Guide to Operating System Security Chapter 1 Operating







































- Slides: 58

Guide to Operating System Security Chapter 1 Operating Systems Security – Keeping Computers and Networks Secure

Objectives l l l Explain what operating system and network security means Discuss why security is necessary Explain the cost factors related to security Describe the types of attacks on operating systems and networks Discuss system hardening, including features in operating systems and networks that enable hardening Guide to Operating System Security 2

What Is Operating System and Network Security? l Ability to reliably store, modify, protect, and grant access to information, so that information is only available to designated users Guide to Operating System Security 3

Operating Systems and Security l Operating systems Provide basic programming instructions to computer hardware u Interface with user application software and computer’s BIOS to allow applications to interact with hardware u l Security issue u Potential to provide security functions at every level of operation Guide to Operating System Security 4

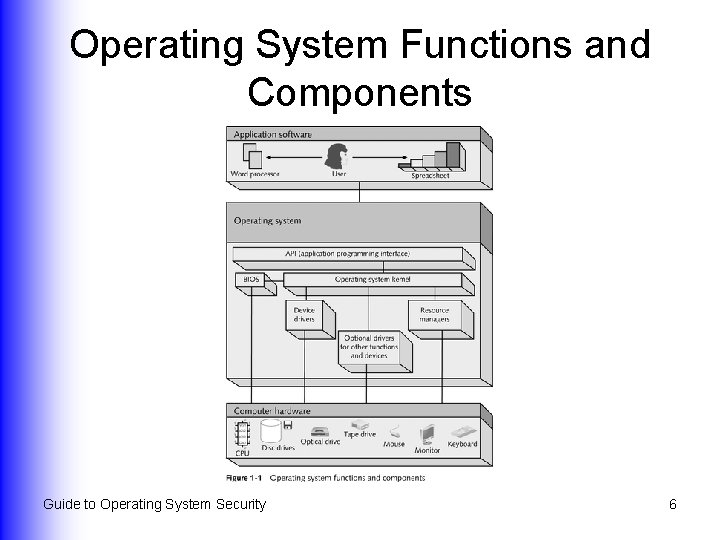
Operating System Components l l Application programming interface (API) Basic input/output system (BIOS) u l l l Basic form of security: Configure BIOS password security Kernel Resource managers Device drivers Guide to Operating System Security 5

Operating System Functions and Components Guide to Operating System Security 6

Computer Networks and Security l Computer network u l System of computers, print devices, network devices, and computer software linked by communications cabling or radio and microwaves Security issue u All networks have vulnerable points that require security Guide to Operating System Security 7

Types of Networks l Classified by reach and complexity Local area networks (LANs) u Metropolitan area networks (MANs) u Wide area networks (WANs) u l Enterprise networks Guide to Operating System Security 8

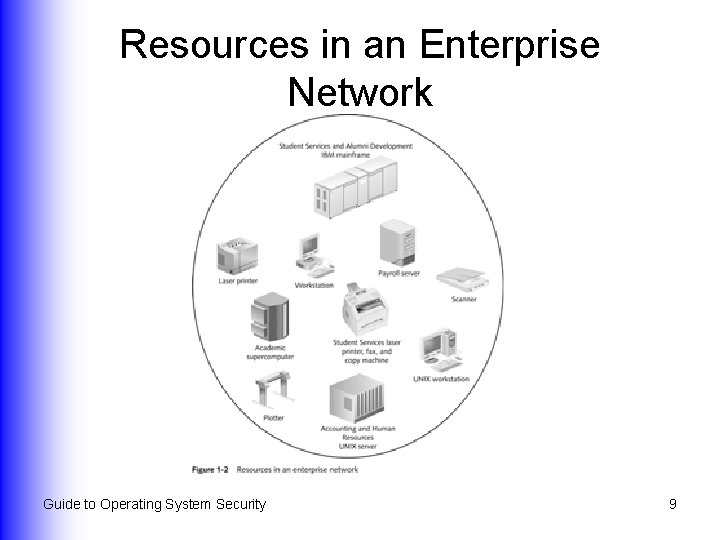
Resources in an Enterprise Network Guide to Operating System Security 9

