Nested Merkles Puzzles Against Sampling Attacks Shlomi Dolev

















- Slides: 29

Nested Merkle's Puzzles Against Sampling Attacks Shlomi Dolev, Nova Fandina, Ximing Li Department of Computer Science, Ben-Gurion University of the Negev, Israel

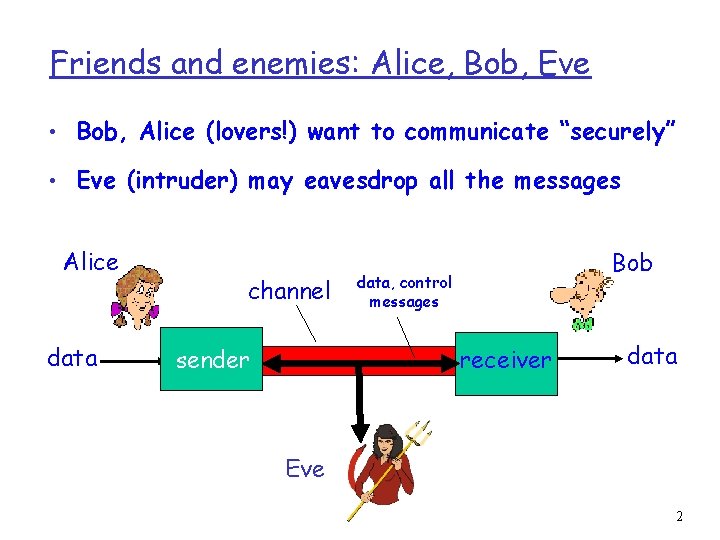
Friends and enemies: Alice, Bob, Eve • Bob, Alice (lovers!) want to communicate “securely” • Eve (intruder) may eavesdrop all the messages Alice data channel sender Bob data, control messages receiver data Eve 2

Merkle’s puzzles • Ralph Merkle (Stanford, 1974) project proposal for CS 244 at U. C. Berkeley. • Merkle’s puzzles are a way of doing key exchange between Alice and Bob • With Authorized communication link • Without the need for a KDC 3

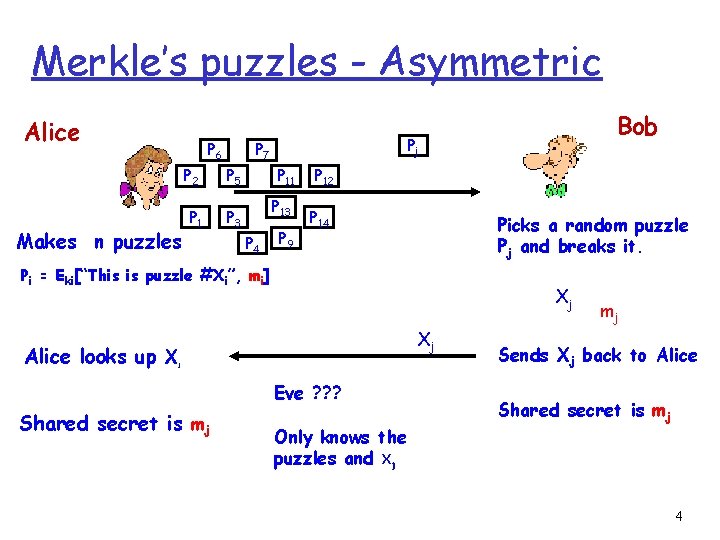
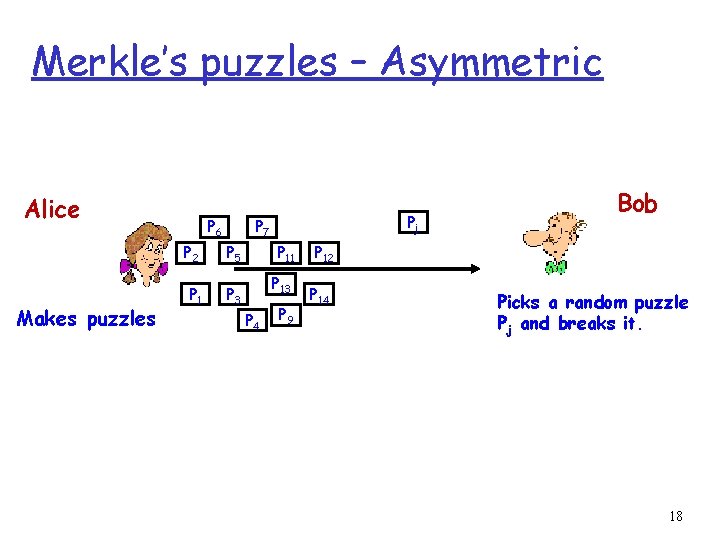
Merkle’s puzzles - Asymmetric Alice P 6 Makes n puzzles Pj P 7 P 2 P 5 P 1 P 3 P 11 P 13 P 4 P 9 P 12 P 14 Picks a random puzzle Pj and breaks it. Pi = Eki[“This is puzzle #Xi”, mi] Alice looks up X Xj Xj j Eve ? ? ? Shared secret is mj Bob Only knows the puzzles and Xj mj Sends Xj back to Alice Shared secret is mj 4

