Vehicle to Vehicle Authentication Shlomi Dolev 1 2

- Slides: 12

Vehicle to Vehicle Authentication Shlomi Dolev 1 2 1 Łukasz Krzywiecki Nisha Panwar Michael Segal 1 1 Ben-Gurion University of the Negev, Israel, 2 Wroclaw University of Technology, Poland. 1/30/2022 1

Contents • Basic scheme: no hardware. • Certificating vehicle public key with vehicle attributes. • Intermediate scheme: simple LASER. • Dynamic attribute based vehicle authentication. • Sophisticated scheme: Physically Unclonable Function (PUF) device. • PUF based vehicle authentication. 1/30/2022 2

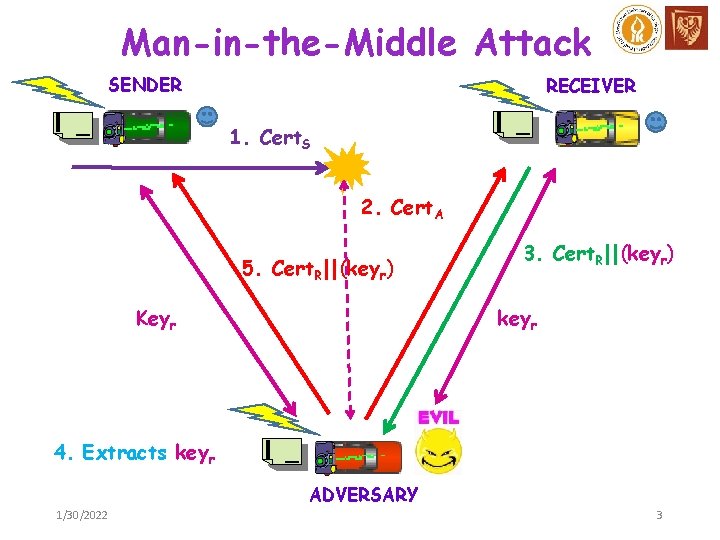
Man-in-the-Middle Attack SENDER RECEIVER 1. Cert. S 2. Cert. A 5. Cert. R||(keyr) Keyr 3. Cert. R||(keyr) keyr 4. Extracts keyr ADVERSARY 1/30/2022 3

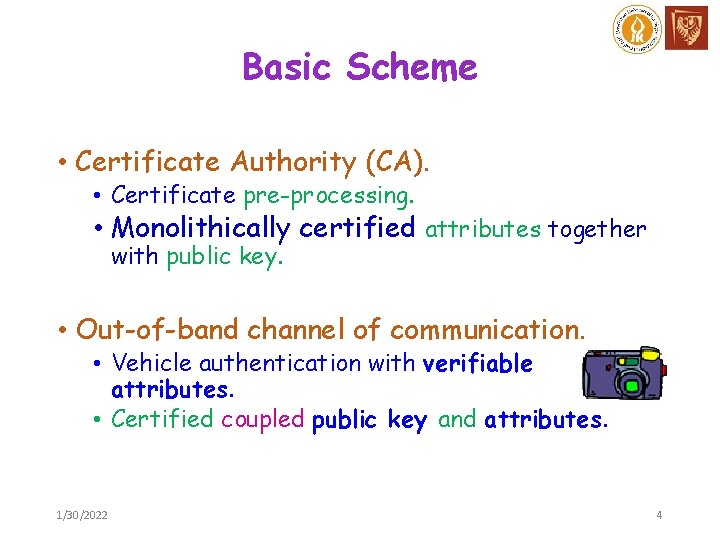
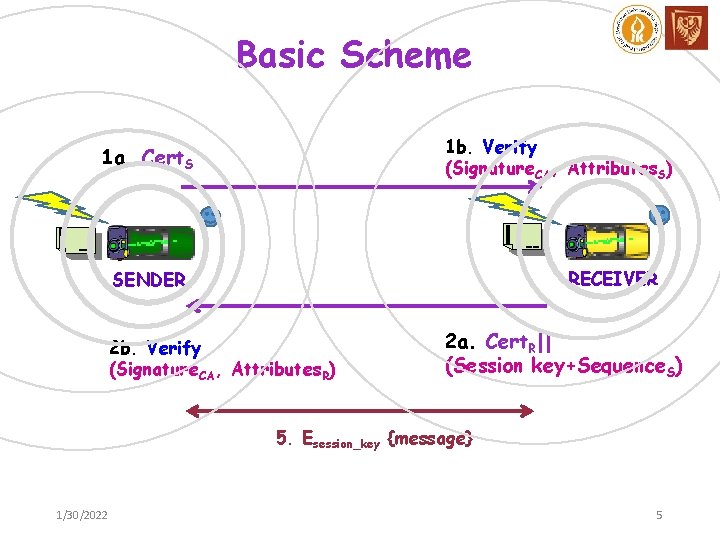
Basic Scheme • Certificate Authority (CA). • Certificate pre-processing. • Monolithically certified attributes together with public key. • Out-of-band channel of communication. • Vehicle authentication with verifiable attributes. • Certified coupled public key and attributes. 1/30/2022 4

