Merged Processes of Petri nets Victor Khomenko Joint












- Slides: 39

Merged Processes of Petri nets Victor Khomenko Joint work with Alex Kondratyev, Maciej Koutny and Walter Vogler

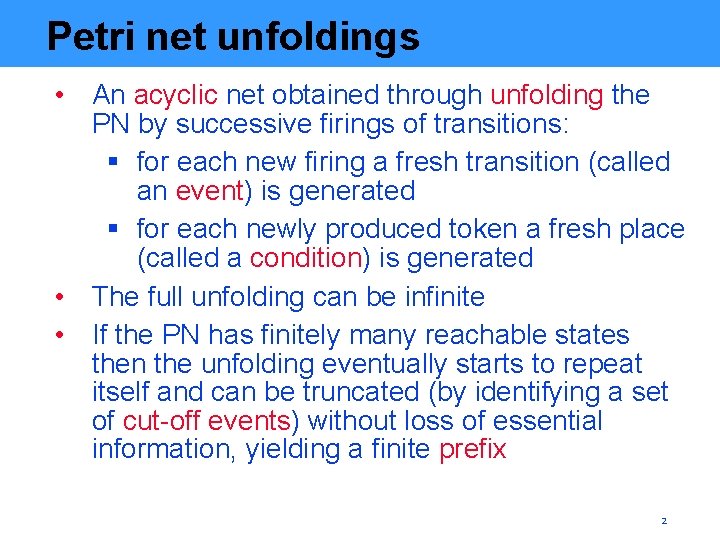
Petri net unfoldings • An acyclic net obtained through unfolding the PN by successive firings of transitions: § for each new firing a fresh transition (called an event) is generated § for each newly produced token a fresh place (called a condition) is generated • The full unfolding can be infinite • If the PN has finitely many reachable states then the unfolding eventually starts to repeat itself and can be truncated (by identifying a set of cut-off events) without loss of essential information, yielding a finite prefix 2

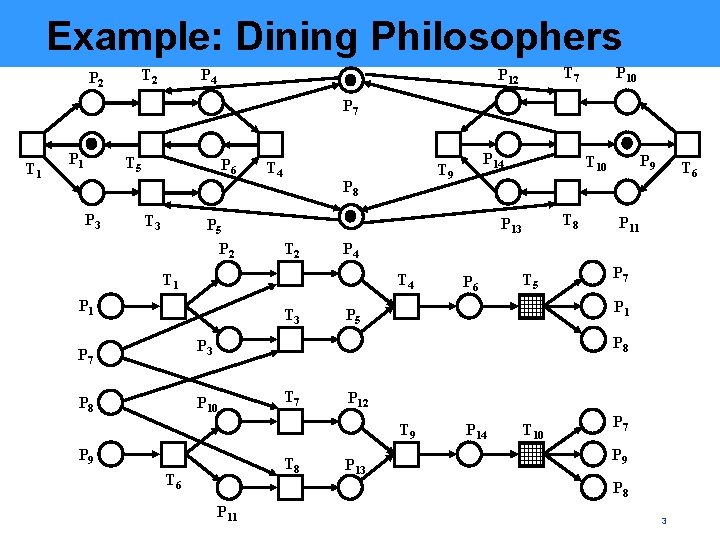
Example: Dining Philosophers T 2 P 4 T 7 P 12 P 10 P 7 T 1 P 1 T 5 P 3 P 6 T 3 P 5 P 2 T 4 P 8 T 2 T 8 P 6 T 5 P 8 P 11 P 7 P 1 P 5 P 8 P 3 P 7 T 6 P 4 T 3 P 9 T 10 P 13 T 1 P 14 T 9 P 10 T 7 P 12 T 9 P 9 T 8 T 6 P 13 P 14 T 10 P 7 P 9 P 8 P 11 3

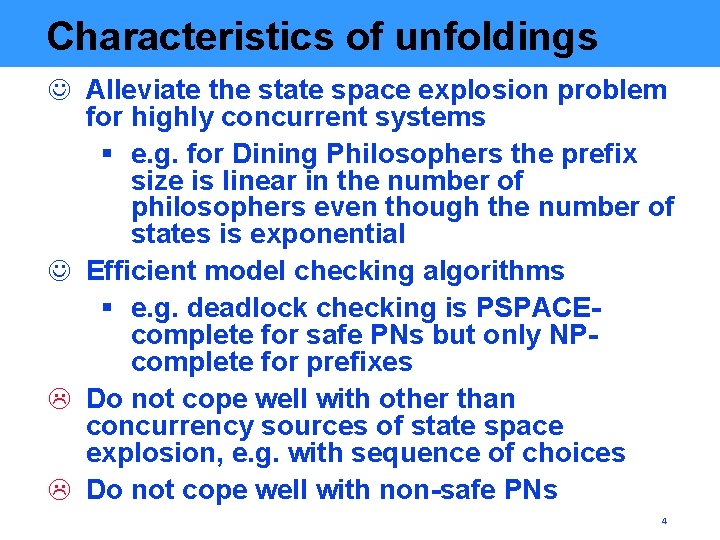
Characteristics of unfoldings J Alleviate the state space explosion problem for highly concurrent systems § e. g. for Dining Philosophers the prefix size is linear in the number of philosophers even though the number of states is exponential J Efficient model checking algorithms § e. g. deadlock checking is PSPACEcomplete for safe PNs but only NPcomplete for prefixes L Do not cope well with other than concurrency sources of state space explosion, e. g. with sequence of choices L Do not cope well with non-safe PNs 4