Careers in Information Security l l Number of jobs has increased by 100% per year since 1998 Potential for healthy salaries and organizational advancement Guide to Operating System Security 10

Why Security Is Necessary l l l Protects information and resources Ensures privacy Facilitates workflow Addresses security holes and software bugs Compensates for human error or neglect Guide to Operating System Security 11

Protecting Information and Resources l Security protects information and resources of: Businesses u Educational institutions u Government u Telecommuters u Personal users u Guide to Operating System Security 12

Ensuring Privacy l Potential for serious legal and business consequences when an intruder accesses private information Guide to Operating System Security 13

Facilitating Workflow l Potential for loss of money, data, or both if a step in the work process is compromised due to a security problem Guide to Operating System Security 14

Addressing Security Holes or Software Bugs l After purchasing a new OS, software, or hardware: Test rigorously for security and reliability u Check security defaults u Install patches immediately u Guide to Operating System Security 15

Compensating for Human Error or Neglect l l Use an OS that enables the organization to set up security policies Develop written security policies Implement training Test security of new operating systems and software Guide to Operating System Security 16

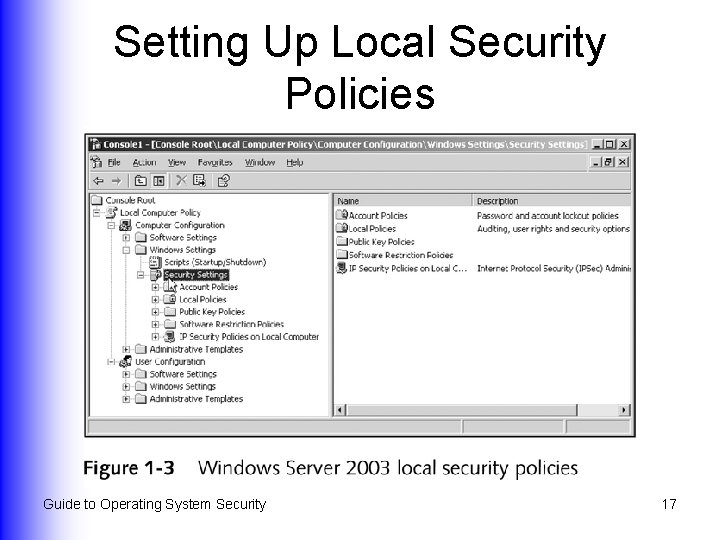
Setting Up Local Security Policies Guide to Operating System Security 17

Cost Factors l Cost of deploying security u l Should be an element in total cost of ownership (TCO) Cost of not deploying security Guide to Operating System Security 18

Types of Attacks l l l Standalone workstation or server attacks Attacks enabled by access to passwords Viruses, worms, and Trojan horses l l l l Guide to Operating System Security Buffer attacks Denial of service Source routing attack Spoofing E-mail attack Port scanning Wireless attacks 19

Standalone Workstation or Server Attacks l l Easy to take advantage of a logged-on computer that is unattended and unprotected Avoid by setting up a password-protected screen saver Guide to Operating System Security 20

Attacks Enabled by Access to Passwords l Users defeat password protection by Sharing them with others u Writing them down and displaying them u l Attackers have sophisticated ways of gaining password access Guide to Operating System Security 21

