MANAGING INFORMATION TECHNOLOGY FIFTH EDITION CHAPTER 13 FACILITATING

















- Slides: 31

MANAGING INFORMATION TECHNOLOGY FIFTH EDITION CHAPTER 13 FACILITATING USER COMPUTING E. Wainright Martin Carol V. Brown Daniel W. De. Hayes Jeffrey A. Hoffer William C. Perkins

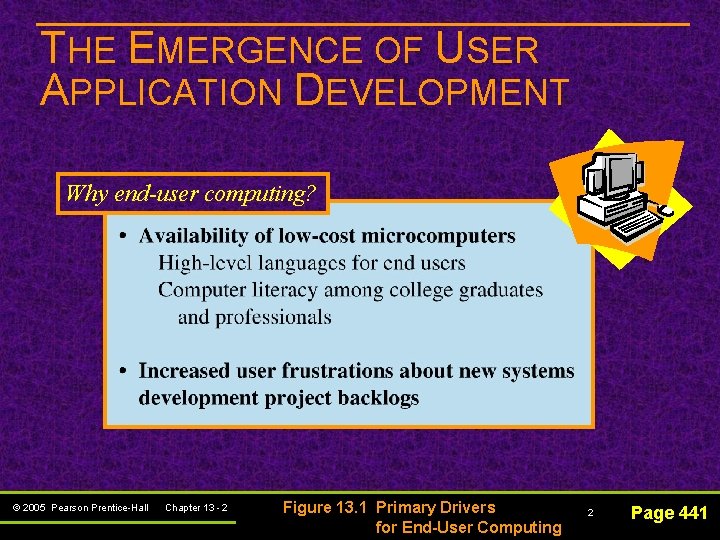
THE EMERGENCE OF USER APPLICATION DEVELOPMENT Why end-user computing? © 2005 Pearson Prentice-Hall Chapter 13 - 2 Figure 13. 1 Primary Drivers for End-User Computing 2 Page 441

THE EMERGENCE OF USER APPLICATION DEVELOPMENT System backlog – the systems development requests by business users that members of the IS organization are not currently working on © 2005 Pearson Prentice-Hall Chapter 13 - 3 3 Page 442

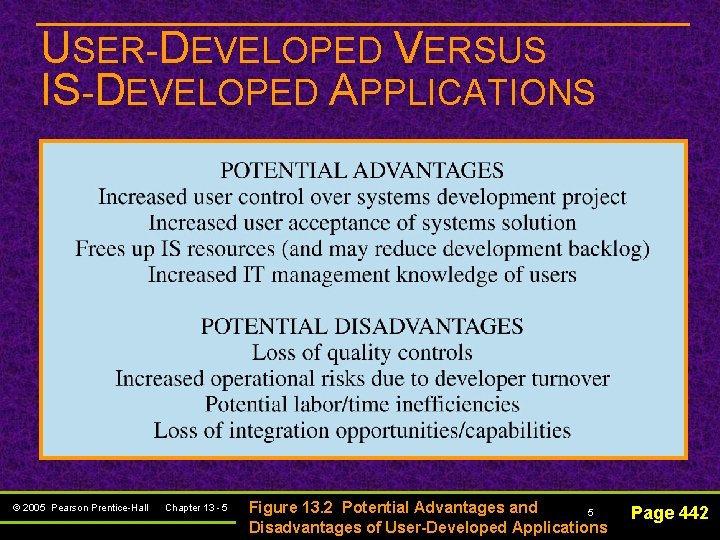
USER-DEVELOPED VERSUS IS-DEVELOPED APPLICATIONS n How should you decide? Understanding the potential advantages and disadvantages of each © 2005 Pearson Prentice-Hall Chapter 13 - 4 4 Page 442

USER-DEVELOPED VERSUS IS-DEVELOPED APPLICATIONS © 2005 Pearson Prentice-Hall Chapter 13 - 5 Figure 13. 2 Potential Advantages and 5 Disadvantages of User-Developed Applications Page 442

USER DEVELOPMENT METHODOLOGY Assessing the Application Risks © 2005 Pearson Prentice-Hall Chapter 13 - 6 Factors to consider Figure 13. 3 Application, Tool, and Developer Characteristics 6 Page 445

