Program Analysis and Software Security Professor Xiangyu Zhang
















- Slides: 19

Program Analysis and Software Security Professor Xiangyu Zhang 2017 Dragon Star Course @ Nanjing University

Computer Science Purdue CS ranks the 20 th in the latest US News ranking CS ranks the 2 nd in Purdue provost’s top 10 priority list 58 Graduate Faculty: • 29 Full Professors • 9 Associate Professors • 20 Assistant Professors 270 Graduate Students • 16% Women • 74% International Students 2

Research It’s Happening Here! • • • Big Data (*) Biological Databases Data Mining and Machine Learning (*) Distributed Systems Embedded Systems Information Retrieval Information Visualization Networking Operating System and Virtualization Programming Languages, Compilers and Software Engineering (*) • Security (*) • Scientific Computing and Parallelization (*) • Theory (*) 5

CS Degrees Awarded in 20152016 59 M. S. 15 Ph. D. 4

Financial Support Fall 2016 • 118 Graduate RAs in CS • 98 Graduate TAs in CS • 17 Graduate Fellows 5

West Lafayette Campus

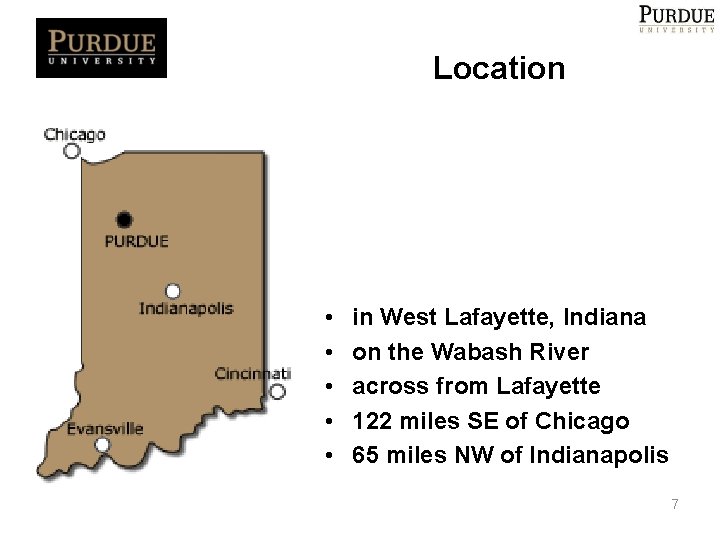
Location • • • in West Lafayette, Indiana on the Wabash River across from Lafayette 122 miles SE of Chicago 65 miles NW of Indianapolis 7

Admission Criteria • CS course background • GPA • Letters of recommendation • Research experience and publications • Statement of purpose • GRE NOT required • We accept applications any time, even though the deadline is 12/15 8

Instructor • Research interest – Program analysis and security – New direction • CPS security • AI security • My research group – 14 current Ph. Ds – 10 former students • Faculty in Georgia Tech, Ohio State, U of Georgia, Simon Fraser University • Apple, Google, IBM, and Intel • Founder of Sensorhound – Best paper awards

This Course • Program analysis (in the context of identifying security vulnerabilities and defending security attacks)

Software Security • CIA – Confidentiality • E. g. , information leak – Integrity • E. g. control flow hijacking, ROP attacks – Authentication • E. g. , component hijacking

