MonkeyintheMiddle Attacks on Campus Networks EDUCAUSE Security Professionals











- Slides: 40

Monkey-in-the-Middle Attacks on Campus Networks EDUCAUSE Security Professionals Conference 2007 Andrew J. Korty Indiana University Sean Krulewitch Indiana University April 12, 2007

Copyright © 2007 The Trustees of Indiana University. This work is the intellectual property of the authors. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the authors. To disseminate otherwise or to republish requires written permission from the authors.

Agenda • • What is a Mit. M attack? Target: Web authentication Target: Kerberos authentication Target: SSH protocol Prevention: Vendors Prevention: Sysadmins, site owners Prevention: Users Q&A Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

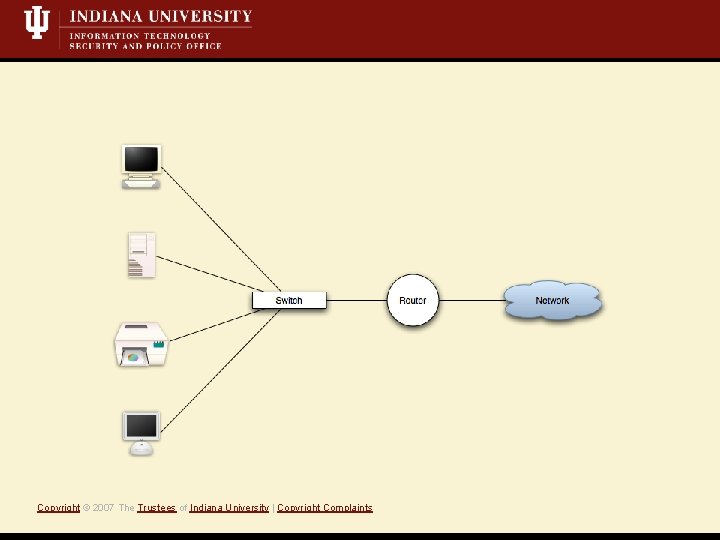
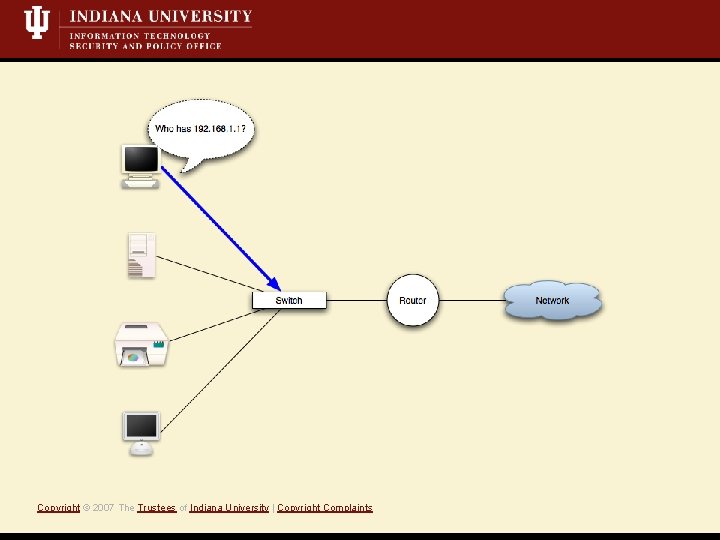
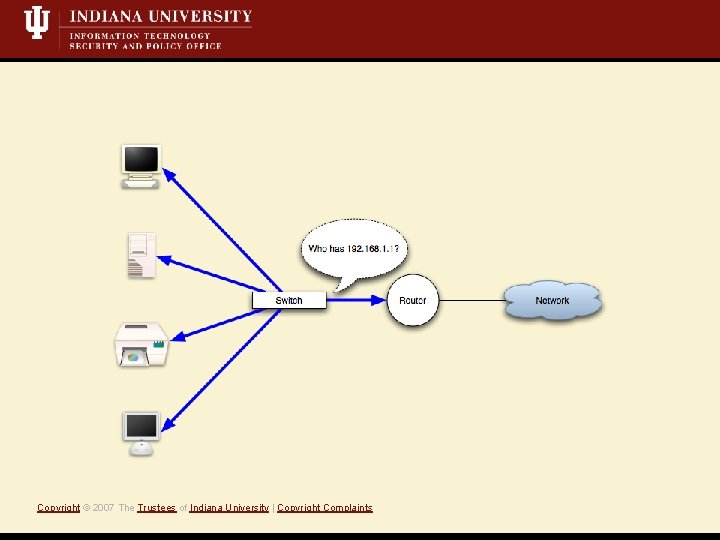
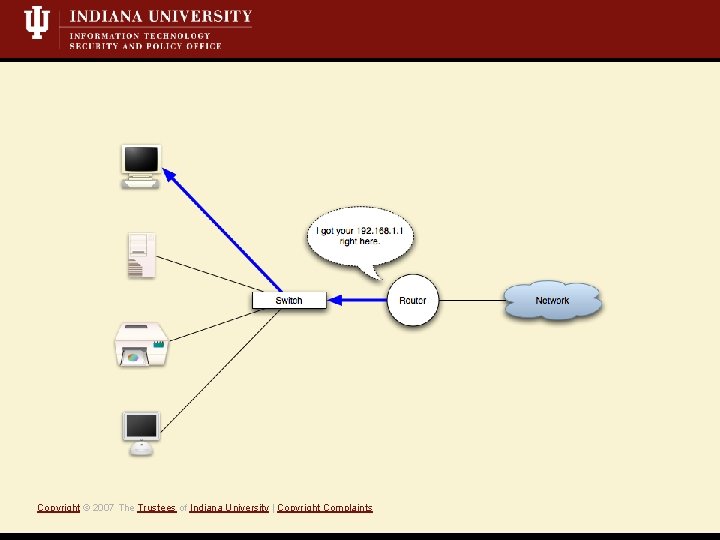
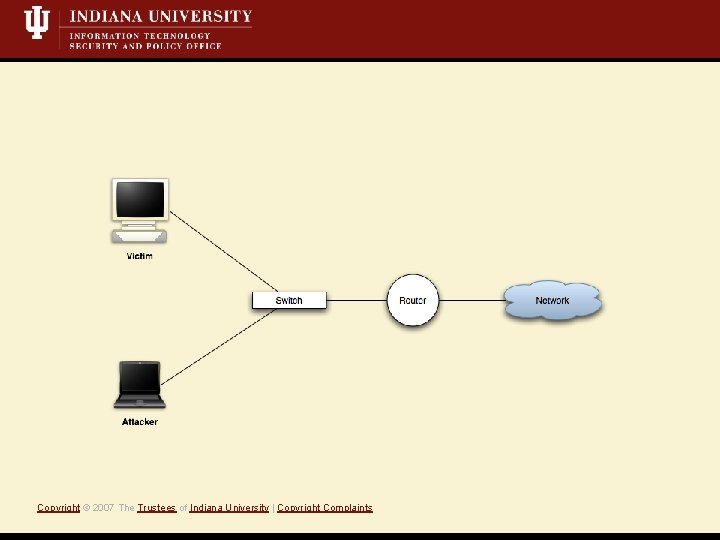
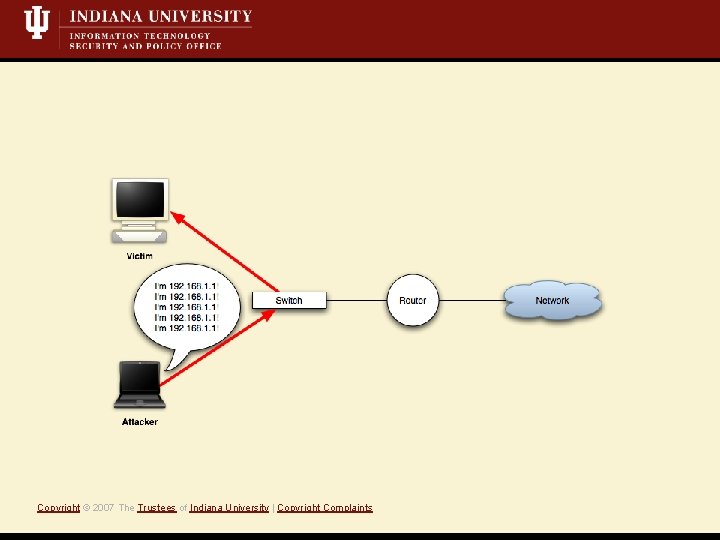