USER-DEVELOPED VERSUS IS-DEVELOPED APPLICATIONS Application Characteristics n Categories of application scope that have different risk levels: Personal applications developed and used by the primary user for personal decision making Departmental applications developed by single user but operated and used by multiple users in a department Organizational applications used by multiple users across a number of departments © 2005 Pearson Prentice-Hall Chapter 13 - 7 7 Page 445

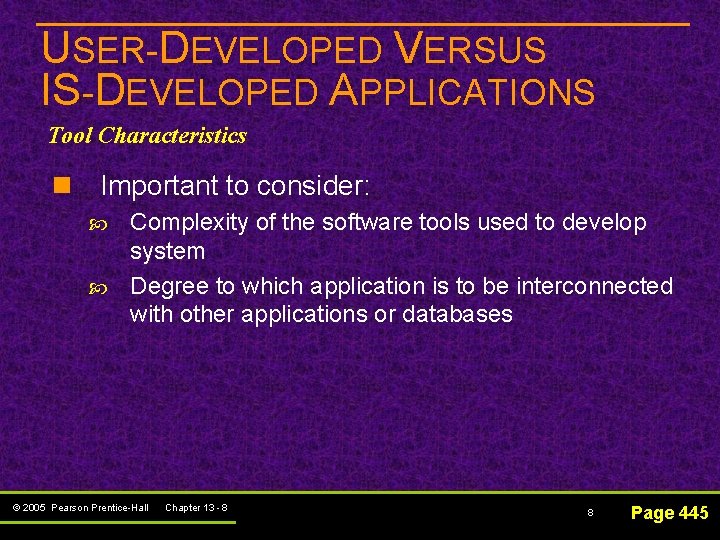
USER-DEVELOPED VERSUS IS-DEVELOPED APPLICATIONS Tool Characteristics n Important to consider: Complexity of the software tools used to develop system Degree to which application is to be interconnected with other applications or databases © 2005 Pearson Prentice-Hall Chapter 13 - 8 8 Page 445

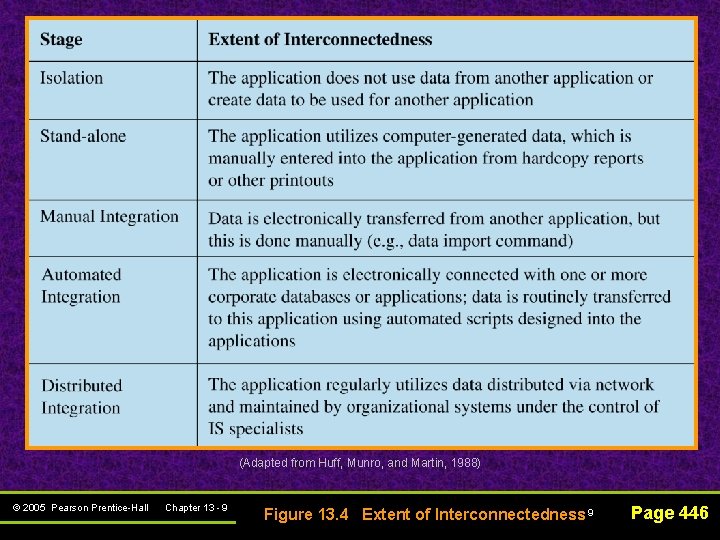
(Adapted from Huff, Munro, and Martin, 1988) © 2005 Pearson Prentice-Hall Chapter 13 - 9 Figure 13. 4 Extent of Interconnectedness 9 Page 446

USER-DEVELOPED VERSUS IS-DEVELOPED APPLICATIONS Developer Characteristics n Important to consider: Relevant skills and experience of potential developers Developers availability to work on project Availability of developer resources in relation to time constraints faced by users © 2005 Pearson Prentice-Hall Chapter 13 - 10 10 Page 446

USER DEVELOPMENT METHODOLOGY Guidelines for Choosing (Based on Panko, 1989) © 2005 Pearson Prentice-Hall Chapter 13 - 11 Figure 13. 5 Guidelines for Choosing the Development Approach 11 Page 447

