Microsoft Virtual Academy Free online technical courses Take




![A leader in Gartner magic quadrants [1] Gartner “x 86 Server Virtualization Infrastructure, ” A leader in Gartner magic quadrants [1] Gartner “x 86 Server Virtualization Infrastructure, ”](https://slidetodoc.com/presentation_image/3a8d485889d7d1964ba63c2673a0ed11/image-5.jpg)




















- Slides: 46

Microsoft Virtual Academy Free, online, technical courses Take a free online course. http: //www. microsoftvirtualacademy. com



![A leader in Gartner magic quadrants 1 Gartner x 86 Server Virtualization Infrastructure A leader in Gartner magic quadrants [1] Gartner “x 86 Server Virtualization Infrastructure, ”](https://slidetodoc.com/presentation_image/3a8d485889d7d1964ba63c2673a0ed11/image-5.jpg)
A leader in Gartner magic quadrants [1] Gartner “x 86 Server Virtualization Infrastructure, ” by Thomas J. Bittman, Michael Warrilow, July 14 2015; [2] Gartner “Public Cloud Storage Services, ” by Arun Chandrasekaran, Raj Bala June 25, 2015; [3] Gartner “Magic Quadrant for Cloud Infrastructure as a Service, ” by Lydia Leong, Douglas Toombs, Bob Gill, May 18, 2015; [4] Gartner “Enterprise Application Platform as a Service, ” by Yefim V. Natis, Massimo Pezzini, Kimihiko Iijima, Anne Thomas, Rob Dunie , March 24, 2015. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.

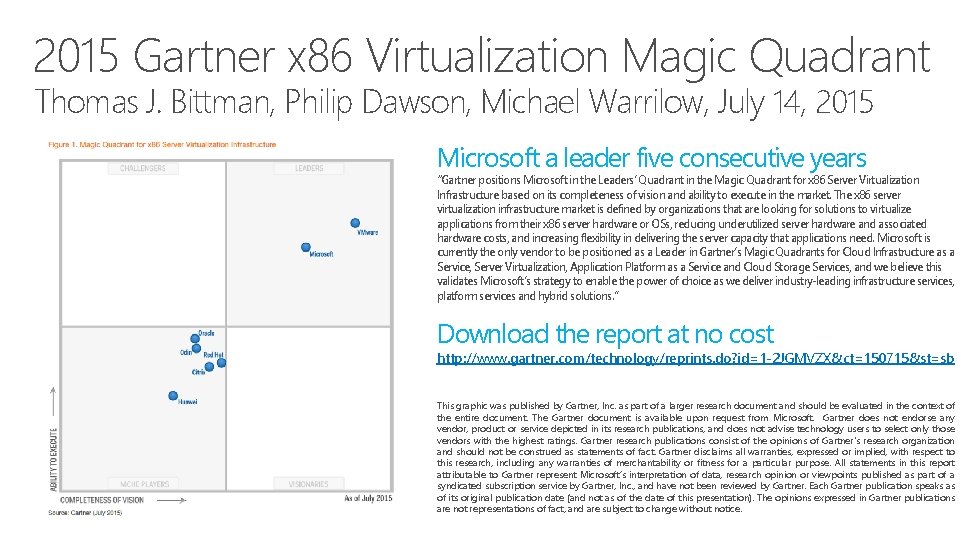
2015 Gartner x 86 Virtualization Magic Quadrant Thomas J. Bittman, Philip Dawson, Michael Warrilow, July 14, 2015 Microsoft a leader five consecutive years “Gartner positions Microsoft in the Leaders’ Quadrant in the Magic Quadrant for x 86 Server Virtualization Infrastructure based on its completeness of vision and ability to execute in the market. The x 86 server virtualization infrastructure market is defined by organizations that are looking for solutions to virtualize applications from their x 86 server hardware or OSs, reducing underutilized server hardware and associated hardware costs, and increasing flexibility in delivering the server capacity that applications need. Microsoft is currently the only vendor to be positioned as a Leader in Gartner’s Magic Quadrants for Cloud Infrastructure as a Service, Server Virtualization, Application Platform as a Service and Cloud Storage Services, and we believe this validates Microsoft’s strategy to enable the power of choice as we deliver industry-leading infrastructure services, platform services and hybrid solutions. ” Download the report at no cost http: //www. gartner. com/technology/reprints. do? id=1 -2 JGMVZX&ct=150715&st=sb This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Microsoft. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. All statements in this report attributable to Gartner represent Microsoft’s interpretation of data, research opinion or viewpoints published as part of a syndicated subscription service by Gartner, Inc. , and have not been reviewed by Gartner. Each Gartner publication speaks as of its original publication date (and not as of the date of this presentation). The opinions expressed in Gartner publications are not representations of fact, and are subject to change without notice.