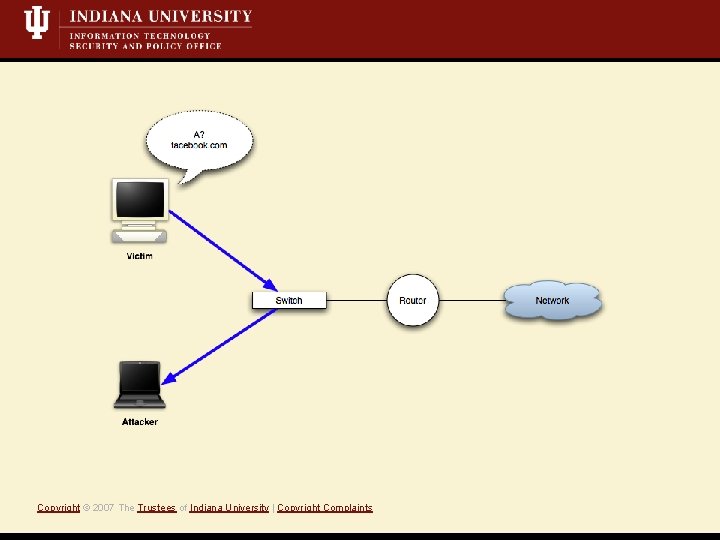
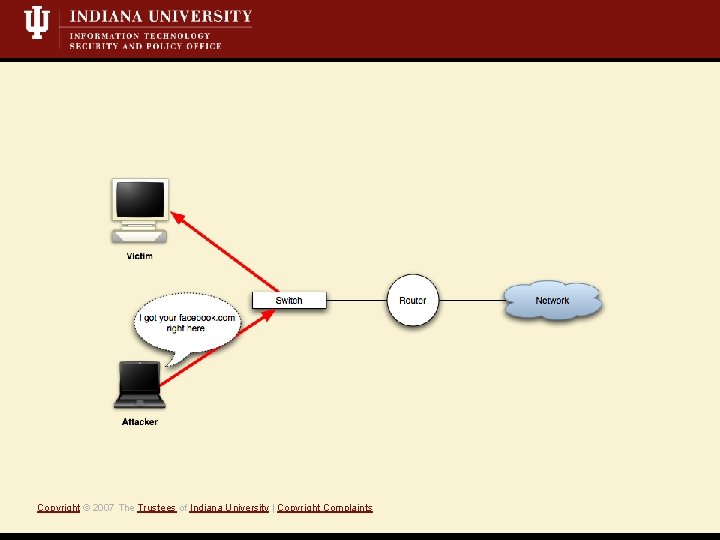
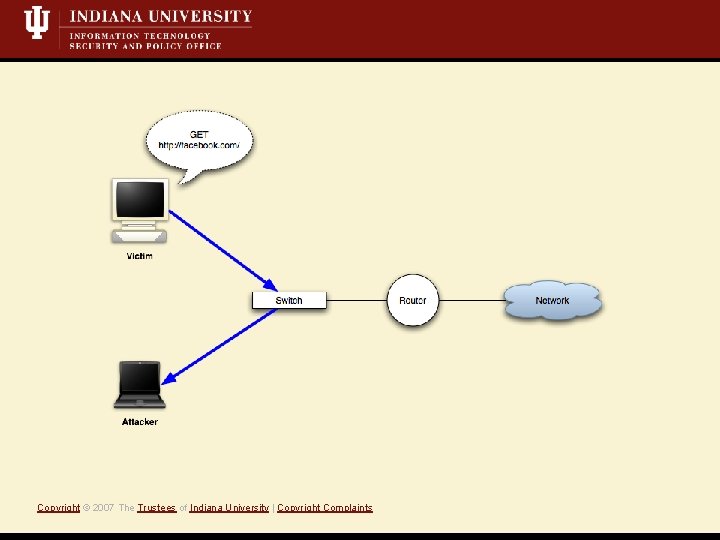
What is a Mit. M attack? • Short Definition: A Monkey-in-the-middle attack is when an attacker controls both sides of conversation, posing as the sender to the receiver *and* the receiver to the sender. • Active attack, i. e. , we’re writing data to the network • Eavesdropping/Sniffing • Insertion/Modification/Deletion Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

