National Research Council Canada Conseil national de recherches



























- Slides: 36

National Research Council Canada Conseil national de recherches Canada Institute for Information Technology Institut de technologie de l'information E-Commerce: Hype, Hope… Help Needed Larry Korba National Research Council of Canada Larry. Korba@iit. nrc. ca http: //www. iit. nrc. ca Canada

Definition and Caveats Definition: Electronic Commerce - the secure exchange of goods, services and information electronically Forester Research Caveats: • Not an E-Commerce “Course” • Research Perspective • Highlights

Outline E-Commerce Today Future of E-Commerce • Now… Near Future Selected Challenges • Only a Few! Conclusions SET Business-Business IP Protection PKI Agent- Based E-Commerce Anywhere

E-Commerce Today…. . Big Money Assumption, “Hi Tech” Other Attractive Internet Words: Java, Agents, Security!

EC Today: Why is it so Business-to-Consumer • Internet Hype • Lower Costs • Market Expansion? Business-to-Business • Now and in Future • Growth ?

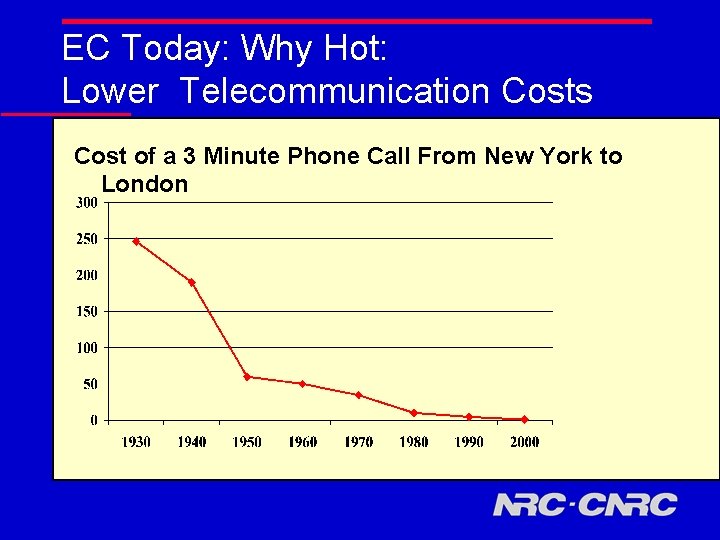
EC Today: Why Hot: Lower Telecommunication Costs Cost of a 3 Minute Phone Call From New York to London

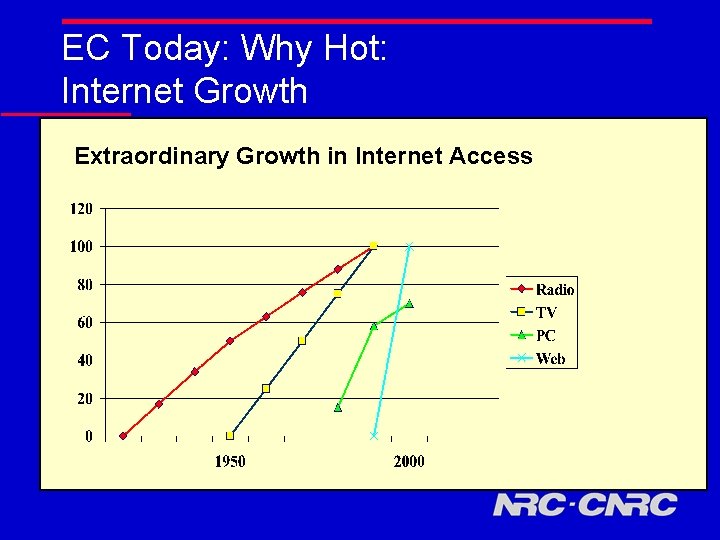
EC Today: Why Hot: Internet Growth Extraordinary Growth in Internet Access

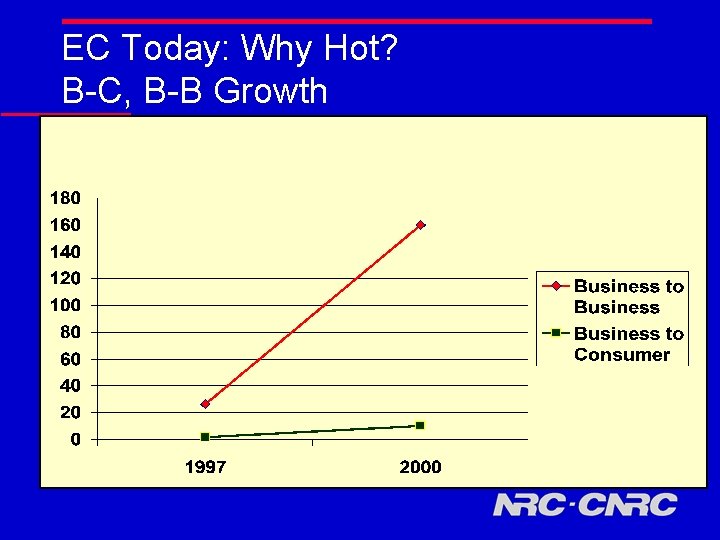
EC Today: Why Hot? B-C, B-B Growth

EC Today: Challenges It Works Quite Well, But…. Many “Standards”, Products Threats • Common Threats • Threats to Buyers • Threats to Sellers • Threats to Financial Institutions