Rising number of organizations suffer from breaches 1 2 1 3 2 3 3

Phishing attacks Stolen admin credentials Insider attacks 1. We know that administrators have the keys to the kingdom; we gave them those keys decades ago 2. But those administrators privileges are being compromised through social engineering, bribery, coercion, private initiatives

Problem A breach will (already did? ) happen Lacking the security-analysis manpower Can’t determine the impact of the breach Unable to adequately respond to the breach New approach (in addition to ‘prevention’) Limit or block the breach from spreading Detect the breach Respond to the breach

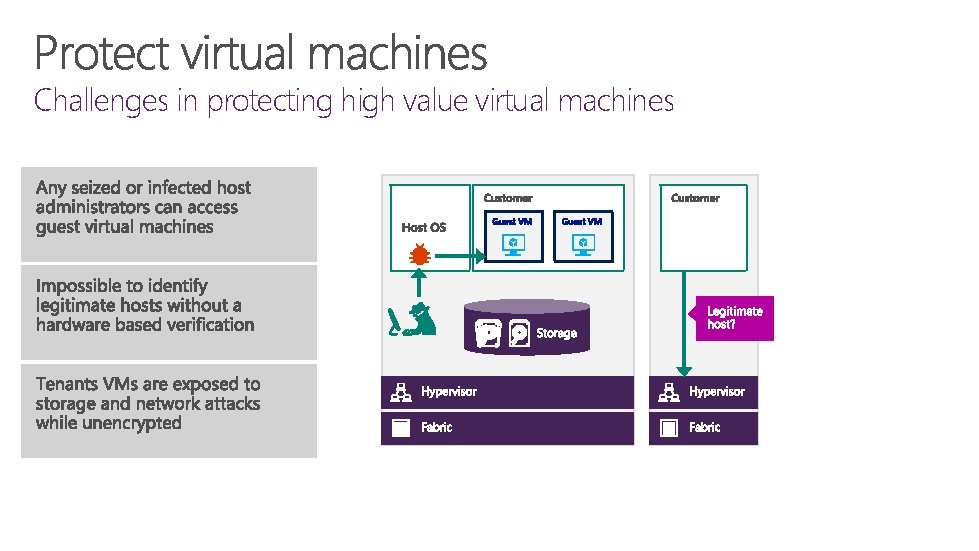
Challenges in protecting high value virtual machines

