Noninteractive Zero Knowledge Arguments for Voting Jens Groth











- Slides: 17

Non-interactive Zero. Knowledge Arguments for Voting Jens Groth UCLA

Voting process Voters Authorities E(vote) + NIZK argument + signature . . . Check signatures Check NIZK arguments Multi-party computation Result

Encryption Homomorphic property E(m 1+m 2) = E(m 1) * E(m 2) Threshold property t authorities can decrypt t-1 authorities cannot decrypt

Single vote elections Candidates 0, 1, . . . , L-1 M > # voters Encoding M 0, M 1, . . . , ML-1 Encrypted votes E(M 2), E(M 1), E(M 2), . . . Authorities Ek = E(M 2) E(M 1) E(M 2). . . = E(M 2+M 1+M 2+. . . ) = E( vi. Mi) Threshold decrypt vi. Mi Result

Contributions Many types of elections - Single vote - Limited vote (each voter N votes) - Shareholder election (each voter Nk votes) - Approval voting (each voter up to L votes) - Borda voting (preferential vote) n Efficient NIZK arguments - random oracle model n

Encoding votes Voter k ivik. Mi Single vote vik = 0, 1 and ivik = 1 Limited vote vik = 0, 1 and ivik = N Approval vote vik = 0, 1 and ivik ≤ L Shareholder vote vik ≥ 0 and ivik = Nk Borda vote vik = πk(i+1) for permutation πk

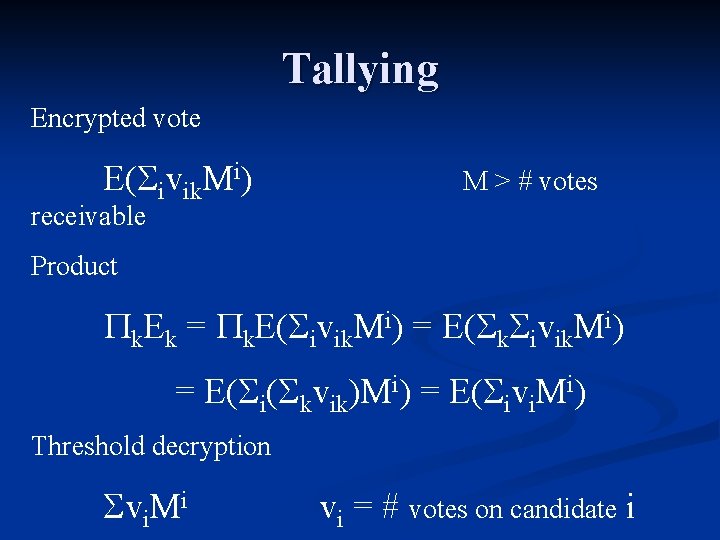
Tallying Encrypted vote E( ivik. Mi) M > # votes receivable Product k. Ek = k. E( ivik. Mi) = E( k ivik. Mi) = E( i( kvik)Mi) = E( ivi. Mi) Threshold decryption vi. Mi vi = # votes on candidate i

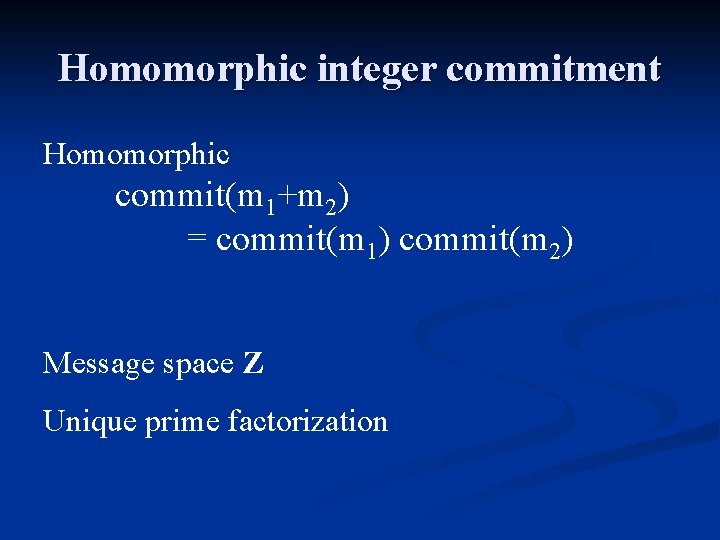
Homomorphic integer commitment Homomorphic commit(m 1+m 2) = commit(m 1) commit(m 2) Message space Z Unique prime factorization

