PHISHING AND ANTIPHISHING TECHNIQUES Sumanth Sanath and Anil













- Slides: 20

PHISHING AND ANTI-PHISHING TECHNIQUES Sumanth, Sanath and Anil Cp. Sc 620

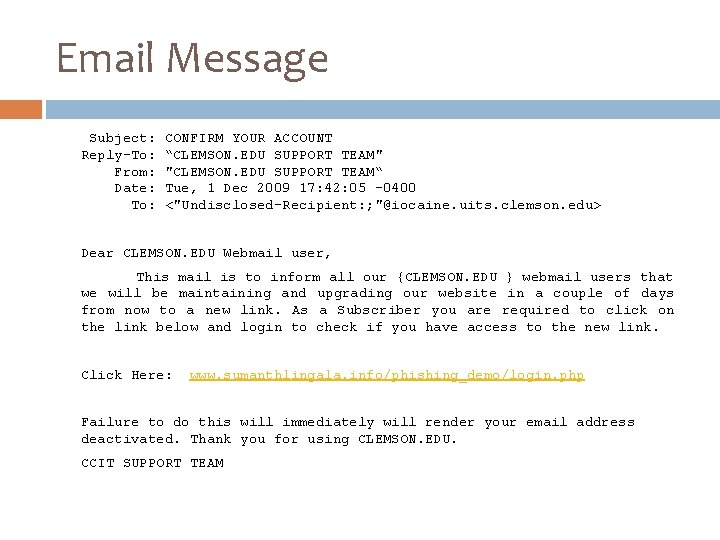
Email Message Subject: Reply-To: From: Date: To: CONFIRM YOUR ACCOUNT “CLEMSON. EDU SUPPORT TEAM" "CLEMSON. EDU SUPPORT TEAM“ Tue, 1 Dec 2009 17: 42: 05 -0400 <"Undisclosed-Recipient: ; "@iocaine. uits. clemson. edu> Dear CLEMSON. EDU Webmail user, This mail is to inform all our {CLEMSON. EDU } webmail users that we will be maintaining and upgrading our website in a couple of days from now to a new link. As a Subscriber you are required to click on the link below and login to check if you have access to the new link. Click Here: www. sumanthlingala. info/phishing_demo/login. php Failure to do this will immediately will render your email address deactivated. Thank you for using CLEMSON. EDU. CCIT SUPPORT TEAM

What is Phishing? Phishing scams are typically fraudulent email messages or websites appearing as legitimate enterprises (e. g. , your university, your Internet service provider, your bank). These scams attempt to gather personal, financial and sensitive information. Derivation of the word “phishing”.

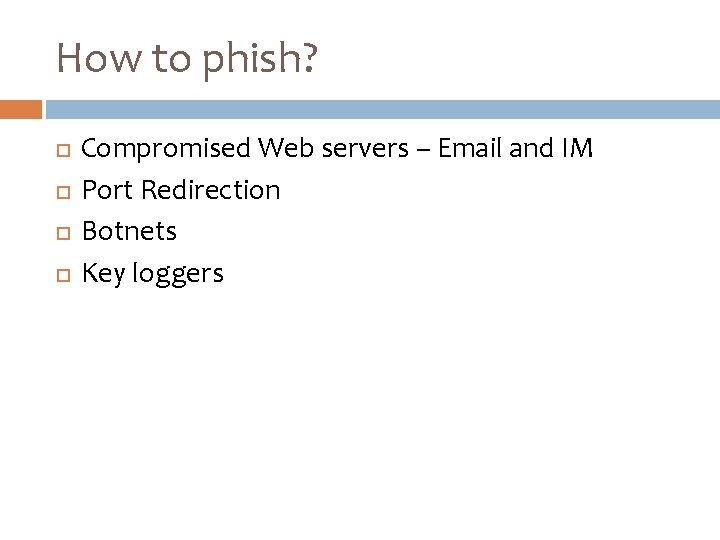
How to phish? Compromised Web servers – Email and IM Port Redirection Botnets Key loggers