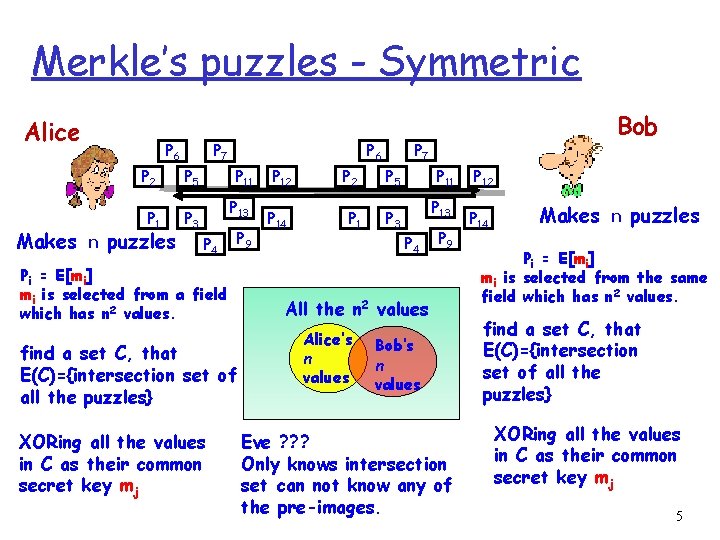
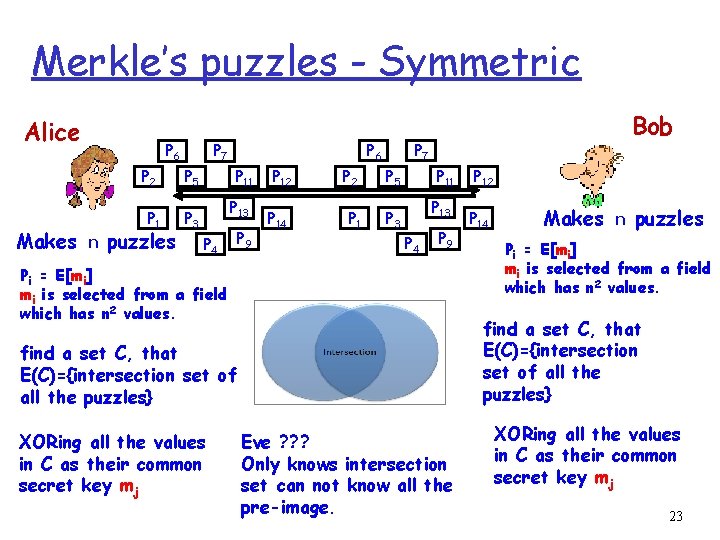
Merkle’s puzzles - Symmetric Alice Makes P 6 n P 2 P 5 P 1 P 3 puzzles P 6 P 7 P 11 P 13 P 4 P 9 Pi = E[mi] mi is selected from a field which has n 2 values. find a set C, that E(C)={intersection set of all the puzzles} XORing all the values in C as their common secret key mj Bob P 7 P 12 P 5 P 14 P 1 P 3 P 11 P 13 P 4 P 9 All the n 2 values Alice’s n values Bob’s n values Eve ? ? ? Only knows intersection set can not know any of the pre-images. P 12 P 14 Makes n puzzles Pi = E[mi] mi is selected from the same field which has n 2 values. find a set C, that E(C)={intersection set of all the puzzles} XORing all the values in C as their common secret key mj 5

Introduction –An example • Alice and Bob are two brokers that coordinate their actions every hour. They establish keys using Merkle's puzzles scheme. • Eve would like to decrypt their communication. • • If Eve is not lucky to choose the right puzzles, Eve does not participate in the stock-exchange in that hour. If Eve is lucky, Eve buys or sells according to their plans in the specific hour. She will get a lot of money. 6

Attack: sampling attack • In every round of the protocol: • • Eve randomly chooses some puzzles being exchanged between Alice and Bob in the present round and stores all the rest in her memory (possibly for a later processing) Eve performs computational processing on the puzzles she has chosen. 7

