Network Security A Lecture 1 NETW 4006 Lecture















- Slides: 27

Network Security - A Lecture 1 - NETW 4006 -Lecture 01 1

Text Book &References • Linux Network Security – Peter G. Smith – Charles River Media • Principle of Information Security – Second Edition – Michael E. Whitman and Herbert J. Mattord – Thomson Course Technology • William Stallings – Cryptography and Network Security. Prentice Hall NETW 4006 -Lecture 01 2

Content NETW 4006 -Lecture 01 3

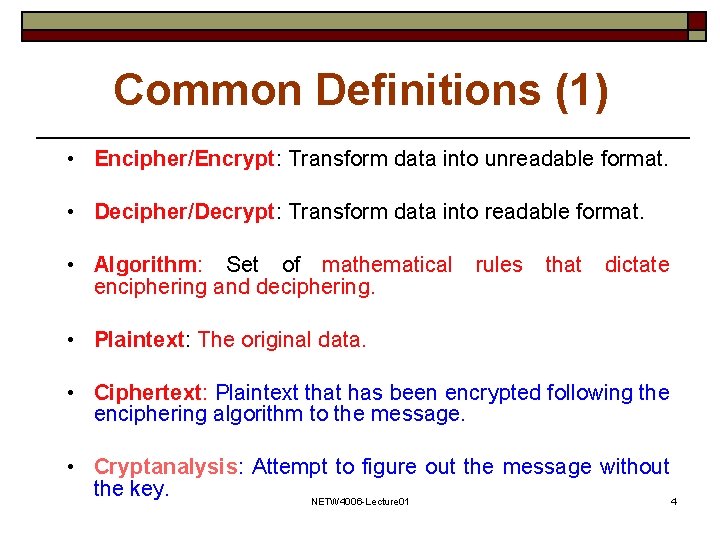
Common Definitions (1) • Encipher/Encrypt: Transform data into unreadable format. • Decipher/Decrypt: Transform data into readable format. • Algorithm: Set of mathematical enciphering and deciphering. rules that dictate • Plaintext: The original data. • Ciphertext: Plaintext that has been encrypted following the enciphering algorithm to the message. • Cryptanalysis: Attempt to figure out the message without the key. NETW 4006 -Lecture 01 4

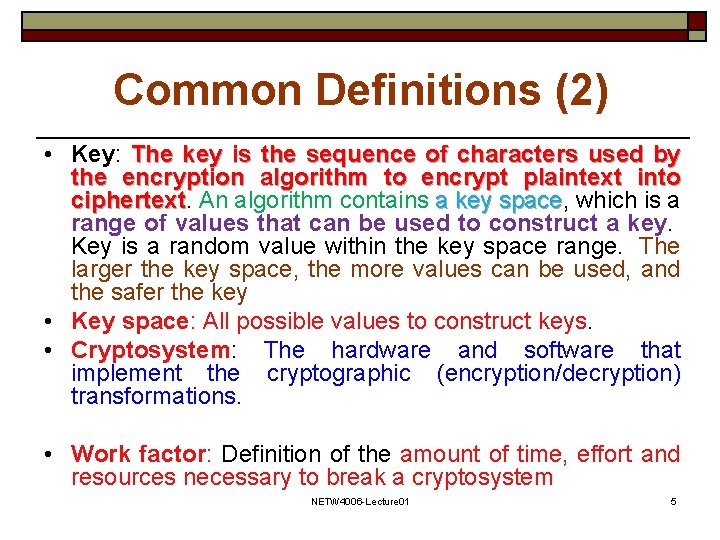
Common Definitions (2) • Key: The key is the sequence of characters used by the encryption algorithm to encrypt plaintext into ciphertext An algorithm contains a key space, space which is a range of values that can be used to construct a key. Key is a random value within the key space range. The larger the key space, the more values can be used, and the safer the key • Key space: All possible values to construct keys. • Cryptosystem: The hardware and software that implement the cryptographic (encryption/decryption) transformations. • Work factor: Definition of the amount of time, effort and resources necessary to break a cryptosystem NETW 4006 -Lecture 01 5

Common Definitions (3) • Confidentiality: The fact of ensuring that information is accessible only to those authorized to have access o Authenticity: The quality of actually coming from the source which is claimed o Integrity: The assurance that information has not been accidentally or maliciously altered or destroyed o Non-Repudiation: The non-repudiation is a way to guarantee that the sender of the message can not later deny having sent the message or having furnished the signature of a message NETW 4006 -Lecture 01 6

Cryptography. . o Cipher Mechanism based up on a Policy. . A C I N Authentication Confidentiality Integrity 7 Non Repudiation.