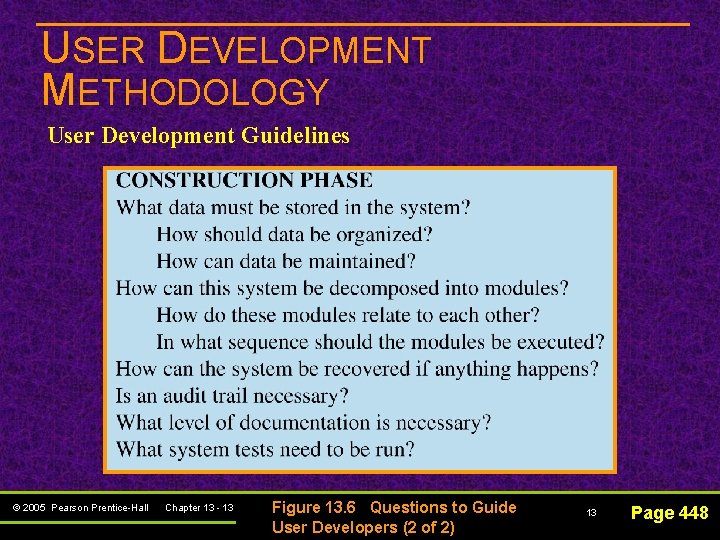
USER DEVELOPMENT METHODOLOGY User Development Guidelines © 2005 Pearson Prentice-Hall Chapter 13 - 12 Figure 13. 6 Questions to Guide User Developers (1 of 2) 12 Page 448

USER DEVELOPMENT METHODOLOGY User Development Guidelines © 2005 Pearson Prentice-Hall Chapter 13 - 13 Figure 13. 6 Questions to Guide User Developers (2 of 2) 13 Page 448

USER DEVELOPMENT METHODOLOGY User Development Guidelines n Also to be considered: Data recovery needs Documentation Testing process Automatic audit features Separate audit programs (especially for spreadsheets) © 2005 Pearson Prentice-Hall Chapter 13 - 14 14 Page 448

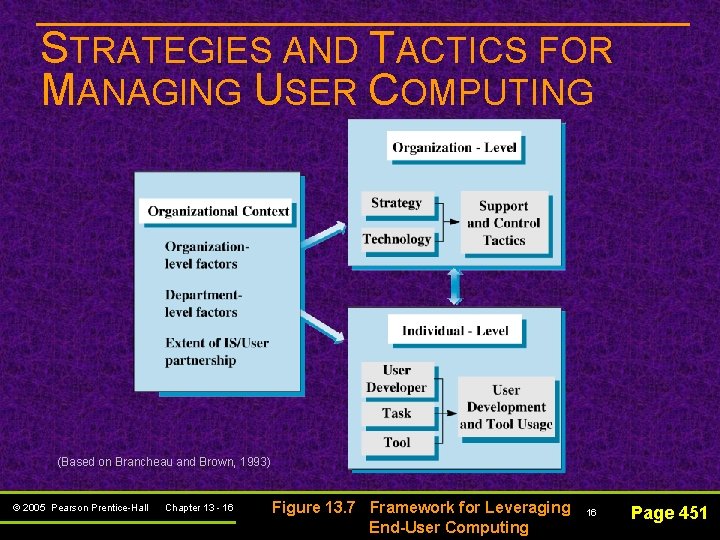
STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING n Responsibility of IS and business managers: Strategy The strategic objectives and overall approach to end-user computing Technology user tools Tactics for Support and Control control policies and procedures © 2005 Pearson Prentice-Hall Chapter 13 - 15 The range and accessibility of end. Support services, 15 Page 451

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING (Based on Brancheau and Brown, 1993) © 2005 Pearson Prentice-Hall Chapter 13 - 16 Figure 13. 7 Framework for Leveraging End-User Computing 16 Page 451