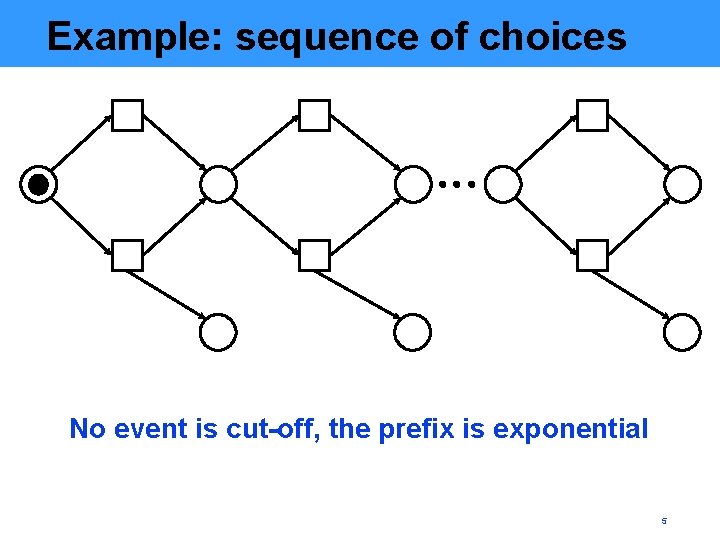
Example: sequence of choices No event is cut-off, the prefix is exponential 5

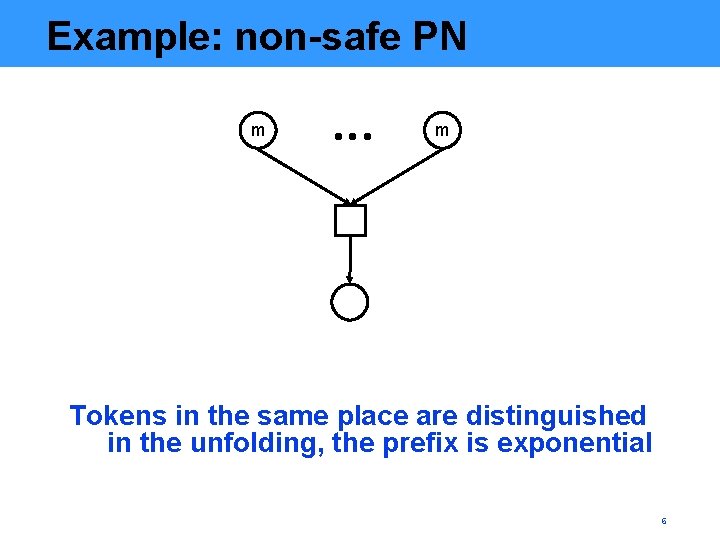
Example: non-safe PN m m Tokens in the same place are distinguished in the unfolding, the prefix is exponential 6

Wanted A data structure coping not only with concurrency but also with other sources of state space explosion 7

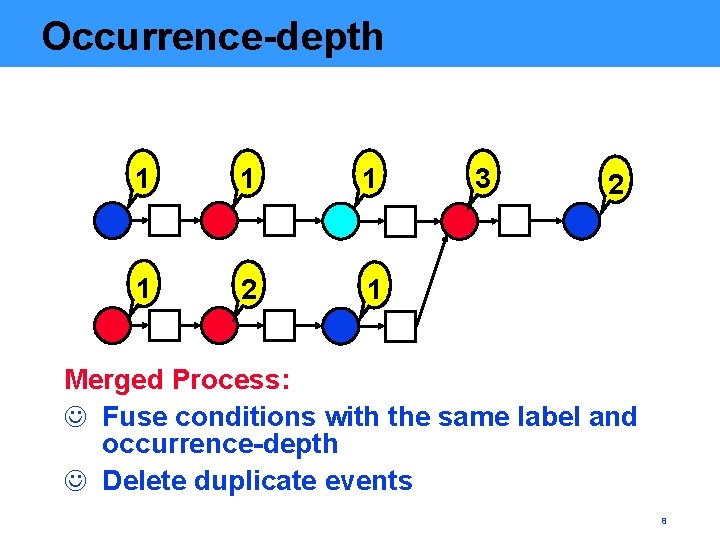
Occurrence-depth 1 1 2 1 3 2 Merged Process: J Fuse conditions with the same label and occurrence-depth J Delete duplicate events 8

