OPERATING SYSTEM EXPLOITS ON WINDOWS AND LINUX PLATFORMS

























- Slides: 29

OPERATING SYSTEM EXPLOITS ON WINDOWS AND LINUX PLATFORMS Group 5 Mervin Hamblin Jing Huang Joseph Schneider Chinmay Trivedi

Some Basic Exploits �Why is there problems with OS ? �Basic vulnerabilities existing in OS: �Invalidated Input �Race Conditions ○ Time of check – Time of use. ○ Inter-process communication �Buffer Overflows ○ Stack Overflow ○ Heap Overflow

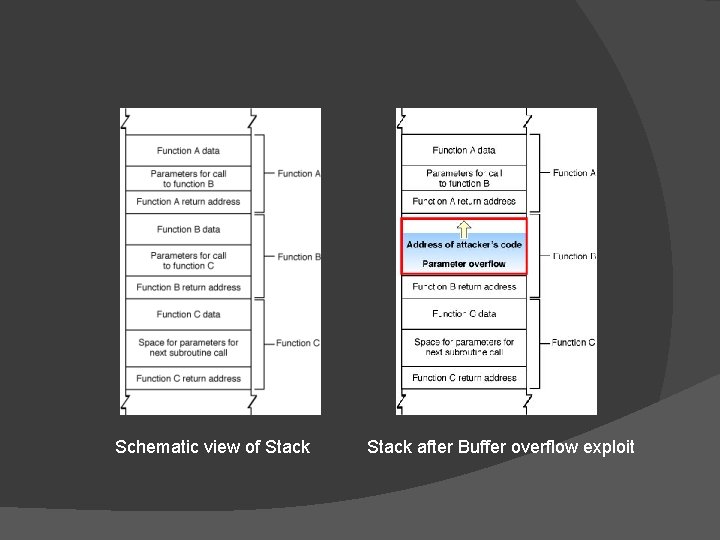
Schematic view of Stack after Buffer overflow exploit

Linux Exploits � Invalidated input causing Cross site scripting attack: �Linux kernel setroubleshoot Invalidated Input vulnerability ○ Input which is passed via process and file names are not properly sanitized before being saved when an AVC denial event takes place. This can be exploited to insert arbitrary HTML and script code, which is executed in a user's browser session in context of an affected site when the malicious logs are viewed. ○ Explanation ○ Impact

� Buffer overflow vulnerabilities in Linux kernel causing Denial of Service attack: �Linux Kernel kfree_skb Vulnerability. ○ Memory leak in the ipip 6_rcv function in net/ipv 6/sit. c in the Linux kernel 2. 4 before 2. 4. 36. 5 and 2. 6 before 2. 6. 25. 3 allows remote attackers to cause a denial of service (memory consumption) via network traffic to a Simple Internet Transition (SIT) tunnel interface, related to the pskb_may_pull and kfree_skb functions, and management of an skb reference count ○ Explanation ○ Impact

Security Bypass: Linux kernel readv/writev Security Bypass Vulnerability. ○ Certain modifications to the Linux kernel 2. 6. 16 and earlier do not add the appropriate Linux Security Modules (LSM) file_permission hooks to the (1) readv and (2) writev functions, which might allow attackers to bypass intended access restrictions. ○ Explanation ○ Impact

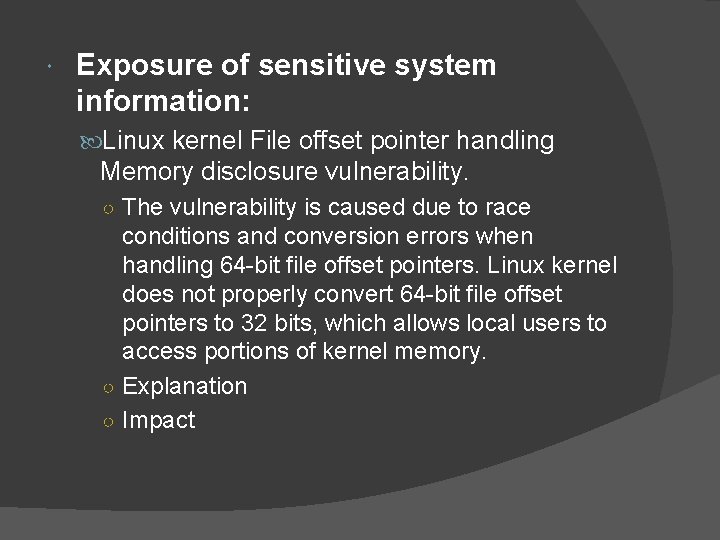
Exposure of sensitive system information: Linux kernel File offset pointer handling Memory disclosure vulnerability. ○ The vulnerability is caused due to race conditions and conversion errors when handling 64 -bit file offset pointers. Linux kernel does not properly convert 64 -bit file offset pointers to 32 bits, which allows local users to access portions of kernel memory. ○ Explanation ○ Impact