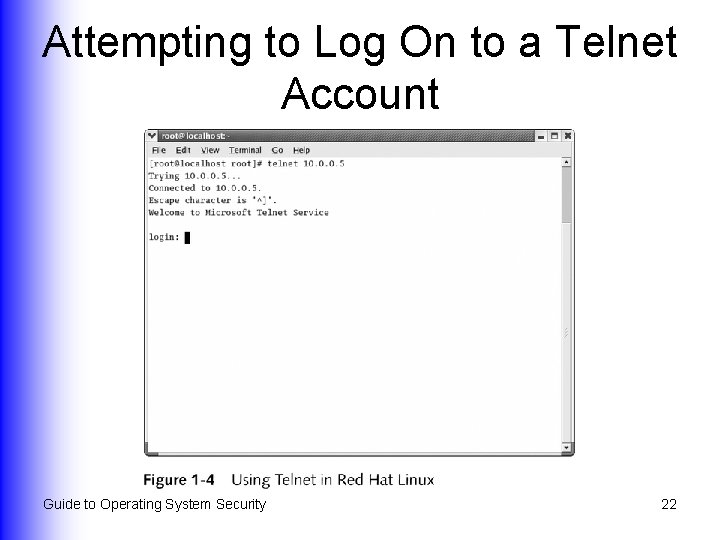
Attempting to Log On to a Telnet Account Guide to Operating System Security 22

Viruses l Virus Able to replicate throughout a system u Infects a disk/file, which infects other disks/files u Some cause damage; some don’t u l Virus hoax u E-mail falsely warning of a virus Guide to Operating System Security 23

Worm l l Endlessly replicates on the same computer, or sends itself to many other computers on a network Continues to create new files but does not infect existing files Guide to Operating System Security 24

Trojan Horse l l Appears useful and harmless, but does harm Can provide hacker with access to or control of the computer Guide to Operating System Security 25

Buffer Attacks l l Attacker tricks buffer software into attempting to store more information than it can contain (buffer overflow) The extra information can be malicious software Guide to Operating System Security 26

Denial of Service (Do. S) Attacks l Interfere with normal access to network host, Web site, or service by flooding network with: Useless information, or u Frames or packets containing errors that are not identified by a network service u l Distributed Do. S attack u One computer causes others to launch attacks directed at one or more targets Guide to Operating System Security 27

Source Routing Attack l l l Attacker modifies source address and routing information to make a packet appear to come from a different source Can be used to breach a privately configured network A form of spoofing Guide to Operating System Security 28

Spoofing l l l Address of source computer is changed to make a packet appear to come from a different computer Can be used to initiate access to a computer Can appear as just another transmission to a computer from a legitimate source Guide to Operating System Security 29

E-mail Attack l Attached file may contain: Virus, worm, or Trojan horse u Macro that contains malicious code u l E-mail may contain Web link to a rogue Web site Guide to Operating System Security 30

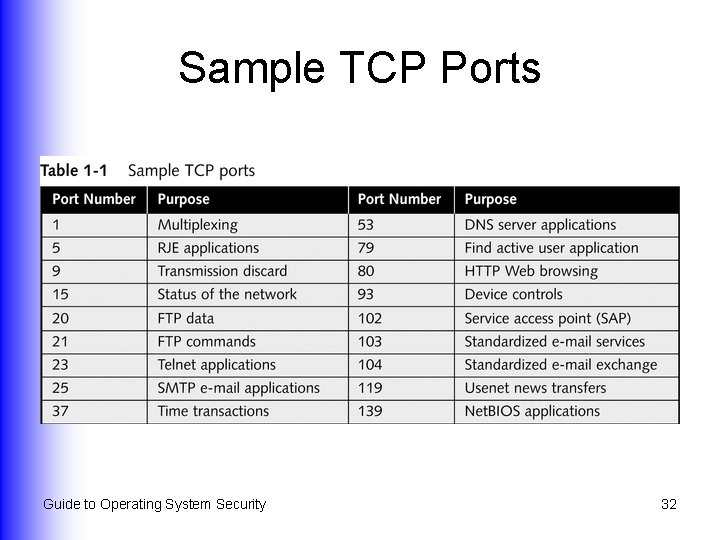
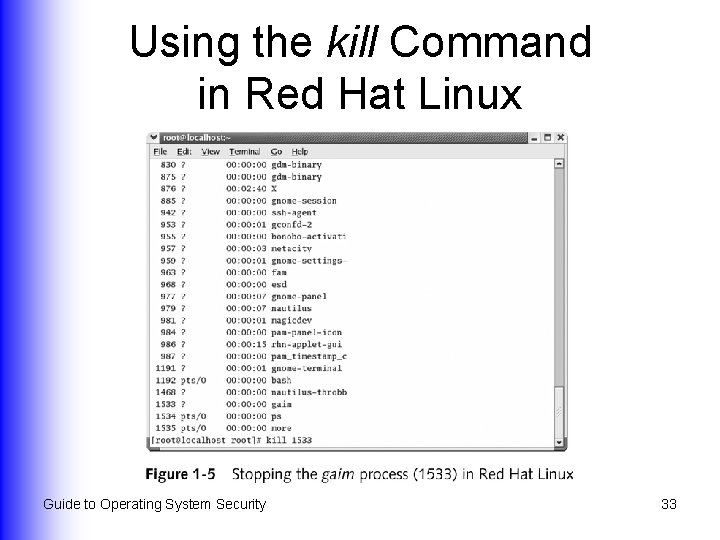
Port Scanning l l Attacker determines live IP address, then runs port scanning software (eg Nmap or Strobe) to find a system on which a key port is open or not in use To block access through open ports: Stop OS services or processes that are not in use u Configure a service only to start manually with your knowledge u Unload unnecessary NLMs u Guide to Operating System Security 31