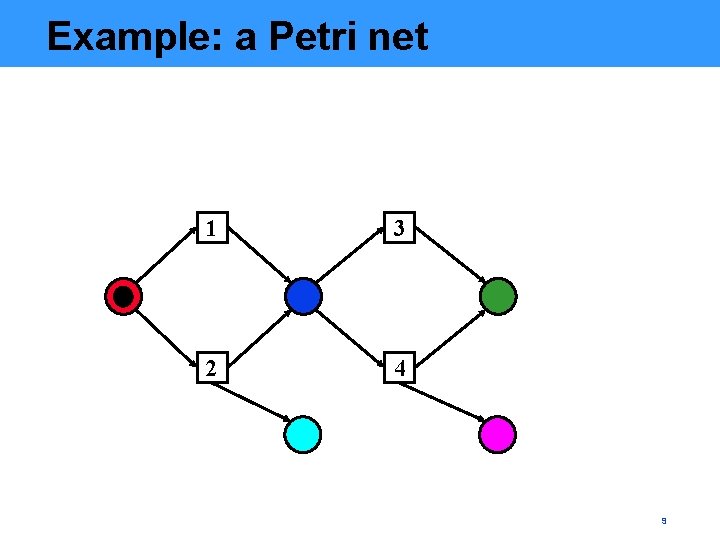
Example: a Petri net 1 3 2 4 9

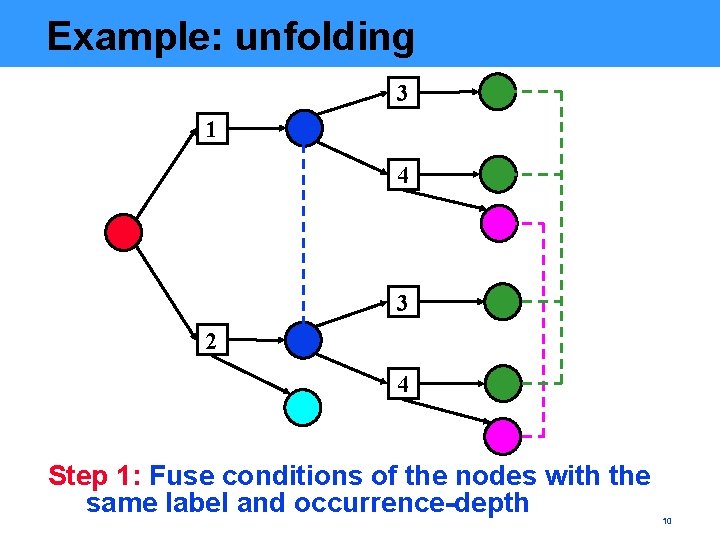
Example: unfolding 3 1 4 3 2 4 Step 1: Fuse conditions of the nodes with the same label and occurrence-depth 10

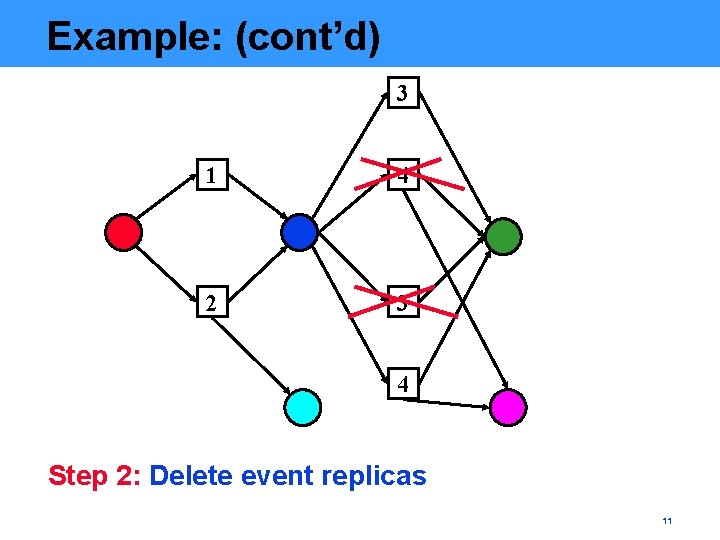
Example: (cont’d) 3 1 4 2 3 4 Step 2: Delete event replicas 11

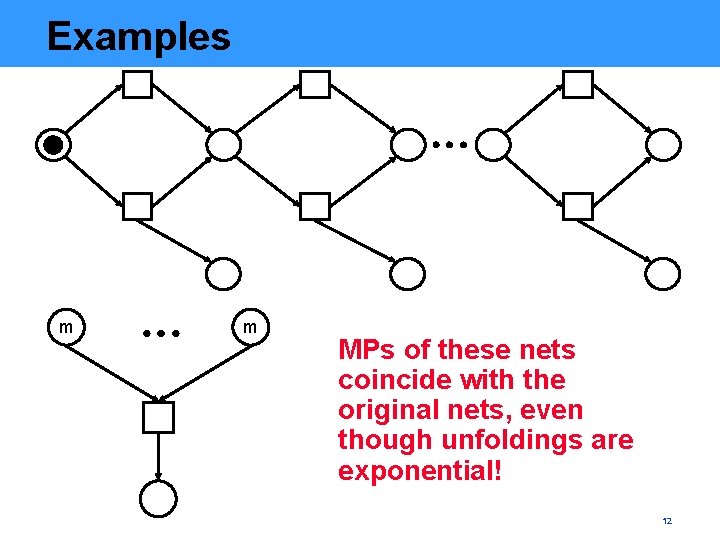
Examples m m MPs of these nets coincide with the original nets, even though unfoldings are exponential! 12

Properties of MPs • • • Canonicity Finiteness Completeness Theoretical upper bounds on size Experimental results: size 13

Canonicity • Easily follows from the canonicity of unfolding prefixes: Canonical MP = Merge(Canonical prefix) 14

