ITP 457 Network Security Joseph Greenfield joseph greenfieldusc



















- Slides: 25

ITP 457 Network Security Joseph Greenfield joseph. greenfield@usc. edu

Overview l l l Introduction Syllabus What are your expectations? Questions? Current affairs with Network Security Introduction to Network Security

Student Introductions l l l Name Major Experience with Linux / Windows

My expectations l Pre-requisites l l Basic Knowledge of Computers No networking experience required !!! l l Ideally you should have taken or be currently enrolled in ITP 325 – Web Security l l We are working to remove all of the overlap between the two My expectations l l Show up to class At the end of the semester, I expect you to have a good understanding of the basic principles of network security l l We will teach you everything you need to know I don’t expect you to be experts, and I will not grade you as if you are an expert Guest Lectures l We are hoping to have two guest lecturers this semester. Attendance is absolutely mandatory. An absence from either lecture will result in a grade penalty of one-third (i. e. a B+ will be lowered to a B)

Brief History of the World

Course Philosophy “The most important step towards securing your network Is trying to break into it. ” Attacks vs. Countermeasures

Course Outline l Computer Networking Fundamentals l l Hackers l l l Networking technologies, products, methodologies Mentality and Mindset Methodology Network Node Security l Windows XP, 2000, and 2003 l l l Linux/Unix Network Security Perimeter Security l l Vista will NOT be covered Firewalls Intrusion Detection Systems Router Security Wireless Network Security Policy

Hacking Today l Congressional Aide is caught trying to solicit hackers for hire(12/22/06): l l http: //www. securityfocus. com/brief/391 UCLA breach exposes 800, 000 individual’s personal information l http: //www. securityfocus. com/brief/391

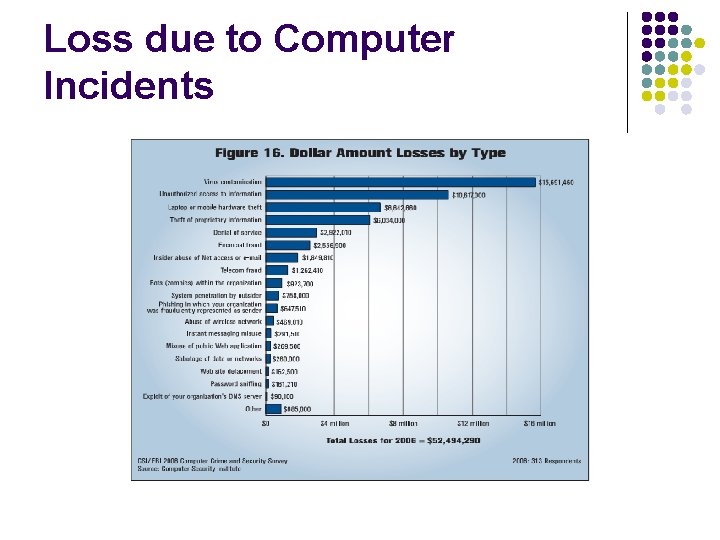
Loss due to Computer Incidents

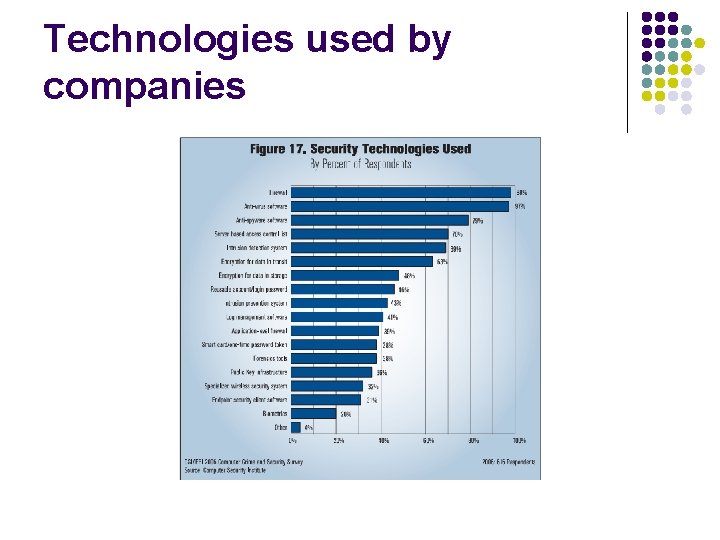
Technologies used by companies

Overview l l l What is Security? Why do we need Security Who is vulnerable?

