A Timeline of Malicious Code Sean Watts Department










- Slides: 22

A Timeline of Malicious Code Sean Watts Department of Computer Science Clemson University As a partial requirement for CP SC 620.

INTRODUCTION What is Malicious Code Ø Software intended to cause undesired effects, security breaches or damage to a system. Ø Malicious code describes a broad category of system security terms Ø Worms. Ø Trojan horses Ø Attack scripts Ø Viruses

Timeline of Malicious Code 1983 The term "computer virus" is proposed

Timeline of Malicious Code 1986 Brain virus The ‘Brain’ begins to ‘think’

Timeline of Malicious Code The Lehigh virus discovered at Lehigh University 1987 Lehigh virus

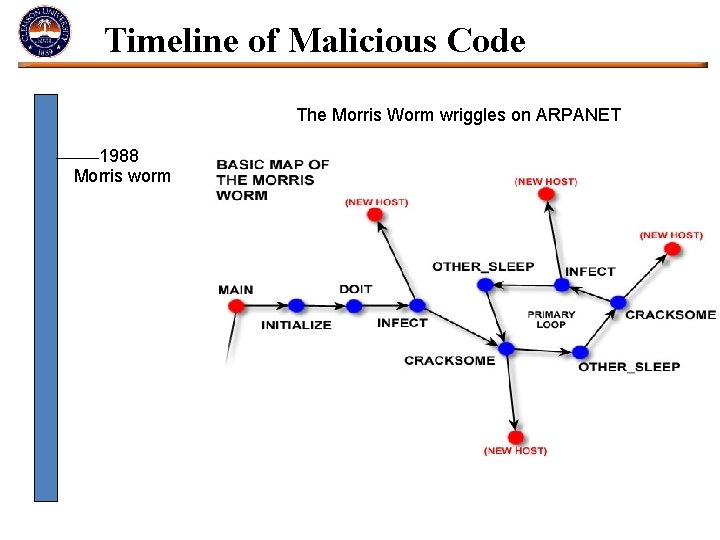
Timeline of Malicious Code The Morris Worm wriggles on ARPANET 1988 Morris worm

Timeline of Malicious Code Symantec launches Norton 1990 Norton anti-virus

Timeline of Malicious Code A new ‘Concept’ 1995 Concept virus

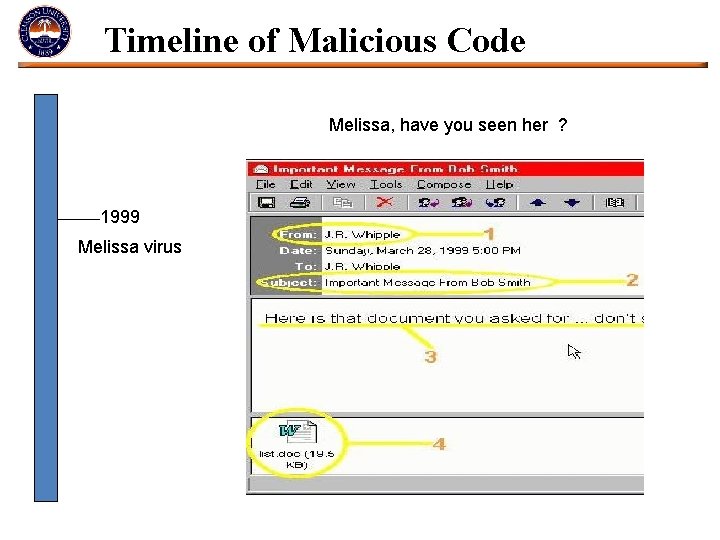
Timeline of Malicious Code Melissa, have you seen her ? 1999 Melissa virus

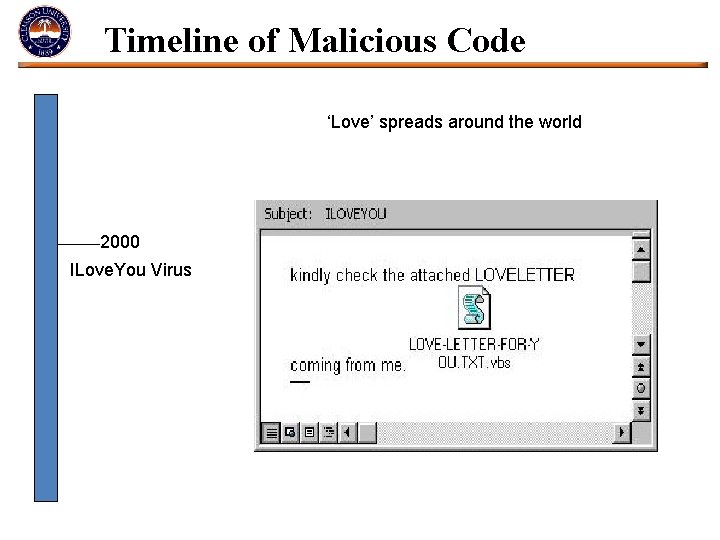
Timeline of Malicious Code ‘Love’ spreads around the world 2000 ILove. You Virus