Cryptography. . A C I N C A I N Confidentiality is Privacy So 8 P A I N

Cryptography. . See. . 9

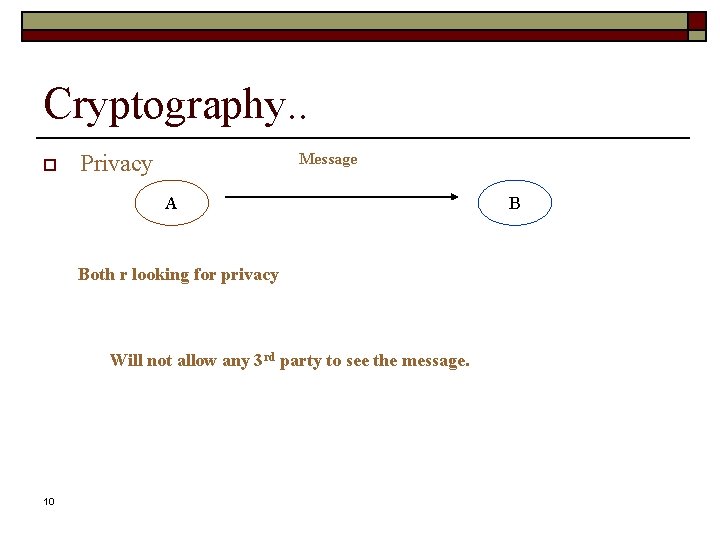
Cryptography. . o Privacy Message A Both r looking for privacy Will not allow any 3 rd party to see the message. 10 B

Cryptography. . o Authentication A & B has to authenticate themselves… i. e. B should get the confidence that this message is from A. 11

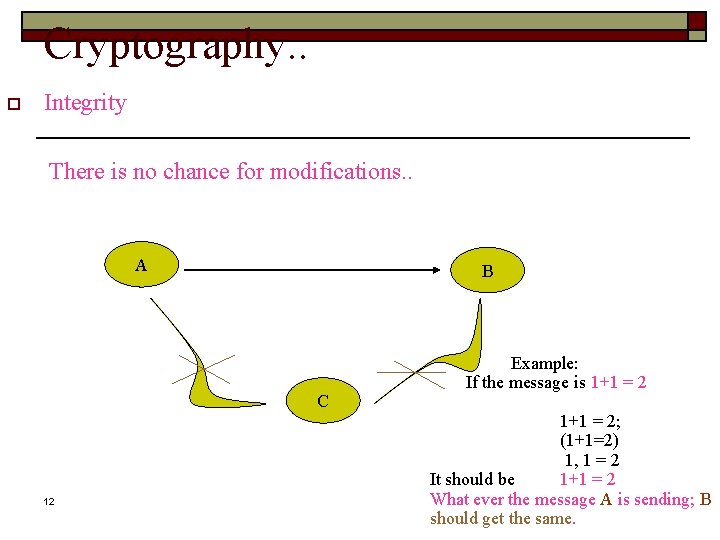
Cryptography. . o Integrity There is no chance for modifications. . A B C 12 Example: If the message is 1+1 = 2; (1+1=2) 1, 1 = 2 It should be 1+1 = 2 What ever the message A is sending; B should get the same.

