Lecture 5 DES Use and Analysis CS 588







![Differential Cryptanalysis • [Biham & Shamir, 1990] • Choose plaintext pairs with fixed difference: Differential Cryptanalysis • [Biham & Shamir, 1990] • Choose plaintext pairs with fixed difference:](https://slidetodoc.com/presentation_image_h/071d28de7baed73f4479233c53a0aa96/image-25.jpg)





- Slides: 40

Lecture 5: DES Use and Analysis CS 588: Security and Privacy David Evans University of Virginia 12 Sept 2001 University of Virginia CS 588 http: //www. cs. virginia. edu/~evans Computer Science

Menu • • • Today’s manifest: on line only DES Review Modes of Operation 3 DES Attacks • Return PS 1 12 Sept 2001 University of Virginia CS 588 2

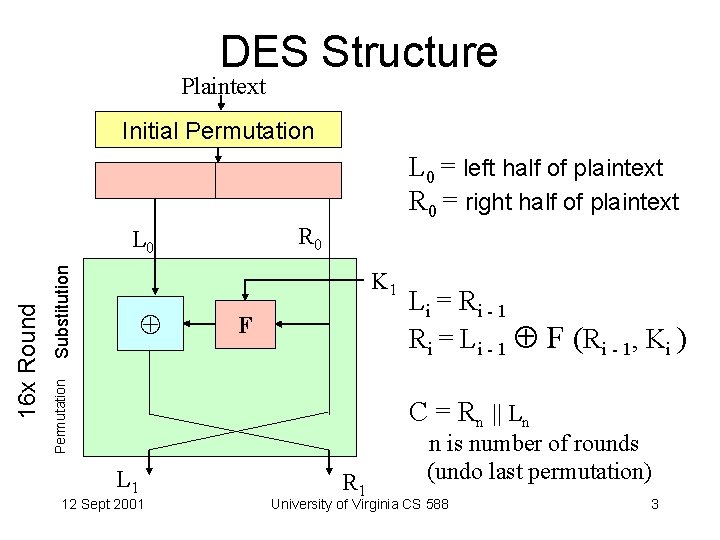
DES Structure Plaintext Initial Permutation L 0 = left half of plaintext R 0 = right half of plaintext R 0 Substitution K 1 F Permutation 16 x Round L 0 Li = Ri - 1 R i = L i - 1 F ( R i - 1, K i ) C = Rn || Ln L 1 12 Sept 2001 R 1 n is number of rounds (undo last permutation) University of Virginia CS 588 3

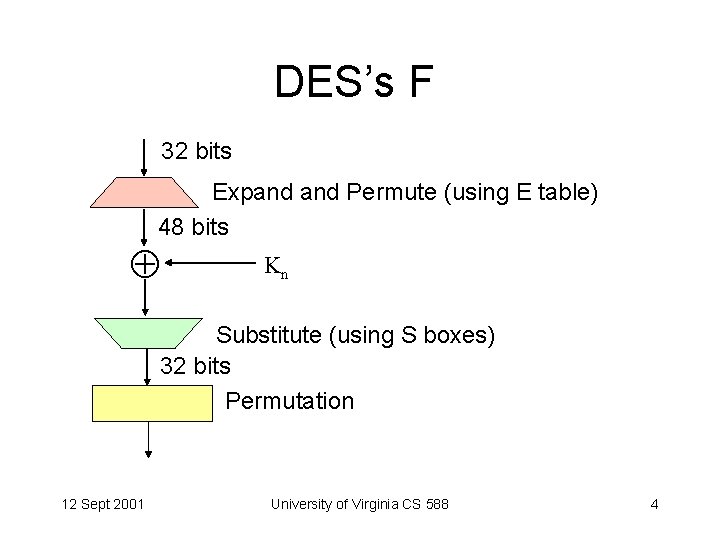
DES’s F 32 bits Expand Permute (using E table) 48 bits Kn Substitute (using S boxes) 32 bits Permutation 12 Sept 2001 University of Virginia CS 588 4

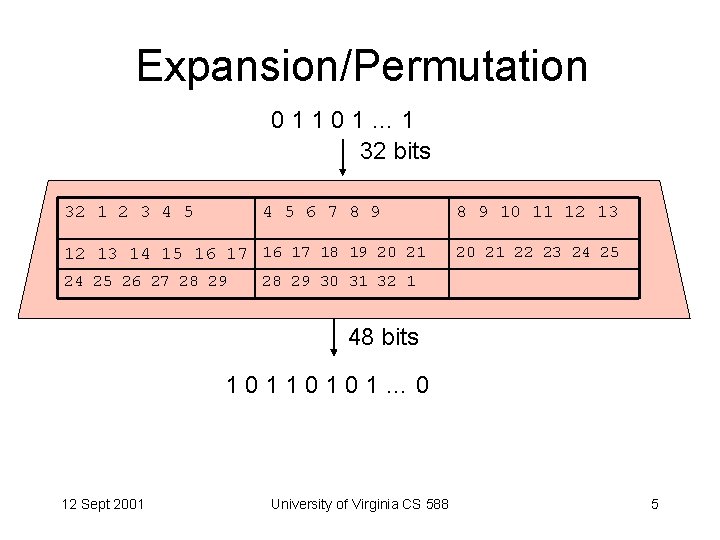
Expansion/Permutation 01101… 1 32 bits 32 1 2 3 4 5 6 7 8 9 12 13 14 15 16 17 18 19 20 21 24 25 26 27 28 29 8 9 10 11 12 13 20 21 22 23 24 25 28 29 30 31 32 1 48 bits 10110101… 0 12 Sept 2001 University of Virginia CS 588 5