Sample TCP Ports Guide to Operating System Security 32

Using the kill Command in Red Hat Linux Guide to Operating System Security 33

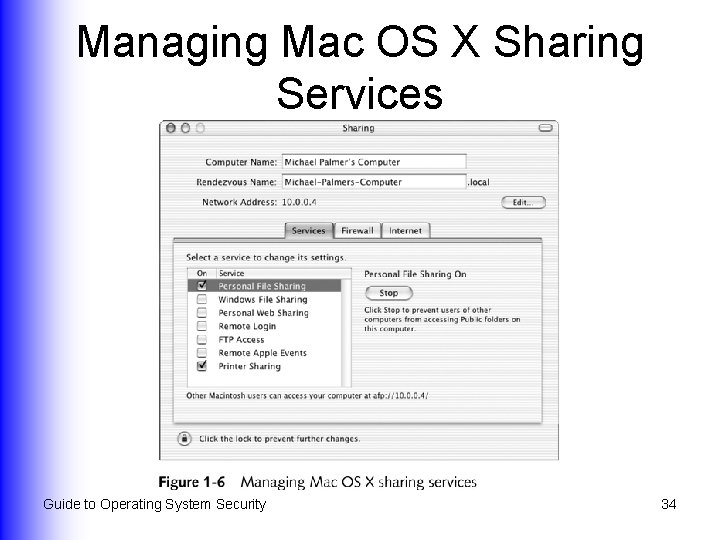
Managing Mac OS X Sharing Services Guide to Operating System Security 34

Wireless Attacks l l Generally involve scanning multiple channels Key elements Wireless network interface card u Omnidirectional antenna u War-driving software u l Difficult to determine when someone has compromised a wireless network Guide to Operating System Security 35

Organizations That Help Prevent Attacks (Continued) l l American Society for Industrial Security (ASIS) Computer Emergency Response Team Coordination Center (CERT/CC) Forum of Incident Response and Security Teams (FIRST) Infra. Gard Guide to Operating System Security 36

Organizations That Help Prevent Attacks (Continued) l l Information Security Forum (ISF) Information Systems Security Association (ISSA) National Security Institute (NSI) Sys. Admin, Audit, Network, Security (SANS) Institute Guide to Operating System Security 37

Hardening Your System l Taking specific actions to block or prevent attacks by means of operating system and network security methods Guide to Operating System Security 38

General Steps to Harden a System (Continued) l l Learn about OS and network security features Consult Web sites of security organizations Only deploy services and processes that are absolutely necessary Deploy dedicated servers, firewalls, and routers Guide to Operating System Security 39

General Steps to Harden a System (Continued) l l l Use OS features that are provided for security Deploy as many obstructions as possible Audit security regularly Train users to be security conscious Monitor OSs and networks regularly for attackers Guide to Operating System Security 40