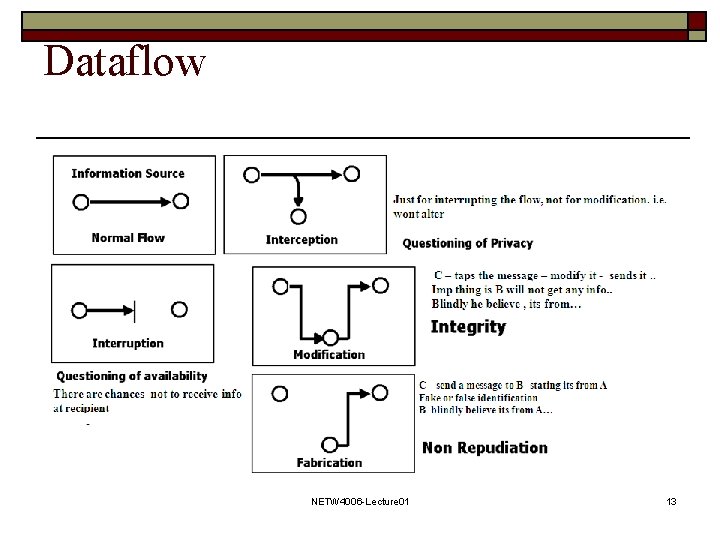
Dataflow NETW 4006 -Lecture 01 13

Cryptographic System Strength • Strength of encryption comes from: Algorithm, secrecy of key, length of key, initialization vectors, and how they all work together. • Improper protection of the key can seriously weaken the cryptosystem • Goals of cryptosystems: confidentiality, authenticity, integrity, non repudiation NETW 4006 -Lecture 01 14

Symmetric and Asymmetric Encryption (1) • Symmetric ciphers use a Pre-Shared-Key (PSK). The same key is used for both encrypting and decrypting • Primary advantage: faster than asymmetric ciphers, ciphers hard to break with large key. • Primary disadvantage: difficult to distribute key (how to securely transmit the key? ). Can we re-key on longer connections, to protect against the key being broken? Cannot authenticate or provide nonrepudiation • Includes: DES (Date Encryption Standard), Triple DES, IDEA (International Data Encryption Algorithm), RC 4, RC 5, AES (Advanced Encryption Standard) NETW 4006 -Lecture 01 15

o How to exchange the key ? ? ? 1. A can select a key and physically deliver it to B 2. A third party can select the key and physically deliver it to A and B 3. If A and B have previously and recently used a key, one party can transmit the new key to the other, encrypted using the old key NETW 4006 -Lecture 01 16

Symmetric and Asymmetric Encryption (2) • Asymmetric ciphers use a public/private key-pair Keys are mathematically linked such that what is encrypted with one is only decrypted by the other. • Keys are linked so that it is computationally hard to guess the private key having the public key • You must keep your private key secret Often encrypted with a pass-phrase • You disclose your public key to whoever wants to communicate with you • You can have your public key signed by a mutually trusted Certificate Authority (CA) (see next) so people can be certain that it is really your key NETW 4006 -Lecture 01 17

Symmetric and Asymmetric Encryption (3) n n n Advantages: Better at key distribution, better scalability for large systems, can provide authentication and non-repudiation Disadvantages: Asymmetric ciphers are many times slower than symmetric ciphers Includes: RSA (Rivest, Shamir, Adelman), Diffie Hellman, El Gamal, DSA (Digital Signature Algorithm), Knapsack, PGP (Pretty Good Privacy). NETW 4006 -Lecture 01 18

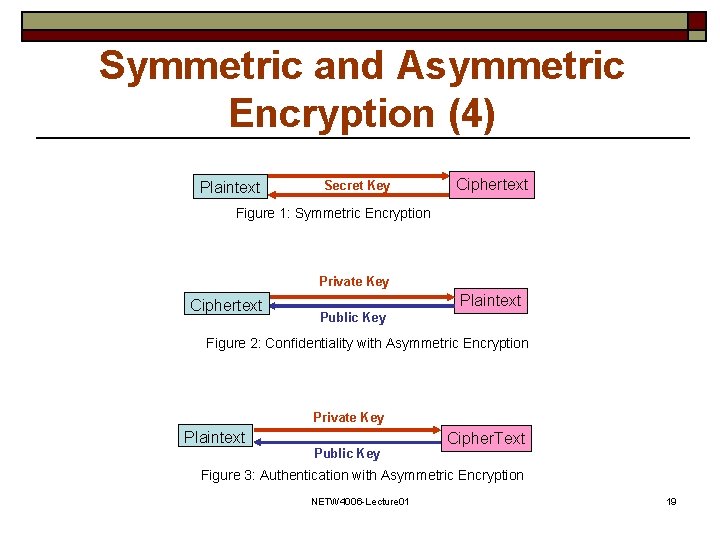
Symmetric and Asymmetric Encryption (4) Plaintext Secret Key Ciphertext Figure 1: Symmetric Encryption Private Key Ciphertext Public Key Plaintext Figure 2: Confidentiality with Asymmetric Encryption Private Key Plaintext Public Key Cipher. Text Figure 3: Authentication with Asymmetric Encryption NETW 4006 -Lecture 01 19