Basic Scheme 1 b. Verify (Signature. CA, Attributes. S) 1 a. Cert. S RECEIVER SENDER 2 b. Verify (Signature. CA, Attributes. R) 2 a. Cert. R|| (Session key+Sequence. S) 5. Esession_key {message} 1/30/2022 5

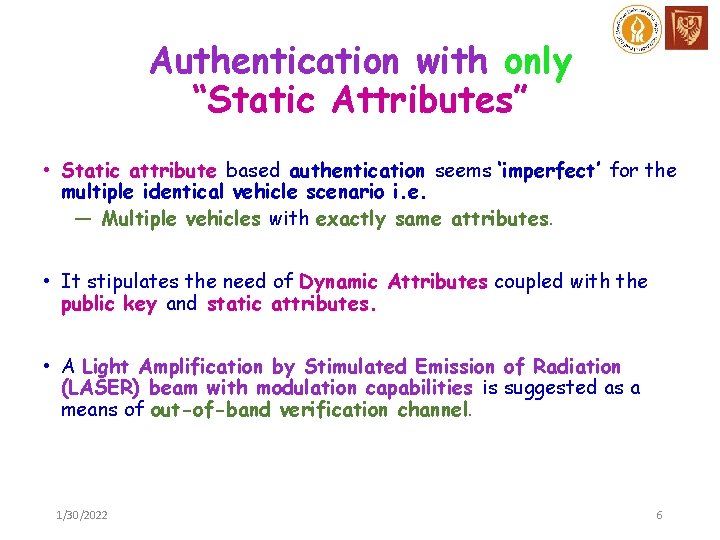
Authentication with only “Static Attributes” • Static attribute based authentication seems ‘imperfect’ for the multiple identical vehicle scenario i. e. — Multiple vehicles with exactly same attributes. • It stipulates the need of Dynamic Attributes coupled with the public key and static attributes. • A Light Amplification by Stimulated Emission of Radiation (LASER) beam with modulation capabilities is suggested as a means of out-of-band verification channel. 1/30/2022 6

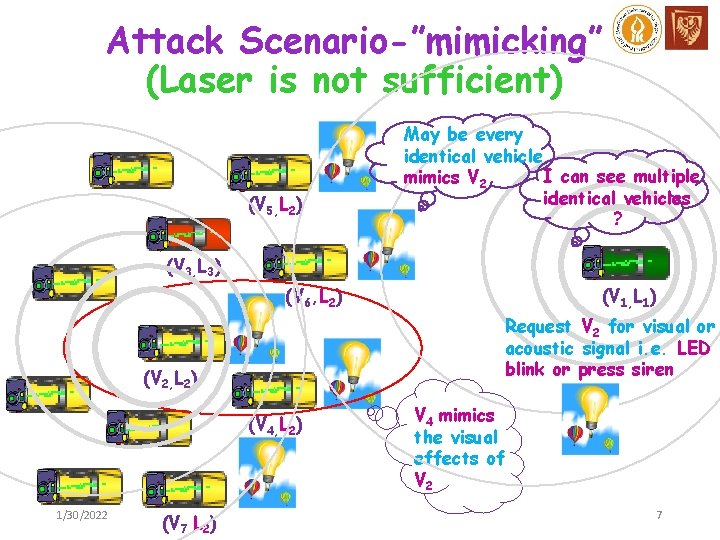
Attack Scenario-”mimicking” (Laser is not sufficient) (V 5, L 2) May be every identical vehicle I can see multiple mimics V 2 identical vehicles ? (V 3, L 3) (V 6, L 2) Request V 2 for visual or acoustic signal i. e. LED blink or press siren (V 2, L 2) (V 4, L 2) 1/30/2022 (V 7, L 2) (V 1, L 1) V 4 mimics the visual effects of V 2 7

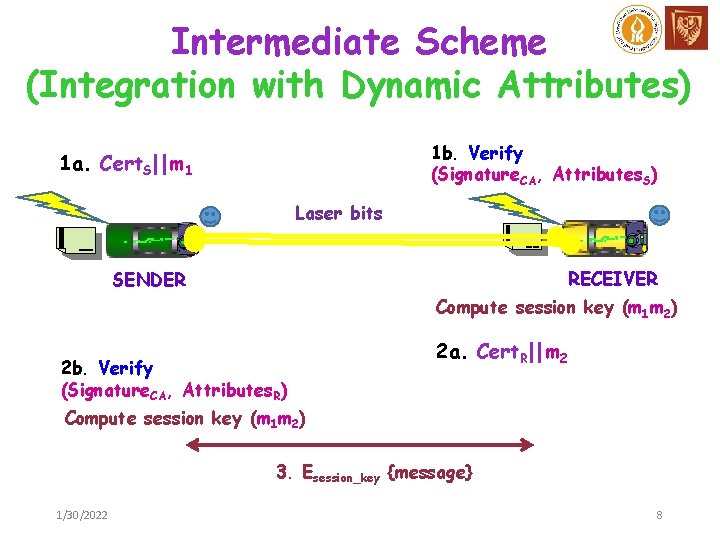
Intermediate Scheme (Integration with Dynamic Attributes) 1 b. Verify (Signature. CA, Attributes. S) 1 a. Cert. S||m 1 Laser bits RECEIVER SENDER Compute session key (m 1 m 2) 2 b. Verify (Signature. CA, Attributes. R) 2 a. Cert. R||m 2 Compute session key (m 1 m 2) 3. Esession_key {message} 1/30/2022 8

