PolicyDriven Systems for EnterpriseWide Security Using PKI and



- Slides: 13

Policy-Driven Systems for Enterprise-Wide Security Using PKI and Policies to build Trusted Distributed Authorization Systems Joe Pato Marco Casassa Mont Hewlett-Packard Labs Sep 18, 2000 Page 1

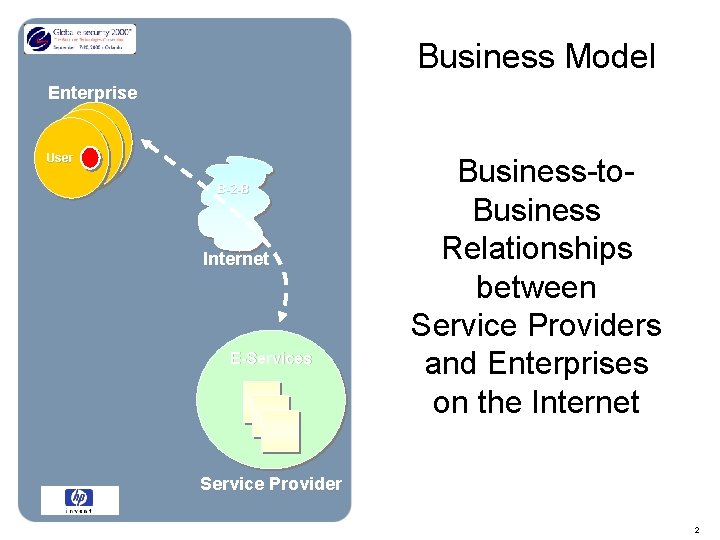
Business Model Enterprise User B-2 -B Internet E-Services Business-to. Business Relationships between Service Providers and Enterprises on the Internet Service Provider 2

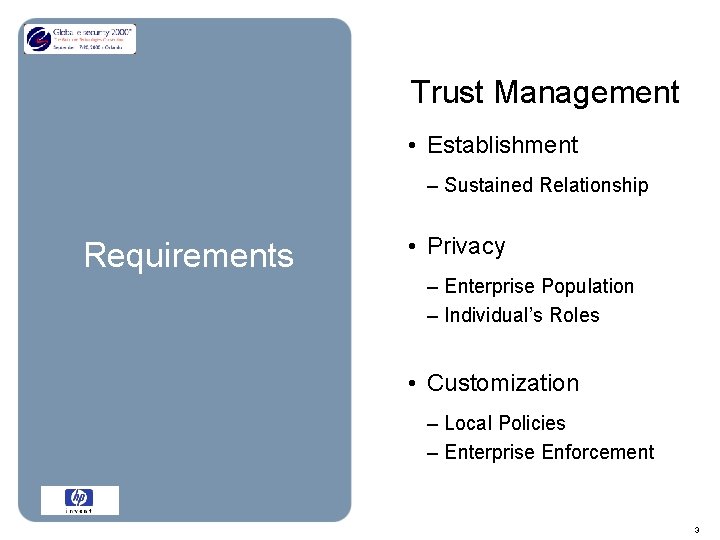
Trust Management • Establishment – Sustained Relationship Requirements • Privacy – Enterprise Population – Individual’s Roles • Customization – Local Policies – Enterprise Enforcement 3

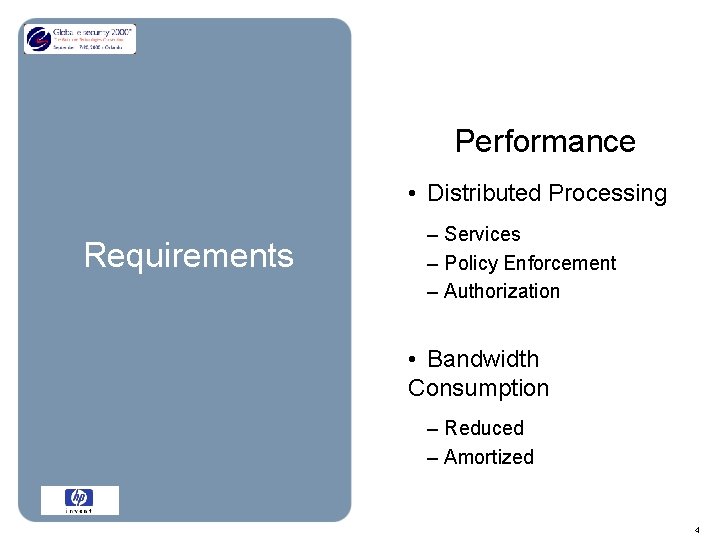
Performance • Distributed Processing Requirements – Services – Policy Enforcement – Authorization • Bandwidth Consumption – Reduced – Amortized 4