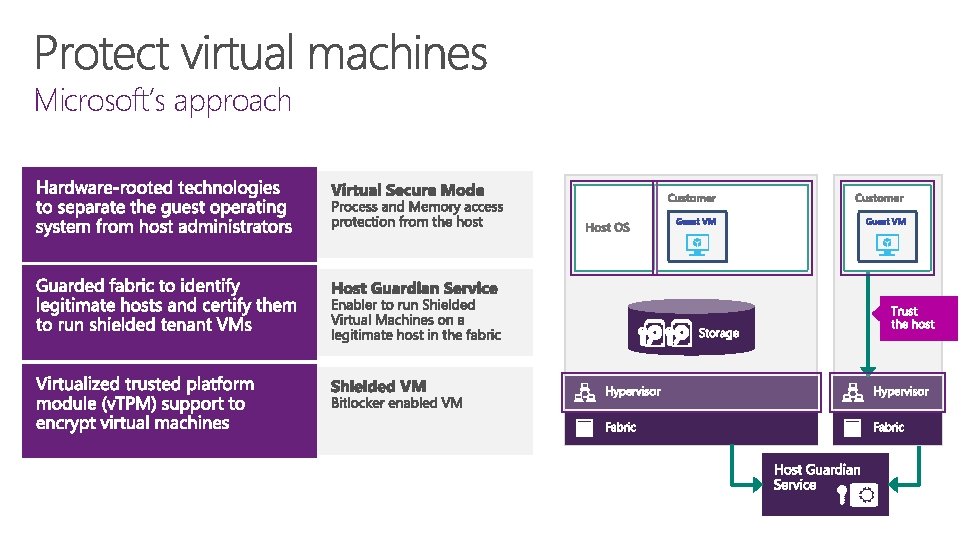
Microsoft’s approach

So what is a ‘Shielded VM’? “The data and state of a shielded VM are protected against inspection, theft and tampering from both malware and datacenter administrators 1. ” 1 fabric admins, storage admins, server admins, network admins

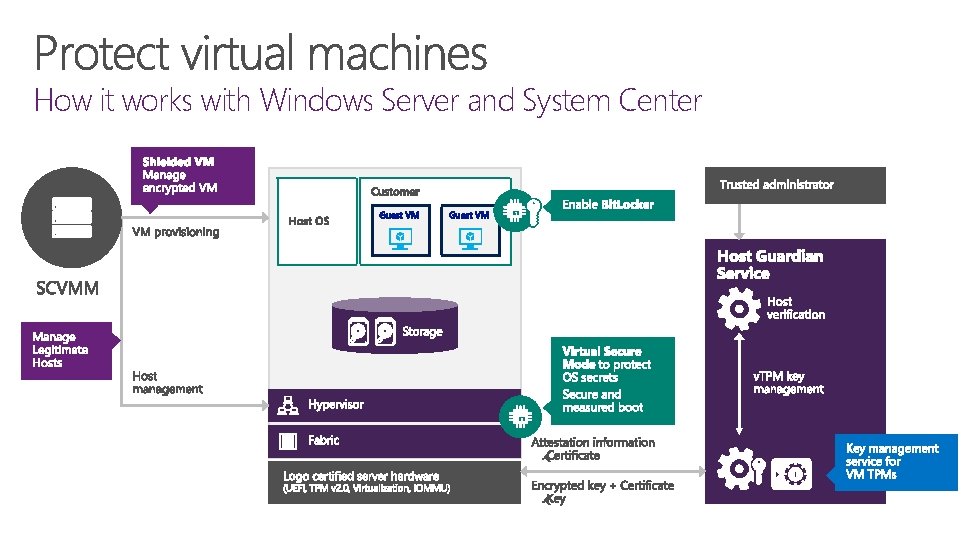
How it works with Windows Server and System Center

