Microsoft Virtual Academy Free online technical courses Take











- Slides: 21

Microsoft Virtual Academy Free, online, technical courses Take a free online course. http: //www. microsoftvirtualacademy. com


Rising number of organizations suffer from breaches 1 2 1 3 2 3 3

Phishing attacks Stolen admin credentials Insider attacks 1. We know that administrators have the keys to the kingdom; we gave them those keys decades ago 2. But those administrators privileges are being compromised through social engineering, bribery, coercion, private initiatives

Problem A breach will (already did? ) happen Lacking the security-analysis manpower Can’t determine the impact of the breach Unable to adequately respond to the breach New approach (in addition to ‘prevention’) Limit or block the breach from spreading Detect the breach Respond to the breach

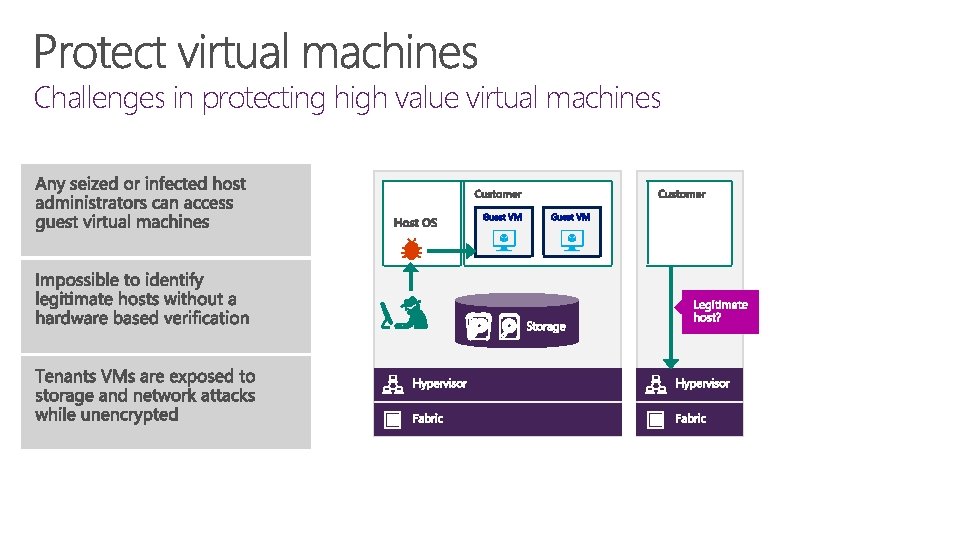
Challenges in protecting high value virtual machines

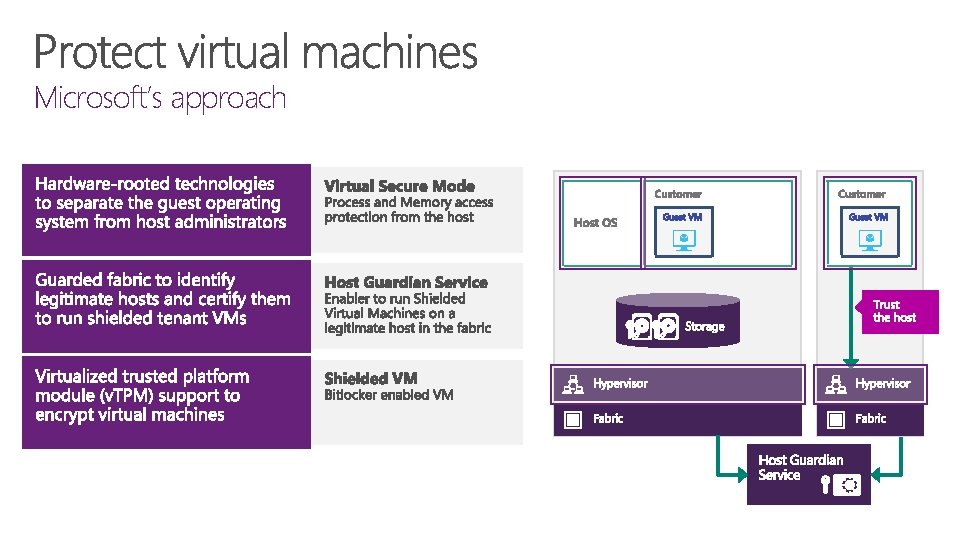
Microsoft’s approach

So what is a ‘Shielded VM’? “The data and state of a shielded VM are protected against inspection, theft and tampering from both malware and datacenter administrators 1. ” 1 fabric admins, storage admins, server admins, network admins

