 110 RWX 001 63

Protection Domains • A capability is a unique, global name for an access right to an object in the system • A protection domain is a set of capabilities to perform certain actions on certain objects • A process can move from protection domain to protection domain so, at any point, it has exactly the capabilities it needs for the current job (the principle of least privilege) • This is more flexible than associating capabilities directly with a process 64

More on Capabilities • Provides an address to object from a very large address space • Possession of a capability represents authorization for access • Implied properties: – Capabilities must be very difficult to guess – Capabilities must be unique and not reused – Capabilities must be distinguishable from randomly generated bit patterns 65

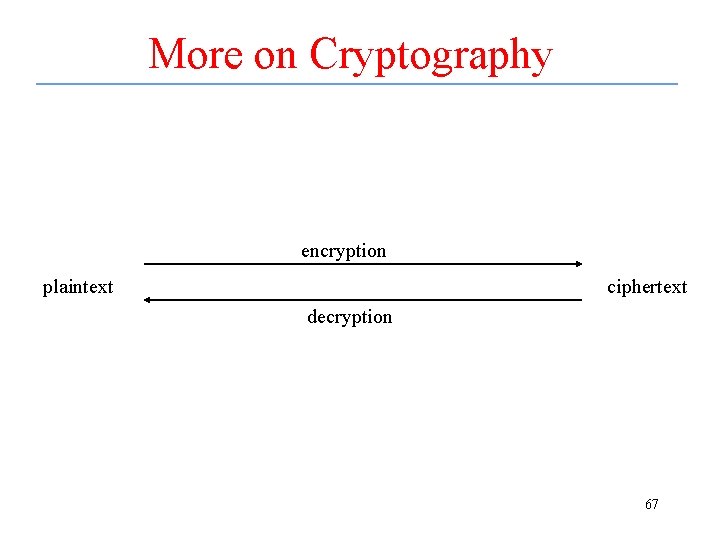
Cryptography • Even in secure OS, information will sometimes be temporarily unprotected – Ex. : while being transferred from one part of OS to another, as in Kerberos authentication strategy • Information can be encoded using a key when it is written (or transferred) -encryption • It is then decoded using a key when it is read (or received) -- decryption 66

More on Cryptography encryption plaintext ciphertext decryption 67

Two Basic Strategies • Details of encryption and decryption are unknown – Functions are complex making it difficult to guess how translation is accomplished • Details are known, but the keys are secret and difficult to forge – Difficult to guess a key 68

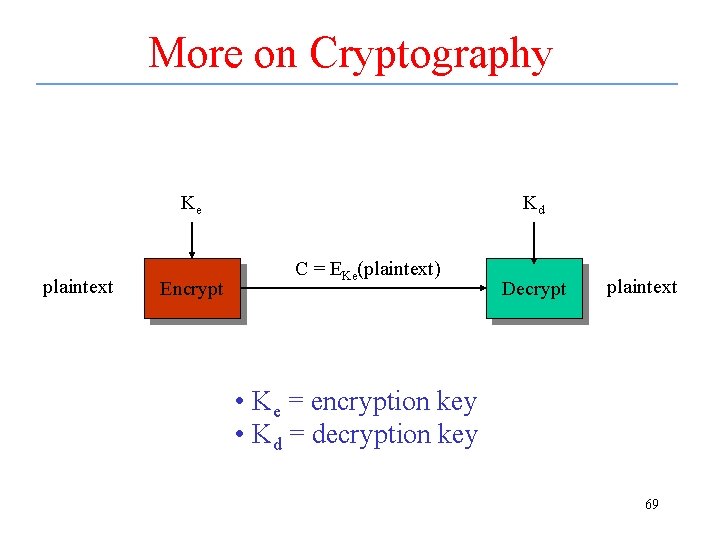
More on Cryptography Ke plaintext Encrypt Kd C = EKe(plaintext) Decrypt plaintext • Ke = encryption key • Kd = decryption key 69

