OTR AKE Protocol OTR Data Protocol Security Properties







- Slides: 15

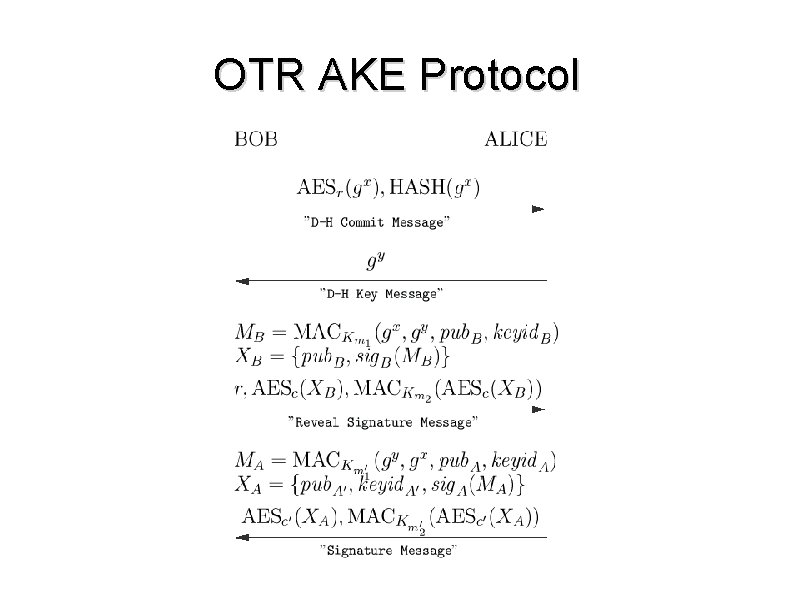
OTR AKE Protocol

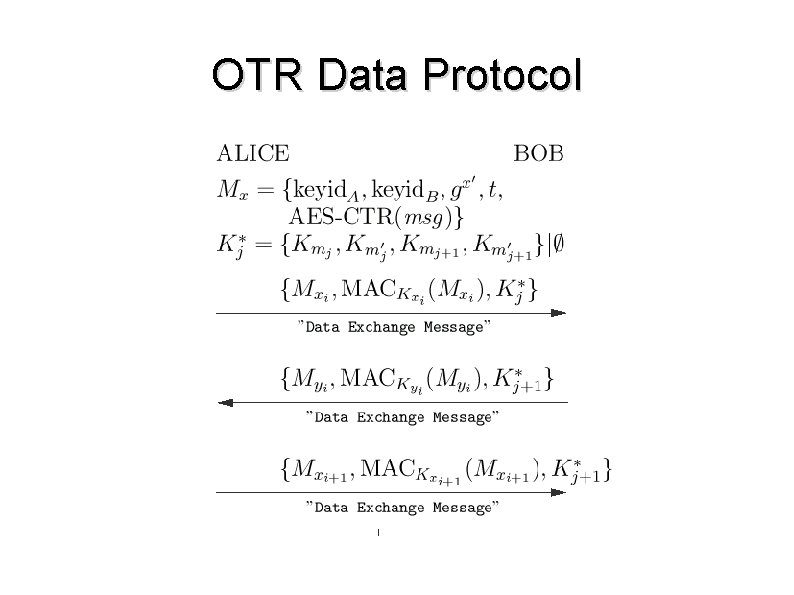
OTR Data Protocol

Security Properties ● Authentication: Public keys and signatures ● Integrity: MACs ● Perfect Forward Secrecy: Constant re-keying ● Deniability – Weak Deniability: Shared secrets – Strong Deniability: Malleable encryption

