My Doom Ian Axelrod Chris Mungol Antonio Silva











- Slides: 16

My. Doom ☉ Ian Axelrod ☉ Chris Mungol ☉ Antonio Silva ☉ Joshua Sole ☉ Somnath Banerjee -----------------------Group 5 CS 4235/8803 Spring 2010

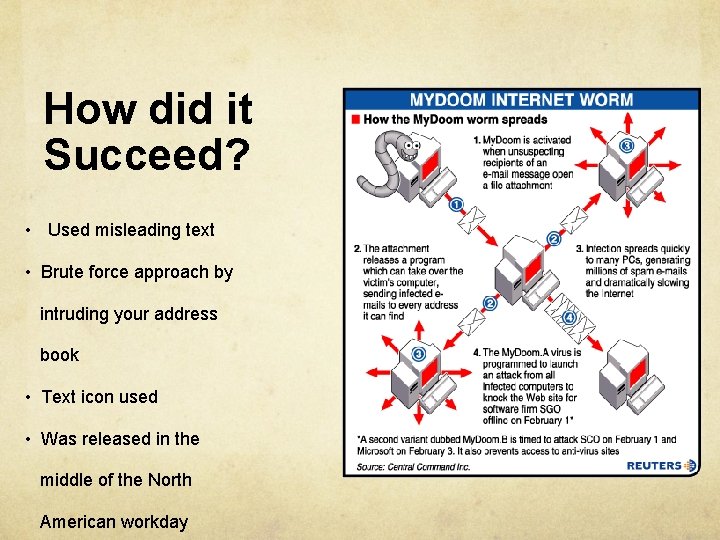
What happened? • Self propagating email based virus (worm) • Claimed to be the fasted spreading email virus • Speculated to have originated in Russia • Aliases: W 32. My. Doom@mm, Novarg, Mimail. R, Shimgapi • First sighted: 26 January 2004 • My. Doom. A & My. Doom. B spread to over 1 Million computers in preparation for a DDOS attack on SCO and Microsoft • My. Doom. A & My. Doom. B stop spreading • Doomjuice appears in backdoors left by My. Doom. A &. B • variants of Mydoom attack Google, Alta. Vista and Lycos

Highlights • The My. Doom computer virus knocked out SCO Group's Web site with a massive DOS attack • Microsoft was able to thwart an attack on its Windows Update site by eliminating the specific Web address the MSBlast worm targeted. The software maker killed off the site's previous address. • The White House stymied a denial-of-service attack aimed at its Web site by diverting a deluge of data, sent by systems infected with the worm, to a different address.

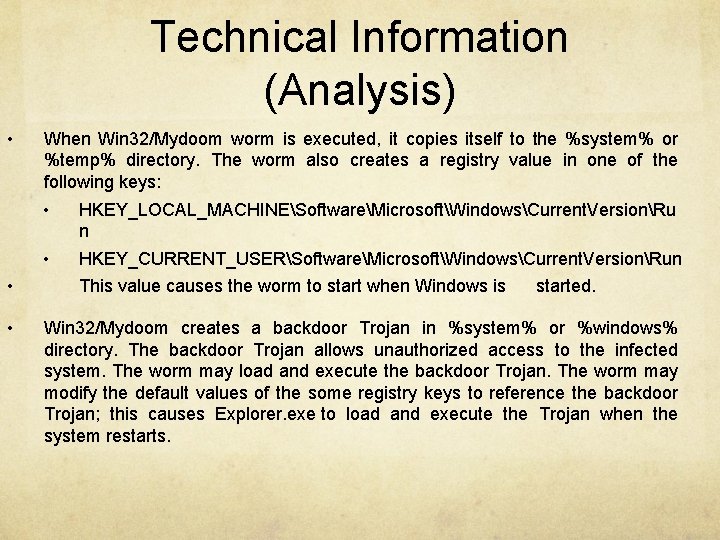
Technical Information (Analysis) • • • When Win 32/Mydoom worm is executed, it copies itself to the %system% or %temp% directory. The worm also creates a registry value in one of the following keys: • HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrent. VersionRu n • HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrent. VersionRun This value causes the worm to start when Windows is started. Win 32/Mydoom creates a backdoor Trojan in %system% or %windows% directory. The backdoor Trojan allows unauthorized access to the infected system. The worm may load and execute the backdoor Trojan. The worm may modify the default values of the some registry keys to reference the backdoor Trojan; this causes Explorer. exe to load and execute the Trojan when the system restarts.

Technical Information (Analysis) • Win 32/Mydoom may copy itself to the share folder of the Kazaa P 2 P application, in order to spread through P 2 P networks. • Win 32/Mydoom may copy itself to random directories on an infected system. • Win 32/Mydoom collects e-mail addresses from files on an infected system and sends e-mail with an attached copy of the worm to the addresses. This function is the primary propagation method the worm uses.