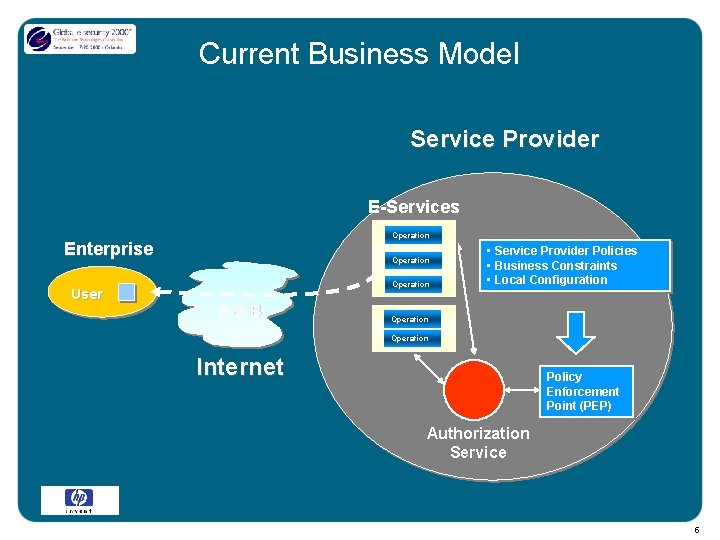
Current Business Model Service Provider E-Services Operation Enterprise User Operation B-2 -B • Service Provider Policies • Business Constraints • Local Configuration Operation Internet Policy Enforcement Point (PEP) Authorization Service 5

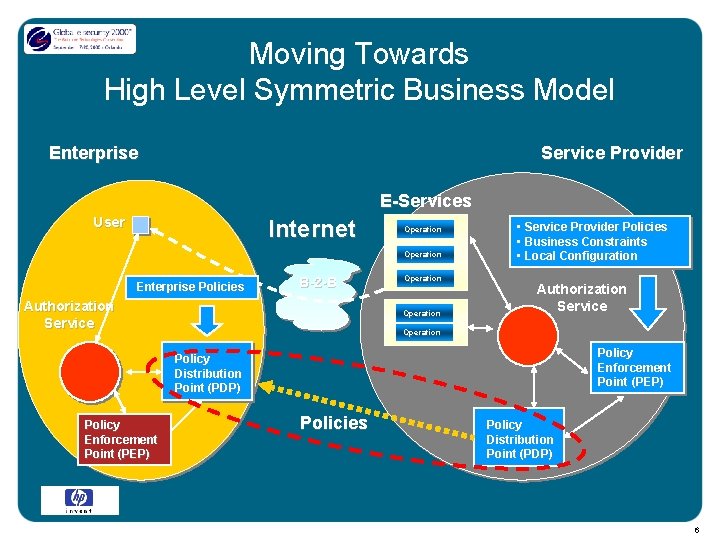
Moving Towards High Level Symmetric Business Model Enterprise Service Provider E-Services User Internet Operation Enterprise Policies B-2 -B Authorization Service Operation • Service Provider Policies • Business Constraints • Local Configuration Authorization Service Operation Policy Enforcement Point (PEP) Policy Distribution Point (PDP) Policy Enforcement Point (PEP) Policies Policy Distribution Point (PDP) 6

• Policy Driven Authorization • (A)Symmetric Authorization • Operation at both parties Distributed Authorization • Policy Distribution Points • Distribute across enterprises • Policy Enforcement Points • Both local and remote policies 7