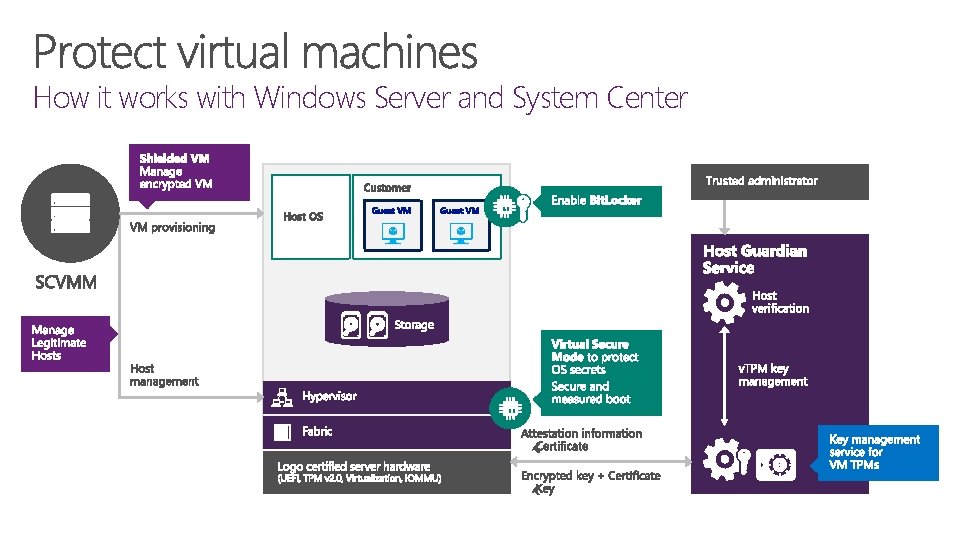
How it works with Windows Server and System Center

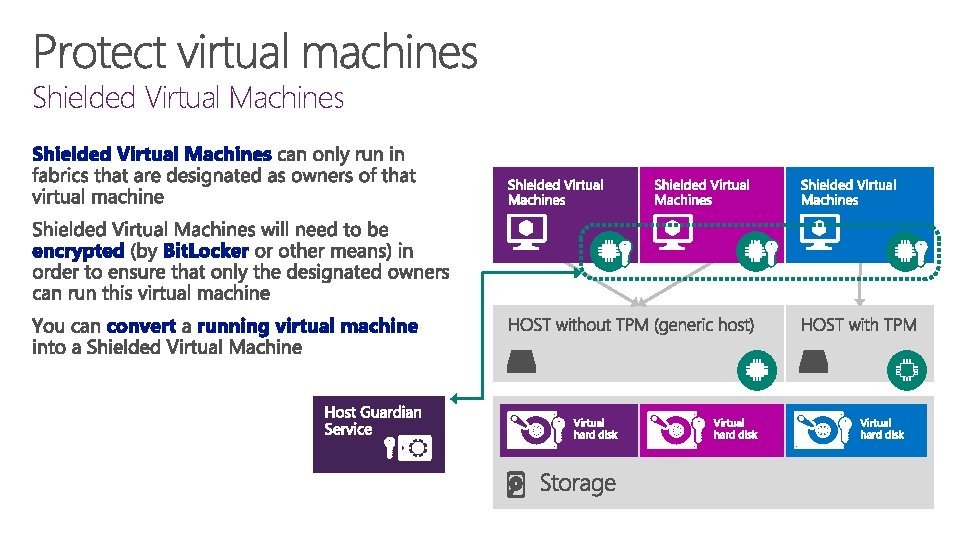
Shielded Virtual Machines

Encryption & data at-rest/in-flight protection Admin-lockout Attestation of health