Outline • Introduction • Problem Specification • Nested Merkle’s Puzzles in the Random Oracle Model • Discussion

Introduction – Our question • Our question is whether the original Merkle's puzzles protocol is secure enough to be used repeatedly in scenario of long communication • • Alice and Bob have agreed on a secret key, after O(n^2) time Eve will reveal the key. An intuitive proactive solution is to run the key agreement protocol again, after some time, to establish a fresh key. 9

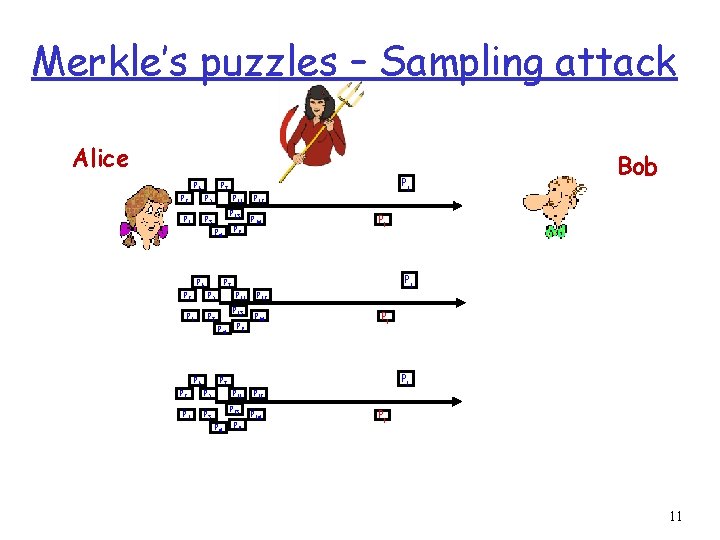
Introduction – Sampling attack • Consider an adversary which records all the information exchanged. • Assume the adversary Eve is performing the following attack. • • In each round Eve randomly chooses only one puzzle (or some constant number, δ, of the puzzles) to solve. If Eve is lucky, Eve will choose the same puzzle as Bob, and thus will be able to decrypt and listen to the communication in the current round of the session with the decrypted key! 10

Merkle’s puzzles – Sampling attack Alice P 6 Pj P 7 P 2 P 5 P 1 P 3 P 11 P 13 P 9 P 4 P 6 P 5 P 1 P 3 P 6 P 14 Pj Pj P 11 P 13 P 4 P 2 P 12 P 7 P 2 P 9 P 12 P 14 Pj Pj P 7 P 5 P 11 P 13 P 4 Bob P 9 P 12 P 14 Pj 11

Introduction -Sampling attack • Repeating, iteratively, the key agreement protocol, there will be a round (one from every O(n) rounds) in which Eve will guess the right puzzle with high probability. • We call this kind of attack as sampling attack. 12

Introduction –Our contribution • We propose a key exchange protocol which is resistant to the sampling attack and find out a non obsolete session key. • The idea is to keep every round be dependent on the previous ones. • • Use the secret keys established in the previous rounds to encrypt the puzzles in the next round. In this way, Eve cannot start to solve puzzles without solving the puzzles from the previous rounds.

Introduction –Our contribution • We: • Increase the security gap in every round • Provide an ability to use the Merkle’ puzzle protocol for continuously secure communication

Outline • Introduction • Problem Specification • Nested Merkle’s Puzzles in the Random Oracle Model • Nested Merkle’s Puzzles in the Standard Model • Discussion

Nested Merkle’s puzzles in the random oracle model • Use the secret keys established in the previous round to protect the puzzles in the present round. • The honest parties can run the protocol infinitely, while using the keys from the previous rounds as the rounds keys. • With this method, parties do not need to wait in order to start to communicate securely. • The security level in such a scenario is growing with time. 16

Nested Merkle’s puzzles in the random oracle model • Use the secret keys established in the previous round to protect the puzzles in the present round. • The honest parties can run the protocol infinitely, while using the keys from the previous rounds as the rounds keys. • With this method, parties do not need to wait in order to start to communicate securely. • The security level in such a scenario is growing with time. 17

Merkle’s puzzles – Asymmetric Alice Makes puzzles P 6 Pj P 7 P 2 P 5 P 1 P 3 P 11 P 13 P 4 P 9 Bob P 12 P 14 Picks a random puzzle Pj and breaks it. 18