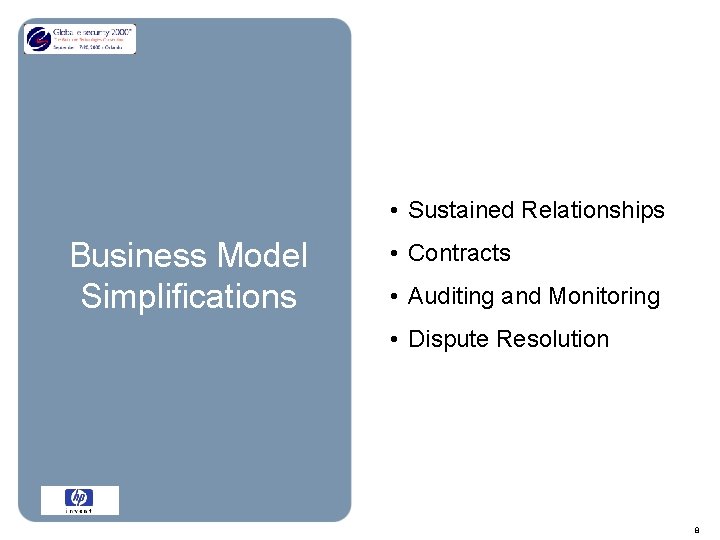
• Sustained Relationships Business Model Simplifications • Contracts • Auditing and Monitoring • Dispute Resolution 8

• Trust Establishment • Tamper Resistant Policy Enforcement Point Technology Problems • Verifiability of Identity of Involved Parties • Verifiability of Policies sent across Enterprise Boundaries • Instrumentation to Gather Evidence • Archival of Evidence 9

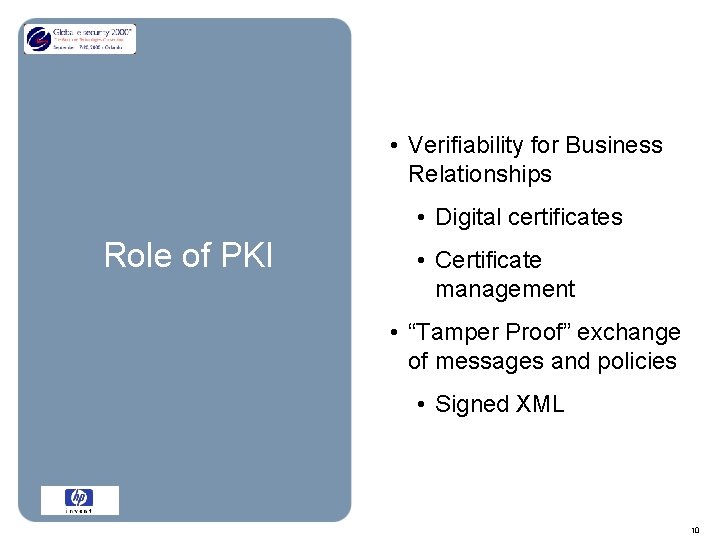
• Verifiability for Business Relationships • Digital certificates Role of PKI • Certificate management • “Tamper Proof” exchange of messages and policies • Signed XML 10

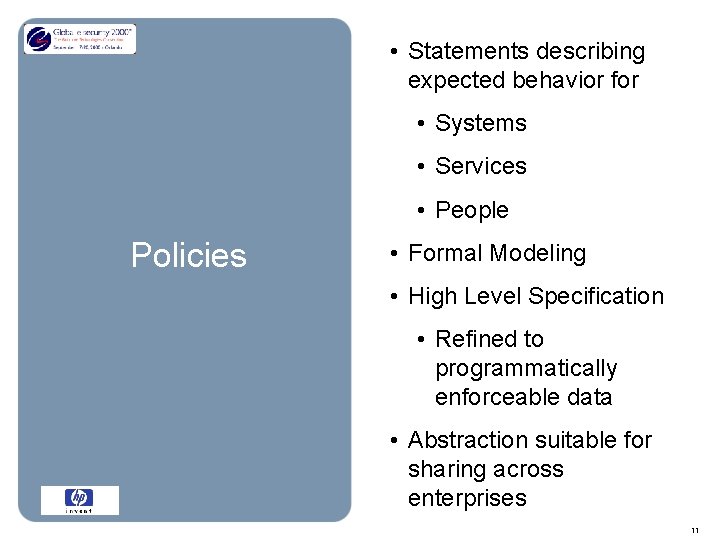
• Statements describing expected behavior for • Systems • Services • People Policies • Formal Modeling • High Level Specification • Refined to programmatically enforceable data • Abstraction suitable for sharing across enterprises 11

• Policies • Describe authorization constraints Role of Policies • Drive authorization decisions • Are exchanged between Enterprises in a Distributed Authorization Framework 12

Conclusion • Distributed Authorization enhances privacy and performance for B 2 B interactions < www. hp. com/security > 13