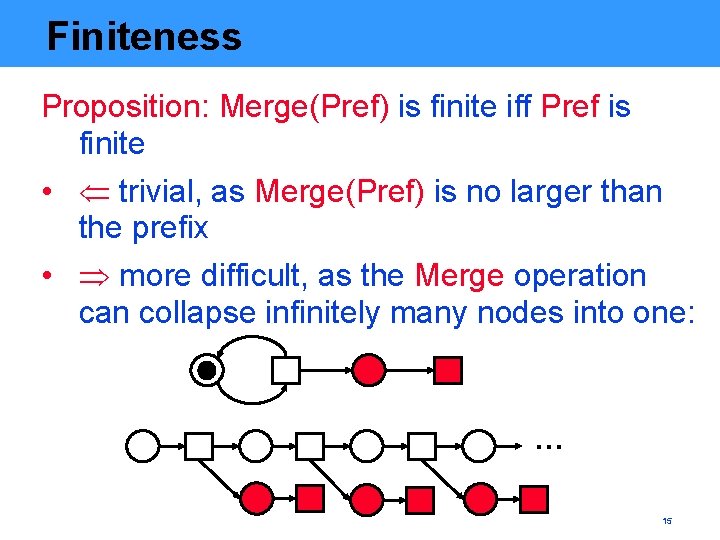
Finiteness Proposition: Merge(Pref) is finite iff Pref is finite • trivial, as Merge(Pref) is no larger than the prefix • more difficult, as the Merge operation can collapse infinitely many nodes into one: … 15

Finiteness (cont’d) • follows from the analog of Köning’s lemma for branching processes: § an infinite branching process contains an infinite causal chain § hence there are infinitely many instances of some place p along it § hence the occurrence-depth of instances of p is unbounded § hence there are infinitely many instances of p in the merged process 16

Completeness • Preservation of firings is tricky – it’s hard to define cut-offs since an event can have multiple local configurations • Hence consider only markingcompleteness (good enough for model checking as the firings can be retrieved from the original PN) Proposition: if Pref is marking-complete then Merge(Pref) is marking-complete 17

Theoretical upper bounds on size • Trivial bound: Merge(Pref) is never larger than Pref, hence never larger than the reachability graph § too pessimistic in practice • MPs of acyclic PN coincide with the original PNs with the dead nodes removed § unfoldings can be exponential • MPs of live and safe free-choice PNs [with minor restrictions] are polynomial in the size of the original PNs § unfoldings can be exponential 18

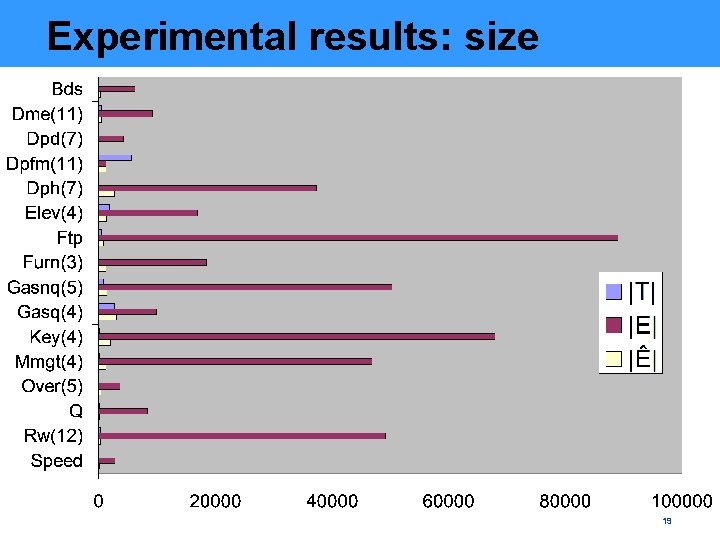
Experimental results: size 19

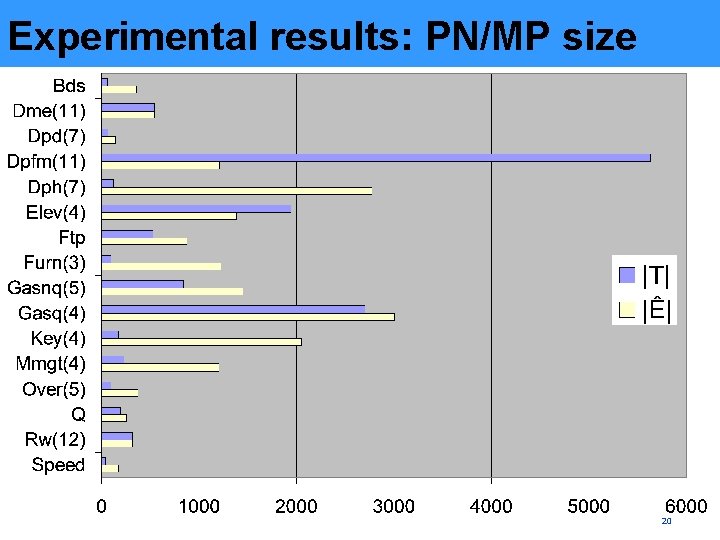
Experimental results: PN/MP size 20

Experimental results: summary • Corbett’s benchmarks were used • MPs are often by orders of magnitude smaller than unfolding prefixes • In many cases MPs are just slightly larger than the original PNs • In some cases MPs are smaller than the original PNs due to removal of dead nodes 21