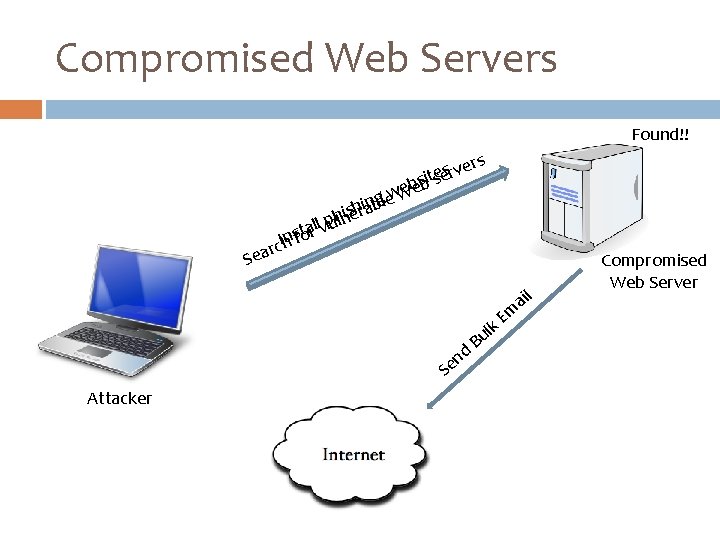
Compromised Web Servers Found!! rs e s v r e sbit se b e e gl ew W n i b isehra h n p l arl l. Vu t s o n c. Ih f r Sea ail u m E lk B d en S Attacker Compromised Web Server

Port Redirection Server is compromised and a program is loaded All the port 80 ie. , http requests are redirected to the attacker’s server Software known as ‘redir’ Execute the software using: redir --lport=80 –l addr=<IP addr orig server> -cport=80 -caddr=IP addr attacker

Using Botnets are computers infected by worms or Trojans and taken over surreptitiously by hackers and brought into networks to send spam, more viruses, or launch denial of service attacks. Remotely controlled by the attacker. SQL Injection attacks

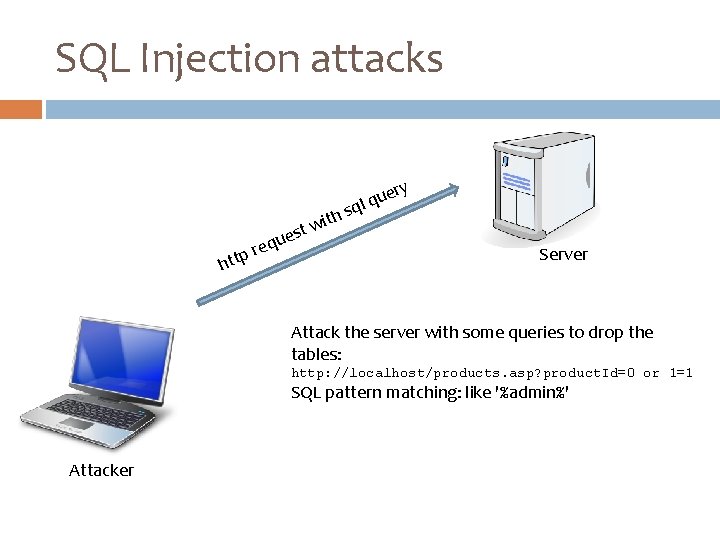
SQL Injection attacks ue q l q qu e r ttp h h s t i w st e ry Server Attack the server with some queries to drop the tables: http: //localhost/products. asp? product. Id=0 or 1=1 SQL pattern matching: like '%admin%' Attacker

Keyloggers are designed to monitor all the key strokes Hardware Software Modified to extract personal information

Current Statistics Source: http: //www. avira. com/

Anti-phishing Ways: Browser Capabilites Desktop Agents Token based Digitally Signed Email Domain Monitoring Client Level Server Level Enterprise Level

Browser Capabilites Disable pop ups Disable Java runtime support Prevent the storage of non-secure cookies Ensure that downloads are checked by anti-virus software Eg: Mozilla Firefox Verification

Browser Capabilites

Desktop Agents Install Anti-virus software which can prevent phishing Personal IDS Firewall Toolbars – Google, Yahoo, Net. Craft