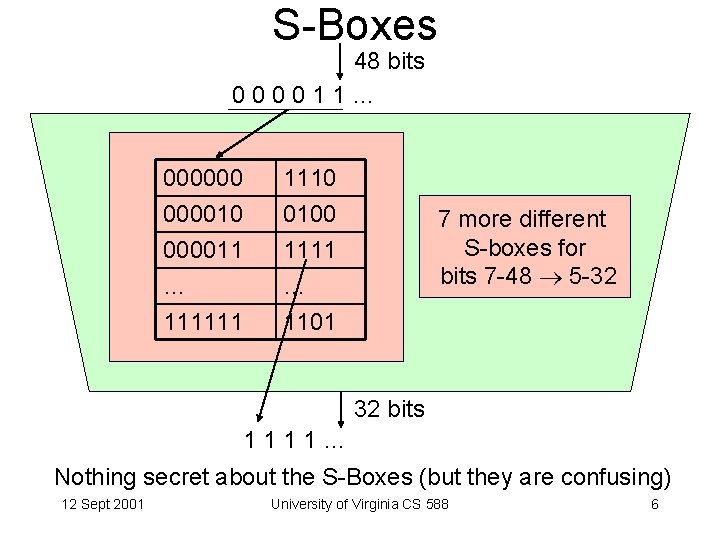
S-Boxes 48 bits 000011… 00000011 … 1110 0100 1111 … 111111 1101 7 more different S-boxes for bits 7 -48 5 -32 32 bits 1111… Nothing secret about the S-Boxes (but they are confusing) 12 Sept 2001 University of Virginia CS 588 6

Modes of Operation 12 Sept 2001 University of Virginia CS 588 7

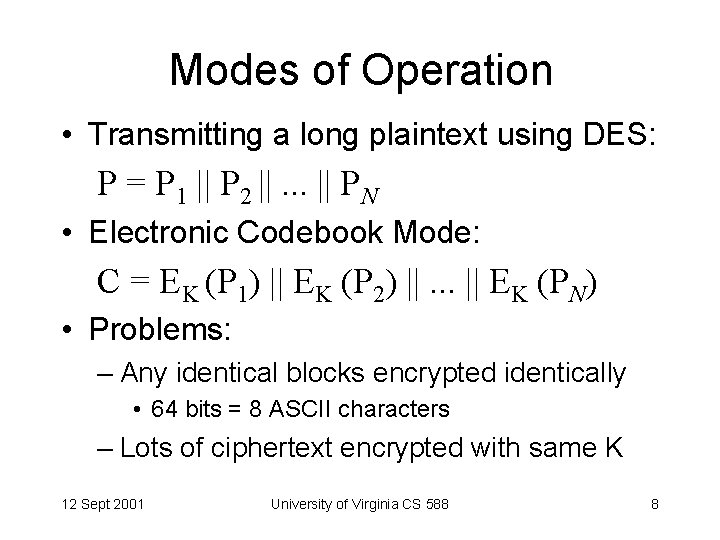
Modes of Operation • Transmitting a long plaintext using DES: P = P 1 || P 2 ||. . . || PN • Electronic Codebook Mode: C = EK (P 1) || EK (P 2) ||. . . || EK (PN) • Problems: – Any identical blocks encrypted identically • 64 bits = 8 ASCII characters – Lots of ciphertext encrypted with same K 12 Sept 2001 University of Virginia CS 588 8

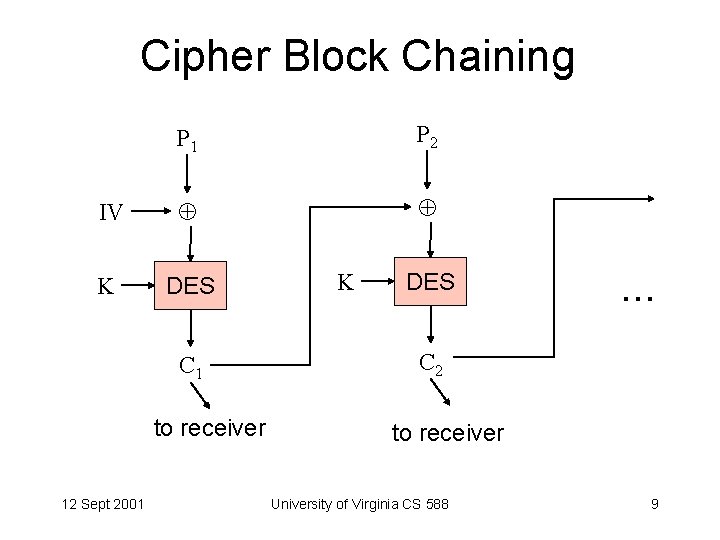
Cipher Block Chaining P 1 P 2 IV K DES C 1 to receiver 12 Sept 2001 K DES . . . C 2 to receiver University of Virginia CS 588 9