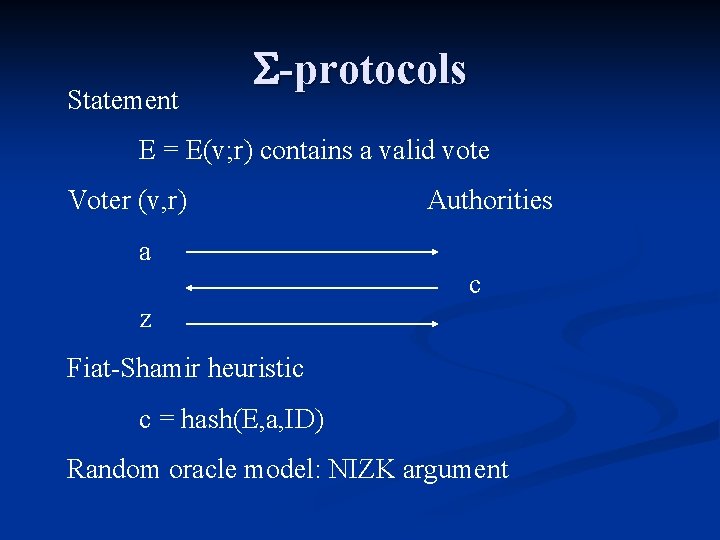
Statement -protocols E = E(v; r) contains a valid vote Voter (v, r) Authorities a c z Fiat-Shamir heuristic c = hash(E, a, ID) Random oracle model: NIZK argument

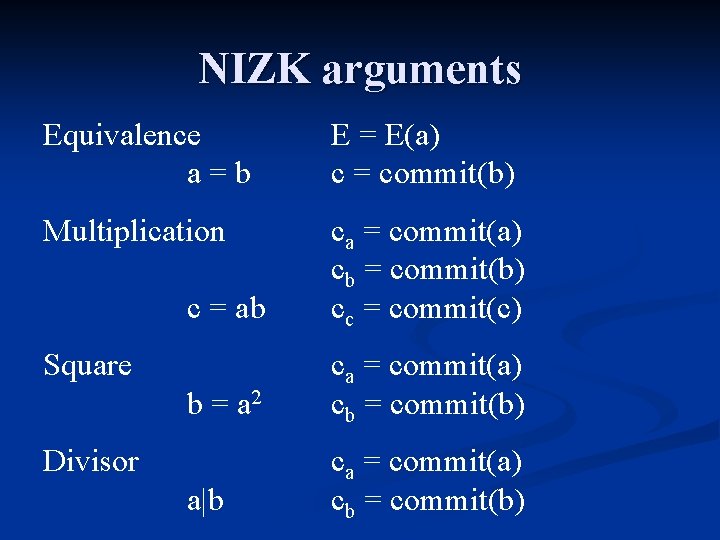
NIZK arguments Equivalence a=b E = E(a) c = commit(b) Multiplication c = ab ca = commit(a) cb = commit(b) cc = commit(c) b = a 2 ca = commit(a) cb = commit(b) a|b ca = commit(a) cb = commit(b) Square Divisor

Encrypted vote Single vote E = E(Mi) M = p 2, p prime NIZK argument ca = commit(pi) 1 Divisor NIZK (ca, commit(p. L-1; 0)) cb = commit(Mi) Square NIZK (ca, cb) a|p. L a 2 = p 2 i