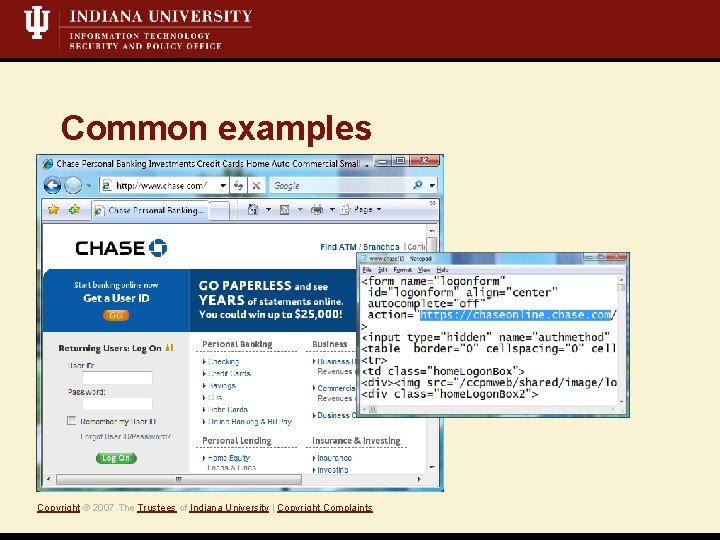
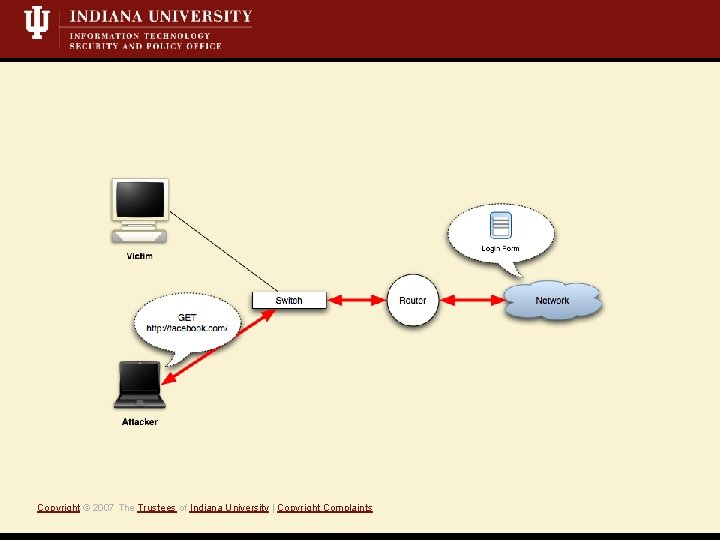
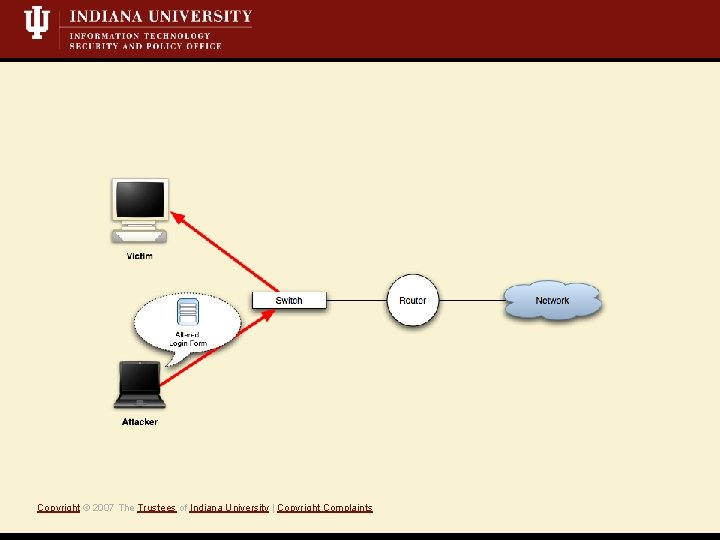
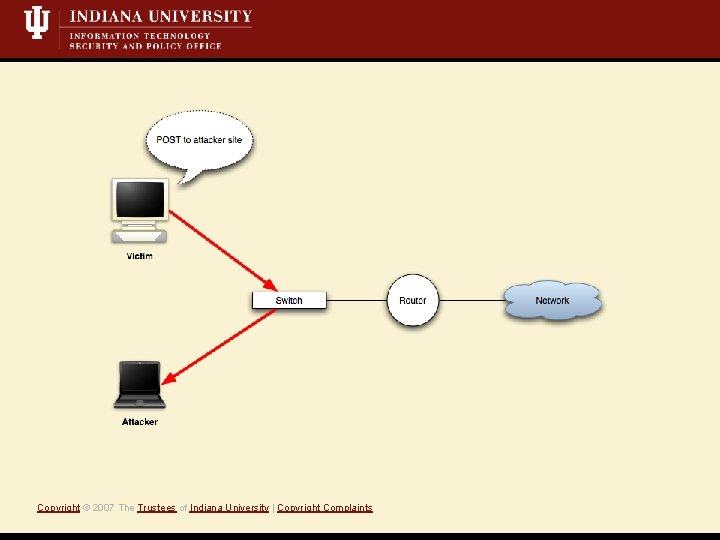
Target: Web authentication • Initial web page requested by user is not authenticated Vulnerability • Attacker directs victim to location of attacker’s choice Exploit Copyright © 2007 The Trustees of Indiana University | Copyright Complaints • http form : https form action • http GET : https 3 xx redirect, meta REFRESH Common examples

