Privacy MGMT 661 Summer 2012 Dannelly Night 3
















- Slides: 20

Privacy MGMT 661 - Summer 2012, Dannelly Night 3, Lecture Part 2

Outline for Tonight n Legal Topics - Part 1 SPAM ¨ Software Warranties ¨ Software Copyrights and Patents ¨ Intellectual Property Laws ¨ n Privacy - Part 2 ¨ privacy from your employer from businesses from the government

Initial Questions n Is privacy a right? ¨ inalienable right? n ¨ legal (civil) right? n ¨ n e. g. life, liberty, pursuit of happiness e. g. right to vote, no taxation without representation not a right What do privacy rights have to do with business?

Types of Privacy n Freedom from Unwarranted Intrusion n Freedom from Interference in One's Personal Affairs n Control over the Flow of Personal Information

Tech's Impact on Privacy n duration of data storage n variety of data that can be shared n amount of data gathered n speed of data movement

Workplace Privacy n you don't have many workplace privacy rights n City of Ontario, California v. Quon et al. ¨ US Supreme Court, June 17, 2010 ¨ supervisors of public employees can read their employees' text messages on government issues devices

Is online shopping different from in-store shopping? n Q: Does online shopping give you more or less privacy? n n more privacy - your neighbors will not see you less privacy - online shopping gives the company much more info about you n Q: Is the data the company gathers different? n online, they know every item you looked at, how long you spent looking, etc

Sources of Personal Data n n n n n phone book public records credit card statements web cookies rewards programs spyware Ti. Vo RFID …

Data Mining n definition: searching through databases to discover patterns and relationships n usually used for prediction n example: ¨ company XYZ operates toll booths and collects data about which car IDs pass and when ¨ company ABC buys XYZ's data and data from credit card companies. ABC now knows the addresses of frequent drivers along with credit limits ¨ ABC sells this secondary data to banks n "We see that your car has 100, 000 miles. Need a car loan? "

Info Security n How safe is that cookie data? n Example: Toysmart. com ¨ privacy statement said that the personal info of users would not be sold or exchanged ¨ the company went bankrupt in 2000 ¨ Toysmart sold its assets, including the customer database

Double. Click. com n gathers data from cookies from banners placed on a large number of web sites n DC can cross-reference data to build profiles of individual users n cookie data can be used to manage which ads individuals see and how many times the ads are seen. ¨ For example, using frequency capping, as I surf from website to website they can make sure I only see the same car ad 10 times per day

n In 1999, DC announced that it planned to purchase Abacus Direct for $1. 7 B, a consumer database company containing the names, addresses, phone numbers, etc of 90% of American Households. n Google bought Double. Click for $3. 1 B in cash in April 2007. congress held hearings to investigate the privacy and monopoly implications of the merger ¨ Microsoft complained about this creating a monopoly ¨

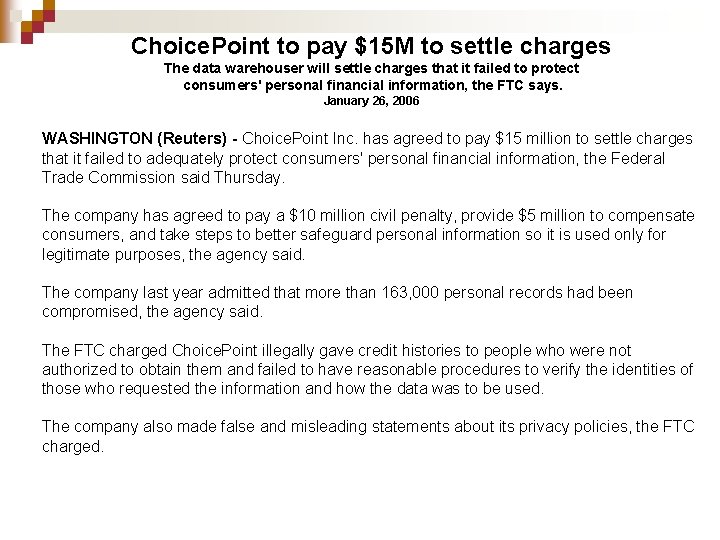
Choice. Point to pay $15 M to settle charges The data warehouser will settle charges that it failed to protect consumers' personal financial information, the FTC says. January 26, 2006 WASHINGTON (Reuters) - Choice. Point Inc. has agreed to pay $15 million to settle charges that it failed to adequately protect consumers' personal financial information, the Federal Trade Commission said Thursday. The company has agreed to pay a $10 million civil penalty, provide $5 million to compensate consumers, and take steps to better safeguard personal information so it is used only for legitimate purposes, the agency said. The company last year admitted that more than 163, 000 personal records had been compromised, the agency said. The FTC charged Choice. Point illegally gave credit histories to people who were not authorized to obtain them and failed to have reasonable procedures to verify the identities of those who requested the information and how the data was to be used. The company also made false and misleading statements about its privacy policies, the FTC charged.