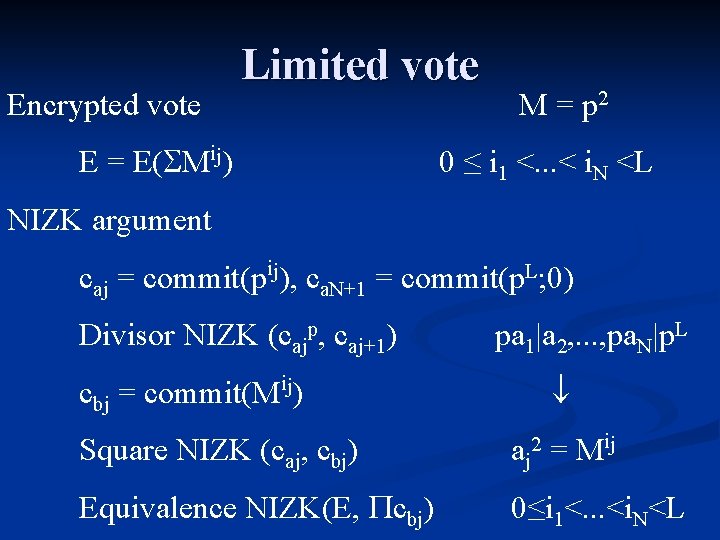
Limited vote Encrypted vote ij E = E( M ) M = p 2 0 ≤ i 1 <. . . < i. N <L NIZK argument caj = commit(pij), ca. N+1 = commit(p. L; 0) Divisor NIZK (cajp, caj+1) pa 1|a 2, . . . , pa. N|p. L cbj = commit(Mij) =M ij Square NIZK (caj, cbj) a j 2 Equivalence NIZK(E, cbj) 0≤i 1<. . . <i. N<L

Approval vote Encrypted vote E = E( ai. Mi) ai = 0, 1 NIZK argument cai = commit(ai) Square NIZK (cai, cai) Equivalence NIZK (E, cai a i 2 = a i ai = 0, 1 Mi ) ai. Mi

Commitment Non-negativity c = commit(m) m≥ 0 Idea 4 m+1 = x 2 + y 2 + z 2 NIZK argument cx = commit(x) cy = commit(y) cz = commit(z) cx 2 = commit(x 2) cy 2 = commit(y 2) cz 2 = commit(z 2) Square NIZKs (cx, cx 2) (cy, cy 2) (cz, cz 2) Equivalence NIZK (c 4 commit(1; 0), cx 2 cy 2 cz 2)

Shareholder vote Encrypted vote ai ≥ 0 and ai = N E = E( ai. Mi) NIZK argument cai = commit(ai) Non-negative NIZK (cai) ai ≥ 0 Equivalence NIZK (commit(N; 0), cai) Equivalence NIZK (E, cai Mi ) ai = N ai. Mi

Borda vote Encrypted vote E = E( ai. Mi-1) ai = π(i) NIZK argument cai = commit(ai) Known shuffle NIZK (1, 2, . . . , L, ca 1, . . . , ca. L) commitments contain 1, 2, . . . , L permuted Equivalence NIZK (E, cai Mi-1) ai. Mi-1

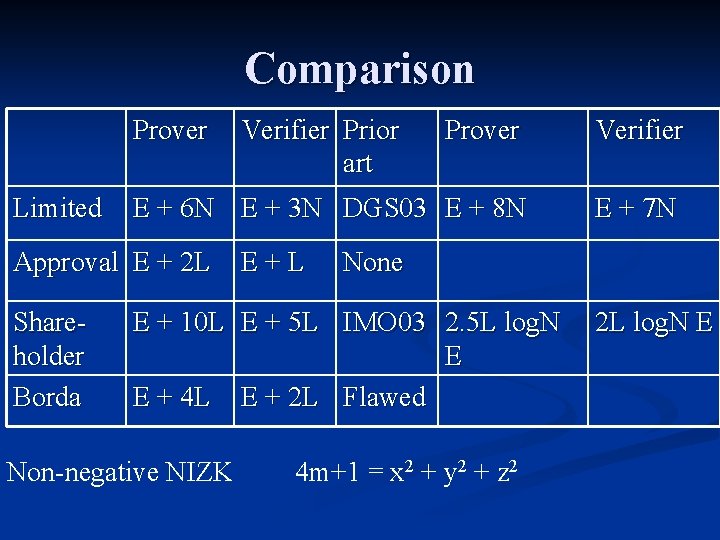
Comparison Prover Limited Prover Verifier E + 6 N E + 3 N DGS 03 E + 8 N E + 7 N Approval E + 2 L Shareholder Borda Verifier Prior art E+L None E + 10 L E + 5 L IMO 03 2. 5 L log. N E E + 4 L E + 2 L Flawed Non-negative NIZK 4 m+1 = x 2 + y 2 + z 2 2 L log. N E