Efficient ZeroKnowledge Proof Systems Jens Groth University College






![Soundness Statement x L Accept or reject Computational soundness: For ppt adversary Pr[Reject] ≈ Soundness Statement x L Accept or reject Computational soundness: For ppt adversary Pr[Reject] ≈](https://slidetodoc.com/presentation_image_h/8ad005b0db2c607a447e972a3ee5d245/image-23.jpg)


- Slides: 28

Efficient Zero-Knowledge Proof Systems Jens Groth University College London

Privacy and verifiability No! It is a trade secret. Hedge fund Did I lose all my money? Show me the current portfolio! Investor

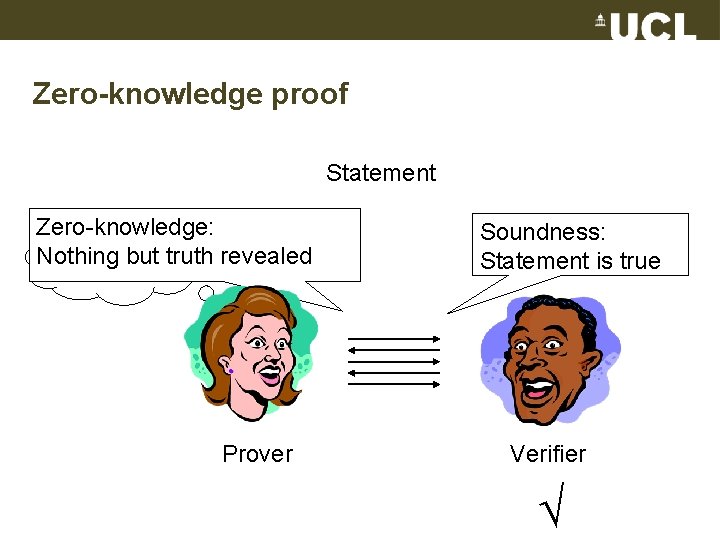
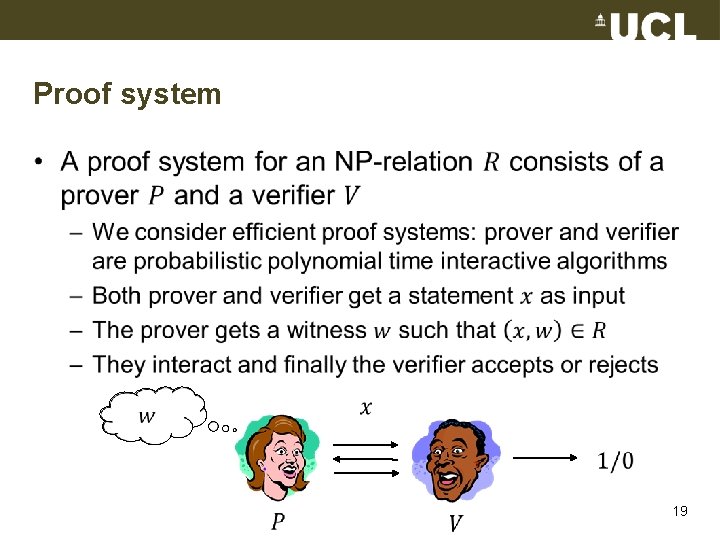
Zero-knowledge proof Statement Zero-knowledge: Witness Nothing but truth revealed Prover Soundness: Statement is true Verifier

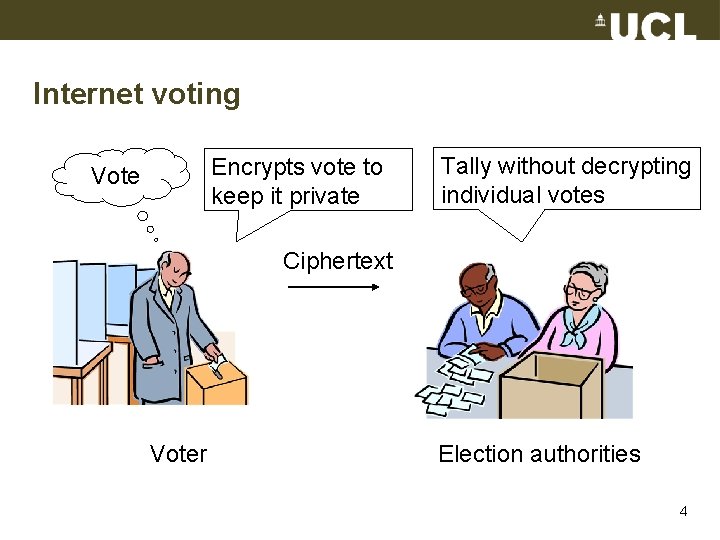
Internet voting Encrypts vote to keep it private Vote Tally without decrypting individual votes Ciphertext Voter Election authorities 4