EC Today: “Standards”, Products SSL <=> SET Many products to chose from Credit Card Transaction Providers Commerce Servers • IBM, Microsoft, Inex, Bestware, MANY MORE Middleware • Shareware, Cold Fusion…. Databases • SQL, DB 2, Oracle, Access… Web Portals Consultants

EC Today: Common Threats • • Insider Fraud Software Security Holes • All O/S & Applications • Good Security Hard to Build • Software Complexity • Security as an Add-On • Installation/Set Up Errors • Shopping Cart Exposure

EC Today: Threats to Buyers • • Hijacking, Spoofing Denial of Service Loss of Privacy Fraudulent Credit Card Use

EC Today: Threats to Sellers • • Fake Order Flood Site Impersonation Site Alteration Denial of Service

EC Today: Threats to Financial Institutions, Transaction Providers • Any Kind of Loss • $ – Credit Card Fraud • Information • Service Obstruction

Future Challenges of E-Commerce What is happening in Research Standardization Trust Business-to-Business Agent-Based E-Commerce • Automation • Learning Copyright Protection • Electronic Distribution E-Commerce Anywhere

Future Challenges: Research Competition Words to get Funding (or to get Published): • Electronic Commerce • Security • Agent • Java • Ontology. . .

Standardization Many Acronyms…. L ED I M O EC SA TP R L/ I OB FX O T P PKIX ICE IM S SE I SSL PK 9 0 X. 5 CI OMG/ CBO XM S OP Development Times, Costs, Interoperability

Trust and Electronic Commerce Biometry • Many Technologies Determining trustworthiness of Transaction Participants • e. g. Auction Sites. Research • Distributed Trust – Web Browsers, Agents • Models for Trust, Formalisms • E-Commerce and Group work applications

Biometry. . . Technologies • Iris, Face, Fingerprint, Hand Geometry, Typing, Handwriting, Voice Must work well • No False Positives: I Got IN!!! • No False Negatives: Let Me IN! Must NOT Lose Biometric Data! • Irreplaceable… • Once stolen, gives access to the store… • Single Sign On for Everything. . .

SET Many different proprietary electronic transaction Third Party Solutions SET: The Answer to Strife in the World! • Open Standard • Eliminates No Card Present Fraud – Visa/Master Card Like that! • Eliminate Non-Repudiation in Transactions • No Middleman

SET: Challenges Complicated Protocol = Slow Response • 3000 Line ASN. 1 • 28 Stage Transaction Process • 6 RSA Encryption Steps (Slow) Four Part Model • Interoperability Constant Evolution • Standard Fragmentation? SET <=> Credit Card-Based Other Possibilities: XML/EDI, Smart SET

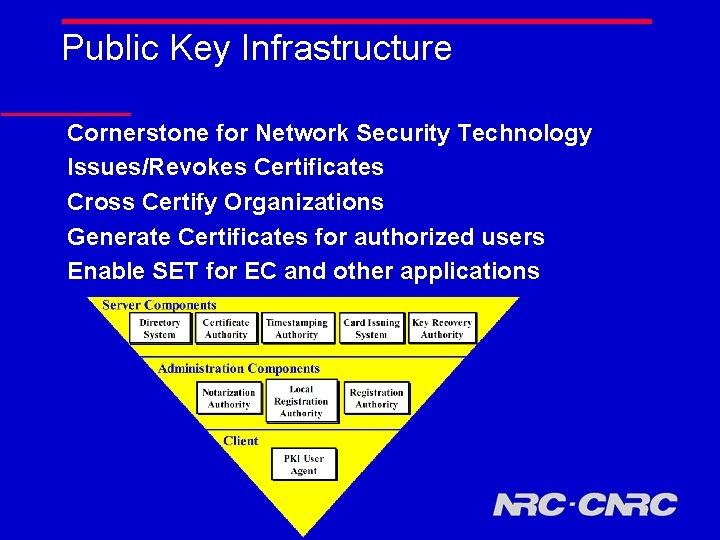
Public Key Infrastructure Cornerstone for Network Security Technology Issues/Revokes Certificates Cross Certify Organizations Generate Certificates for authorized users Enable SET for EC and other applications

PKI: Challenges Non-Trivial to set up • Cross-Certification • A lot like Beta Testing Software! Interoperability Issues • X. 509 v 3 Extensions Network Overhead Costs • Infrastructure is one thing, you need to buy the applications Dealing with Multiple Certificates

Business-to-Business Factors • Just-In-Time Delivery Requirement – Reduce Inventory, Cycle Times – Reduced Costs • International Trade (Globalization, Deregulation) • Move to Automated Transactions

Business-to-Business: Challenges Developing Trust • With New Partners • Contract Protocols: Formal, Creative Low-Cost, Secure Large Transactions Sharing Minimum Required Operational Information Company A Company C Company B ?