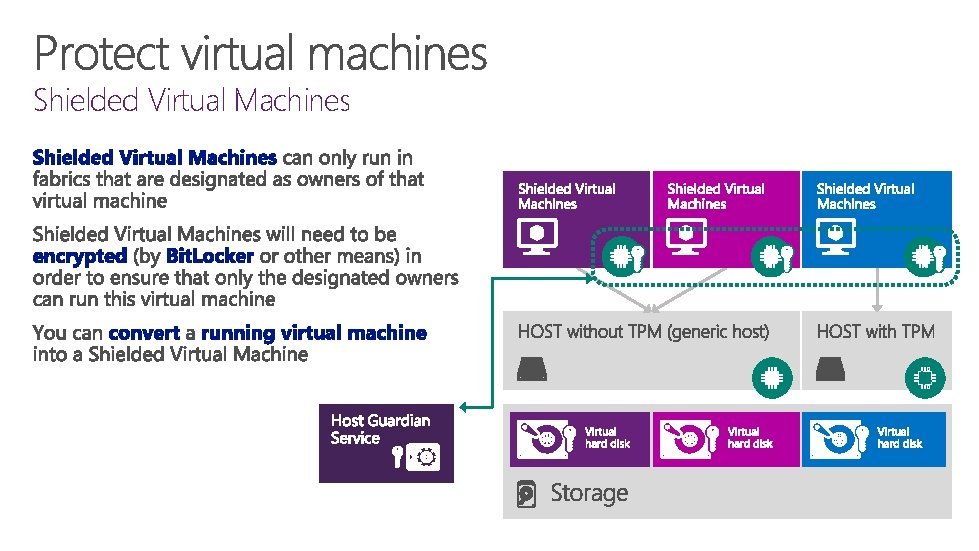
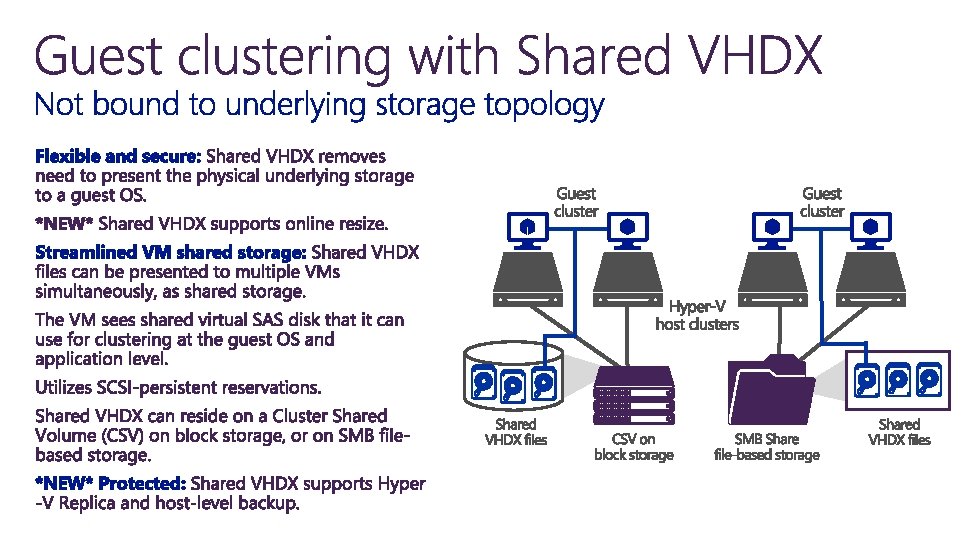
Shielded Virtual Machines

Encryption & data at-rest/in-flight protection Admin-lockout Attestation of health