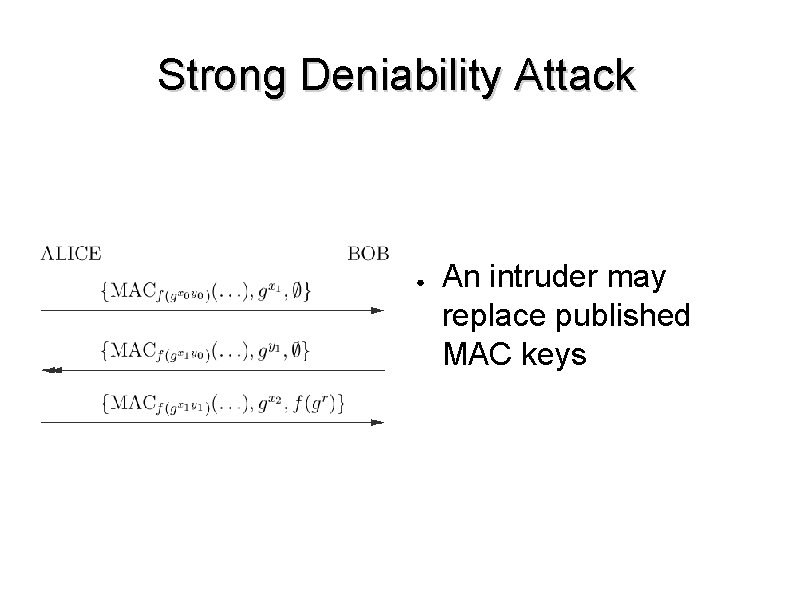
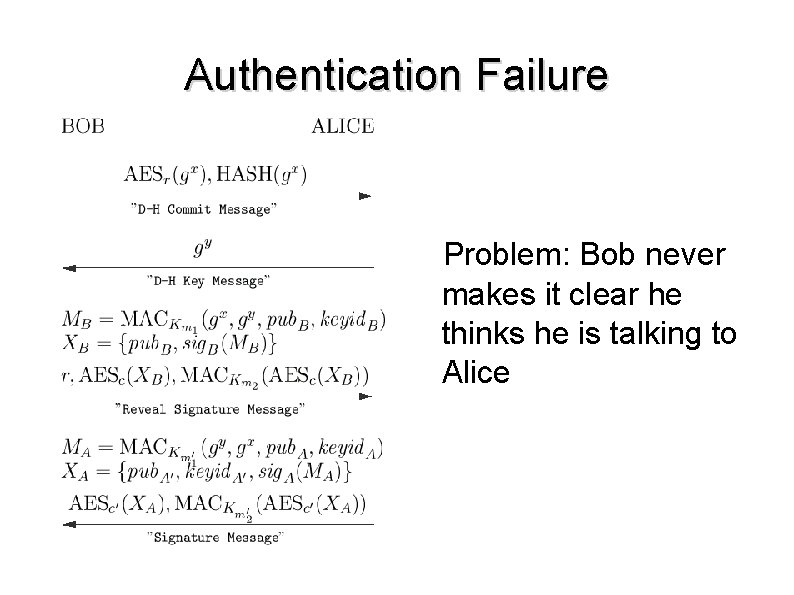
Found Attacks ● Version Rollback Attack – ● Strong Deniablity Attack – ● An attacker with strong network control may disable the strong deniability property. Authentication Failure – ● An attacker may arbitrarily set the version of OTR. Alice may be convinced to commit to an AKE key exchange not knowing who she is speaking with. Message Integrity Attack – An intruder may arbitrarily alter a message.

Strong Deniability Attack invariant "Strong Deniability" forall a: Principal. Id do forall b: Principal. Id do forall i: Intruder. Id do int[i]. mac_keys[a][b]. k_A >= 0 & int[i]. mac_keys[b][a]. k_B >= 0 -> int[i]. mac_keys[a][b]. k_A = pri[a]. c[b]. k_ours - 2 & int[i]. mac_keys[b][a]. k_B = pri[a]. c[b]. k_theirs - 1 end end;

Strong Deniability Attack ● An intruder may replace published MAC keys

Authentication Failure Problem: Bob never makes it clear he thinks he is talking to Alice

Authentication Failure ● Bob believes he is talking to Mallory ● Alice believes she is talking to Bob

Authentication Failure ● Bob believes he is talking to Mallory ● Alice believes she is talking to Bob ● After receiving the third message, Alice commits to a successful key exchange with Bob

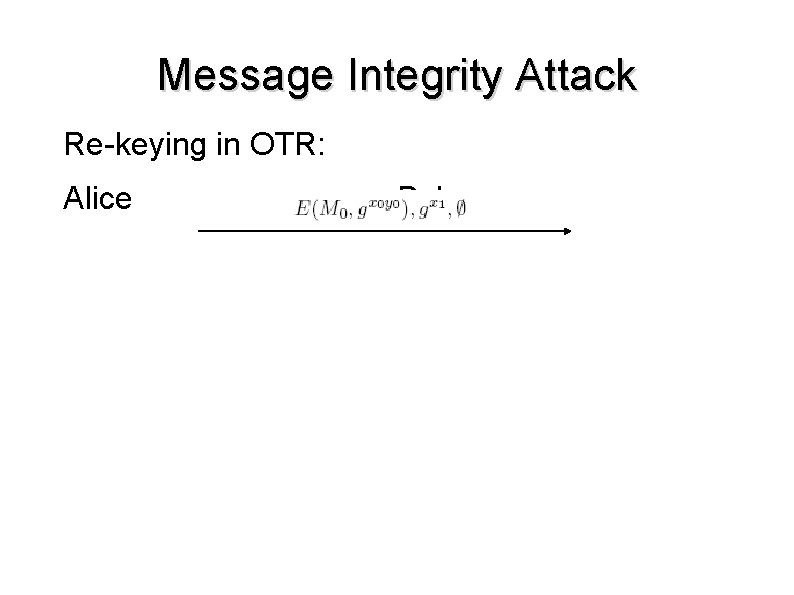
Message Integrity Attack Re-keying in OTR: Alice Bob