Common examples Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

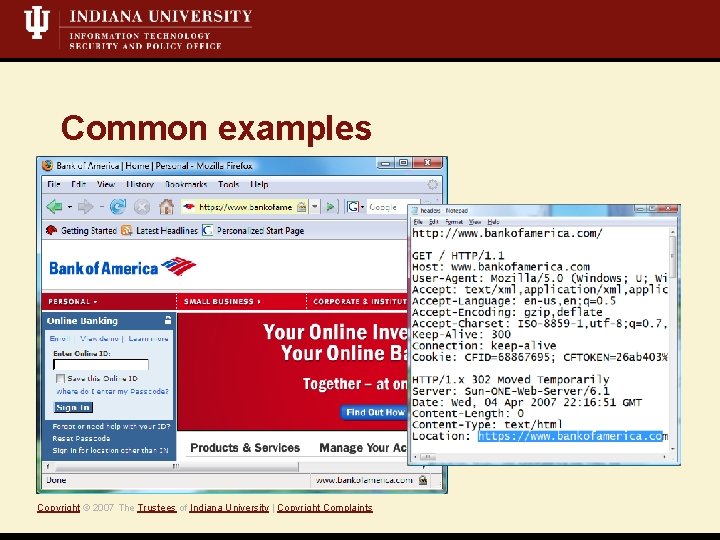
Common examples Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Common examples Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

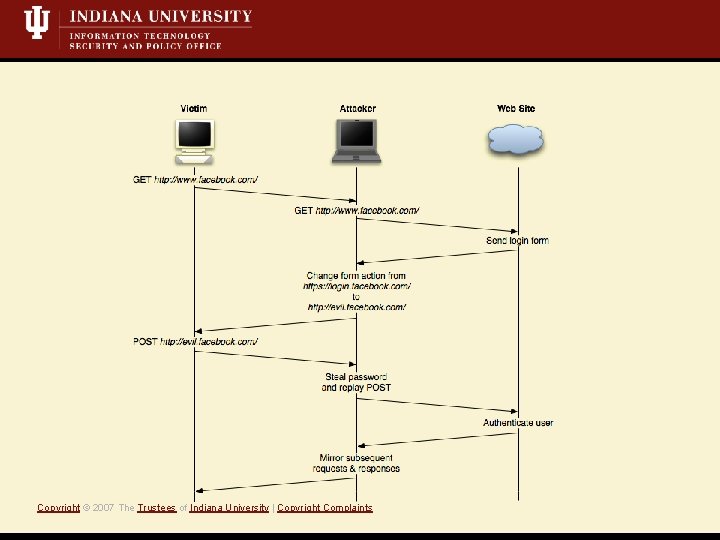
Mit. M: Web authentication demo Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

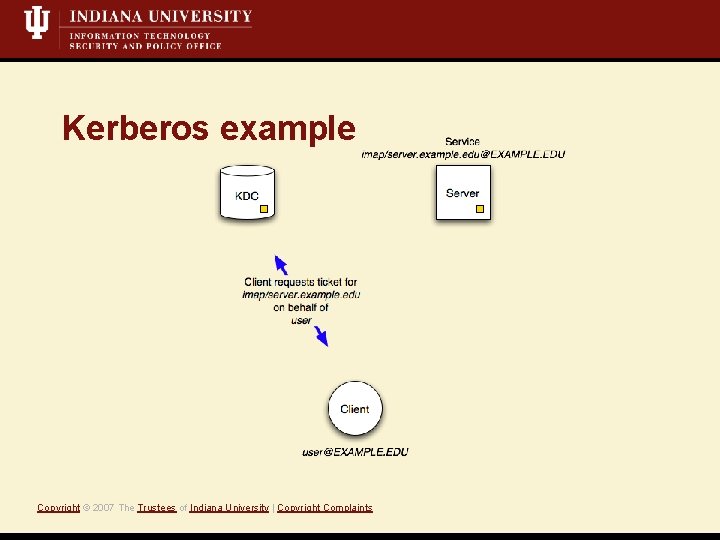
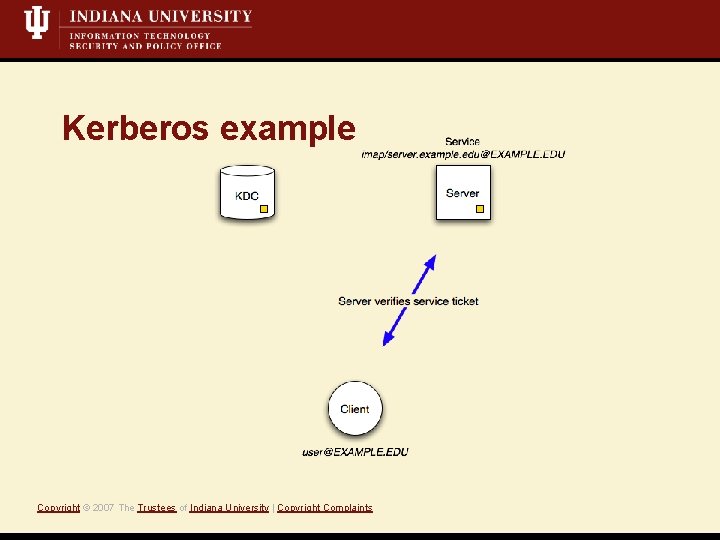
Kerberos example Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Kerberos example Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