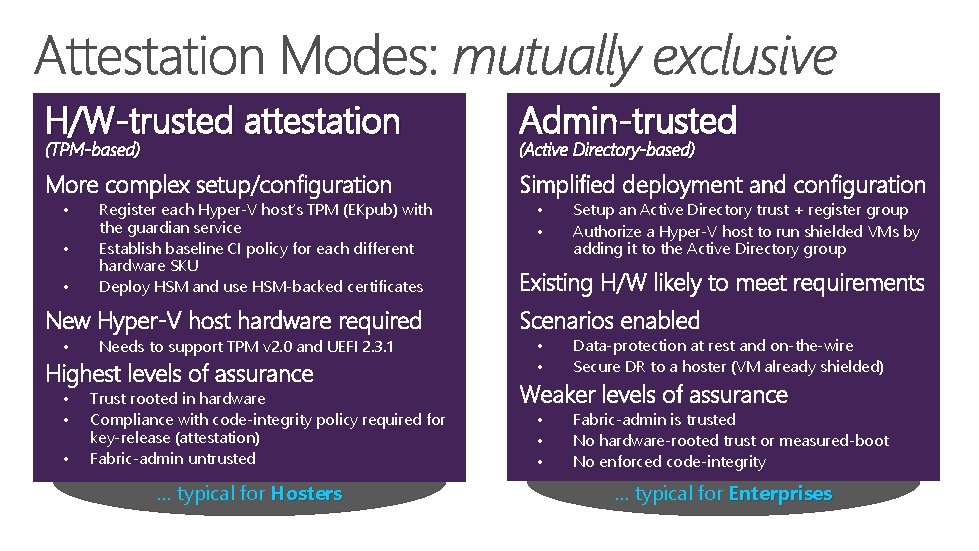
H/W-trusted attestation Admin-trusted More complex setup/configuration Simplified deployment and configuration (TPM-based) • • • Register each Hyper-V host’s TPM (EKpub) with the guardian service Establish baseline CI policy for each different hardware SKU Deploy HSM and use HSM-backed certificates New Hyper-V host hardware required • Needs to support TPM v 2. 0 and UEFI 2. 3. 1 Highest levels of assurance • • • Trust rooted in hardware Compliance with code-integrity policy required for key-release (attestation) Fabric-admin untrusted … typical for Hosters (Active Directory-based) • • Setup an Active Directory trust + register group Authorize a Hyper-V host to run shielded VMs by adding it to the Active Directory group Existing H/W likely to meet requirements Scenarios enabled • • Data-protection at rest and on-the-wire Secure DR to a hoster (VM already shielded) Weaker levels of assurance • • • Fabric-admin is trusted No hardware-rooted trust or measured-boot No enforced code-integrity … typical for Enterprises