Model checking • MPs are small, but are they of any use in practice? • Can model checking algorithms developed for unfoldings be lifted to MPs? • In what follows, we consider safe PNs only 22

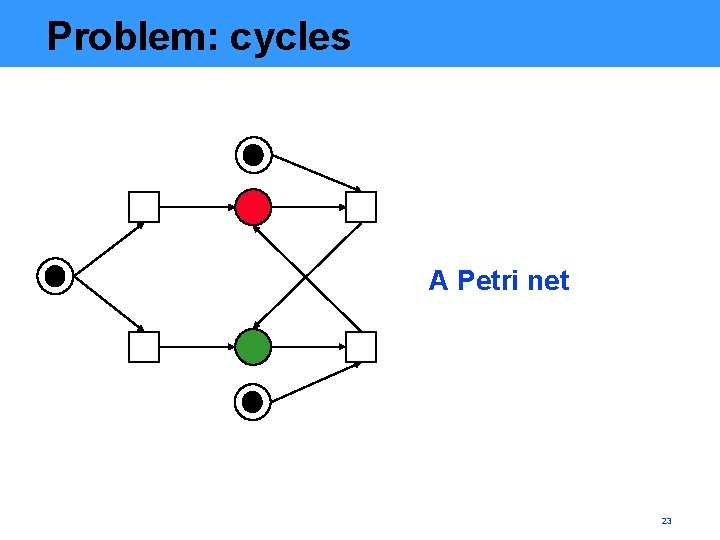
Problem: cycles A Petri net 23

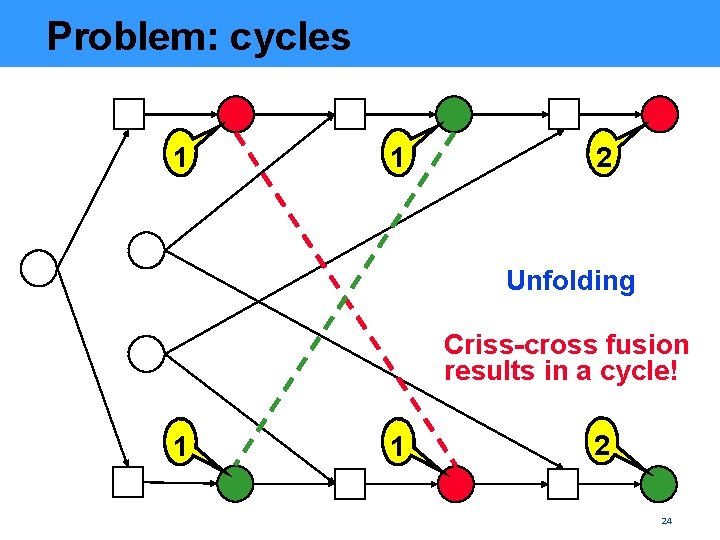
Problem: cycles 1 1 2 Unfolding Criss-cross fusion results in a cycle! 1 1 2 24

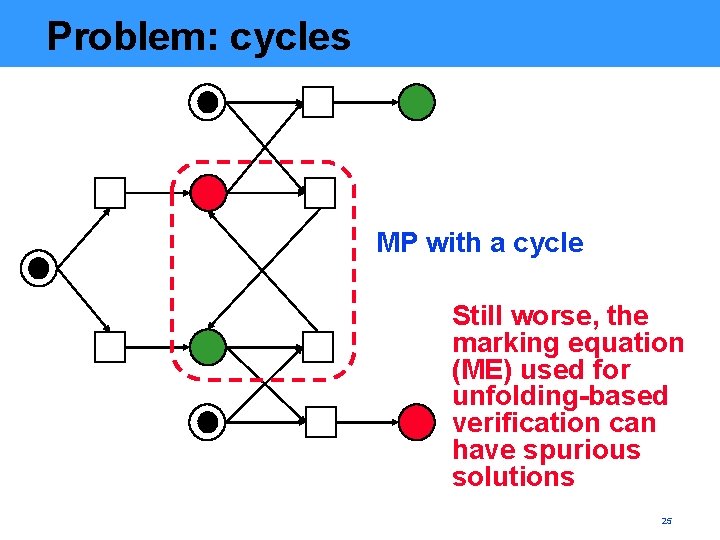
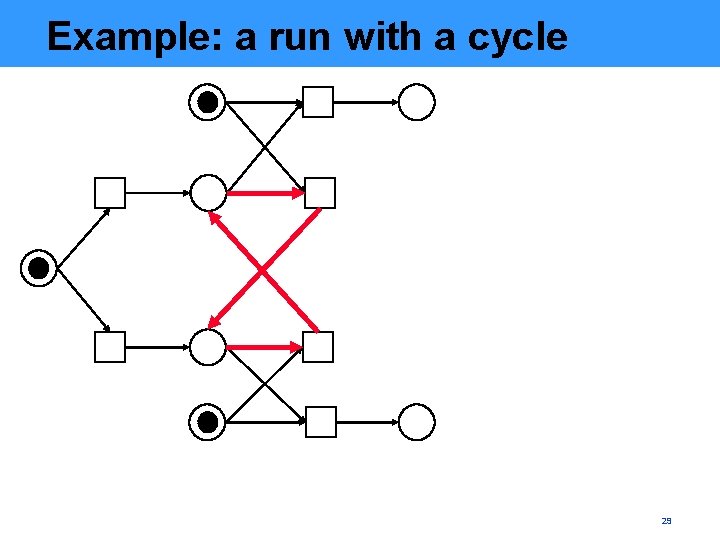
Problem: cycles MP with a cycle Still worse, the marking equation (ME) used for unfolding-based verification can have spurious solutions 25