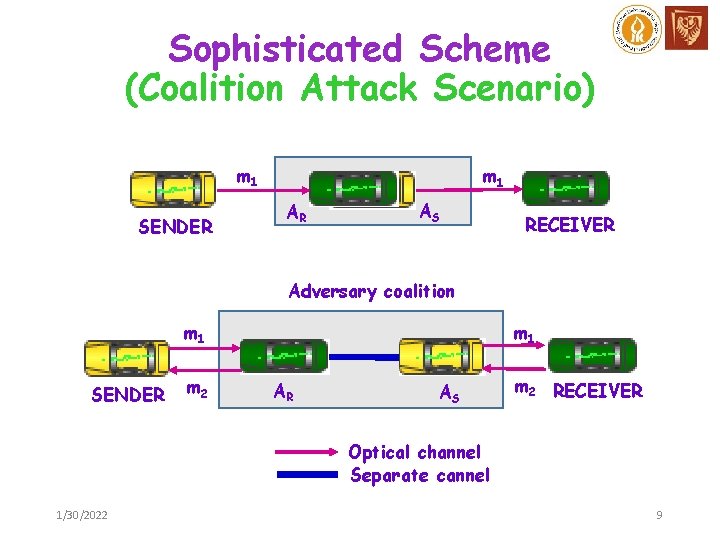
Sophisticated Scheme (Coalition Attack Scenario) m 1 SENDER m 1 AR AS RECEIVER Adversary coalition m 1 SENDER m 2 m 1 AR AS m 2 RECEIVER Optical channel Separate cannel 1/30/2022 9

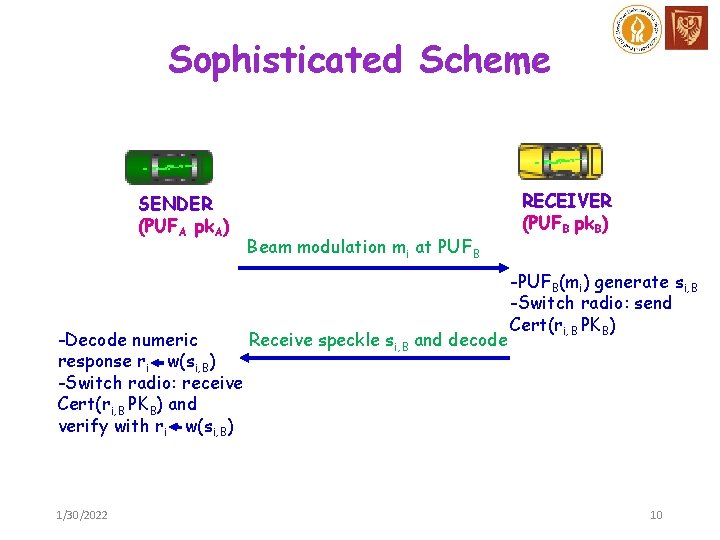
Sophisticated Scheme SENDER (PUFA pk. A) Beam modulation mi at PUFB -Decode numeric Receive speckle si, B and decode response ri w(si, B) -Switch radio: receive Cert(ri, B PKB) and verify with ri w(si, B) 1/30/2022 RECEIVER (PUFB pk. B) -PUFB(mi) generate si, B -Switch radio: send Cert(ri, B PKB) 10

Applications • Byzantine tolerant virtual traffic light • Replicated state machine • Synchronized state transition • Adaptive agreement before movement • Secure digital periphery for static vehicles • Knowledge based initial pairing • Commitment based authentication • Personified localization 11

Future directions • How to secure internal flexray network communication ? • How to utilize reactive data dissemination via probe vehicles? • How to ensure privacy in Internet of Things? • How to provide a secure vehicle-to-telecom integration via 5 G infrastructure? 12
 Shlomi dolev
Shlomi dolev Shlomi dolev
Shlomi dolev Dr dolev
Dr dolev Iff
Iff What is peer entity authentication
What is peer entity authentication Public class vehicle private string name protected vehicle
Public class vehicle private string name protected vehicle Edl authentication
Edl authentication Broken authentication acunetix
Broken authentication acunetix Message authentication code
Message authentication code Approaches to message authentication
Approaches to message authentication Debug ppp authentication
Debug ppp authentication Uf two factor authentication
Uf two factor authentication Ffeic authentication guidance
Ffeic authentication guidance