Mata Kuliah CSS113 Konsep Sistem Informasi Tahun Akademik















- Slides: 20

Mata Kuliah : CSS-113 , Konsep Sistem Informasi Tahun Akademik : 2012/2013 MEMBUAT , MENGELOLA RESIKO DAN KRIMINALITAS SISTEM INFORMASI Pertemuan-10 Sasaran Pembelajaran Pada akhir pertemuan ini, diharapkan mahasiswa akan mampu : Menjelaskan sistem keamanan dan kontrol pada 10 -1 Teknologi Informasi

Materi Pokok • Ancaman terhadap kegagalan project • Ancaman terhadap tidak berfungsinya sistem • Ancaman terhadap kriminalitas komputer Information System Security and Control • • • Threat of Project Failure Threat of Accidents and Malfunctions Threat of Computer Crime Factors That Increase the Risks Methods for Minimizing Risks 10 -2

Introductory Case: London Ambulance Service • • Wow, what a mess! What did they do wrong? Did they do anything right? Was this a system that should have even been attempted? 10 -3

Threat of Project Failure • When can projects fail? INITIATION • • The reasons for building the system have too little support. The system seems too expensive. DEVELOPMENT • • • It is too difficult to define the requirements. The system is not technically feasible. The project is too difficult for technical staff assigned. IMPLEMENTATION • The system requires too great a change from existing work practices. • Potential users dislike the system or resist using it. • Too little effort is put into the implementation. OPERATION AND MAINTENANCE • System controls are insufficient. • Too little effort goes into supporting effective use. • The system is not updated as business needs change. 10 -4

Threat of Project Failure • Remember this? • What do you think the curve would look like for cost of failure? 10 -5

Threat of Accidents and Malfunctions • Operator error • Hardware malfunction – Intel Pentium bug – Was like the embedded chip issue for Y 2 K • Software bugs • Data errors • Damage to physical facilities – We’ll talk more about this for disaster recovery • Inadequate system performance – London ambulance case 10 -6

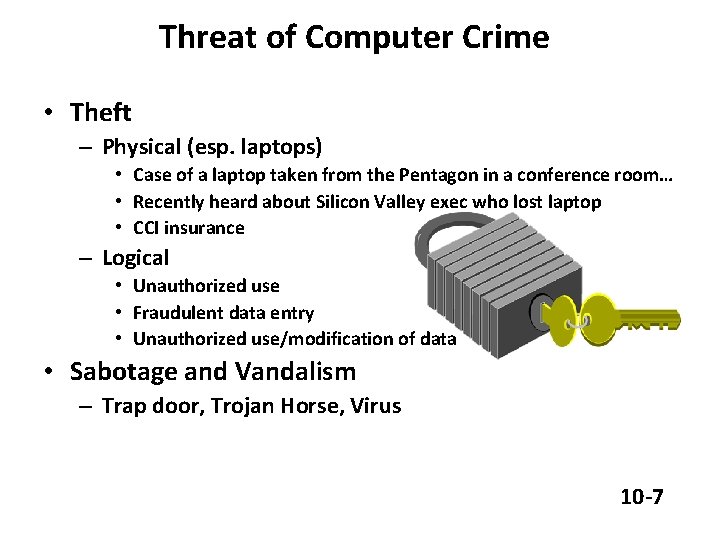
Threat of Computer Crime • Theft – Physical (esp. laptops) • Case of a laptop taken from the Pentagon in a conference room… • Recently heard about Silicon Valley exec who lost laptop • CCI insurance – Logical • Unauthorized use • Fraudulent data entry • Unauthorized use/modification of data • Sabotage and Vandalism – Trap door, Trojan Horse, Virus 10 -7

Factors that Increase Risk • Nature of Complex Systems • Human Limitations • Pressures in the Business Environment 10 -8

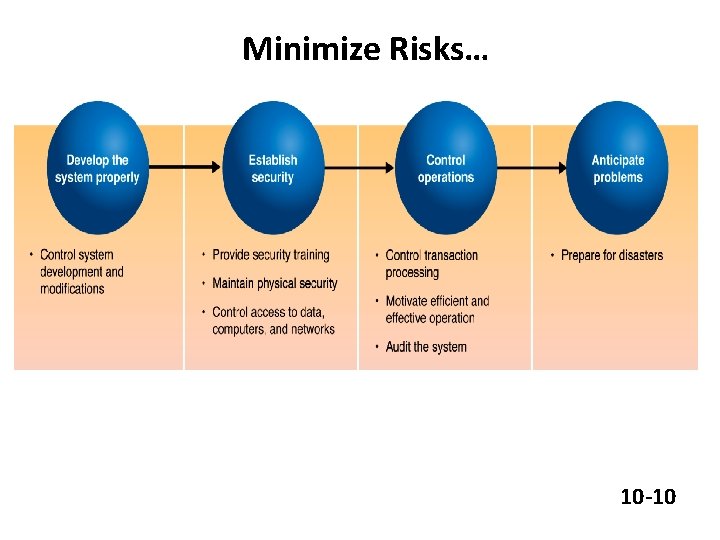
Methods for Minimizing Risks • • Controlling System Development and Modifications Providing Security Training Maintaining Physical Security Controlling Access to Data, Computers, and Networks Controlling Transaction Processing Motivating Efficient and Effective Operation Auditing the Information System Preparing for Disasters 10 -9