Agent-Based E-commerce Bargain Finder Negotiator User Interface Mobile Agents? Agent A Agent B

Agent-Based E-commerce: Challenges Trust • Agent Code • Agent Environment Confidentiality/Integrity • Customer/vendor Information Standards • Agent Communication • Agent Environments • APIs

Intellectual Property Protection Electronically Transferable IP Network Distribution: • Lower Cost • Potential Risks Potential for New Forms of Licensing

IP Protection: Challenges It’s Hard to Protect IP • Text • Graphics • E-Books • Software • 3 D Models Different Restrictions • Trade • Exclusivity • Usage


IP Protection: Examples Software Protection • Software Copying/Cracking is Epidemic • Hardware (Dongles), Software • Flexible Electronic Licensing Needed Recording Industry • Analog Copying is Easy • Audio CD copying • MP 3 Distribution

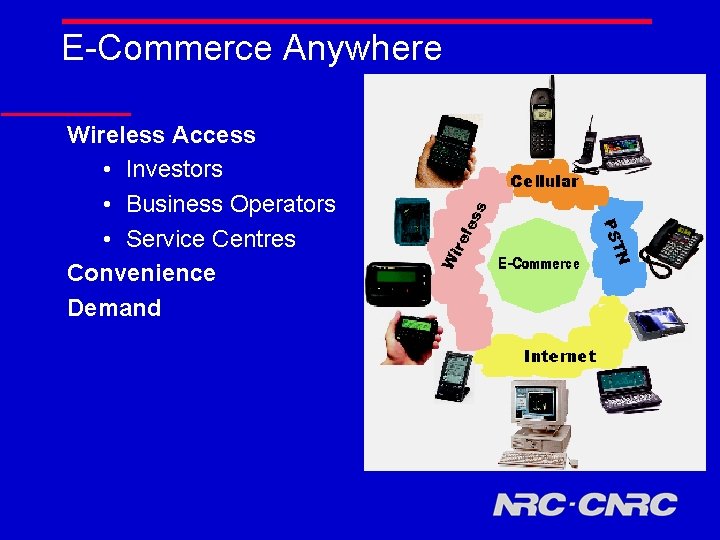
E-Commerce Anywhere Wireless Access • Investors • Business Operators • Service Centres Convenience Demand

E-Commerce Anywhere: Challenges V-Commerce • Tedious • Secure? False Negatives Eavesdropping? • Electronic • Human Replay? SSL/SET over voice/pager? Wireless LANs • Coverage, Implementation

Wireless LAN Implementation IEEE 802. 11 Symmetric Key Available For View! • In Network Dialog Box for Client • Or Via SNMP from Access Point

Summary E-Commerce is here, and Thriving • Works quite well Big Money going into E-Commerce • Researchers • Developers Software Implementation Errors • Prevention • SW/HW Version Authentication Electronic Delivery • Enforcing Copyright Protection

Summary (Continued) Secure E-Commerce Everywhere • Portable Electronic Wallet • Biometry E-Commerce Agents • Trust and Privacy • Agent Mobility Room for Innovation Resource Page: http: //132. 246. 128. 180/ecommerce/ecomlinks. html Email Address: Larry. Korba@iit. nrc. ca
 Saxenda efficacité
Saxenda efficacité National airlines council of canada
National airlines council of canada Conseil national de la vie associative
Conseil national de la vie associative Forest stewardship council canada
Forest stewardship council canada Conseil de vie
Conseil de vie Wude men conseil formation
Wude men conseil formation Bac pro services accueil assistance conseil
Bac pro services accueil assistance conseil Rita raemy
Rita raemy Cabinet gestion de projet
Cabinet gestion de projet Conseil dynamiser collaborateurs strasbourg
Conseil dynamiser collaborateurs strasbourg Pass cyber conseil
Pass cyber conseil Porter conseil
Porter conseil Conseil de la vie
Conseil de la vie 13 conseil de la vie
13 conseil de la vie Conseil de discipline collège
Conseil de discipline collège Gabriel garca marquez
Gabriel garca marquez Oral brevet parcours avenir avocat
Oral brevet parcours avenir avocat Conseil ingenierie informatique
Conseil ingenierie informatique Conseil hse
Conseil hse Greece's national animal
Greece's national animal National animal of canada
National animal of canada Research council oman
Research council oman Raw materials research and development council
Raw materials research and development council Tnscert
Tnscert Development research centre of the state council
Development research centre of the state council Corporate leadership council
Corporate leadership council Citizens research council
Citizens research council Mrc scala forza
Mrc scala forza Research council
Research council Research council
Research council Seo for youth sports clubs
Seo for youth sports clubs National water quality monitoring council
National water quality monitoring council National water quality monitoring council
National water quality monitoring council National employment law council
National employment law council Dignity champion ideas
Dignity champion ideas National council for special education
National council for special education National aids council tenders
National aids council tenders




























