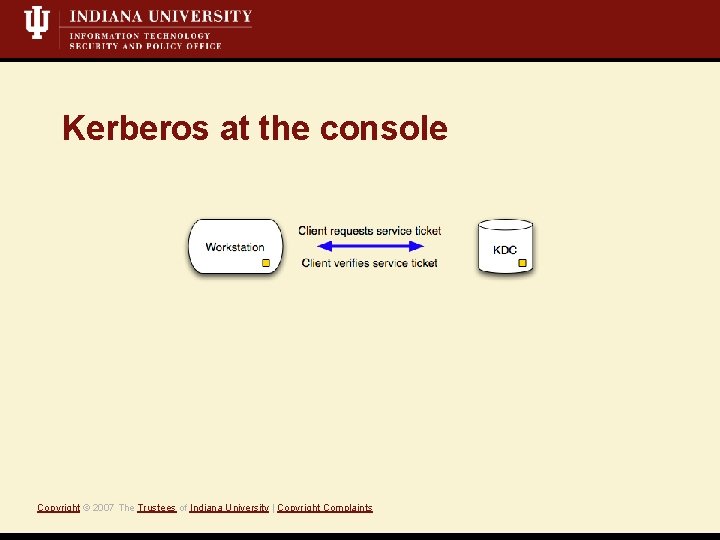
Kerberos at the console Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

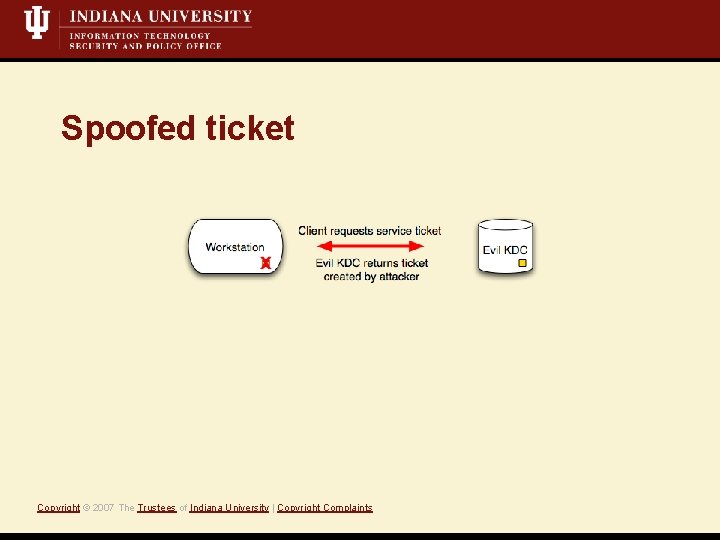
Target: Kerberos authentication • Kerberos responses are not validated Vulnerability • Spoof ticket encrypted with key of attacker’s choice Exploit Copyright © 2007 The Trustees of Indiana University | Copyright Complaints • KDC Verify off • Pam_krb 5, mod_auth_kerb, etc. without a keytab Common examples

Spoofed ticket Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Mit. M: Kerberos demo Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