H/W-trusted attestation Admin-trusted More complex setup/configuration Simplified deployment and configuration New Hyper-V host hardware required Existing H/W likely to meet requirements Scenarios enabled (TPM-based) Register each Hyper-V host’s TPM (EKpub) with the HGS Establish baseline CI policy for each different H/W SKU Deploy HSM and use HSM-backed certificates Needs to support TPM v 2. 0 and UEFI 2. 3. 1 Highest levels of assurance Trust rooted in hardware Compliance with code-integrity policy required for keyrelease (attestation) Fabric-admin untrusted (Active Directory-based) Setup an Active Directory trust + register group Authorize a Hyper-V host to run shielded VMs by adding it to the Active Directory group Data-protection at rest and on-the-wire Secure DR to a hoster (VM already shielded) Weaker levels of assurance Fabric-admin is trusted No hardware-rooted trust or measured-boot No enforced code-integrity

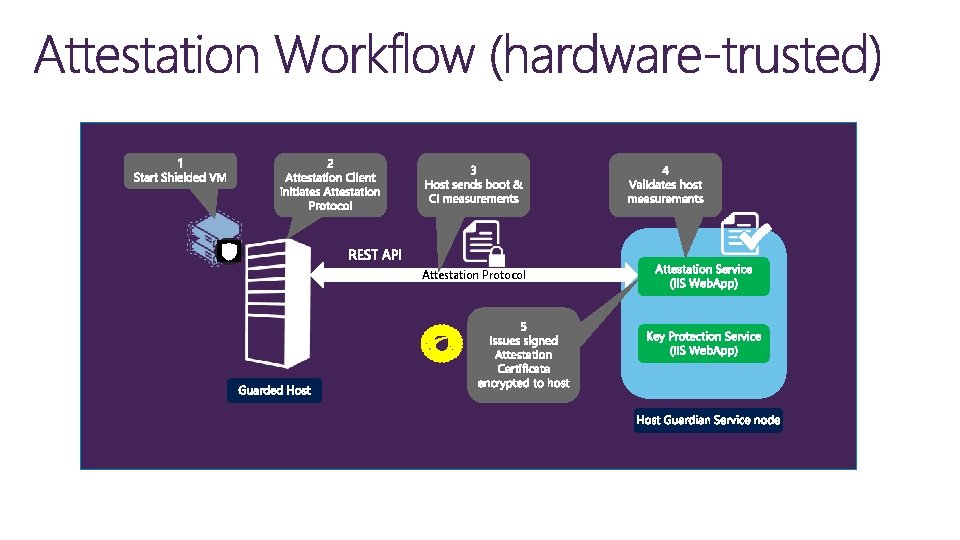
Attestation Protocol

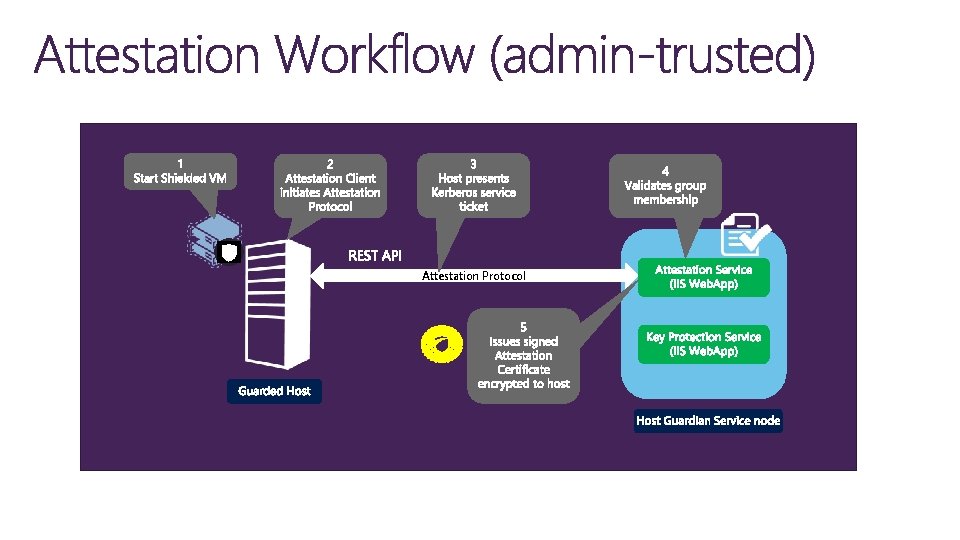
Attestation Protocol

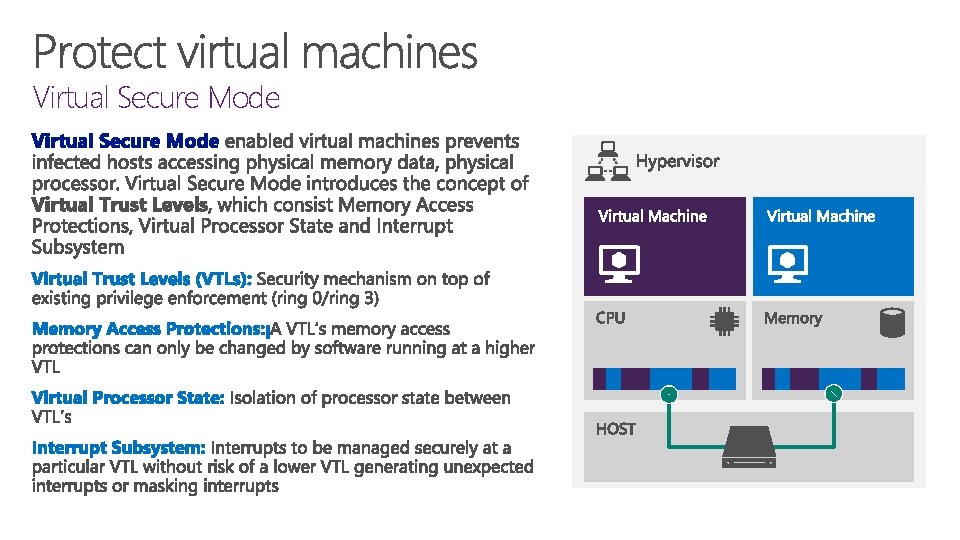
Virtual Secure Mode

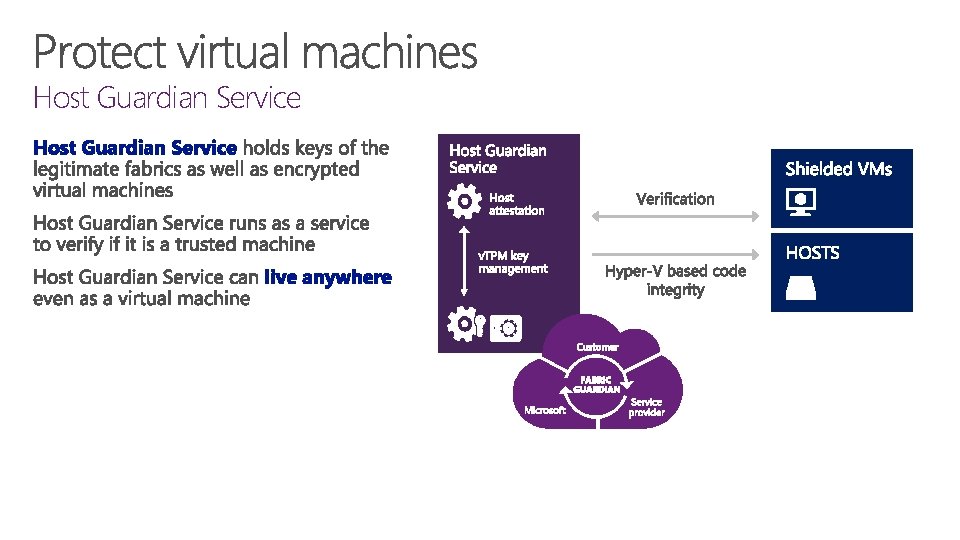
Host Guardian Service


• Providing kernel code integrity protections for Linux guest operating systems • Works with: • Power. Shell to enable: • Set-VMFirmware “Ubuntu” -Secure. Boot. Template Microsoft. UEFICertificate. Authority


Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