Privilege Escalation: Linux kernel cups and cupsys Privilege Escalation: ○ pstopdf in CUPS 1. 3. 8 allows local users to overwrite arbitrary files via a symlink attack on the /tmp/pstopdf. log temporary file which can be exploited by malicious, local users to perform certain actions with escalated privileges. ○ Explanation ○ Impact

Attack against ASLR Address space layout randomization, or ASLR, is an idea to introduce artificial diversity by randomizing the memory location of certain system components. � ASLR + DEP : Stronger Defense against memory manipulation vulnerabilities. � W X Pages and Return to libc attack: � �In this technique, the pages in heap, stack and other memory segments are marked either writeable (W) or executable (X), but not both. �Impacts of using W X pages. �Attack against this scheme - return to libc attack.

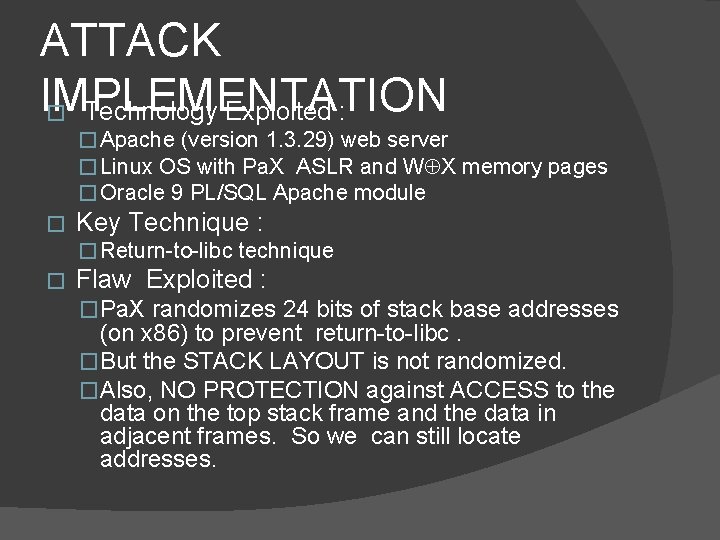
ATTACK IMPLEMENTATION � Technology Exploited : � Apache (version 1. 3. 29) web server � Linux OS with Pa. X ASLR and W X memory pages � Oracle 9 PL/SQL Apache module � Key Technique : � Return-to-libc technique � Flaw Exploited : �Pa. X randomizes 24 bits of stack base addresses (on x 86) to prevent return-to-libc. �But the STACK LAYOUT is not randomized. �Also, NO PROTECTION against ACCESS to the data on the top stack frame and the data in adjacent frames. So we can still locate addresses.

� Repeatedly overflow the stack buffer exposed by Oracle hole and find delta mmap �Guess address of usleep() �Incorrect guess -> crashes Apache’ child process & parent forks new child with same deltas �Correct guess -> hangs up connection for 16 s and delta mmap is deduced. �Delta mmap provides locations of all libc functions � Mount a shell by executing return-to-libc attack on the same buffer and invoke system() function.

Windows Market Share Vulnerability Process Windows Vulnerabilities Windows Exploits