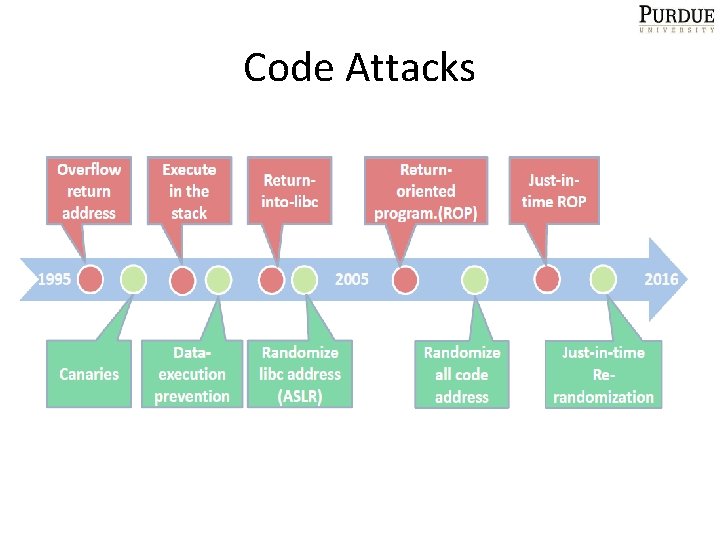
Code Attacks

Need For Program Analysis • A software related vulnerability is essentially a bug in the software – Identification • Defending software oriented attacks – Software transformation

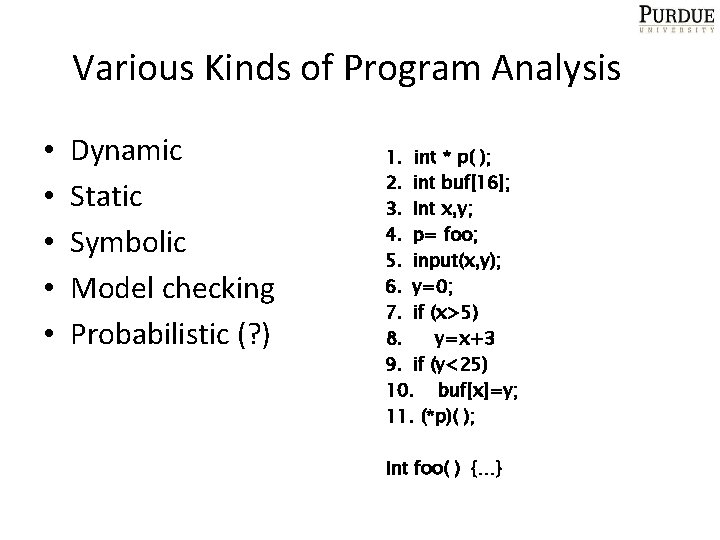
Various Kinds of Program Analysis • • • Dynamic Static Symbolic Model checking Probabilistic (? ) 1. int * p( ); 2. int buf[16]; 3. Int x, y; 4. p= foo; 5. input(x, y); 6. y=0; 7. if (x>5) 8. y=x+3 9. if (y<25) 10. buf[x]=y; 11. (*p)( ); Int foo( ) {…}

Learning Objectives • Hands-on experience – Project 1: Collecting memory access trace using Valgrind – Project 2: Provenance tracking (2 options) – Project 3: Equivalence checking • Understand the various state-of-the-art analysis approaches • Design and formulate program analysis – Given a hack, how do we formulate it as a analysis problem – How do we prove its correctness

Logistics • Morning – – – 09: 30 – 10: 20 (lecture I) 10: 20 – 10: 30 (break) 10: 30 – 11: 10 (lecture II) 11: 10 – 11: 20 (break) 11: 20 – 12: 00 (lecture III) • Afternoon – – – – 1: 30 – 2: 10 (lecture IV) 2: 10 – 2: 20 (break) 2: 20 – 3: 00 (lecture V / in-class exercise) 3: 00 – 3: 20 (break) 3: 20 – 4: 20 (discussion) 4: 20 – 4: 30 (break) 4: 30 – 6: 00 (course project) • Evening – independent study

Discussion Session • • • Introduce yourself Talk about your research and your group 3 min per individual presentation 5 min per group presentation Try to represent each school (Let’s create a wechat group: xiangyu-zhang 2015)

Teaching Assistant • • Zhilong Wang Weiping Zhou Jinshan Ouyang Jun Zhu

Useful Textbooks • Alfred V. Aho, Monical S. Lam, Ravi Sethi, Jeffrey D. Ullman, Compilers Principles, Techniques, & Tools. • Aaron R. Bradley, Zohar Manna, The Calculus of Computation.