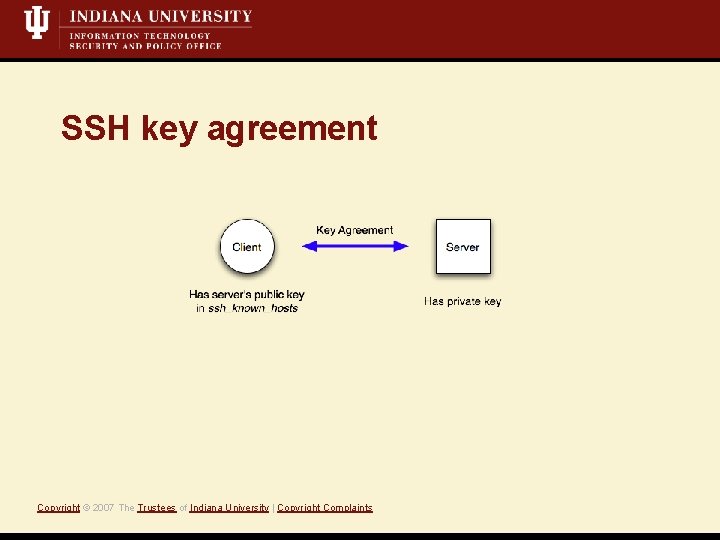
SSH key agreement Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

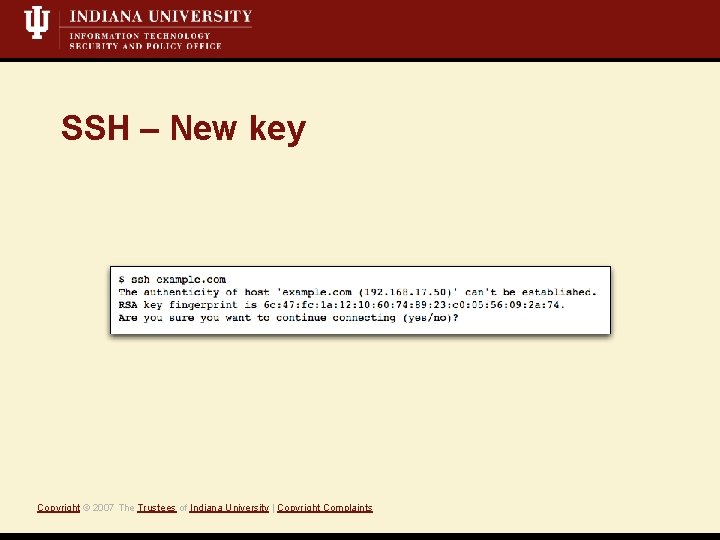
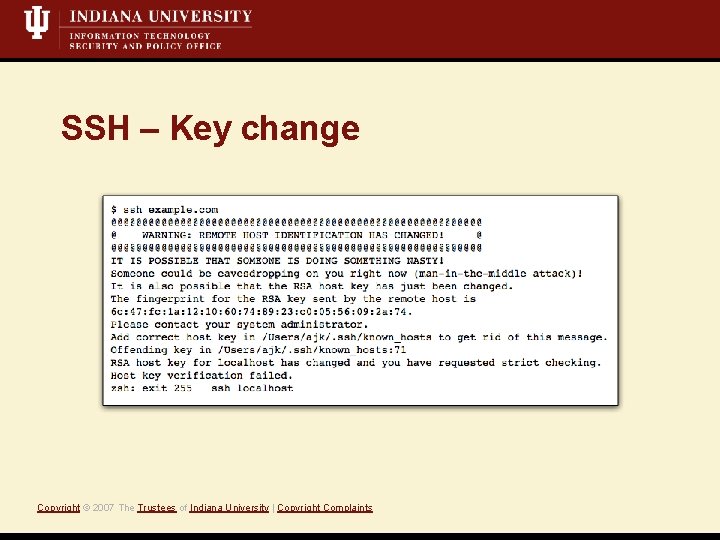
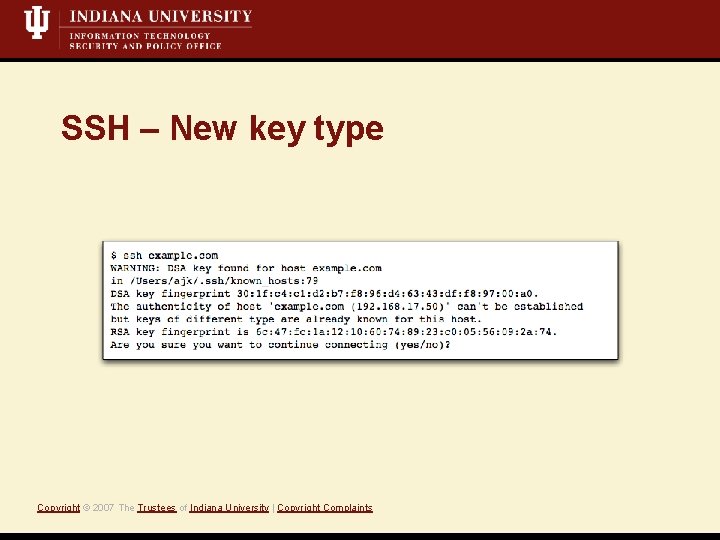
Target: SSH protocol • Client doesn’t verify host-key • Attacker offers a different key from a spoofed server Vulnerability Exploit Copyright © 2007 The Trustees of Indiana University | Copyright Complaints • Fingerprints aren’t validated on new/changed host keys • SSH servers in compatibility mode (i. e. , version 1. 99) Common examples