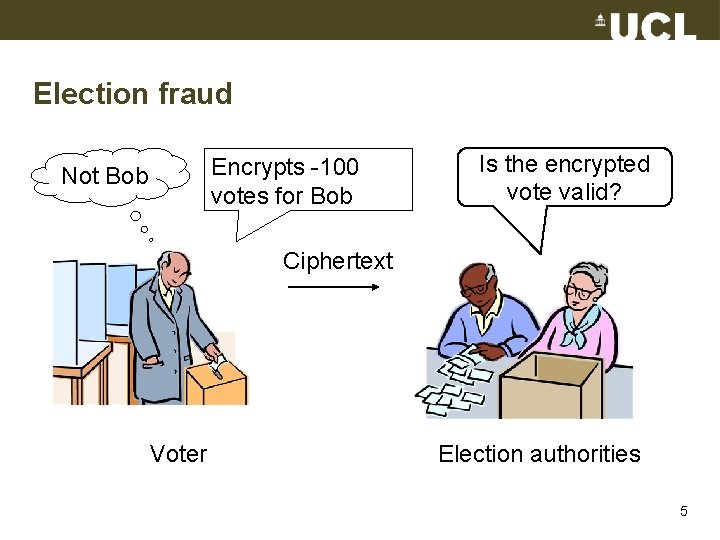
Election fraud Encrypts -100 votes for Bob Not Bob Is the encrypted vote valid? Ciphertext Voter Election authorities 5

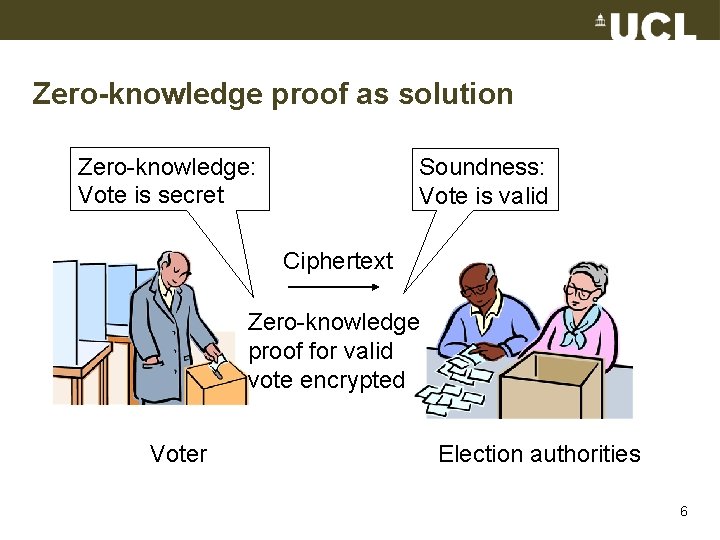
Zero-knowledge proof as solution Zero-knowledge: Vote is secret Soundness: Vote is valid Ciphertext Zero-knowledge proof for valid vote encrypted Voter Election authorities 6

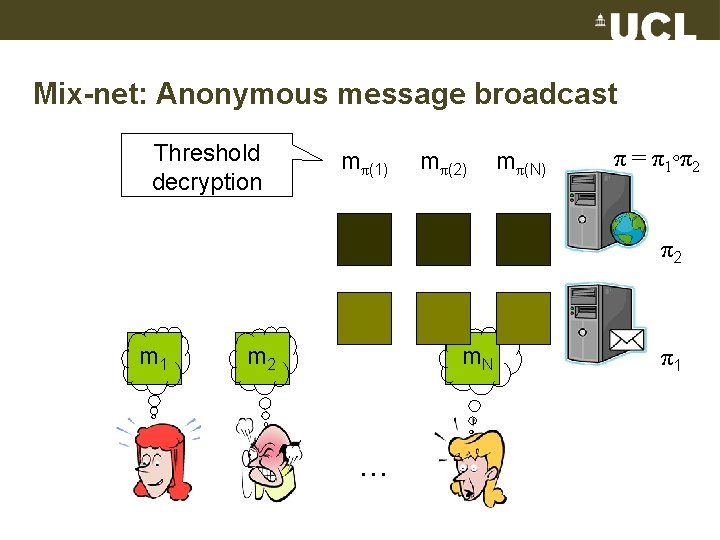
Mix-net: Anonymous message broadcast Threshold decryption mπ(1) mπ(2) mπ(N) π = π1◦π2 π2 m 1 m 2 m. N … π1