What is Security? l Dictionary. com says: l l l 1. Freedom from risk or danger; safety. 2. Freedom from doubt, anxiety, or fear; confidence. 3. Something that gives or assures safety, as: l 1. A group or department of private guards: Call building security if a visitor acts suspicious. l 2. Measures adopted by a government to prevent espionage, sabotage, or attack. l 3. Measures adopted, as by a business or homeowner, to prevent a crime such as burglary or assault: Security was lax at the firm's smaller plant.

Why do we need Security l Protect vital information while still allowing access to those who need it l l l Trade secrets, medical records, etc. Provide authentication and access control for resources Guarantee availability of resources l Ex: 5 9’s (99. 999% reliability)

Who is vulnerable? l l l l Financial institutions and banks Internet service providers Pharmaceutical companies Government and defense agencies Contractors to various government agencies Multinational corporations Educational Institutions Basically ANYONE ON A NETWORK

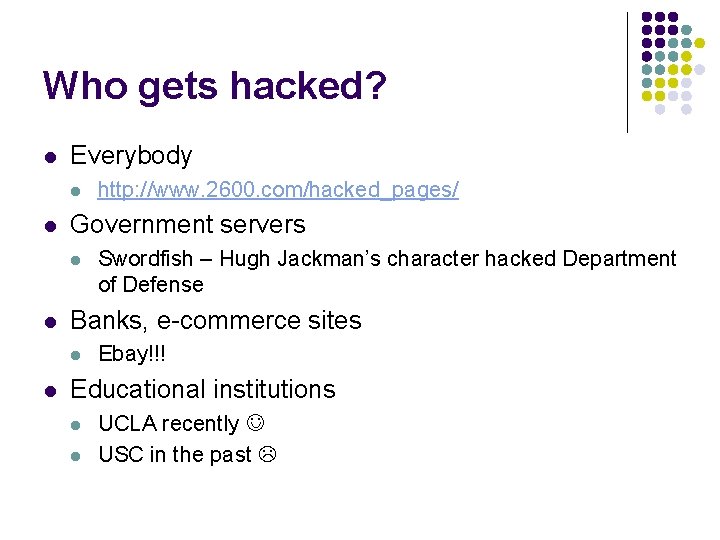
Who gets hacked? l Everybody l l Government servers l l Swordfish – Hugh Jackman’s character hacked Department of Defense Banks, e-commerce sites l l http: //www. 2600. com/hacked_pages/ Ebay!!! Educational institutions l l UCLA recently USC in the past

What is a Hacker? l Wikipedia has three definitions: l Hacker: Highly skilled programmer l One who has l 33 t c 0 ding skillz l Generally, then can get the job done when no one else can by writing “hack-job” code § l l Downside – impossible to maintain without the “hacker” Hacker: Computer and network security expert l One who specializes in access control mechanisms for computer and network systems l In a sense, you are taking this class to become hackers Hacker: Hardware Modifier l Not normally used anymore; they are called “modders”

What does the rest of the world think a hacker is? l Media definition of hacker = our definition of cracker l l Someone who maliciously breaks into networks and systems for personal gain Crack (v) – to break into a system with malicious intent

Who are these hackers? l Internal threats (rogue insiders) l l l Bored students Disgruntled employees External threats l l Bored people (lots of them out there worldwide!), political action groups l Example: Phil Angelides, Democratic Candidate for Governor of California http: //www. theregister. co. uk/2006/09/13/schwarzeneg ger_audio_hack/ crackers & hackers ex-employees

Levels of Hackers l Script kiddies/Cyberpunks l l l Intermediate Hackers l l Novices Very little actual knowledge of what goes on behind the scenes. They simply find a cool tool on the net Media stereotype (pimply faced, lives in his mom’s basement, etc) Sloppy, leave all sorts of digital evidence of their actions Most annoying and cause the most headaches “halfway hackers” Know enough to cause serious damage Most want to be advanced (l 33 t), and will get there if they’re not caught Advanced Hackers l l Criminal Experts Uber/l 33 t hackers These are the authors of the hacking tools, viruses, and malware They know enough to hide their tracks – most of the time you won’t even know that your system has been compromised