Minimize Risks… 10 -10

Build the system correctly… • Software change control 10 -11

Train the users about security… Maintain physical security… 10 -12

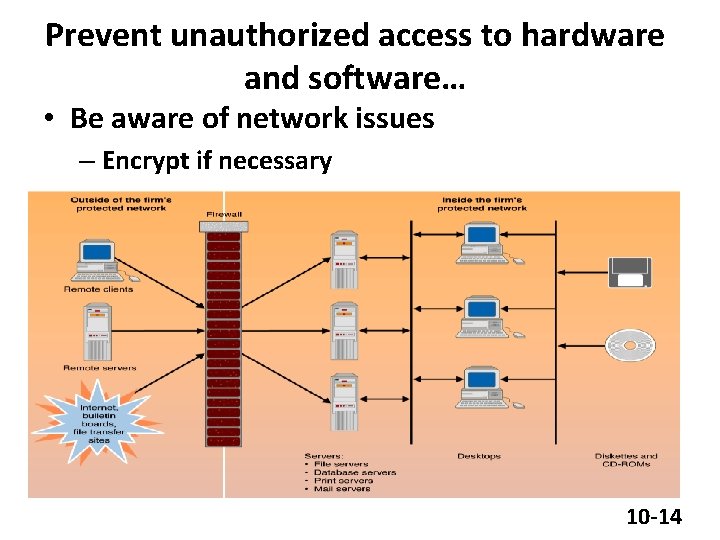
Prevent unauthorized access to hardware and software… • Manual data handling • Access privileges • Access control – What you know – What you have – Where you are – Who you are 10 -13

Prevent unauthorized access to hardware and software… • Be aware of network issues – Encrypt if necessary 10 -14

Perform transactions correctly… • • Segregation of duties Data validation Error correction Backup & recovery 10 -15

Innovate for efficiency… • • Monitor systems Look for opportunities Look for incentives Look for disincentives 10 -16

Audit your system… • Trust but verify… 10 -17

Prepare for disasters… • Remember Murphy's Law 10 -18

Closing • Ancaman terhadap kegagalan project • Ancaman terhadap tidak berfungsinya sistem • Ancaman terhadap kriminalitas komputer 10 -19

Diskusikan bersama kelompoknya dan Jawablah sendiri-sendiri 1. Jelaskanlah trend gangguan yang mengancam keamanan sistem komputer saat ini! 2. Jelaskanlah solusi yang dapat digunakan untuk mengatasi ancaman terhadap kegagalan project disetiap tahapnya! 3. Jelaskanlah siapakah yang bertanggung jawab terhadap keamanan sistem dalam perusahaan! ===== thanks 4 your attention ===== 10 -20
 Sks sistem informasi gunadarma
Sks sistem informasi gunadarma Mata kuliah keamanan sistem informasi
Mata kuliah keamanan sistem informasi Materi sistem informasi manajemen semester 4
Materi sistem informasi manajemen semester 4 Mata kuliah manajemen proyek sistem informasi
Mata kuliah manajemen proyek sistem informasi Mata kuliah keamanan sistem informasi
Mata kuliah keamanan sistem informasi Mata kuliah testing dan implementasi sistem
Mata kuliah testing dan implementasi sistem Mata kuliah sistem produksi
Mata kuliah sistem produksi Ocusert adalah
Ocusert adalah Identifikasi blok blok sistem informasi akademik
Identifikasi blok blok sistem informasi akademik Transkrip gunadarma
Transkrip gunadarma Http //siat.ung.ac.id atau http //pmb.ung.ac.id
Http //siat.ung.ac.id atau http //pmb.ung.ac.id Etika profesi mahasiswa
Etika profesi mahasiswa Materi pengembangan diri mahasiswa
Materi pengembangan diri mahasiswa Notasi erd
Notasi erd Mata kuliah ekonomi pembangunan ub
Mata kuliah ekonomi pembangunan ub Mata kuliah pelayanan prima
Mata kuliah pelayanan prima Cara menghitung modal kerja
Cara menghitung modal kerja Silabus mata kuliah metodologi penelitian
Silabus mata kuliah metodologi penelitian Mata kuliah ilmu kelautan unpad
Mata kuliah ilmu kelautan unpad Deskripsi mata kuliah ekonomi mikro
Deskripsi mata kuliah ekonomi mikro Mata kuliah creative writing
Mata kuliah creative writing