Penetration Testing Dr X Pen Testing Penetration Testing












- Slides: 20

Penetration Testing Dr. X

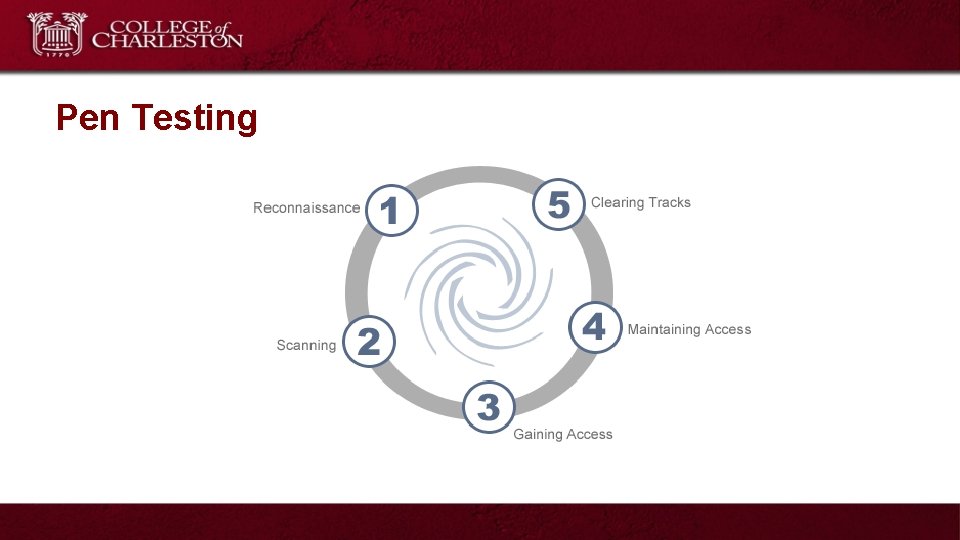
Pen Testing

Penetration Testing Methodology • AKA – The “Attack Chain” • Methodology for this course: – 1 - Reconnaissance and Vulnerability Discovery – 2 - Exploitation: Establishing a Foothold – 3 - Privilege Escalation and Lateral Movement – 4 - Data Exfiltration

Reconnaissance and Scanning • Initial Enumeration • Port scanning • Manual information gathering

Scanning • Port scanning – Open – Closed – Filtered • Tools – Nmap – Mascan – Maltego – Wireshark – Your own custom socket programming tools

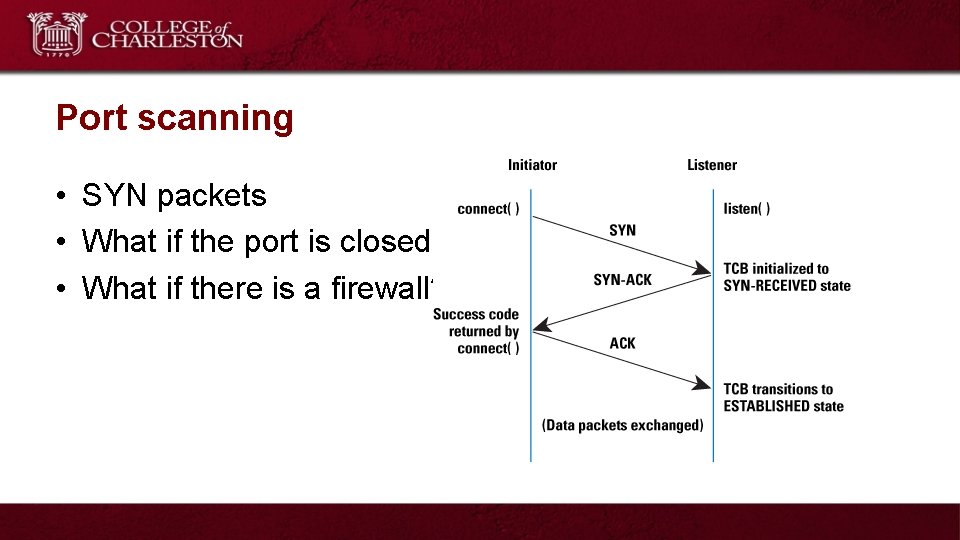
Port scanning • SYN packets • What if the port is closed? • What if there is a firewall?

Nmap • • • Network Map Developed by Fyodor (see http: //insecure. org/) Inventory of all devices in network Detect OS Nmap can perform: – TCP SYN scan – TCP connect() scans – UDP scans – • Is there such thing as UDP SYN? • How will machine respond? – ICMP scans, etc.