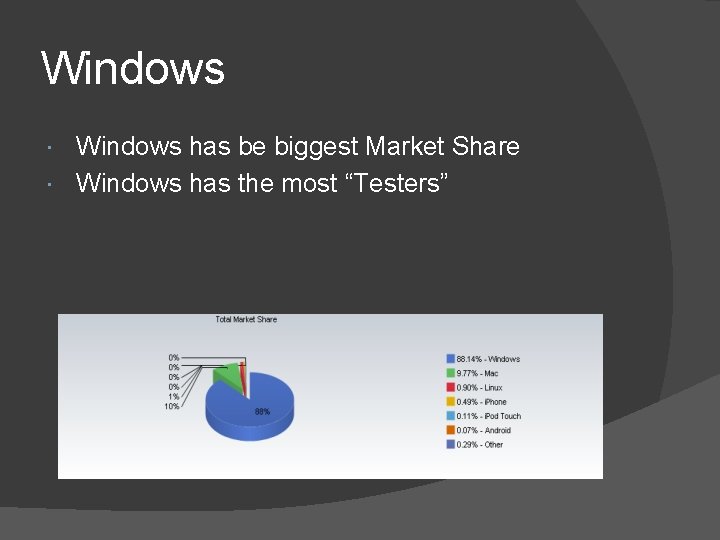
Windows has be biggest Market Share Windows has the most “Testers”

Vulnerabilities Discovery From Data Sources ○ Security. Focus, Internet Security Systems, etc. Assigned CVE Identifiers CVE – Common Vulnerabilities & Exposures Candidate Status CVE Editorial Board discusses Candidate & Votes If Accepted Status is Changed to Entry

Windows Vulnerabilities National Vulnerability Database 10 Most Recent Vulnerabilities Must be Windows Specific Windows XP and Windows Server 2003 Discuss Four Vulnerabilities

Windows Kernel Input Validation Vulnerability CVE-2009 -0081 March 10, 2009 CVSS Severity: 9. 3 (High) Microsoft Rating: Critical What is the Vulnerability & How can it be Exploited

Explanation – Remote Code Execution The Windows Kernel does not properly validate input passed from user mode through the kernel component of GDI. Mitigation – Apply Patch (MS 09 -006) Must be user invoked. How Exploited? Use specially crafted image files ○ Website ○ Email No known Exploits Consequence Attacker could install programs; view, change, delete data; or create user.

SMB Buffer Overflow Remote Code Execution Vulnerability CVE-2008 -4834 January 13, 2009 CVSS Security: 10. 0 (High) Microsoft Rating: Critical What is the Vulnerability & How can it be Exploited

Explanation – Remote Code Execution The vulnerability is caused by the Microsoft Server Message Block (SMB) Protocol software insufficiently validating the buffer size before writing to it. Mitigation – Apply Patch (MS 09 -01) Firewall best practices Upgrade Windows (Vista, Server 2008) How Exploited? Create specially crafted SMB messages No known exploits Consequence Denial of Service

Use-After-Free Vulnerability CVE-2008 -4844 December 11, 2008 CVSS Severity: 9. 3 (High) Microsoft Rating: Critical What is the Vulnerability & How can it be Exploited

Explanation – Remote Code Execution The vulnerability exists as an invalid pointer reference in the data binding function of Internet Explorer 6. Mitigation – Apply Patch (MS 08 -078) Must be user invoked Gains the same rights as local user Upgrade to Internet Explorer 7 How Exploited? Specially crafted web site to call function There are Exploits Consequence Attacker could gain the same user rights as the local user.

SMB Credential Reflection Vulnerability CVE-2008 -4037 November 12, 2008 CVSS Severity: 9. 3 (High) Microsoft Rating: Important What is the Vulnerability & How can it be Exploited

Explanation – Remote Code Execution The SMB protocol does not correctly opt-in to NTLM credential-reflection protections. Mitigation – Apply Patch (MS 08 -068) Firewall best practices Gains the same rights as local user Upgrade Windows (Vista, Server 2008) How Exploited? Requires a user with affected SMB to access a malicious server. No know Exploits Consequences Attacker could gain the same user rights as the local user.

Against OS Exploits A complementary investigation on the practices toward a safer OS environment What can PC users do? What are researchers doing?

Best practices for computer users Install operating system patches. Verify user account security. Eliminate unnecessary applications and network services. Install and configure necessary applications and network services Configure system logging to record significant events. Keep applications and operating system patches up to date

Best practices for computer users Password Security Secure file transfer and remote login SSH Software tools Secure-It™ (Windows) Bastille Linux

Research on OS security Secure Auditing System in Linux Kernel improve the original auditing mechanism of Linux and strengthen the security management of audit logs Live Updating Operating Systems Using Virtualization through which patches and upgrades can be applied without rebooting Secure Virtual Architecture provide a safe execution environment for an entire operating system and all its applications

Against OS Exploits Root: secure programming is not established Theory Practice Education Training Effective and fully practical protecting approaches still remain a challenge.

Demonstration