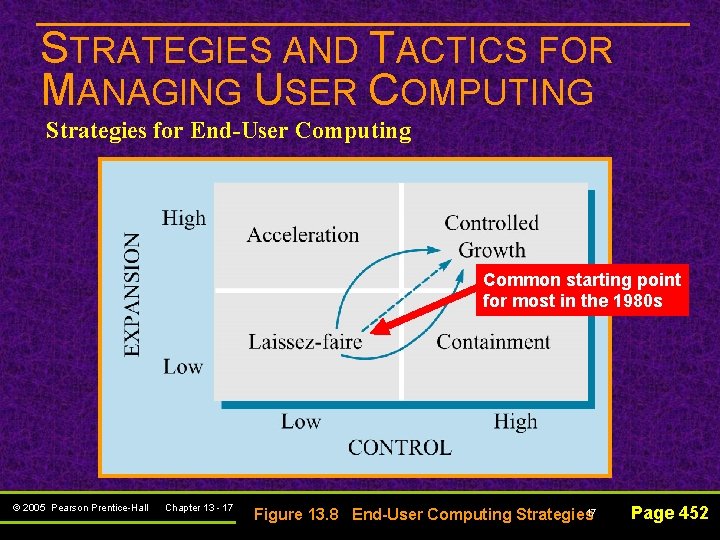
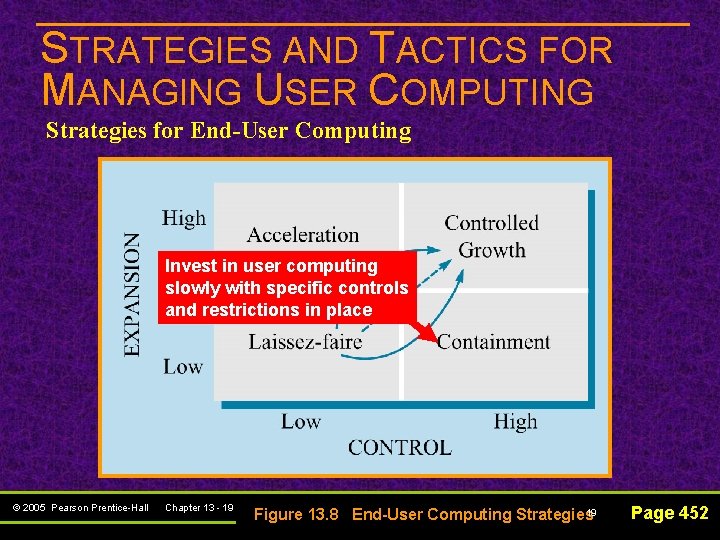
STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Strategies for End-User Computing Common starting point for most in the 1980 s © 2005 Pearson Prentice-Hall Chapter 13 - 17 17 Figure 13. 8 End-User Computing Strategies Page 452

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Strategies for End-User Computing Invest heavily in end-user computing but little formal controls © 2005 Pearson Prentice-Hall Chapter 13 - 18 18 Figure 13. 8 End-User Computing Strategies Page 452

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Strategies for End-User Computing Invest in user computing slowly with specific controls and restrictions in place © 2005 Pearson Prentice-Hall Chapter 13 - 19 19 Figure 13. 8 End-User Computing Strategies Page 452

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Strategies for End-User Computing Most mature approach – Start with small investments and few controls, then increase both over time © 2005 Pearson Prentice-Hall Chapter 13 - 20 20 Figure 13. 8 End-User Computing Strategies Page 452

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Centralized Support (Information Center) Approaches Information center (IC) – a centralized support unit for managing end-user computing activities that typically began in 1980 s © 2005 Pearson Prentice-Hall Chapter 13 - 21 21 Page 452

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING IS/Business Partnering Approaches n Managed free economy approach: Less centralized approach to supporting users Has five components: ü ü Explicit strategy reflecting a support and control philosophy User/IS working partnership End-user support unit well integrated with other IS units Emphasis on end-user education of IS development methods and quality controls ü Targeting of critical end-user applications © 2005 Pearson Prentice-Hall Chapter 13 - 22 22 Page 454