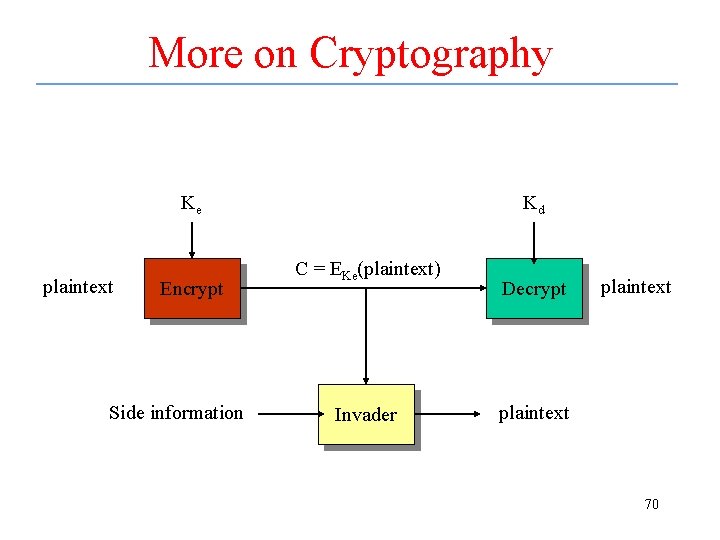
More on Cryptography Ke plaintext Encrypt Side information Kd C = EKe(plaintext) Invader Decrypt plaintext 70

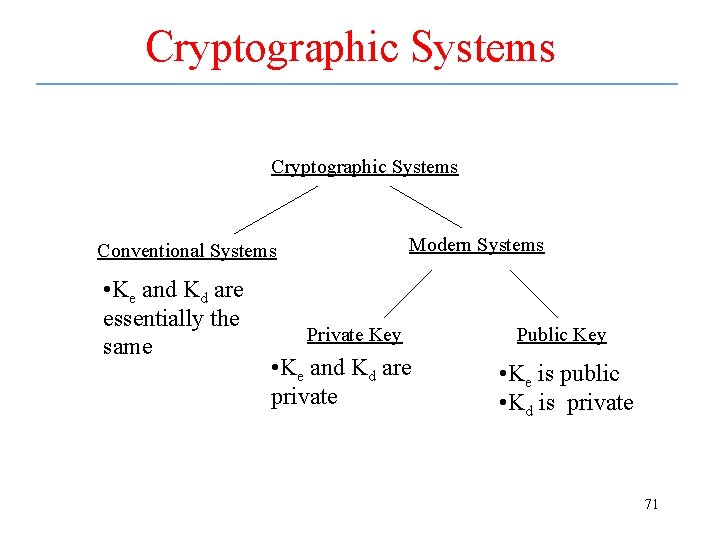
Cryptographic Systems Modern Systems Conventional Systems • Ke and Kd are essentially the same Private Key • Ke and Kd are private Public Key • Ke is public • Kd is private 71

Encryption • Encrypt clear text into cipher text. • Properties of good encryption technique: – Relatively simple for authorized users to encrypt and decrypt data. – Encryption scheme depends not on the secrecy of the algorithm but on a parameter of the algorithm called the encryption key – Extremely difficult for an intruder to determine the encryption key • Data Encryption Standard substitutes characters and rearranges their order on the basis of an encryption key provided to authorized users via a secure mechanism. Scheme only as secure as the mechanism. 72

Encryption - cont. • Public-key encryption based on each user having two keys: – public key – published key used to encrypt data. – private key – key known only to individual user used to decrypt data. • Must be an encryption scheme that can be made public without making it easy to figure out the decryption scheme. – Efficient algorithm for testing whether or not a number is prime. – No efficient algorithm is known for finding the prime factors of a number. 73

Public Key Cryptography • Clear text encrypted by public key can be decrypted by private key, and vice versa • Two users can generate authenticated, private communications – Information is signed by user 1 and encrypted with user 1’s private key – The entire message is then encrypted with user 2’s public key and transmitted – User 2 then decrypts using user 2’s private key and then with user 1’s public key 74