Module 2 Pen Test Overview Penetration Testing Methodologies





- Slides: 15

Module 2 – Pen. Test Overview Penetration Testing Methodologies Penetration Test Management (ISSAF) Pen. Test Project Management Engineer Assessment Effort Heorot. net

Penetration Testing Methodologies ISSAF ○ http: //www. oissg. org/issaf OSSTMM ○ http: //www. isecom. org/osstmm/ NIST SP 800 -42 ○ http: //csrc. nist. gov/publications/Pubs. SPs. html Heorot. net

Penetration Testing Methodologies ISSAF Peer-Reviewed Contains two separate documents ○ Management (ISSAF 0. 2. 1 A) ○ Penetration Testing (ISSAF 0. 2. 1 B) Checklists for Auditing / Hardening Systems Tool-Centric Heorot. net

Penetration Testing Methodologies ISSAF Advantages ○ Does not assume previous knowledge ○ Provides examples of pentest tool use ○ “In the weeds” Disadvantages ○ Out of date quickly ○ Pentest tool examples are not extensive ○ Last update: May 2006 Heorot. net

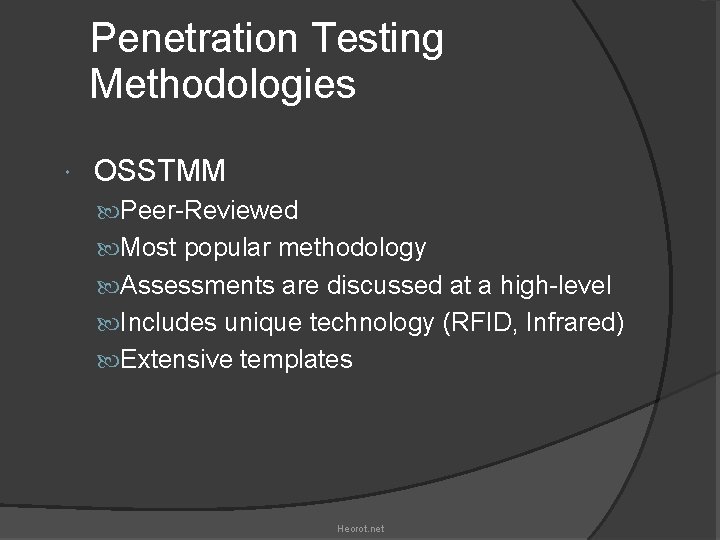
Penetration Testing Methodologies OSSTMM Peer-Reviewed Most popular methodology Assessments are discussed at a high-level Includes unique technology (RFID, Infrared) Extensive templates Heorot. net

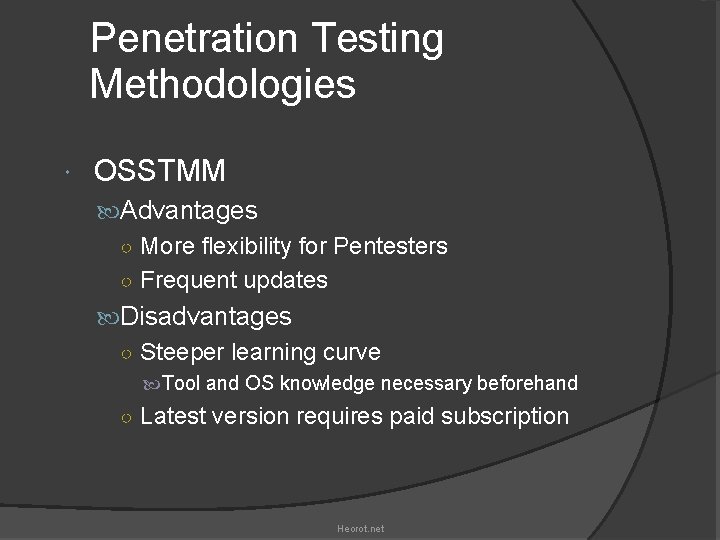
Penetration Testing Methodologies OSSTMM Advantages ○ More flexibility for Pentesters ○ Frequent updates Disadvantages ○ Steeper learning curve Tool and OS knowledge necessary beforehand ○ Latest version requires paid subscription Heorot. net

Penetration Testing Methodologies NIST SP 800 -42 Federal Publication Least comprehensive methodology Tools-oriented NIST publications rarely get updated If you can't use anything else, at least use something Heorot. net