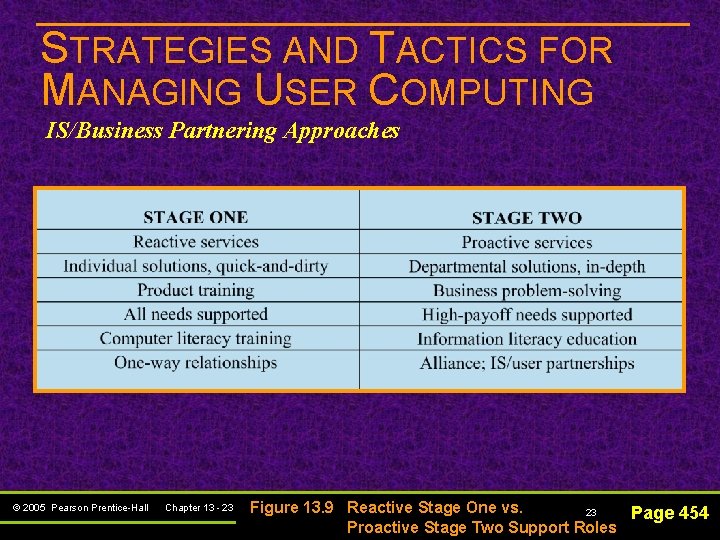
STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING IS/Business Partnering Approaches © 2005 Pearson Prentice-Hall Chapter 13 - 23 Figure 13. 9 Reactive Stage One vs. 23 Page 454 Proactive Stage Two Support Roles

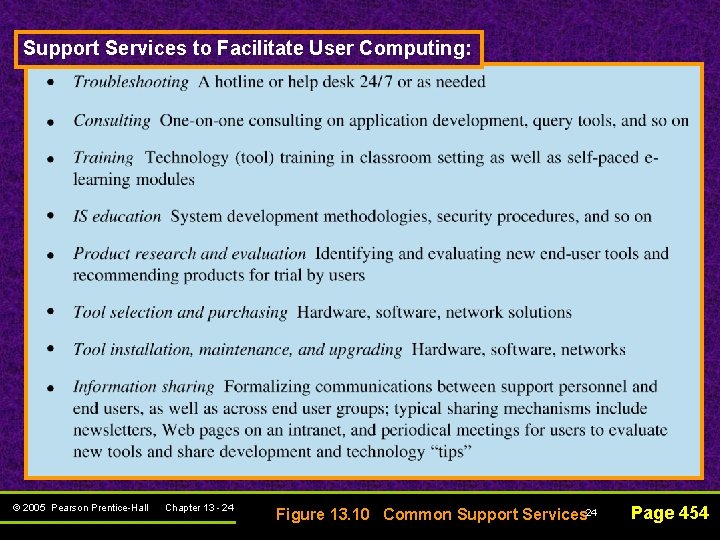
Support Services to Facilitate User Computing: © 2005 Pearson Prentice-Hall Chapter 13 - 24 Figure 13. 10 Common Support Services 24 Page 454

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Common Support Tactics n Supporting end users also involves: Preparing them for new software releases Retraining Refitting end-user workstations © 2005 Pearson Prentice-Hall Chapter 13 - 25 25 Page 454

Common Control Tactics Sample © 2005 Pearson Prentice-Hall Chapter 13 - 26 Policie s and P rocedu res 26 Figure 13. 11 Common Policies and Procedures Page 456

STRATEGIES AND TACTICS FOR MANAGING USER COMPUTING Common Control Tactics n Other control issues include: Use of peer-to-peer or file-sharing applications ü Can slow down internal networks ü Create major security problems Blocking unwanted e-mail © 2005 Pearson Prentice-Hall Chapter 13 - 27 27 Page 456

SPECIAL CASE: SUPPORTING TELECOMMUTERS Telecommuter – a worker who spends at least a part of his or her regular business hours using IT to perform job outside of a company’s physical facility, using a mobile office, an office in personal home, or at a temporary office at a shared work center away from the company’s main office © 2005 Pearson Prentice-Hall Chapter 13 - 28 28 Page 457

SPECIAL CASE: SUPPORTING TELECOMMUTERS n Personal benefits to telecommuters: More productive Increased workday flexibility Improved work/life balance Easier accommodation of communications across time zones © 2005 Pearson Prentice-Hall Chapter 13 - 29 29 Page 458

SPECIAL CASE: SUPPORTING TELECOMMUTERS n Barriers to telecommuting: Initial investment costs for technology Need for support during off hours Business redesign required to make work Performance appraisal systems need changes Employee isolation Security and legal issues © 2005 Pearson Prentice-Hall Chapter 13 - 30 Page 458 -459 30

SPECIAL CASE: SUPPORTING TELECOMMUTERS (Based on Kostner, 1996) © 2005 Pearson Prentice-Hall Chapter 13 - 31 Figure 13. 12 Six Leadership Secrets 31 for Managing Remote Workers Page 459