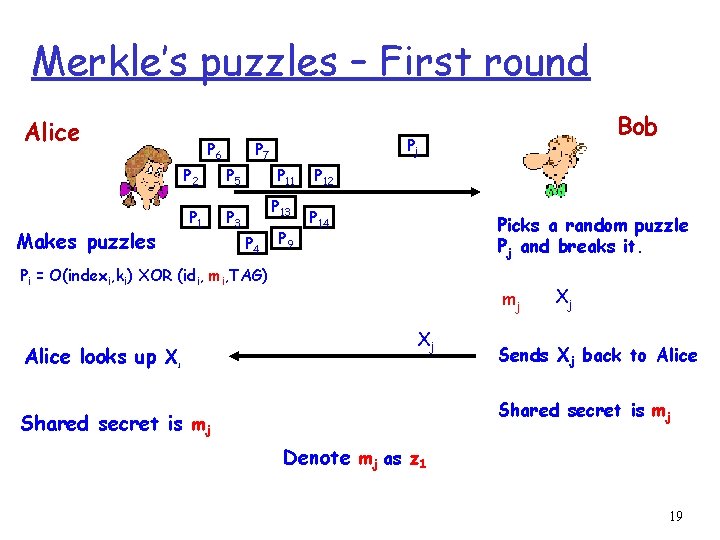
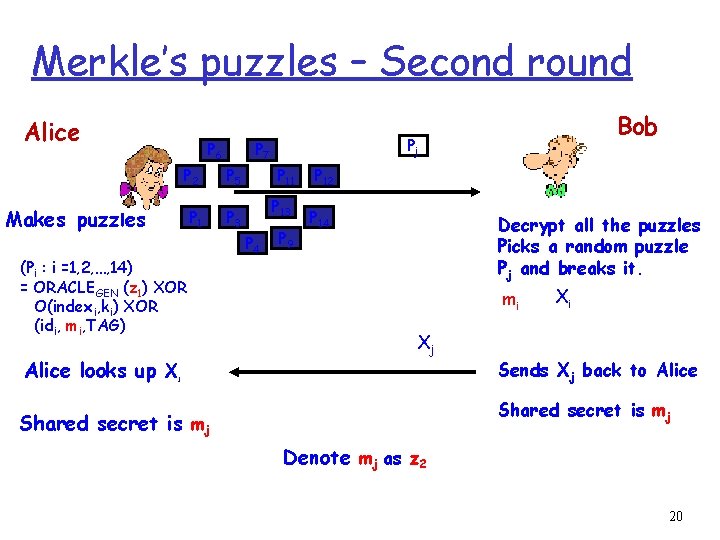
Merkle’s puzzles – First round Alice P 6 Makes puzzles Pj P 7 P 2 P 5 P 1 P 3 P 11 P 13 P 4 P 9 P 12 P 14 Picks a random puzzle Pj and breaks it. Pi = O(indexi, ki) XOR (idi, mi, TAG) Alice looks up X Bob mj Xj Sends Xj back to Alice Shared secret is mj Denote mj as z 1 19

Merkle’s puzzles – Second round Alice P 6 P 5 P 1 P 3 Makes puzzles (Pi : i =1, 2, …, 14) = ORACLEGEN (z 1) XOR O(indexi, ki) XOR (idi, mi, TAG) Alice looks up X Pj P 7 P 2 P 11 P 13 P 4 Bob P 9 P 12 P 14 Decrypt all the puzzles Picks a random puzzle Pj and breaks it. mi Xj j Xi Sends Xj back to Alice Shared secret is mj Denote mj as z 2 20

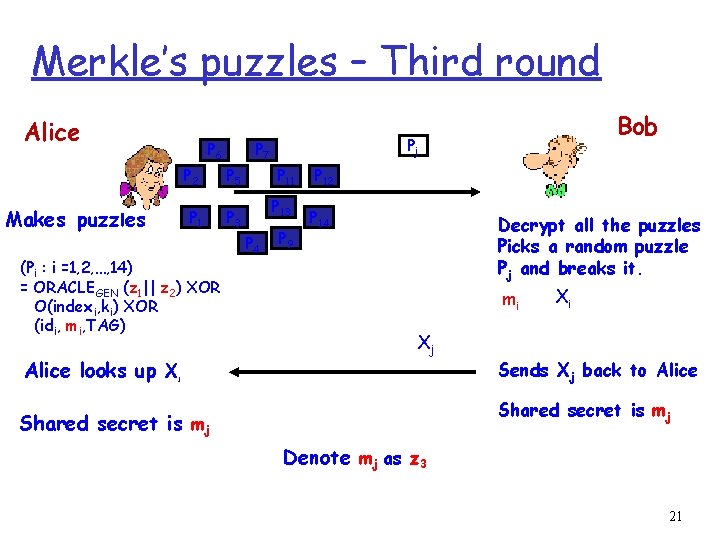
Merkle’s puzzles – Third round Alice P 6 Makes puzzles P 5 P 1 P 3 (Pi : i =1, 2, …, 14) = ORACLEGEN (z 1|| z 2) XOR O(indexi, ki) XOR (idi, mi, TAG) Alice looks up X Pj P 7 P 2 P 11 P 13 P 4 Bob P 9 P 12 P 14 Decrypt all the puzzles Picks a random puzzle Pj and breaks it. mi Xj j Xi Sends Xj back to Alice Shared secret is mj Denote mj as z 3 21