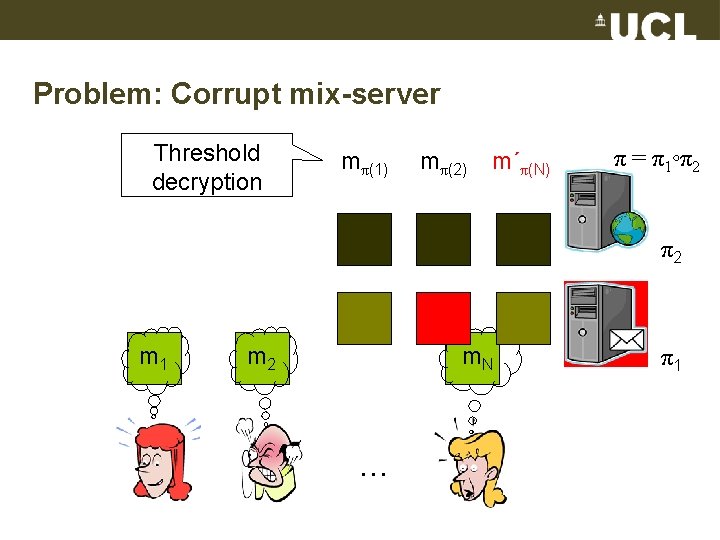
Problem: Corrupt mix-server Threshold decryption mπ(1) mπ(2) m´π(N) π = π1◦π2 π2 m 1 m 2 m. N … π1

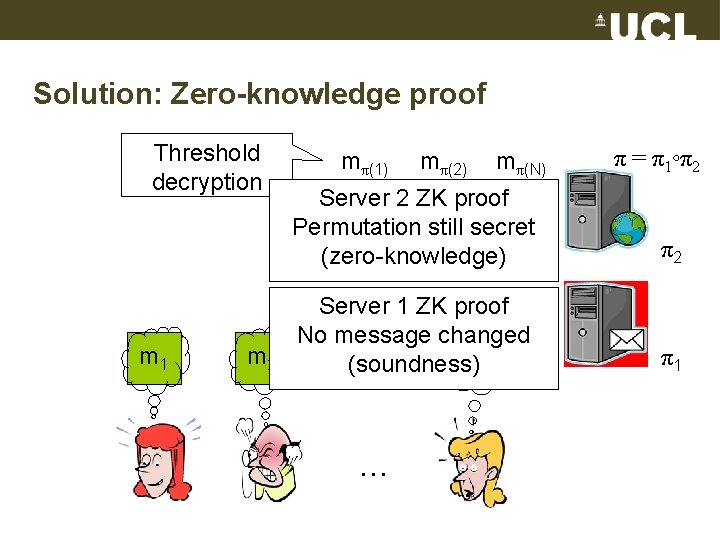
Solution: Zero-knowledge proof Threshold decryption m 1 m 2 mπ(1) mπ(2) mπ(N) π = π1◦π2 Server 2 ZK proof Permutation still secret (zero-knowledge) π2 Server 1 ZK proof No message changed m. N (soundness) π1 …