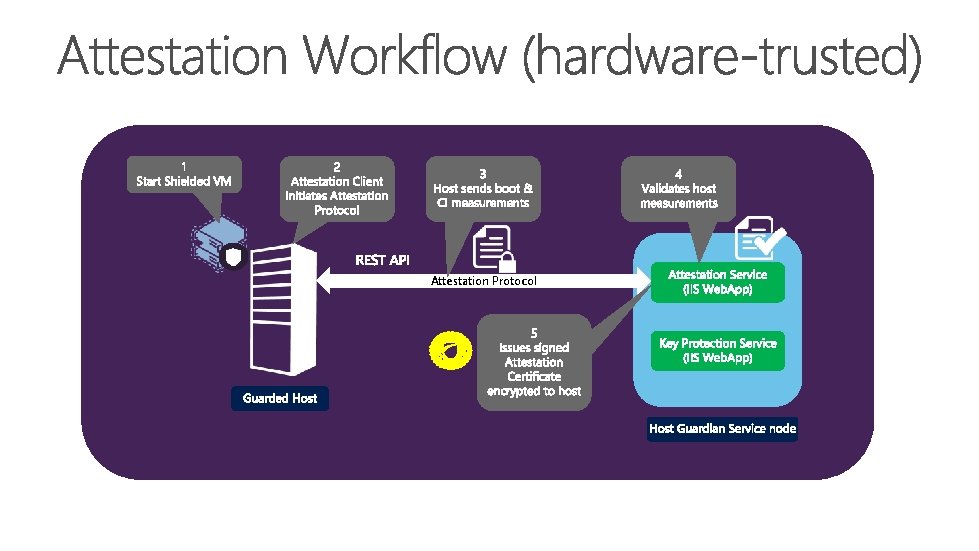
Attestation Protocol

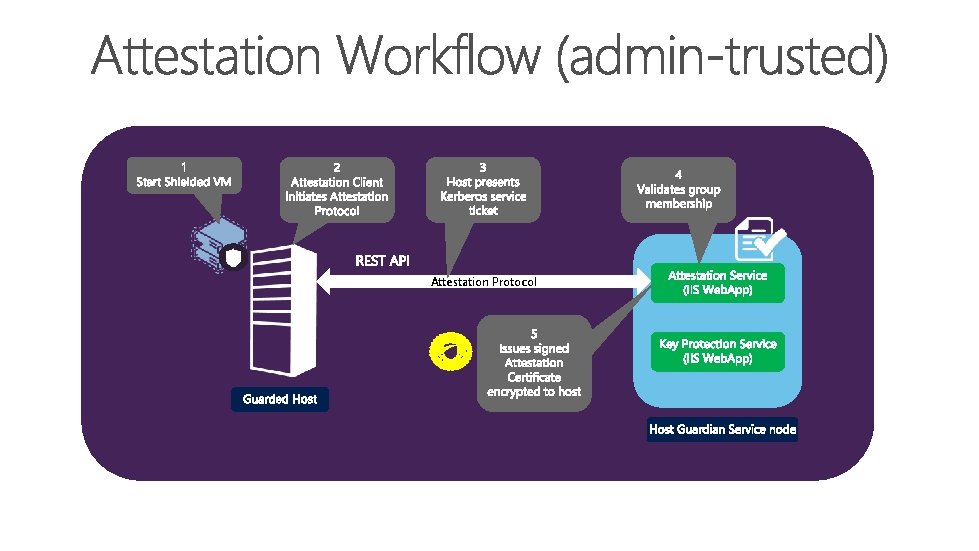
Attestation Protocol


• Providing kernel code integrity protections for Linux guest operating systems • Works with: • Power. Shell to enable: • Set-VMFirmware “Ubuntu” -Secure. Boot. Template Microsoft. UEFICertificate. Authority







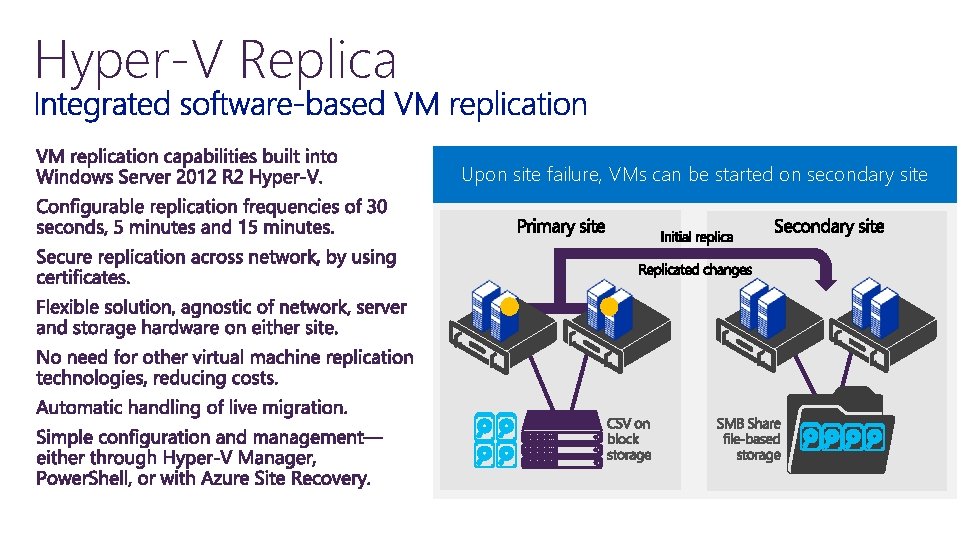
Hyper-V Replica Once Uponreplicated, Hyper-V site failure, Replica changes VMs is can enabled, replicated be started VMs onon chosen begin secondary replication frequency site