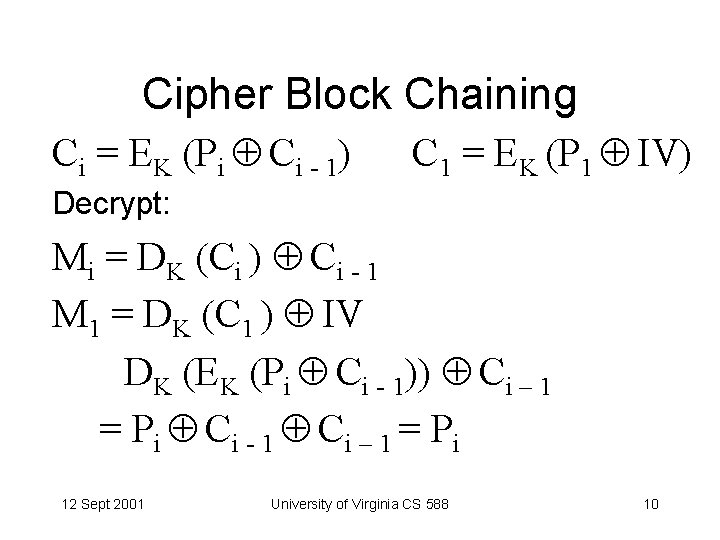
Cipher Block Chaining Ci = EK (Pi Ci - 1) C 1 = EK (P 1 IV) Decrypt: Mi = DK (Ci ) Ci - 1 M 1 = DK (C 1 ) IV DK (EK (Pi Ci - 1)) Ci – 1 = Pi Ci - 1 Ci – 1 = Pi 12 Sept 2001 University of Virginia CS 588 10

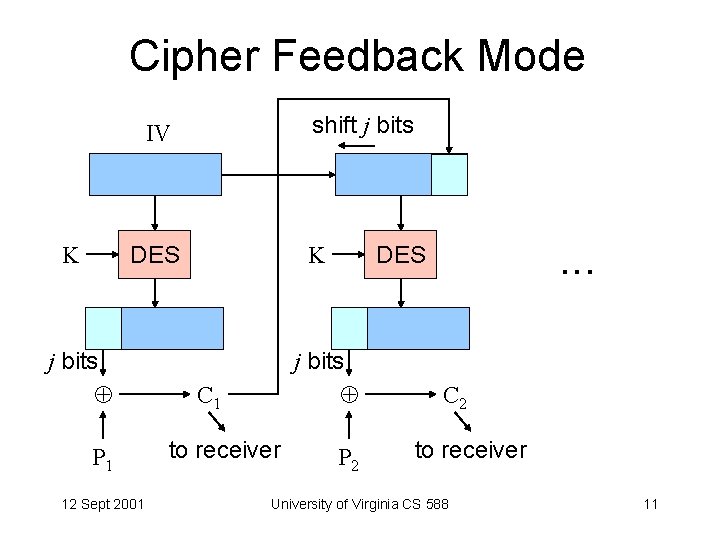
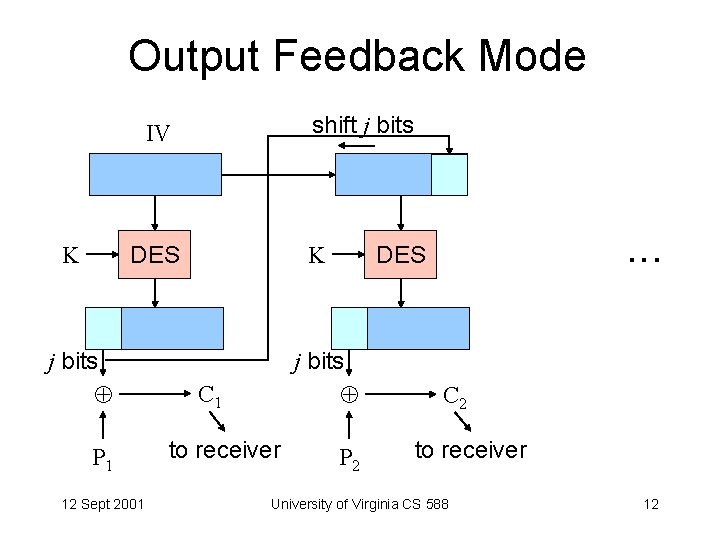
Cipher Feedback Mode shift j bits IV K K DES j bits P 1 12 Sept 2001 j bits C 1 to receiver . . . DES P 2 C 2 to receiver University of Virginia CS 588 11

Output Feedback Mode shift j bits IV K K DES j bits P 1 12 Sept 2001 j bits C 1 to receiver . . . DES P 2 C 2 to receiver University of Virginia CS 588 12

Cipher/Output Feedback • 1 -bit transmission error • Active eavesdropper • Performance 12 Sept 2001 University of Virginia CS 588 13