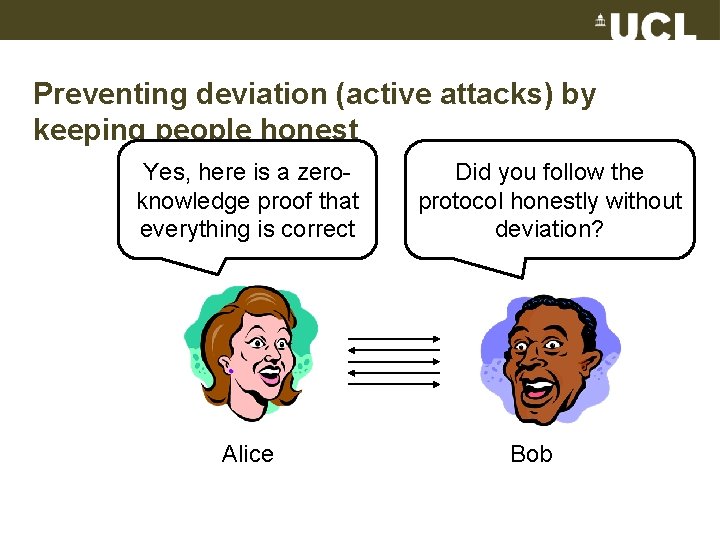
Preventing deviation (active attacks) by keeping people honest Yes, here is a zeroknowledge proof that everything is correct Alice Did you follow the protocol honestly without deviation? Bob

Cryptography Problems typically arise when attackers deviate from a protocol (active attack) Zero-knowledge proofs prevent deviation and give security against active attacks 11

Fundamental building block Доверяй, но проверяй - Trust but verify zero-knowledge signatures encryption 12

Zero-knowledge proofs • Completeness – Prover can convince verifier when statement is true • Soundness – Cannot convince verifier when statement is false • Zero-knowledge – No leakage of information (except truth of statement) even if interacting with a cheating verifier 13

Parameters • Efficiency – – Communication (bits) Prover’s computation (seconds) Verifier’s computation (seconds) Round complexity (number of messages) • Security – Setup – Cryptographic assumptions

Round complexity • Interactive zero-knowledge proof • Non-interactive zero-knowledge proof 15

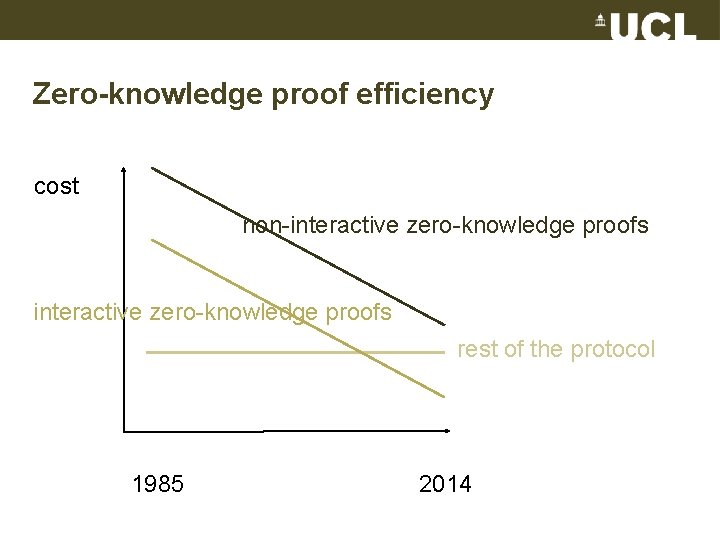
Zero-knowledge proof efficiency cost non-interactive zero-knowledge proofs rest of the protocol 1985 2014

Vision • Main goal – Efficient and versatile zero-knowledge proofs • Vision – Negligible overhead from using zero-knowledge proofs zero-knowledge core – Security against active attacks standard feature 17

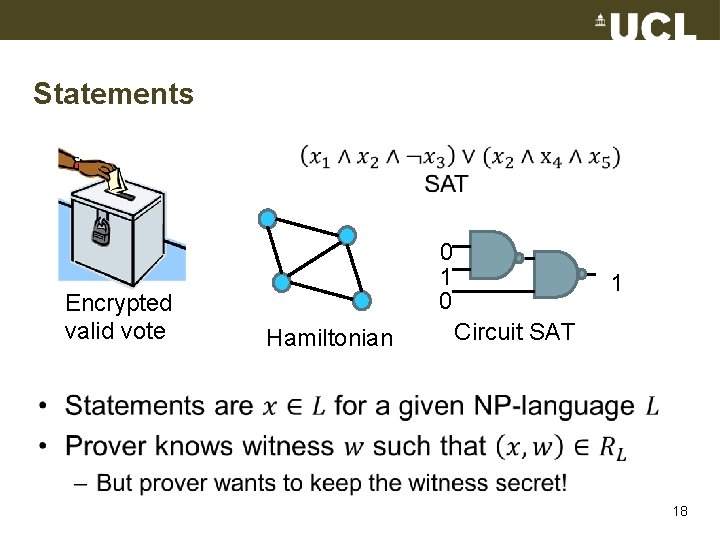
Statements Encrypted valid vote 0 1 0 Hamiltonian 1 Circuit SAT • 18