Timeline of Malicious Code ‘Anna’ goes beyond the court 2001 Anna virus

Timeline of Malicious Code Red !!! 2001 Code Red Worm

Timeline of Malicious Code You’ve been Slammered 2003 Slammer worm

Timeline of Malicious Code We are all DOOMED ! 2004 My. Doom worm

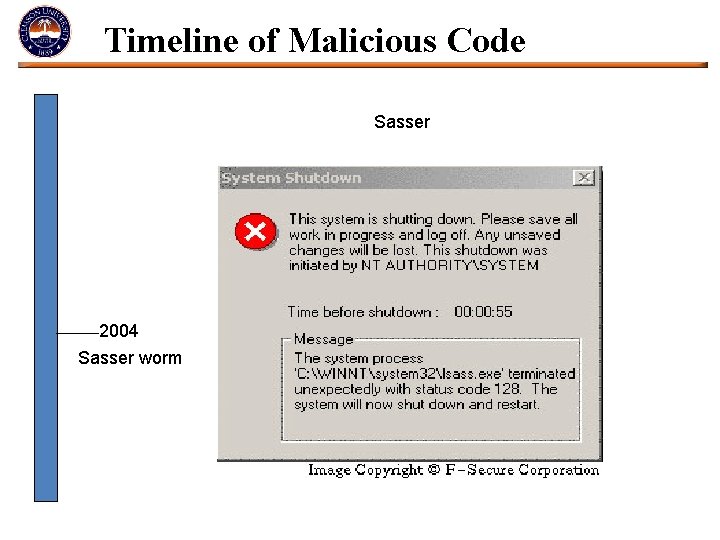
Timeline of Malicious Code Sasser 2004 Sasser worm

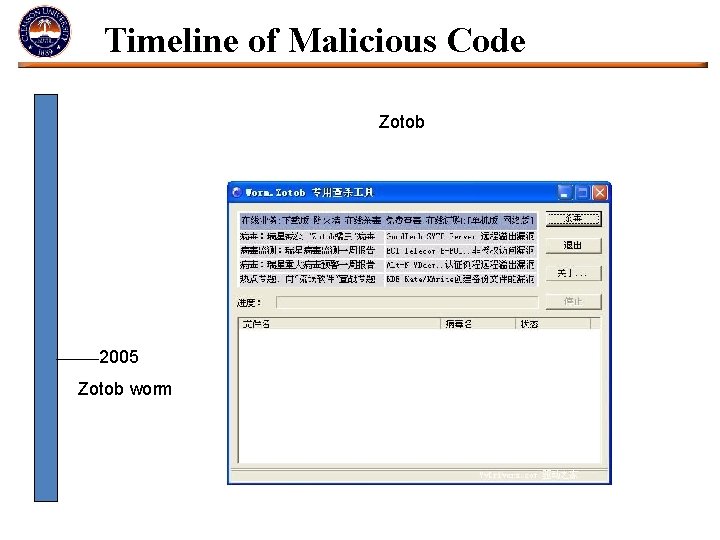
Timeline of Malicious Code Zotob 2005 Zotob worm

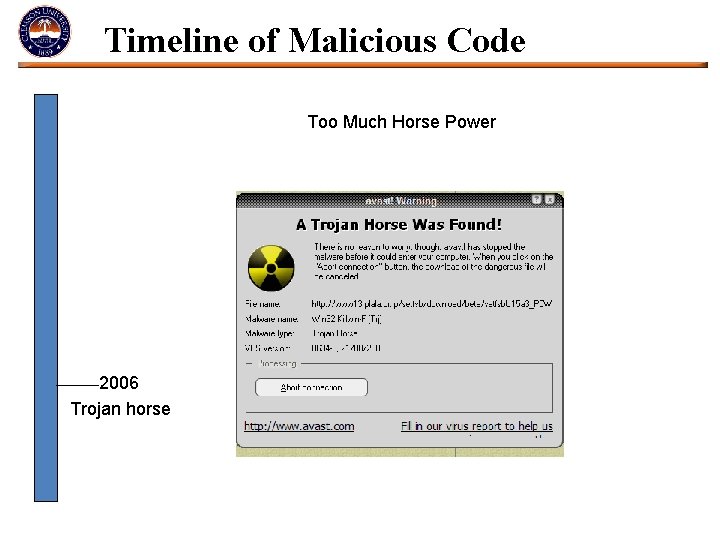
Timeline of Malicious Code Too Much Horse Power 2006 Trojan horse

Timeline of Malicious Code A ‘Storm’ is brewing 2007 Storm worm

Conclusion • Malicious code has been around for a long time. • Users should be mindful of the harm viruses can cause a computer system. • Malicious code are a clear and present danger. • Venture into cyberspace with care and caution

References • www. techshout. com • http: //inventors. about. com • http: //www. techweb. com/ • www. virus-scan-software. com • www. washingtonpost. com • http: //www. exn. ca • www. howstuffworks. com • http: //support. microsoft. com • http: //technology. newscientist. com • http: //infoplease. com

Questions Any Questions ?

Thank You