Multiple Encryption 12 Sept 2001 University of Virginia CS 588 14

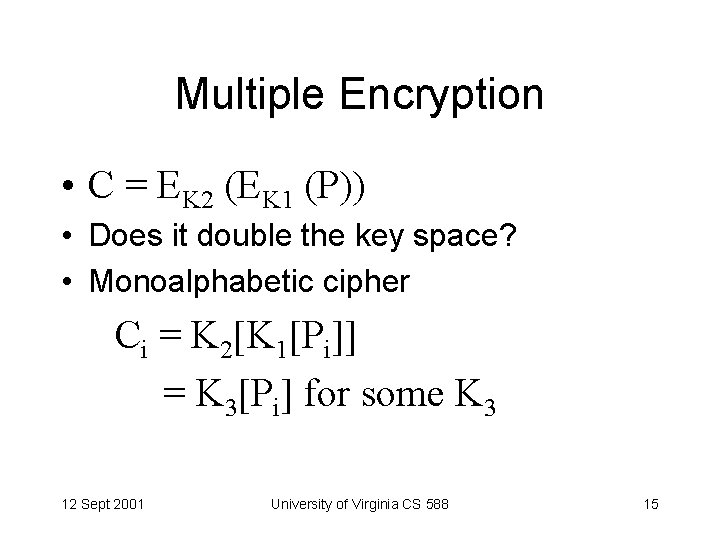
Multiple Encryption • C = EK 2 (EK 1 (P)) • Does it double the key space? • Monoalphabetic cipher Ci = K 2[K 1[Pi]] = K 3[Pi] for some K 3 12 Sept 2001 University of Virginia CS 588 15

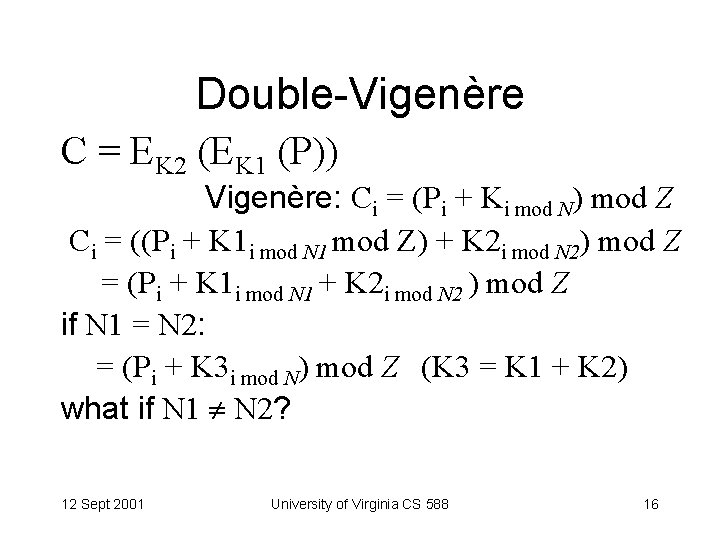
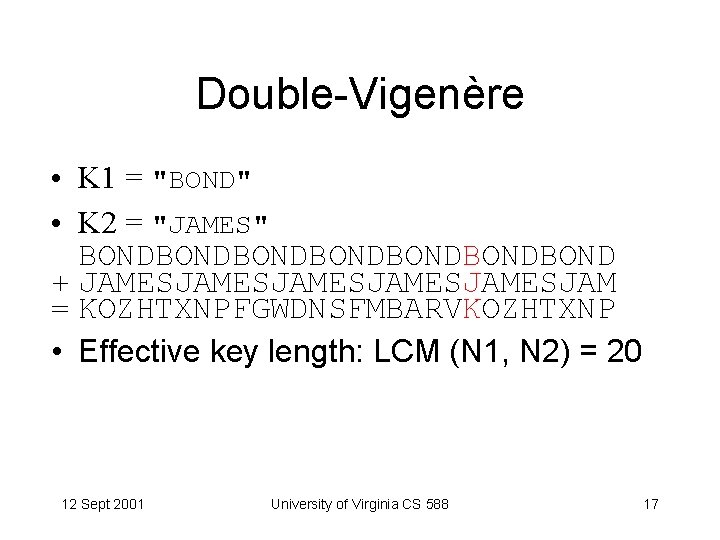
Double-Vigenère C = EK 2 (EK 1 (P)) Vigenère: Ci = (Pi + Ki mod N) mod Z Ci = ((Pi + K 1 i mod N 1 mod Z) + K 2 i mod N 2) mod Z = (Pi + K 1 i mod N 1 + K 2 i mod N 2 ) mod Z if N 1 = N 2: = (Pi + K 3 i mod N) mod Z (K 3 = K 1 + K 2) what if N 1 N 2? 12 Sept 2001 University of Virginia CS 588 16

Double-Vigenère • K 1 = "BOND" • K 2 = "JAMES" BONDBONDBONDBOND + JAMESJAMESJAMESJAM = KOZHTXNPFGWDNSFMBARVKOZHTXNP • Effective key length: LCM (N 1, N 2) = 20 12 Sept 2001 University of Virginia CS 588 17

Double DES • C = EK 2 (EK 1 (P)) • Is there a K 3 such that C = EK 3 (P)? – There are 256 keys, and 264! mappings – If DES is good, keys map randomly to mappings. – Probability that a randomly chosen mapping corresponds to a DES key: 256 / 264! << 1 / 263! • Effective key size of Double DES? = 256 * 256 = 2112 WRONG! 12 Sept 2001 University of Virginia CS 588 18