Proof system • 19

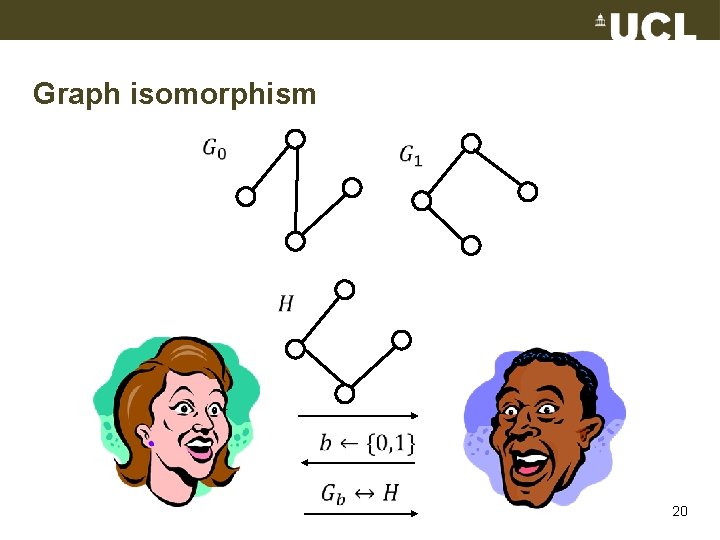
Graph isomorphism 20

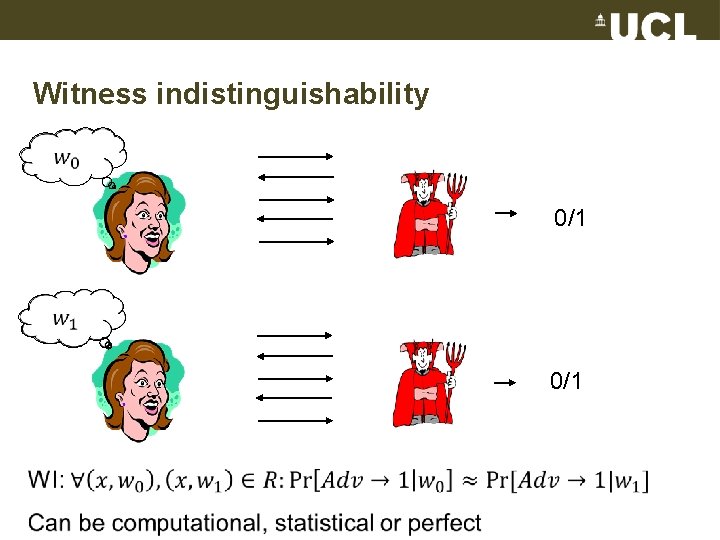
Exercise • Argue the GI proof system is complete • What is the probability of the prover cheating the verifier? (soundness) • Argue the GI proof system is witness indistinguishable, i. e. , when there are several isomorphisms between the two graphs it is not possible to know which one the prover has in mind 21

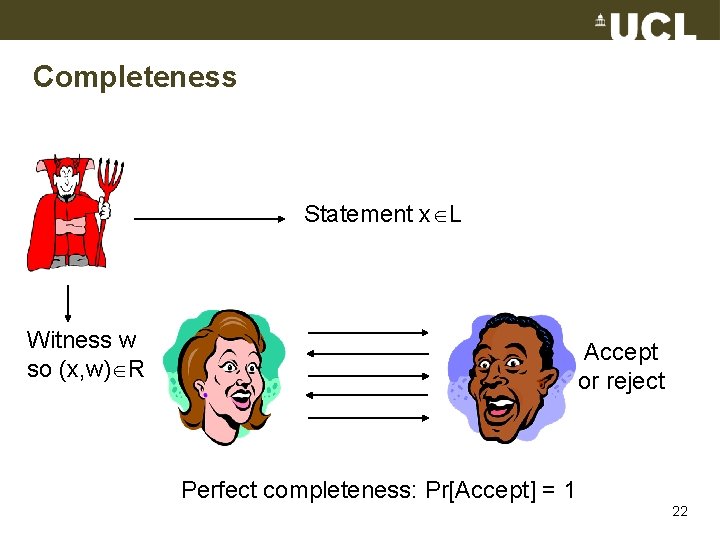
Completeness Statement x L Witness w so (x, w) R Accept or reject Perfect completeness: Pr[Accept] = 1 22
![Soundness Statement x L Accept or reject Computational soundness For ppt adversary PrReject Soundness Statement x L Accept or reject Computational soundness: For ppt adversary Pr[Reject] ≈](https://slidetodoc.com/presentation_image_h/8ad005b0db2c607a447e972a3ee5d245/image-23.jpg)
Soundness Statement x L Accept or reject Computational soundness: For ppt adversary Pr[Reject] ≈ 1 Statistical soundness: For any adversary Pr[Reject] ≈ 1 Perfect soundness: Pr[Reject] = 1 23