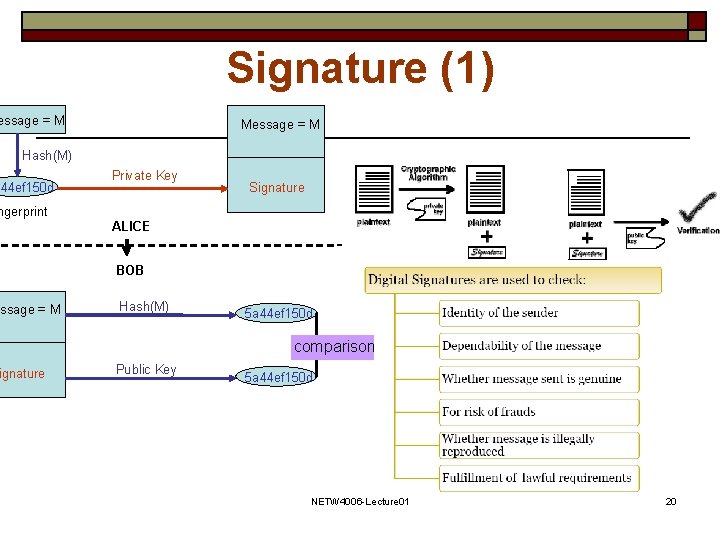
Signature (1) essage = M Message = M Hash(M) a 44 ef 150 d Private Key Signature ngerprint essage = M ignature ALICE BOB Hash(M) 5 a 44 ef 150 d comparison Public Key 5 a 44 ef 150 d NETW 4006 -Lecture 01 20

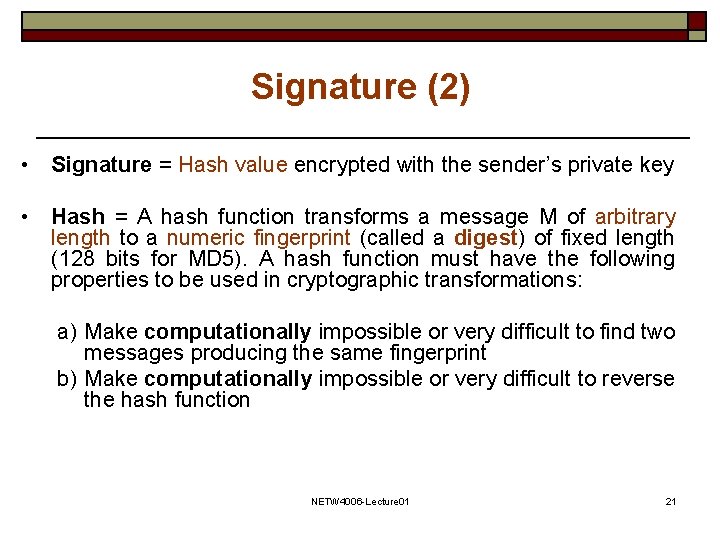
Signature (2) • Signature = Hash value encrypted with the sender’s private key • Hash = A hash function transforms a message M of arbitrary length to a numeric fingerprint (called a digest) of fixed length (128 bits for MD 5). A hash function must have the following properties to be used in cryptographic transformations: a) Make computationally impossible or very difficult to find two messages producing the same fingerprint b) Make computationally impossible or very difficult to reverse the hash function NETW 4006 -Lecture 01 21

Signature (3) o o Due to a) and b) hash functions are used to ensure the integrity of a message when transmitted through a non secure channel Act of signing means encrypting message’s hash value with private key n n Ensures integrity, authentication, and nonrepudiation: Ensures that message was not altered and also came from Bob Hash includes: DSS (Digital Signature Standard), MD 2 (Message Digest 2), MD 4, MD 5, SHA (Secure Hash Algorithm) NETW 4006 -Lecture 01 22