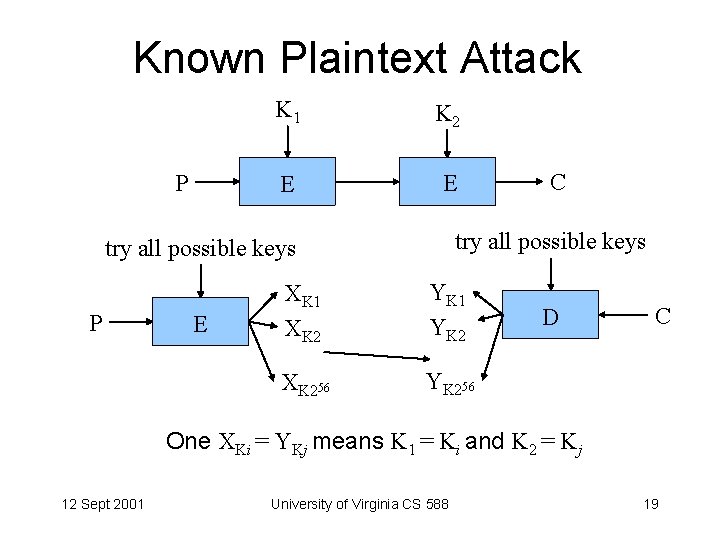
Known Plaintext Attack P K 1 K 2 E E try all possible keys P E C XK 1 XK 2 YK 1 YK 2 XK 256 YK 256 D C One XKi = YKj means K 1 = Ki and K 2 = Kj 12 Sept 2001 University of Virginia CS 588 19

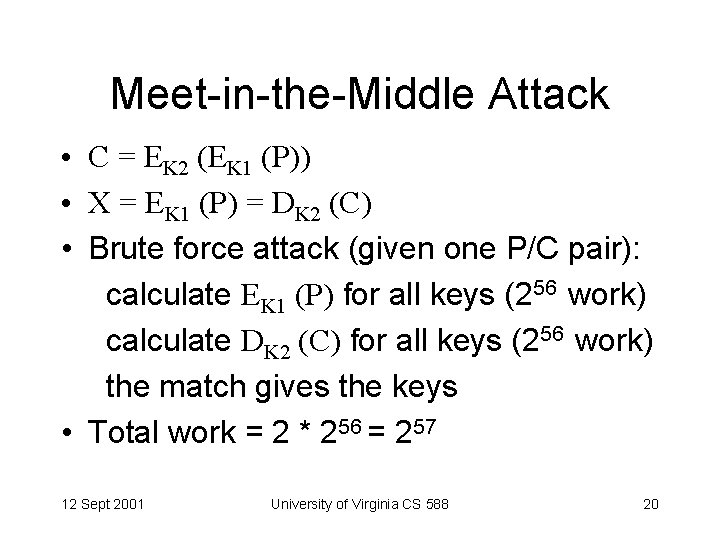
Meet-in-the-Middle Attack • C = EK 2 (EK 1 (P)) • X = EK 1 (P) = DK 2 (C) • Brute force attack (given one P/C pair): calculate EK 1 (P) for all keys (256 work) calculate DK 2 (C) for all keys (256 work) the match gives the keys • Total work = 2 * 256 = 257 12 Sept 2001 University of Virginia CS 588 20

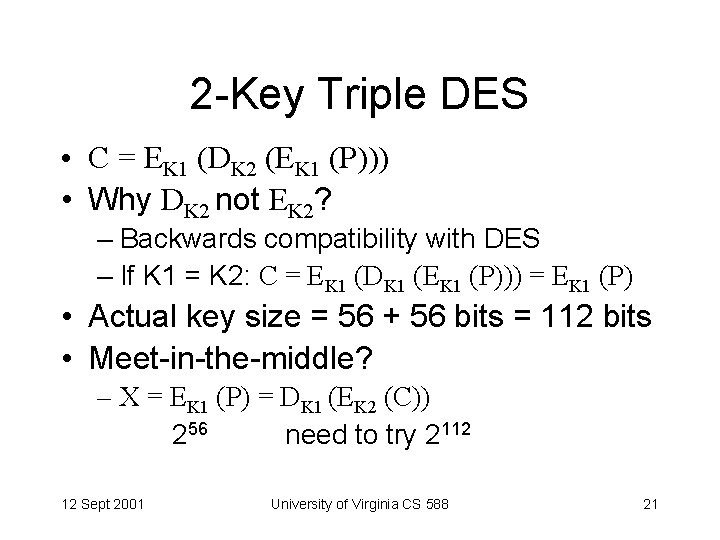
2 -Key Triple DES • C = EK 1 (DK 2 (EK 1 (P))) • Why DK 2 not EK 2? – Backwards compatibility with DES – If K 1 = K 2: C = EK 1 (DK 1 (EK 1 (P))) = EK 1 (P) • Actual key size = 56 + 56 bits = 112 bits • Meet-in-the-middle? – X = EK 1 (P) = DK 1 (EK 2 (C)) 256 need to try 2112 12 Sept 2001 University of Virginia CS 588 21

How secure is Triple-DES • Brute force search: 2112 keys – Best DES attack: 245 B keys/second – 6. 7 * 1014 years (compared to 22 hours) – 1011 years = total lifetime of universe (closed universe theory) • Best known attack - reduces to 2120 -log 2 n – n = number of known P-C pairs – n = 264, work is 256 Realistic? 12 Sept 2001 University of Virginia CS 588 22