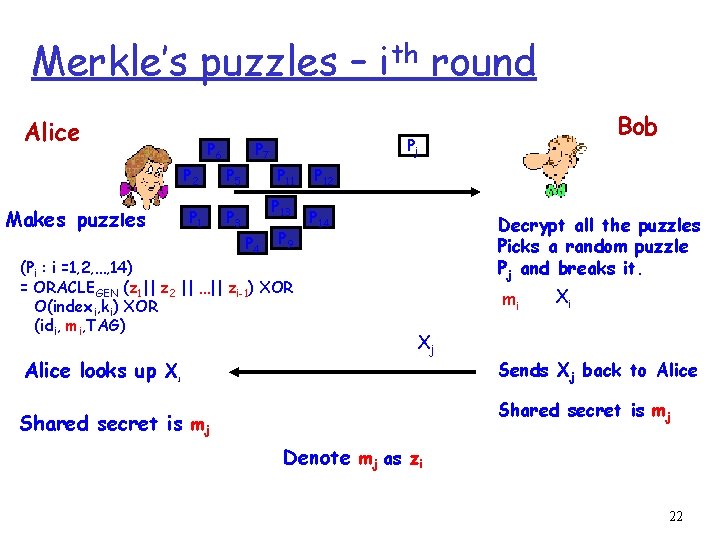
Merkle’s puzzles – ith round Alice P 6 Makes puzzles Pj P 7 P 2 P 5 P 1 P 3 P 11 P 13 P 4 P 9 (Pi : i =1, 2, …, 14) = ORACLEGEN (z 1|| z 2 || …|| zi-1) XOR O(indexi, ki) XOR (idi, mi, TAG) Alice looks up X Bob P 12 P 14 Decrypt all the puzzles Picks a random puzzle Pj and breaks it. mi Xj j Xi Sends Xj back to Alice Shared secret is mj Denote mj as zi 22

Merkle’s puzzles - Symmetric Alice Makes P 6 n P 2 P 5 P 1 P 3 puzzles P 6 P 7 P 11 P 13 P 4 P 9 Bob P 7 P 12 P 5 P 14 P 1 P 3 P 11 P 13 P 4 P 9 Pi = E[mi] mi is selected from a field which has n 2 values. P 14 Makes n puzzles Pi = E[mi] mi is selected from a field which has n 2 values. find a set C, that E(C)={intersection set of all the puzzles} XORing all the values in C as their common secret key mj P 12 Eve ? ? ? Only knows intersection set can not know all the pre-image. XORing all the values in C as their common secret key mj 23

Nested Merkle’s puzzles in the random oracle model • Symmetric nested Merkle’s puzzles has nearly the same structure with the asymmetric nested Merkle’s puzzles • Omitted here 24

Outline • Introduction • Problem Specification • Nested Merkle’s Puzzles in the Random Oracle Model • Nested Merkle’s Puzzles in the Standard Model • Discussion

Fast Nested Merkle's Puzzles Protocol (for asymmetric model) • Improve the security of the system by accelerate the rate of puzzle sending. • Actually Alice needs not to wait for Bob to send the ID back, it will cost her a lot of time to wait. Alice just sends puzzles to Bob at every time no matter she receives information from Bob or not. 26

Merkle's Puzzles Protocol Based on Broadcast Channel • Assume there is a random source which broadcast a long random bit string Str to all the parties. Alice, Bob and adversary Eve will get all of them without error. • Alice and Bob publically agree on n 2 oracles. They randomly choose n of the oracles and perform the oracle on Str , send the result to each other. • By the Birthday Paradox, they will find a collision set which can be used to construct session key. 27

Conclusion • We presented – Sampling attack in the Merkle’s puzzles protocol – Nested Merkle's puzzles protocol in the random oracle model – Nested Merkle's puzzles protocol in strandard model 28