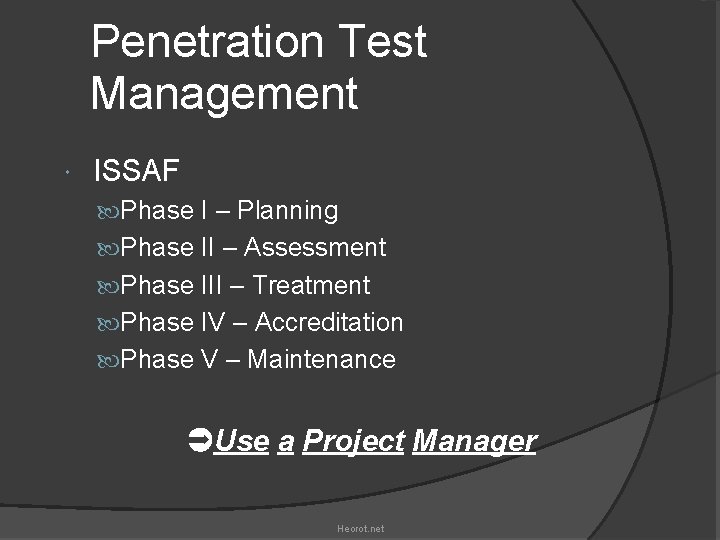
Penetration Test Management ISSAF Phase I – Planning Phase II – Assessment Phase III – Treatment Phase IV – Accreditation Phase V – Maintenance Use a Project Manager Heorot. net

Pen. Test Project Management Phase I – Planning Information Gathering Project Chartering Resource Identification Budgeting Bidding & Estimating (Called “Cash Flow”) Work Breakdown Structure (WBS) Project Kick-Off Heorot. net

Pen. Test Project Management Phase II – Assessment Inherent Risk Assessment Controls Assessment ○ Legal & Regulatory Compliance ○ Information Security Policy ○ Information Security Organization and Mgmt. ○ Enterprise Information Systems Security and Controls (Penetration Testing) ○ Security Operations Management ○ Business Continuity Management Heorot. net

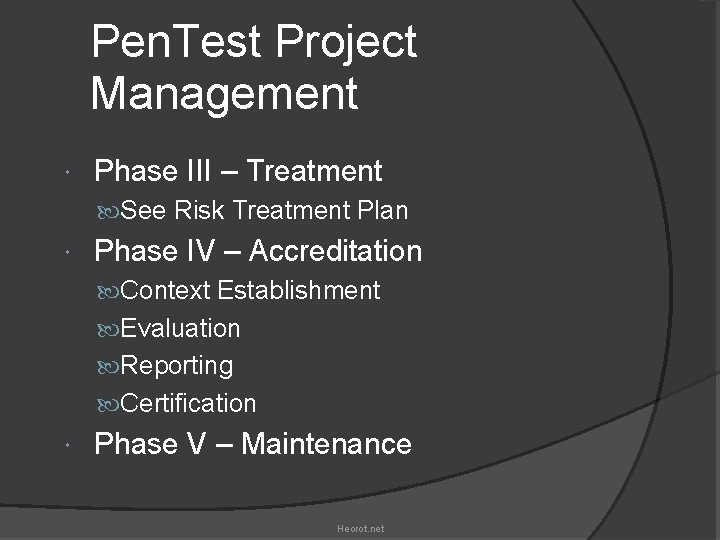
Pen. Test Project Management Phase III – Treatment See Risk Treatment Plan Phase IV – Accreditation Context Establishment Evaluation Reporting Certification Phase V – Maintenance Heorot. net

Pen. Test Project Management Phase II – Assessment Inherent Risk Assessment Controls Assessment ○ Legal & Regulatory Compliance ○ Information Security Policy ○. . . etc. Each assessment is broken down further. . . Heorot. net

Pen. Test Project Management Phase II – Assessment Project Management Documents ○ Engagement Scope ○ Communications Plan ○ Issue Escalation Plan ○ Scheduling ○ Responsibility Matrix ○ Deliverables Heorot. net

Engineer Assessment Effort Phase II – Assessment Scheduling (Engineering Effort) ○ Information Gathering ○ Network Mapping ○ Vulnerability Identification ○ Penetration ○ Gaining Access & Privilege Escalation ○ Enumerating Further ○ Compromise Remote Users/Sites ○ Maintaining Access ○ Cover the Tracks Heorot. net

Module 2 – Conclusion Penetration Testing Methodologies Penetration Test Management (ISSAF) Pen. Test Project Management Engineer Assessment Effort Heorot. net