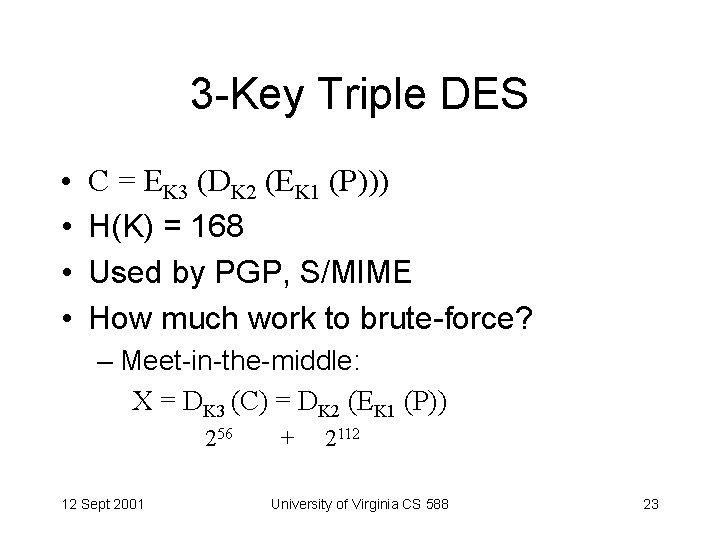
3 -Key Triple DES • • C = EK 3 (DK 2 (EK 1 (P))) H(K) = 168 Used by PGP, S/MIME How much work to brute-force? – Meet-in-the-middle: X = DK 3 (C) = DK 2 (EK 1 (P)) 256 12 Sept 2001 + 2112 University of Virginia CS 588 23

DES Attacks • Last time: brute force – Best result: 22 hours – But no where near good enough for 3 DES • Differential Cryptanalysis • Power Cryptanalysis 12 Sept 2001 University of Virginia CS 588 24
![Differential Cryptanalysis Biham Shamir 1990 Choose plaintext pairs with fixed difference Differential Cryptanalysis • [Biham & Shamir, 1990] • Choose plaintext pairs with fixed difference:](https://slidetodoc.com/presentation_image_h/071d28de7baed73f4479233c53a0aa96/image-25.jpg)
Differential Cryptanalysis • [Biham & Shamir, 1990] • Choose plaintext pairs with fixed difference: X = X X’ • Use differences in resulting ciphertext to guess key probabilities • With enough work (247) and enough chosen plaintexts (247) can find key (compared to 256 brute force work) Takes 3 years of 1. 5 Mbps encrypting chosen plaintext! 12 Sept 2001 University of Virginia CS 588 25

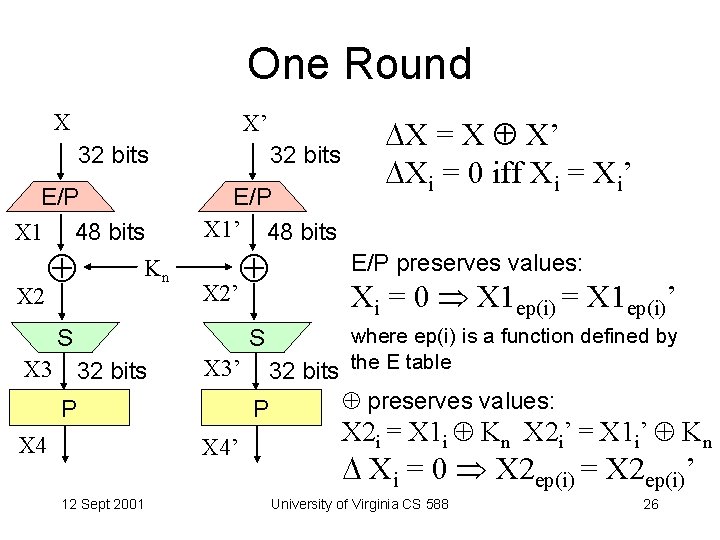
One Round X X’ 32 bits E/P X 1 48 bits Kn X 2 32 bits E/P X 1’ 48 bits X 2’ S S X 3 32 bits X 3’ P X 4 12 Sept 2001 E/P preserves values: Xi = 0 X 1 ep(i) = X 1 ep(i)’ where ep(i) is a function defined by 32 bits the E table P X 4’ X = X X’ Xi = 0 iff Xi = Xi’ preserves values: X 2 i = X 1 i Kn X 2 i’ = X 1 i’ Kn Xi = 0 X 2 ep(i) = X 2 ep(i)’ University of Virginia CS 588 26

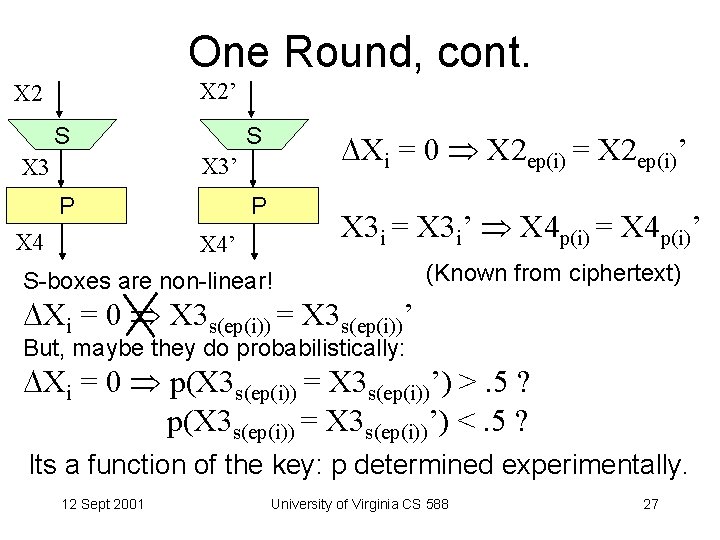
One Round, cont. X 2’ X 2 S S Xi = 0 X 2 ep(i) = X 2 ep(i)’ X 3 P X 4 P X 3 i = X 3 i’ X 4 p(i) = X 4 p(i)’ X 4’ S-boxes are non-linear! (Known from ciphertext) Xi = 0 X 3 s(ep(i)) = X 3 s(ep(i))’ But, maybe they do probabilistically: Xi = 0 p(X 3 s(ep(i)) = X 3 s(ep(i))’) >. 5 ? p(X 3 s(ep(i)) = X 3 s(ep(i))’) <. 5 ? Its a function of the key: p determined experimentally. 12 Sept 2001 University of Virginia CS 588 27