Key Signing and PKC (1) • Certificate is a document provided by a trustworthy authority (organization). The certificate associates the public key of an asymmetric ciphering algorithm to information related to a subject (user name, server name, E-mail address, etc. ). The goal of a certificate is the authenticated association between a subject and its public key Certification Authority (CA): Trusted entity that issues certificates • • • Multiple issuers pose validation problem: Alice’s CA is Cathy, Bob’s CA is Don; how can Alice validate Bob’s certificate? Have Cathy and Don cross-certify: Each issues certificate for the other NETW 4006 -Lecture 01 23

Key Signing and PKC (2) • A digital certificate is usually signed by a CA (CA’s private key), in order to prove that the CA generated the certificate (non-repudiation) • CA’s signature: This is achieved by the CA hashing the certificate (the hash value will change if anything in the certificate changes), and then encrypting the hash value of the certificate with the CA private key. The CA includes the resulting digital signature in the certificate, making it signed and provides it to the requester. NETW 4006 -Lecture 01 24

Key Signing and PKC (3) • Verification of the CA’s signature: The CA signature can be verified by a third party by decrypting the digital signature with the CA’s public key, and comparing the certificate hash value to the result of the hash function applied to the certificate. If there is a difference, either the certificate has been altered (integrity) or the signature has been generated with a private key that does not match the CA’s public key. Usually the main CA certificates containing the CA public key are already installed in the Netscape Communicator, Firefox and Internet Explorer, allowing the automatic verification of the CA’s signature. NETW 4006 -Lecture 01 25

X. 509 Standard (1) • Definition: X. 509 is the ITU (International Telecommunication Union) standard that specifies the content of a numeric certificate. Key certificate fields in X. 509 v 3 • • • Version Serial number (unique) Signature algorithm identifier: hash algorithm (ex: MD 5) Issuer’s name: uniquely identifies issuer (CA) Interval of validity Subject’s name; uniquely identifies subject (Alice) Subject’s public key Signature • • Identifies algorithm used to sign the certificate (ex: RSA) Signature (enciphered hash) NETW 4006 -Lecture 01 26

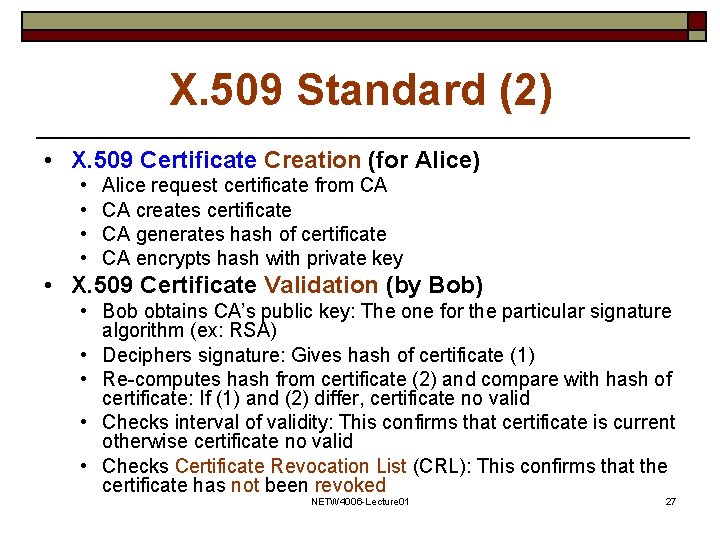
X. 509 Standard (2) • X. 509 Certificate Creation (for Alice) • • Alice request certificate from CA CA creates certificate CA generates hash of certificate CA encrypts hash with private key • X. 509 Certificate Validation (by Bob) • Bob obtains CA’s public key: The one for the particular signature algorithm (ex: RSA) • Deciphers signature: Gives hash of certificate (1) • Re-computes hash from certificate (2) and compare with hash of certificate: If (1) and (2) differ, certificate no valid • Checks interval of validity: This confirms that certificate is current otherwise certificate no valid • Checks Certificate Revocation List (CRL): This confirms that the certificate has not been revoked NETW 4006 -Lecture 01 27