Why Hack? l l l Because they can! Curiosity, notoriety, fame Profit ($$$ or other gain) l Hackers for Hire l l l Korean National Police Agency busted the Internet’s largest known organized hacking mafia 4, 400 members!!!!! Sell people’s personal information on the black market

Why hack? l l l Underlying the psyche of the criminal hacker is a deep sense of inferiority l Consequently, the mastery of computer technology, or the shut down of a major site, might give them a sense of power l "Causing millions of dollars of damage is a real power trip“ Hacktivism – hactivist. net l “Free Kevin” messages that were put onto websites without the owners permission Cyberterrorists l Crash critical systems, bring down power grids & air traffic control towers l US fights this through the Department of Homeland Security l Customs, FBI & CIA

Hacker Methodology 1. Gather target information 2. Identify services offered by target to the public (whether intentional or not) 3. Research the discovered services for known vulnerabilities 4. Attempt to exploit the services 5. Utilize exploited services to gain additional privileges from the target 6. Reiterate steps 1 -5 until goals are achieved

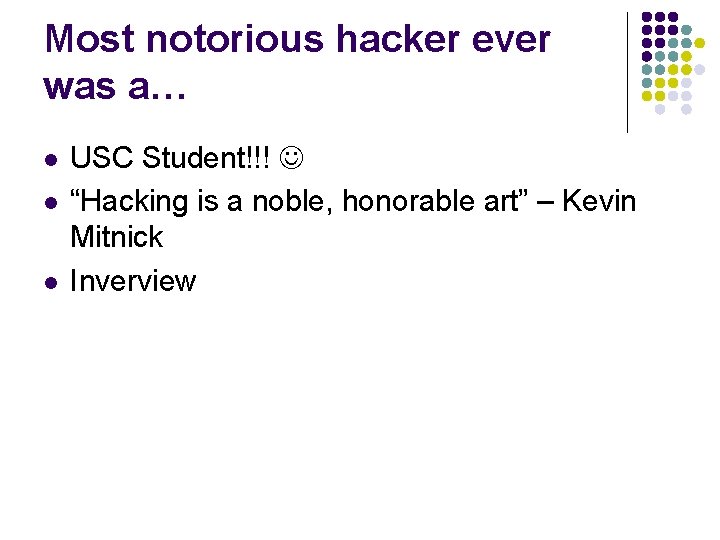
Most notorious hacker ever was a… l l l USC Student!!! “Hacking is a noble, honorable art” – Kevin Mitnick Inverview

Dangers of Security l l l Fine line between legal and illegal hacking No laws in place to protect hackers from technically illiterate lawyers Ethics

Assignment Read “Hacker Hall of Fame” 1. l http: //tlc. discovery. com/convergence/hackers/bio. html Visit the following websites and search for security related articles in the past 2 weeks. 2. l www. cnn. com, www. news. com, www. nytimes. com and www. latimes. com
 Private securty
Private securty Osi security architecture with neat diagram
Osi security architecture with neat diagram Security guide to network security fundamentals
Security guide to network security fundamentals Wireless security in cryptography
Wireless security in cryptography Electronic mail security in network security
Electronic mail security in network security Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
Security guide to network security fundamentals Vumc eprocurement
Vumc eprocurement 457 1
457 1 Cs 457
Cs 457 Cpsc 457
Cpsc 457 Region 10 rams 457 plan
Region 10 rams 457 plan Ece 458
Ece 458 Enee457
Enee457 Artaxerxes decree 444
Artaxerxes decree 444 Cpsc 457
Cpsc 457 Ran nssmf
Ran nssmf Brownfield site disadvantages
Brownfield site disadvantages Greenfield advantages and disadvantages
Greenfield advantages and disadvantages Pros and cons of greenfield investment
Pros and cons of greenfield investment Filtro greenfield
Filtro greenfield Adam & eve greenfield
Adam & eve greenfield Analisis swot pt greenfield
Analisis swot pt greenfield Talk about a family eloise greenfield
Talk about a family eloise greenfield Lazar greenfield
Lazar greenfield Bruce evans greenfield township pa
Bruce evans greenfield township pa