SSH – New key Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

SSH – Key change Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

SSH – New key type Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Prevention: Vendors Target: Web authentication • Check for https by default • Disable unencrypted password submit Target: Kerberos authentication • Required KDC Verification Target: SSH protocol • Enforce Strict. Host. Key. Checking and offer stronger warning messages Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

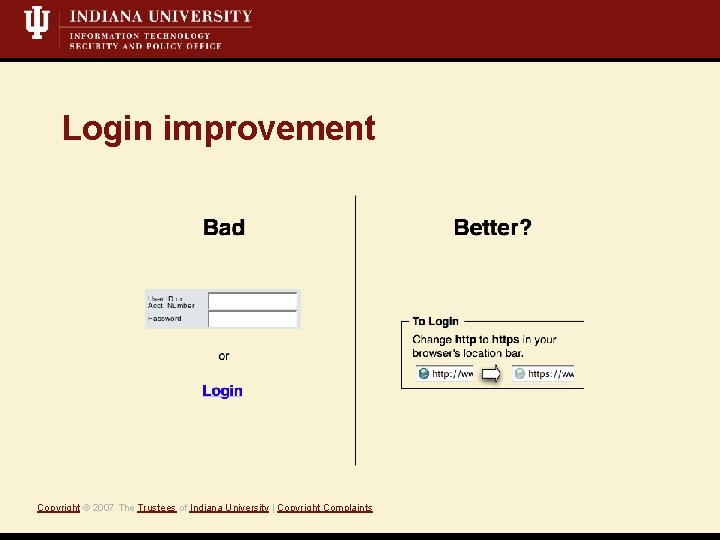
Prevention: Sysadmins, site owners Target: Web authentication • Make https URLs obvious (i. e. , the same) • Disable http? Target: Kerberos authentication • Always use keytabs • Enable KDC verification Target: SSH protocol • Deploy clients with Strict. Host. Key. Checking • Pre-distribute keys of both types (RSA, DSA) Other prevention techniques • DNSSEC • Site. Key? Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Login improvement Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

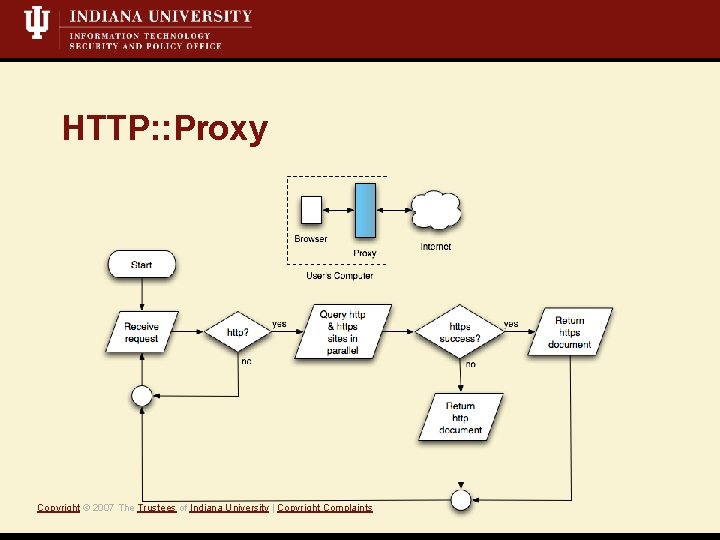
Prevention: Users Target: Web authentication • Always try https first • Use bookmarks • Proxy Target: SSH protocol • Always validate host-key fingerprints out-of-band • Enable Strict. Host. Key. Checking Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

HTTP: : Proxy Copyright © 2007 The Trustees of Indiana University | Copyright Complaints

Q&A Copyright © 2007 The Trustees of Indiana University | Copyright Complaints