Token based Authentication Token based Authentation

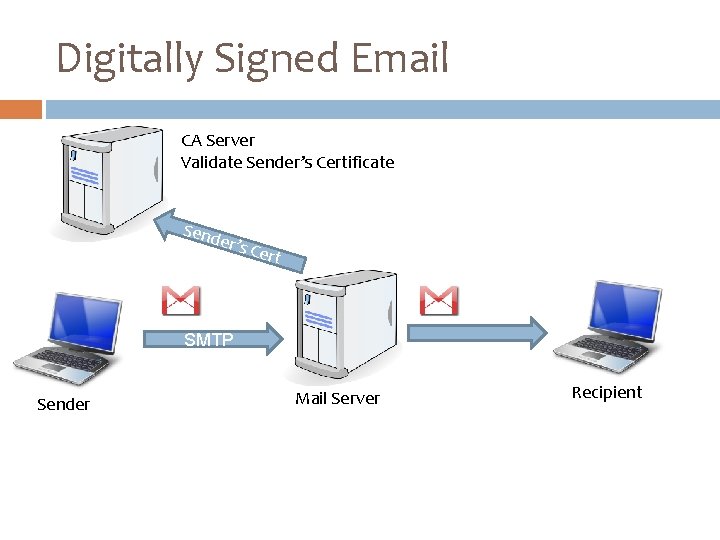
Digitally Signed Email CA Server Validate Sender’s Certificate Send er’s C ert SMTP Sender Mail Server Recipient

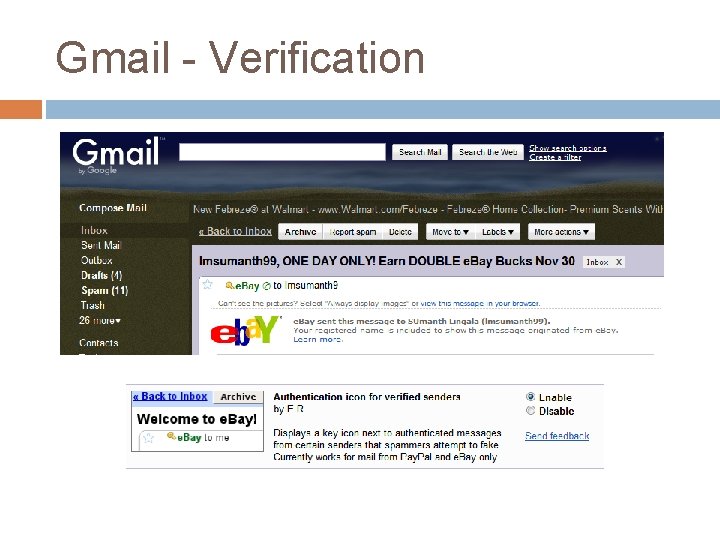
Gmail - Verification

Domain Monitoring Monitor the registration of Internet domains relating to their organisation and the expiry of corporate domains Google - Safe Browsing API www. phishtank. com

References Honeynet Projecy – http: //www. honeynet. org The Phishing Guide - Understanding and Preventing Phishing attacks Justice Department - http: //www. justice. gov/ Statistics - http: //www. avira. com/ Cross-site scripting attacks – http: //www. wikipedia. org/ Images from Pay. Pal, Gmail Demo - Clemson Webmail – Only for Ethical Hacking RSA Token Authentication - http: //www. entrust. com

Thank You !!!!
 Knowyourmeme
Knowyourmeme Phishing
Phishing Howsecureismypassword phishing
Howsecureismypassword phishing Phishing austin texas
Phishing austin texas Mobi fish
Mobi fish Phishing
Phishing How do fake social media accounts breach the cia triad
How do fake social media accounts breach the cia triad Types of phishing attacks
Types of phishing attacks Csirt playbook
Csirt playbook Halloween phishing
Halloween phishing Anti phishing phil
Anti phishing phil Setoolkit
Setoolkit Email phishing
Email phishing Webroot security awareness training
Webroot security awareness training Super phisher
Super phisher Ics phishing sms
Ics phishing sms Sunderlal bahuguna quotes in malayalam
Sunderlal bahuguna quotes in malayalam Doa penutup allahumma bihaqqil fatihah
Doa penutup allahumma bihaqqil fatihah Toppcluster
Toppcluster Anil hassan
Anil hassan Anil kumar polsani mainframe
Anil kumar polsani mainframe