Arguments and proofs Arguments can be more efficient than proofs • Argument (or computationally sound proof) – Computational soundness, holds against polynomial time adversary, relies on cryptographic assumptions • Proof – Unconditional soundness, holds against unbounded adversary, and in particular without relying on cryptographic assumptions 24

Witness indistinguishability 0/1

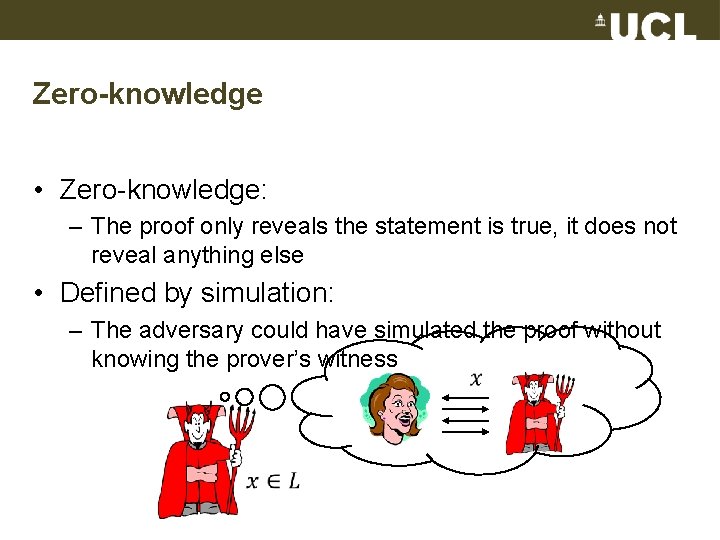
Zero-knowledge • Zero-knowledge: – The proof only reveals the statement is true, it does not reveal anything else • Defined by simulation: – The adversary could have simulated the proof without knowing the prover’s witness

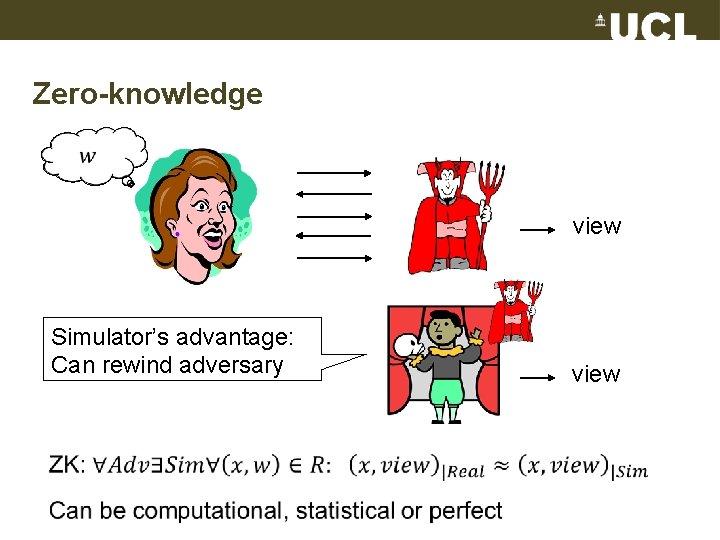
Zero-knowledge view Simulator’s advantage: Can rewind adversary view

Exercises • Show the GI proof is perfect zero-knowledge • Argue why zero-knowledge implies witness indistinguishability • Give an example of a language and a proof system that is witness indistinguishable but not zero-knowledge (under reasonable assumptions) 28