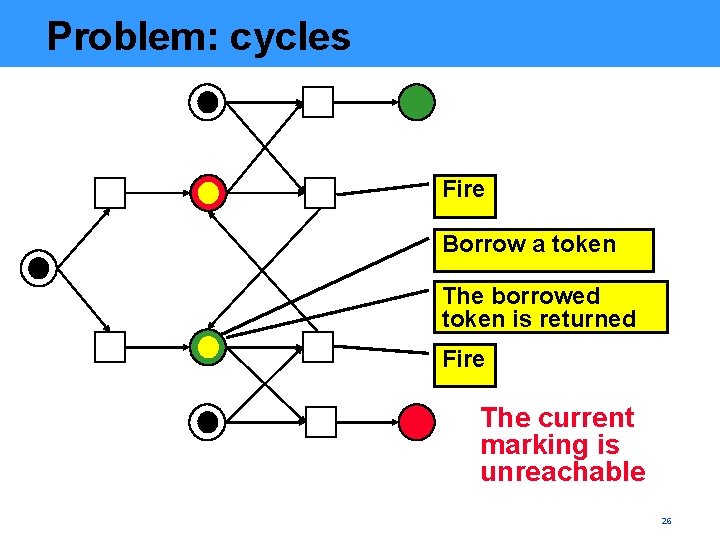
Problem: cycles Fire Borrow a token The borrowed token is returned Fire The current marking is unreachable 26

Solution • Add to the marking equation another constraint, ACYCLIC, requiring the run to be acyclic: ME & ACYCLIC 27

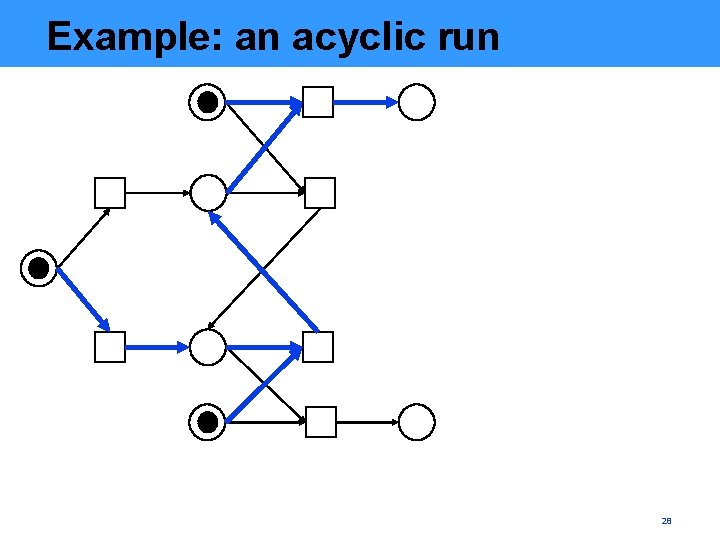
Example: an acyclic run 28

Example: a run with a cycle 29

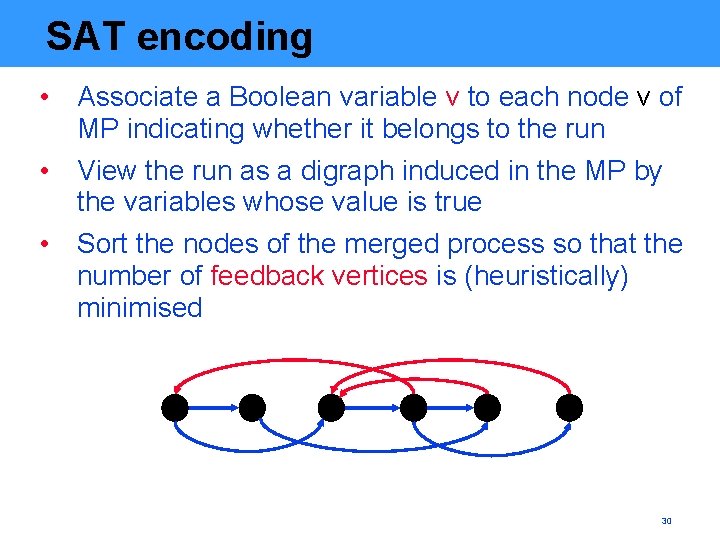
SAT encoding • Associate a Boolean variable v to each node v of MP indicating whether it belongs to the run • View the run as a digraph induced in the MP by the variables whose value is true • Sort the nodes of the merged process so that the number of feedback vertices is (heuristically) minimised 30