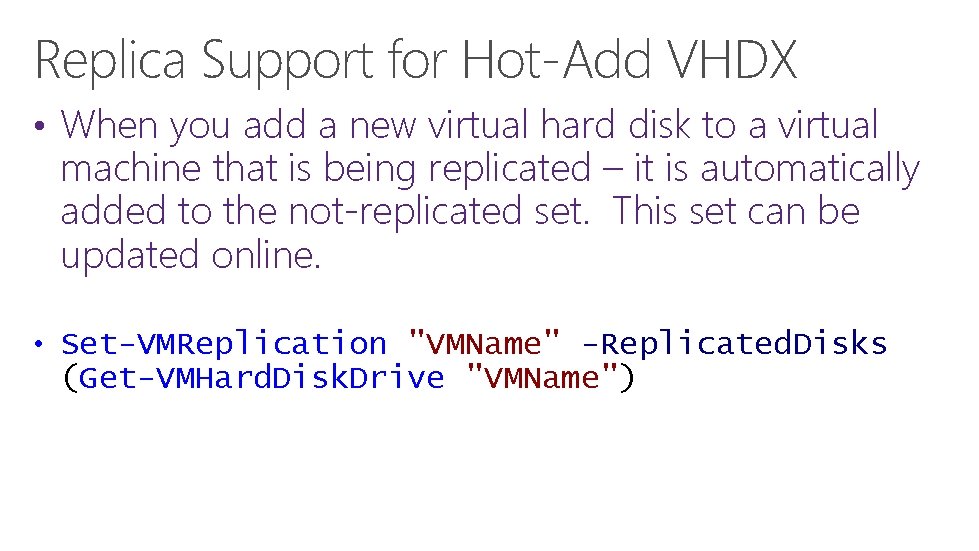
Replica Support for Hot-Add VHDX • When you add a new virtual hard disk to a virtual machine that is being replicated – it is automatically added to the not-replicated set. This set can be updated online. • Set-VMReplication "VMName" -Replicated. Disks (Get-VMHard. Disk. Drive "VMName")



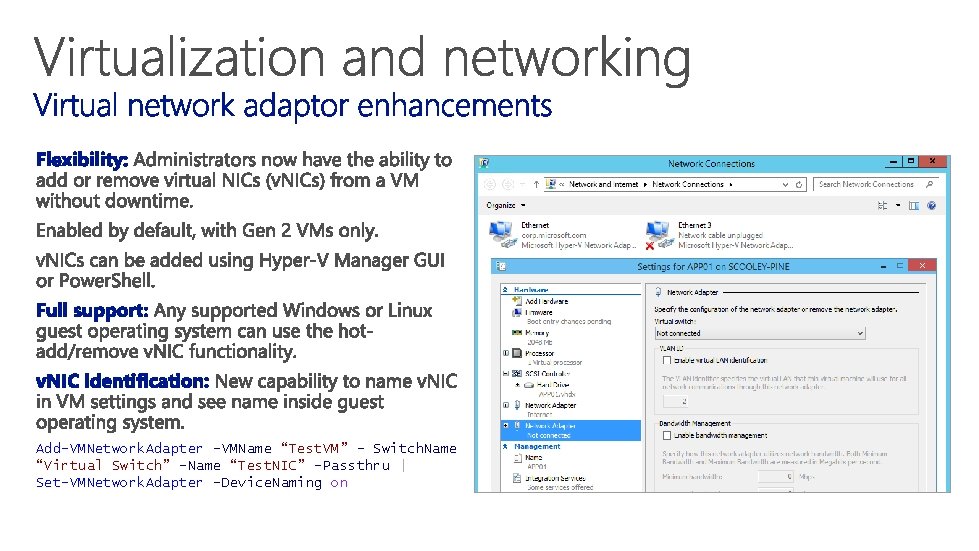
Add-VMNetwork. Adapter -VMName “Test. VM” – Switch. Name “Virtual Switch” -Name “Test. NIC” -Passthru | Set-VMNetwork. Adapter -Device. Naming on