Overview of Operating System Security Features l l Logon security Digital certificate security File and folder security Shared resource security Guide to Operating System Security l l Security policies Remote access security Wireless security Disaster recovery 41

Logon Security l l Requires user account and password to access OS or network User account provides access to the domain Guide to Operating System Security 42

Objects in a Domain Guide to Operating System Security 43

Digital Certificate Security l Verifies authenticity of the communication to ensure that communicating parties are who they say they are Guide to Operating System Security 44

File and Folder Security l l Lists of users and user groups can be given permission to access resources Attributes can be associated with resources to manage access and support creation of backups Guide to Operating System Security 45

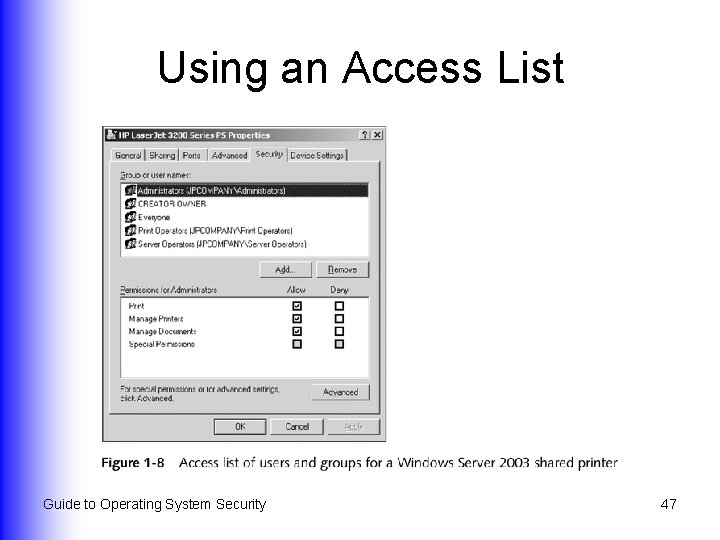
Shared Resource Security l Ways to control access to resources: Use a list of users and groups that should be configured u Use domains u Publish resources in a directory service (eg, Active Directory or NDS) u Guide to Operating System Security 46

Using an Access List Guide to Operating System Security 47

Security Policies l l l Security default settings that apply to a resource offered through an OS or directory service May apply only to local computer, or to other computers May specify that user account passwords must be a minimum length and be changed at regular intervals Guide to Operating System Security 48

Remote Access Security l l Enable remote access only when absolutely necessary Many forms, including: Callback security u Data encryption u Access authentication u Password security u Guide to Operating System Security 49

Wireless Security l l Implement Wired Equivalent Privacy (WEP) Create a list of authorized wireless users based on the permanent address assigned to the wireless interface in the computer Guide to Operating System Security 50

Disaster Recovery l Use of hardware and software techniques to prevent loss of data Perform backups u Store backups in a second location u Use redundant hard disks u l Enables restoration of systems and data without loss of critical information Guide to Operating System Security 51

Overview of Network Security Features l l Authentication and encryption Firewalls Topology Monitoring Guide to Operating System Security 52

Authentication l l Using a method to validate users who attempt to access a network or resources, to ensure they are authorized Examples User accounts with passwords u Smart cards u Biometrics u Guide to Operating System Security 53

Encryption l l Protects information sent over a network by making it appear unintelligible Generally involves using a mathematical key Guide to Operating System Security 54

Firewalls l Software or hardware placed between networks that selectively allows or denies access Guide to Operating System Security 55

Topology l l Different designs yield different results in terms of security planning and hardening Also affects security in terms of where specific devices are placed Guide to Operating System Security 56

Monitoring l l Involves determining performance and use of an OS or network Enables you to determine weak points of a system or network and address them before a problem occurs Guide to Operating System Security 57

Summary l l l Operating system and network security Why such security is vital Careers in information security The cost of security; the cost of not having security Common types of attacks Techniques for guarding against attacks on operating systems and on networks Guide to Operating System Security 58