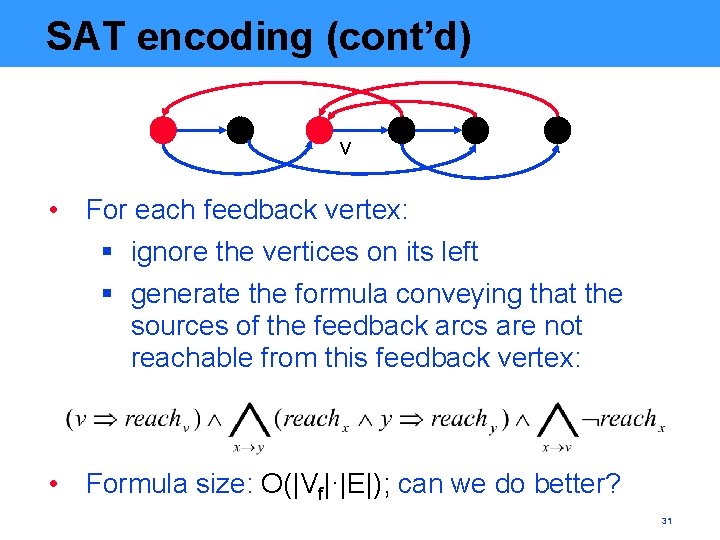
SAT encoding (cont’d) v • For each feedback vertex: § ignore the vertices on its left § generate the formula conveying that the sources of the feedback arcs are not reachable from this feedback vertex: • Formula size: O(|Vf|·|E|); can we do better? 31

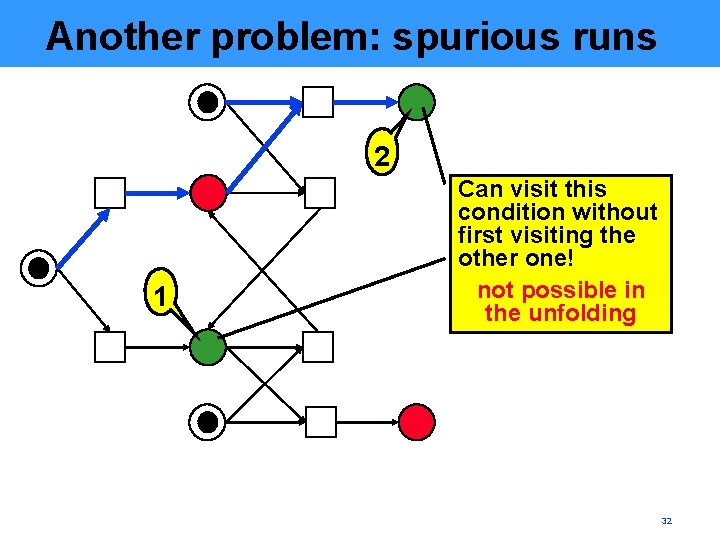
Another problem: spurious runs 2 1 Can visit this condition without first visiting the other one! not possible in the unfolding 32

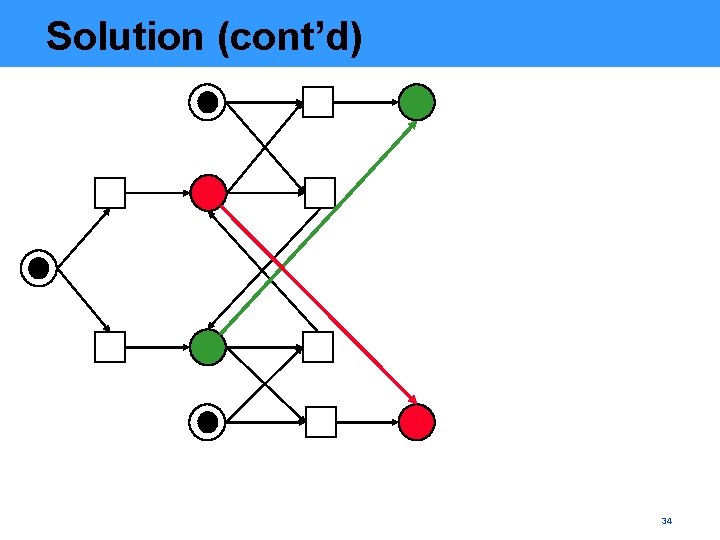
Solution • Add another constraint, NG (no-gap), conveying that § if a condition with occurrence-depth k>1 is visited then the condition with the same label and occurrence-depth k-1 is also visited § the conditions with the same label are visited in the order of increase of the occurrence depth (can be enforced by ACYCLIC by adding a few arcs) 33

Solution (cont’d) 34

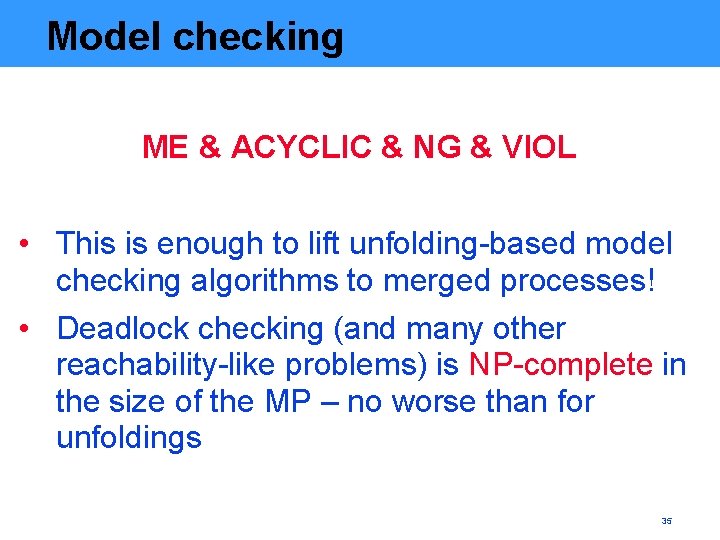
Model checking ME & ACYCLIC & NG & VIOL • This is enough to lift unfolding-based model checking algorithms to merged processes! • Deadlock checking (and many other reachability-like problems) is NP-complete in the size of the MP – no worse than for unfoldings 35