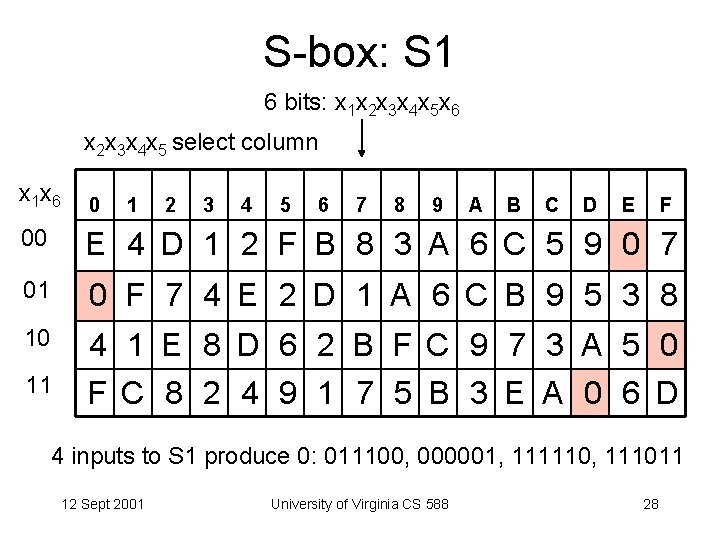
S-box: S 1 6 bits: x 1 x 2 x 3 x 4 x 5 x 6 x 2 x 3 x 4 x 5 select column x 1 x 6 0 1 2 3 4 5 6 7 8 9 A B C D E F 00 E 4 D 1 2 F B 8 3 A 6 C 5 9 0 7 01 0 F 7 4 E 2 D 1 A 6 C B 9 5 3 8 10 4 1 E 8 D 6 2 B F C 9 7 3 A 5 0 F C 8 2 4 9 1 7 5 B 3 E A 0 6 D 11 4 inputs to S 1 produce 0: 011100, 000001, 111110, 111011 12 Sept 2001 University of Virginia CS 588 28

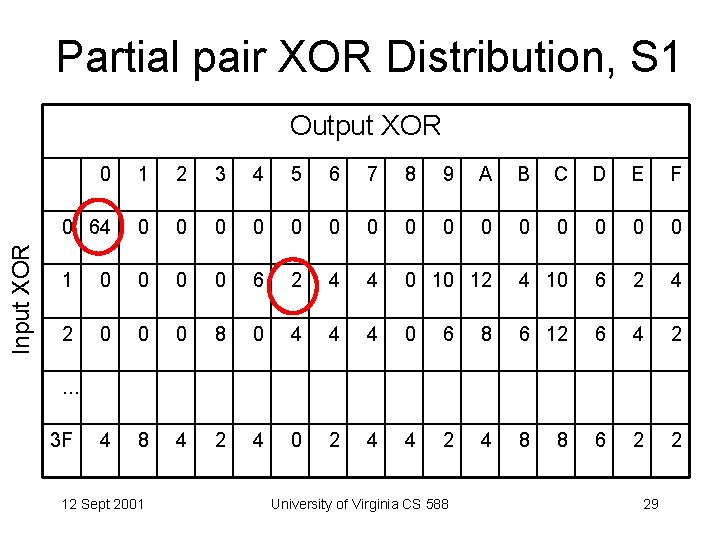
Partial pair XOR Distribution, S 1 Input XOR Output XOR 0 1 2 3 4 5 6 7 8 9 A B C D E F 0 64 0 0 0 0 1 0 0 6 2 4 4 0 10 12 4 10 6 2 4 2 0 0 0 8 0 4 4 4 0 6 8 6 12 6 4 2 4 8 4 2 4 0 2 4 4 2 4 8 6 2 2 . . . 3 F 12 Sept 2001 University of Virginia CS 588 8 29

S-box: S 1 00 01 10 11 0 1 2 3 4 5 6 7 8 9 A B C D E F E 0 4 F 1 C D 7 E 8 1 4 8 2 2 E D 4 F 2 6 9 B D 2 1 8 1 B 7 3 A F 5 A 6 C B 6 C 9 3 C B 7 E 5 9 3 A 9 5 A 0 0 3 5 6 7 8 0 D Difference in last input bit difference in output bits 0101 0001 + 0101 = 0100 (1 XOR 5 = 1) 1011 + 0101 = 1110 (B XOR 5 = E) 12 Sept 2001 University of Virginia CS 588 30