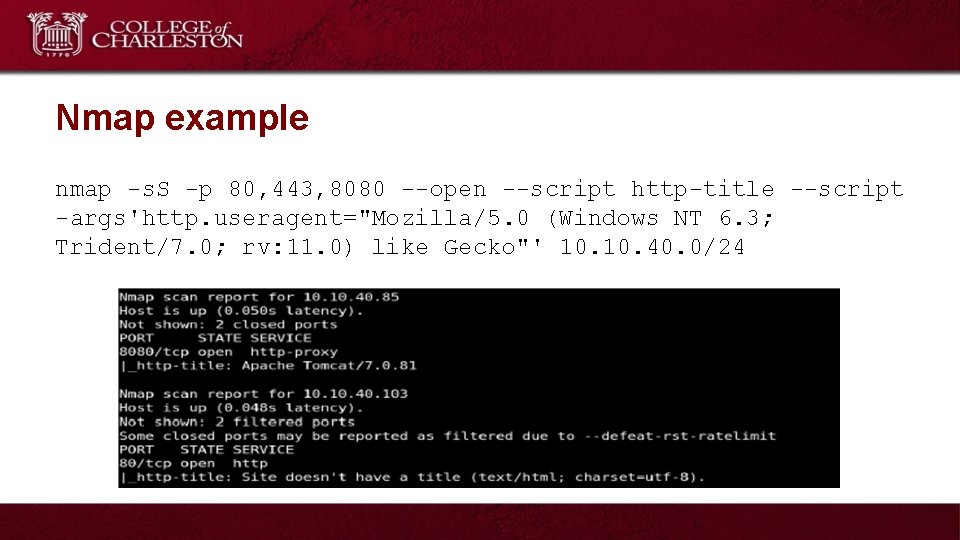
Nmap example nmap -s. S -p 80, 443, 8080 --open --script http-title --script -args'http. useragent="Mozilla/5. 0 (Windows NT 6. 3; Trident/7. 0; rv: 11. 0) like Gecko"' 10. 40. 0/24

Gaining access • Exploiting the vulnerabilities identified • Gaining code execution • Establishing a command control channel

Gaining access • R 2 L • U 2 R • Active exploitation testing – Login checking and brute forcing – Vulnerability exploitation (Metasploit, Core Impact) – 0 day and exploit discovery (Fuzzing, program analysis) – Post exploitation techniques to assess severity (permission levels, backdoors, rootkits, etc)

Gaining access tools - Common tools and frameworks: - Metasploit Framework (Nexpose); - Burp Suite; - Nikto; - Zed Attack Proxy (ZAP) - SQLMap - Hydra; - John the Ripper; - Specialized OS distributions (Linux): - Kali Linux; - Backtrack – discontinued;

Metasploit framework - An exploitation framework written in Ruby, currently at version 4. 14. 3 - It’s modular - Contains exploits, payloads, encoders and auxiliaries - 1817 Exploits 1031 Auxiliary 539 Payloads 42 Encoders - The framework is Open Source

Metasploit framework - Is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime - Stealthy - Powerful - Extensible - Features can be added at runtime: new features are added to Meterpreter by loading extensions.

Metasploit framework - msfconsole is probably the most popular interface to the MSF - It provides an "all-in-one" centralized console

Privilege Escalation and Lateral Movement • Go from “User” to “Administrator” – Via local security misconfigurations • Identify other targets on the network – Testing admin access • Establish C 2 channels to those targets with remote management functionality – PSEXEC – WMI

msfconsole PRACTICAL EXAMPLE

Persistence • Maintain access • Backdoor • The Metasploit Framework comes with two options for backdooring a system. – Persistence – Metsvc https: //pentestlab. blog/tag/persistent-backdoor/

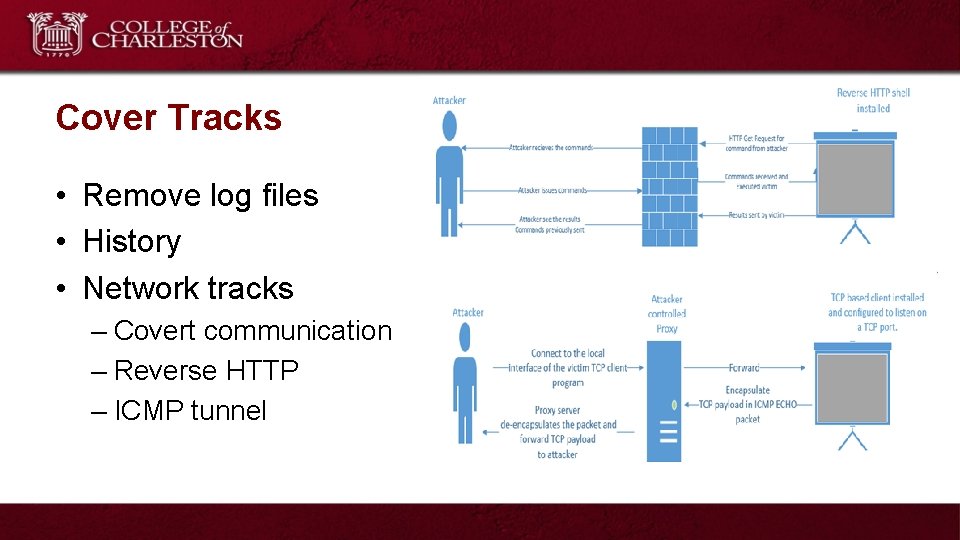
Cover Tracks • Remove log files • History • Network tracks – Covert communication – Reverse HTTP – ICMP tunnel

Penetration testing summary • • • Different than vulnerability assessment Distinct phases Iterative process Tools Art and science

PENETRATION TESTING LAB ON GENI