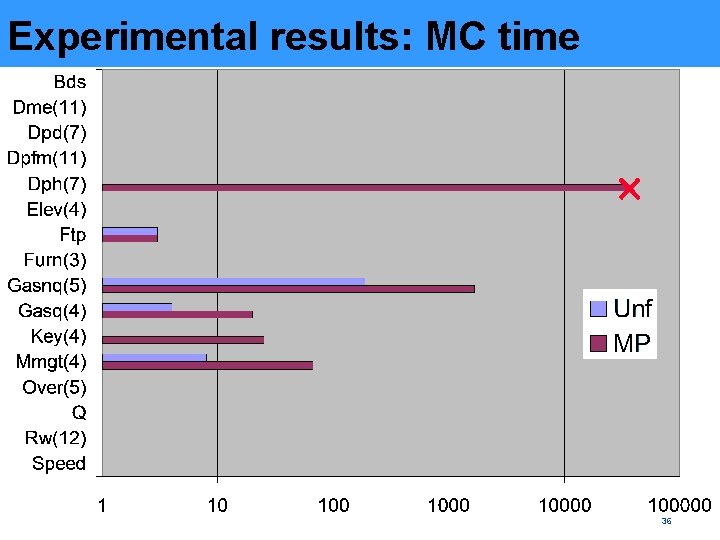
Experimental results: MC time 36

Experimental results • Corbett’s benchmarks were used • Model checking is practical – running times are comparable with those of an unfolding-based algorithm • Still deteriorates on a couple of benchmarks – but it’s early days of this approach and we keep improving it 37

Open problems / future work • Direct characterization of MPs (cf. the characterization of unfoldings by occurrence nets) § currently much is done via unfoldings • Improve the efficiency of model checking § the SAT encoding of ACYCLIC is the main problem • A direct algorithm for building MPs § currently built by fusing nodes in the unfolding prefix 38

Algorithm for building MPs Idea: reduce the problem of finding a possible extension to the following problem: • Find a configuration C in the built part of the MP such that: § C can be extended by a new event and § C contains no cut-offs, i. e. for each event e in C there is no configuration C’ in the built part of MP such that Mark([e]C)=Mark(C’) and C’ [e]C • Reducible to QBF with 1(? ) alternation • Reducible to SAT if the adequate order is 39
 Victor khomenko
Victor khomenko Victor khomenko
Victor khomenko Victor khomenko
Victor khomenko Petri nets properties analysis and applications
Petri nets properties analysis and applications Petri nets properties analysis and applications
Petri nets properties analysis and applications Nfa merged with ffa
Nfa merged with ffa Northern renaissance thinkers merged humanist ideas with
Northern renaissance thinkers merged humanist ideas with Suggested upper merged ontology
Suggested upper merged ontology Nejime definition floral design
Nejime definition floral design Concurrent processes are processes that
Concurrent processes are processes that List the 4 nets for better internet searching
List the 4 nets for better internet searching Nets and drawing for visualizing geometry
Nets and drawing for visualizing geometry Yuygo
Yuygo Nets and drawings for visualizing geometry
Nets and drawings for visualizing geometry Represent solid figures using nets
Represent solid figures using nets Crystallography
Crystallography Stca aviation
Stca aviation Net of a cube
Net of a cube Partitioned semantic network in artificial intelligence
Partitioned semantic network in artificial intelligence Nets of square pyramid
Nets of square pyramid Slot filler
Slot filler Lesson 1 nets and drawings for visualizing geometry
Lesson 1 nets and drawings for visualizing geometry Nets blox
Nets blox Surface area using nets
Surface area using nets Nets church planting
Nets church planting Apple sweatshops
Apple sweatshops Semantic nets and frames
Semantic nets and frames Bayes nets
Bayes nets 29 cfr 1926 subpart m
29 cfr 1926 subpart m What is a permanent joint
What is a permanent joint Memorandum joint venture
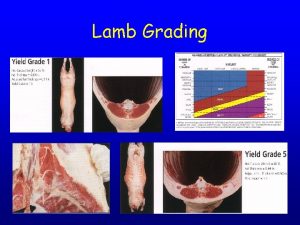
Memorandum joint venture Lamb grading chart
Lamb grading chart Lamb carcass grading
Lamb carcass grading Hyaline cartilage between vertebrae
Hyaline cartilage between vertebrae Condyloid ellipsoidal joint
Condyloid ellipsoidal joint Reseaux de petri
Reseaux de petri Ortopedi kotka
Ortopedi kotka Petri nietosvaara
Petri nietosvaara Petri sipola
Petri sipola Petri dish - tradução
Petri dish - tradução