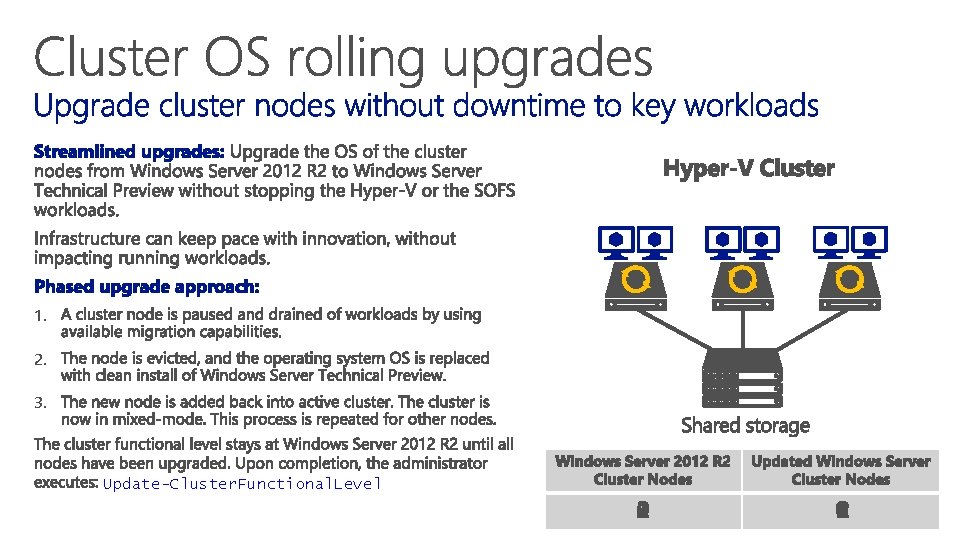
1. 2. 3. Update-Cluster. Functional. Level 0 1 2 3 1 0

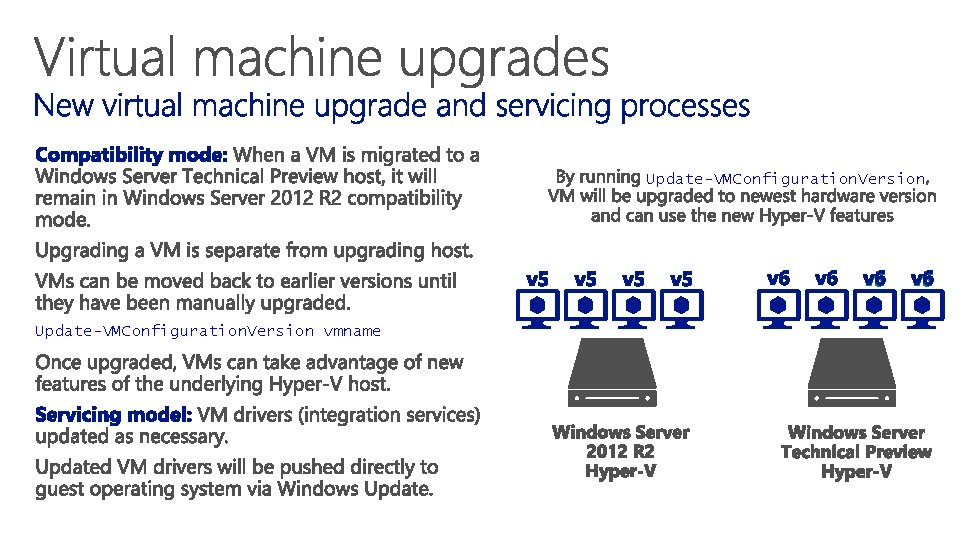
Update-VMConfiguration. Version vmname


• Windows 8. 1 / 2012 R 2 • Windows 10 / Windows Server Technical Preview



• Bridge the boundary between Hyper-V host and guest VM in a secure way to issue PS cmdlets and run scripts easily. • • No need to configure PS Remoting Or Network Connectivity. Just need the guest credentials Can only connect to particular guest from that host. Enter-PSSession -VMName Invoke-Command -VMName -Script. Block { Fancy Script }


• Resilient File System • It maximizes data availability, despite errors that would historically cause data loss or downtime. • Taking advantage of an intelligent file system for:


Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