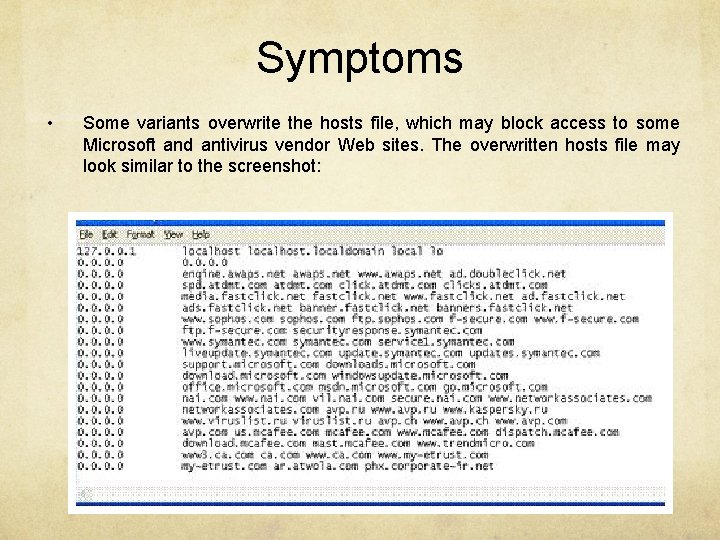
Symptoms • Some variants overwrite the hosts file, which may block access to some Microsoft and antivirus vendor Web sites. The overwritten hosts file may look similar to the screenshot:

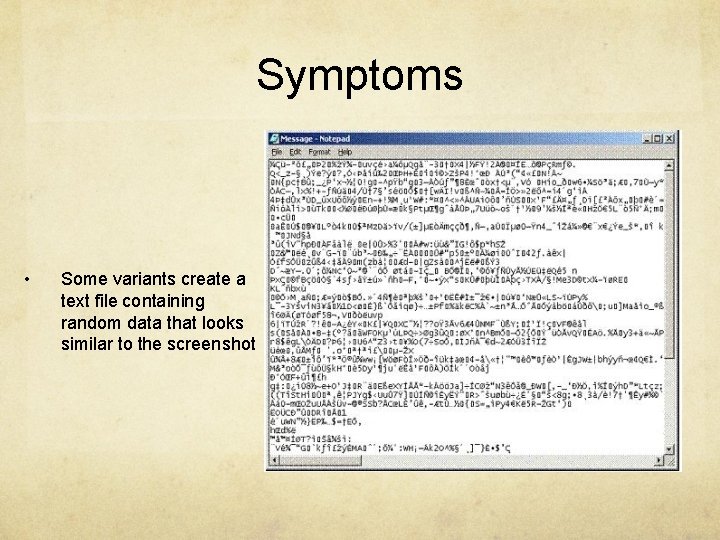
Symptoms • Some variants create a text file containing random data that looks similar to the screenshot

Impact? • At a point the worm was accounting for 20 percent to 30 percent of worldwide e-mail traffic • Slowed Internet performance by 10% • Web-page load time down by 50%

How did it Succeed? • Used misleading text • Brute force approach by intruding your address book • Text icon used • Was released in the middle of the North American workday

Aftermath? • Sparked new versions • Version U, V, W, X, and AO • Expensive repurcussions • My. Doom 2009 ?

Keeping systems safe from the My. Doom virus • System Administrators • Users

System Administrator • Filter network traffic- blocking specific inbound and outbound traffic to ports 1080, 3128, 8080, 10080 • If filtering ports are not feasible, try to block all network traffic that is not required for normal operation • Symptoms of viruses or specifically the my. Doom virus may be found by detecting increased CPU load and/or higher than normal SMTP traffic. • Scan e-mails internally for viruses. Use of Mail Transfer Agents (MTAs) to block e-mail with W 32/My. Doom. B signatures • Disable automatic response messages: . Important that responses do not return the infected attachment Source: US-CERT

Users • Always trust the end user of any attachment or program received. • Email users should be circumspect of unwarranted attachments and Peer-to-Peer (P 2 P) users should be wary of. exe files • Always run and maintain an antivirus tool or application. Updating antivirus app will guarantee extra security with new strains of viruses. • Almost all antivirus vendors offer a My. Doom removal tool. Bottom line: Do not open attachments from users you do not know or trust! Source: US-CERT

More Info. In Textbook Chapter 3 Section 3. 3 Viruses and Other Malicious Code • Why worry about malicious code? • Difference between virus, worm, and other malevolent programs. • The technical aspects of viruses. • The first malicious code and it’s implications.

Sources • Wikipedia • CNET • How. Stuff. Works. com • US-CERT • Google images • Microsoft. com

Thank You
 Ian axelrod
Ian axelrod Cyril axelrod
Cyril axelrod Tit
Tit The flywheel and the doom loop
The flywheel and the doom loop Travis doom
Travis doom Flywheel and doom loop
Flywheel and doom loop Irving lichtenstein
Irving lichtenstein Poetic devices in elementary school classroom
Poetic devices in elementary school classroom The spinning wheel of doom
The spinning wheel of doom Sayangabang dalnet
Sayangabang dalnet Doom timeline
Doom timeline Doom game design document
Doom game design document Azure multi-factor authentication server download
Azure multi-factor authentication server download Doom and boom
Doom and boom Worm timeline
Worm timeline Mercy king doom
Mercy king doom Axila doom 2
Axila doom 2