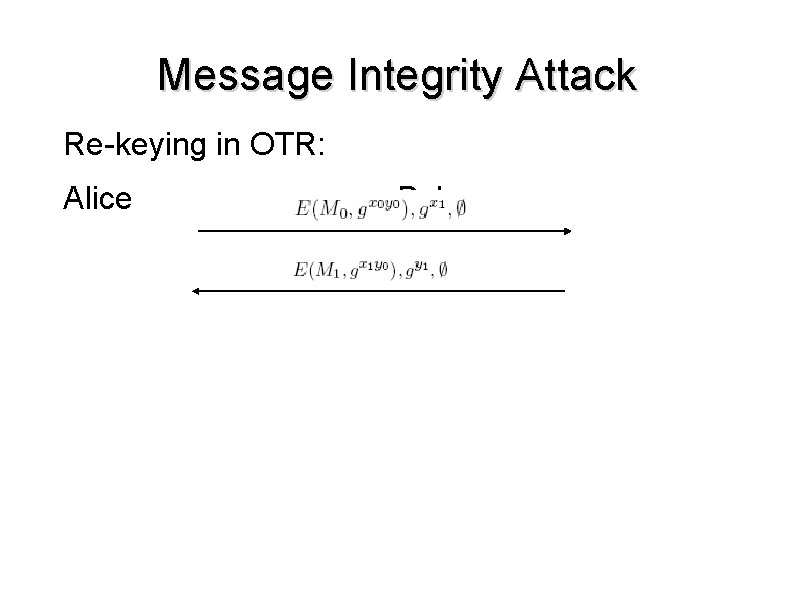
Message Integrity Attack Re-keying in OTR: Alice Bob

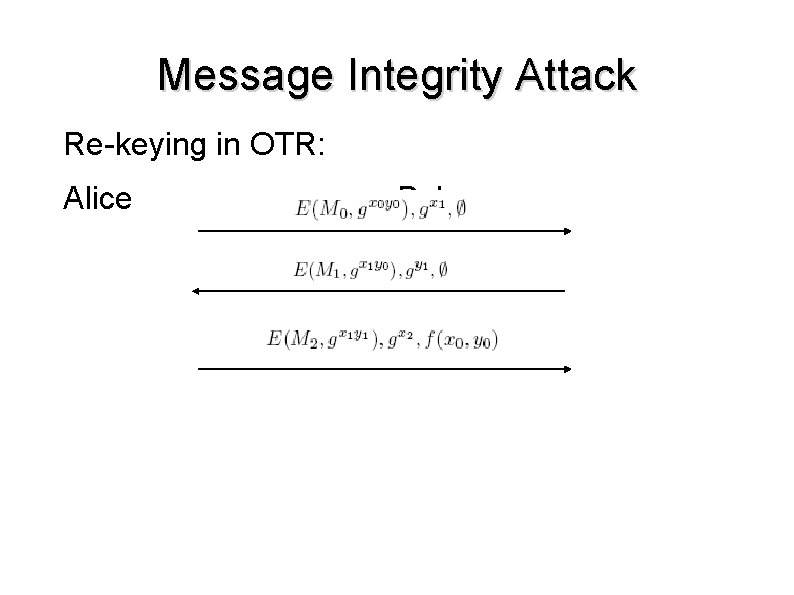
Message Integrity Attack Re-keying in OTR: Alice Bob

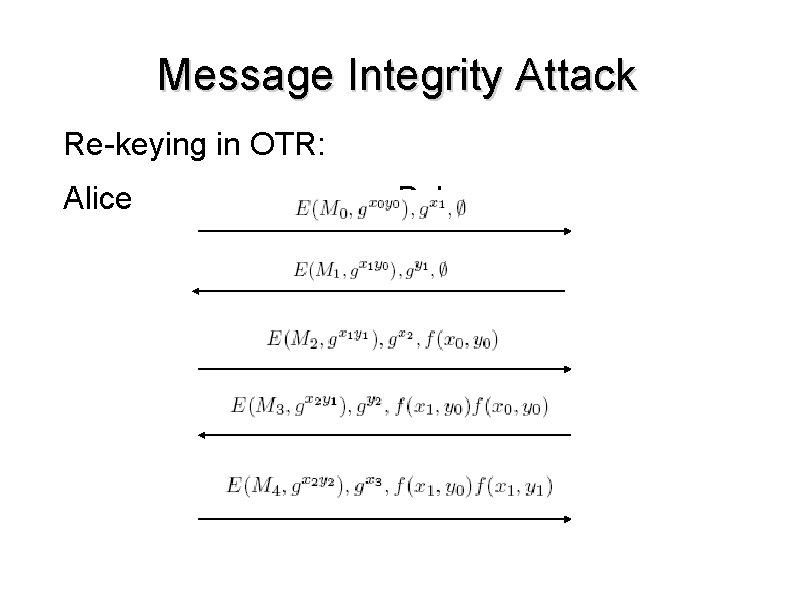
Message Integrity Attack Re-keying in OTR: Alice Bob

Message Integrity Attack ● ● ● Mallory blocks a message containing published MAC keys Mallory uses published keys to re-send a modified message to Bob thinks it was sent before his message was received. Negative feature interaction occurring between forward

Message Integrity Attack The Official Response: . . . Good call on this one. Bizarrely, it doesn't turn out to be a security hole in the deployed software because there's a bug in it. (!) The deployed software only publishes MAC keys that were used to receive messages, not ones on messages it sent. This is safe, because it knows for sure that it'll never trust a MAC key that it's already published. . . - OTR Author Ian Goldberg