Differential Cryptanalysis • Propagate experimental probabilities for 1 round through 16 rounds • After enough P-C pairs, one key becomes most probable • Difficulty depends heavily on S-Box choices • First published in 1990, but NSA knew about it in 1973! 12 Sept 2001 University of Virginia CS 588 31

Differential Cryptanalysis • “Successful” on DES up to 15 rounds (better than exhaustive search) • By 16 th round, characteristics probabilities are 2 -56 • Very successful on DES variants (breaks GDES with 6 chosen plaintexts) • Very successful on FEAL (FEAL-4, FEAL-8, FEAL-NX, . . . ) 12 Sept 2001 University of Virginia CS 588 32

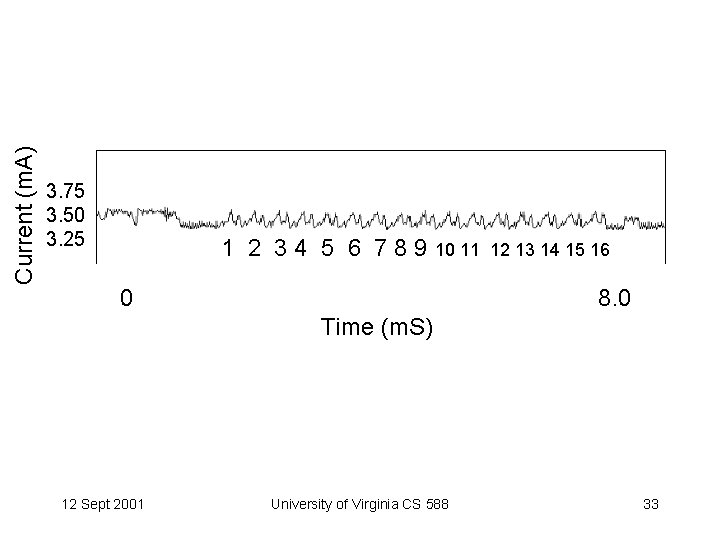
Current (m. A) 3. 75 3. 50 3. 25 1 2 3 4 5 6 7 8 9 10 11 0 12 13 14 15 16 8. 0 Time (m. S) 12 Sept 2001 University of Virginia CS 588 33

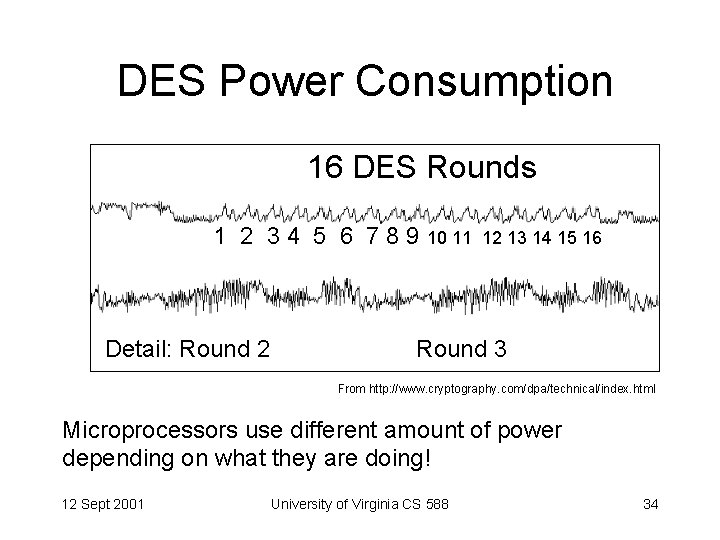
DES Power Consumption 16 DES Rounds 1 2 3 4 5 6 7 8 9 10 11 Detail: Round 2 12 13 14 15 16 Round 3 From http: //www. cryptography. com/dpa/technical/index. html Microprocessors use different amount of power depending on what they are doing! 12 Sept 2001 University of Virginia CS 588 34

Power Analysis Scenario • Attacker has physical device that encrypts and decrypts using a secret key • Is this realistic? Smart Cards (Mondex) 12 Sept 2001 University of Virginia CS 588 35

Side Channel Cryptanalysis • Regular Cryptanalysis: mathematical – Attacker sees inputs, outputs • Side Channel Cryptanalysis – Attacker sees something else: power consumption, encryption/decryption time, radiation, etc. • Depends on implementation of algorithm 12 Sept 2001 University of Virginia CS 588 36

Measuring Power Consumption • Add a resistor between power source and device, measure voltage across resistor I = V/R • Can sample at over 1 GHz with < 1% error 12 Sept 2001 University of Virginia CS 588 37

Power Use Reveals Key • Current for a left shift depends on leftmost bit: – if 1, need to set rightmost bit after • DES key schedule uses shifts, can tell bits in key! • Current for XOR may depend on number of switches 12 Sept 2001 University of Virginia CS 588 38

Defenses • Reduce signal – Physical shielding, microprocessor design (make all shifts use same power, etc. ) • Introduce random noise – Change execution order, do random computation, etc. • Design cryptosystems with DPA in mind – Nonlinear key updates between transactions 12 Sept 2001 University of Virginia CS 588 39

Charge • Continue thinking about project ideas – Each project group should send me email or talk to me by next week about what you are considering • Next time: modern block ciphers – Read AES papers before next class 12 Sept 2001 University of Virginia CS 588 40