Is your right to privacy protected by the U. S. Constitution? n No. Well, maybe. . n 1 st Amendment ¨ n 14 th Amendment ¨ n Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or … No State shall deprive any person of life, liberty, or property, without due process of law. 9 th Amendment ¨ The enumeration in the Constitution, of certain rights, shall not be construed to deny or disparage others retained by the people.

4 th Amendment The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.

Katz v United States n without a warrant, police placed a bug on the outside of a public phone booth used by Katz to make illegal bets n In 1967, the US Supreme Court ruled Katz's rights were violated. Katz reasonably thought his conversation was private, hence the recording was an illegal search and seizure ¨ the 4 th amendment protects people, not places ¨ the 4 th amendment governs seizure of tangible items, as well as recording of oral statements ¨

Electronic Communications Privacy Act n n enacted in 1986 ECPA was an amendment to Title III of the Omnibus Crime Control and Safe Streets Act of 1968, which was primarily designed to prevent unauthorized government access to private electronic communications. ¨ Title I of ECPA protects electronic communications while in transit. ¨ Title II of the ECPA, protects messages stored on computers. ¨ Title III prohibits the use of pen register and/or trap and trace devices to record dialing, routing, addressing, and signaling information used in the process of transmitting wire or electronic communications. http: //en. wikipedia. org/wiki/Electronic_Communications_Privacy_Act

NSA and FISA Foreign Intelligence Surveillance Act of 1978 (FISA) ¨ warrant required with 72 hours if "US person" involved ¨ amended n by Patriot Act in 2001 to include terrorism warrantless wiretaps of US citizens ended in 2007 ¨ replaced by Protect America Act of 2007, which expired ¨ replaced by FISA Amendments Act of 2008 n granted immunity to telecoms that had helped the NSA

Patriot Act n n n Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT) allows officials to track emails without showing probable cause allows roving surveillance for intelligence (not just crime investigation), tapped device does not have to be owned by the suspect search warrants no longer have to be served warrants for records do not require probable cause …

Summary of Privacy http: //imaginingtheinternet. wordpress. com/2011/04/25/opening-up-the-privacy-of-cyberspace/
 Kpp-0-661
Kpp-0-661 661 aess denver
661 aess denver Cvs privacy awareness and hipaa training answers
Cvs privacy awareness and hipaa training answers Tim washington ppm
Tim washington ppm Mgmt ama
Mgmt ama 2016 cengage learning
2016 cengage learning Mgmt 371 final exam
Mgmt 371 final exam Chapter 2 history of management
Chapter 2 history of management Mgmt 310 purdue
Mgmt 310 purdue Mgmt 371
Mgmt 371 Mgmt 650 quiz 4
Mgmt 650 quiz 4 Tfanet
Tfanet Keller graduate school of mgmt
Keller graduate school of mgmt Infrastructure mgmt
Infrastructure mgmt Mgmt ama
Mgmt ama Locational break even analysis
Locational break even analysis Mgmt 371
Mgmt 371 Mgmt 341
Mgmt 341 Symbols of night by elie wiesel
Symbols of night by elie wiesel Silent night holy night all is calm
Silent night holy night all is calm Dilys thomas
Dilys thomas