IT AUDITS IT audits pemeriksaan terhadap proses atau

















- Slides: 22

IT AUDITS Ø IT audits: pemeriksaan terhadap proses atau data yang melekat dengan teknologi informasi. Ø Ø Ø Berkaitan dengan internal, external, dan fraud audits Jangkauan pemeriksaan IT semakin meningkat Teknik Audit Berbantuan Komputer (TABK) CAATTs (Computer Assisted Audit Tools and Techniques) audit through computer IT governance as part of corporate governance Sertifikasi CISA (Certified Information Systems Auditor) Standar, pedoman dan sertifikasi dikelola oleh: ISACA (Information Systems Audit and Control Association)

Audit Around The Computer Seperti audit manual n Hanya memeriksa input dan output saja, tanpa pemeriksaan lebih dalam terhadap penggunaan program. Jika input dan output benar dianggap benar n Dilakukan jika sebagian besar pengolahan data masih manual dan penggunaan komputer hanya ut beberapa bagian saja n

Audit With The Computer n Selain input dan output juga diperiksa proses pada komputer, dapat digunakan file transaksi yang berkaitan

Audit Through The Computer n Melaksanakan pekerjaan audit dengan bantuan komputer

IT AUDITS IT audits (Hall, 2005) : Focus on the computer-based aspects of an organization’s information system – Assess the proper implementation, operation, and control of computer resources – 5

Information System Auditing (Weber, 1999) “IS Auditing is the process of collecting and evaluating evidence to determine whether a computer system safeguards assets, maintains data integrity, allows organizational goals to be achieved effectively, and uses resources efficiently” 6

The Work of an IT Auditor Evaluating controls over specific applications n Providing assurance over specific processes n Providing third-party assurance n Penetration testing n Supporting the financial audit n Searching for IT-based fraud (Hunton, 2004) n 7

What is an IT Audit? … most accounting transactions to be in electronic form without any paper documentation because electronic storage is more efficient. … These technologies greatly change the nature of audits, which have so long relied on paper documents.

IT Audit? n Proses pengumpulan dan evaluasi fakta/bukti untuk menentukan apakah sistem (terkomputerisasi): – – – Menjaga aset Memelihara integritas data Memampukan komunikasi & akses informasi Mencapai tujuan operasional secara efektif Mengkonsumsi sumber daya secara efisien

Issues in IS Auditing v Why we are concerned about control and audit of computer systems v Nature & types of management and application controls and their relative strengths and limitations v Types of evidence collection techniques available v Types of evidence evaluation techniques available v How to do an IS audit and how to manage its 10

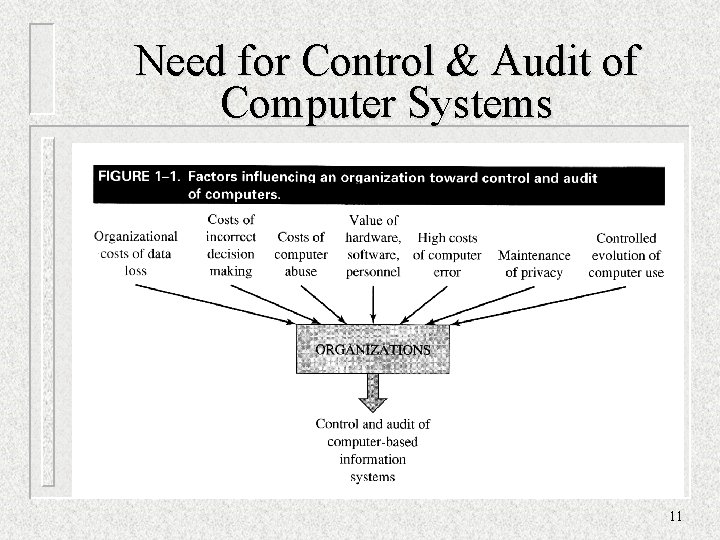
Need for Control & Audit of Computer Systems 11

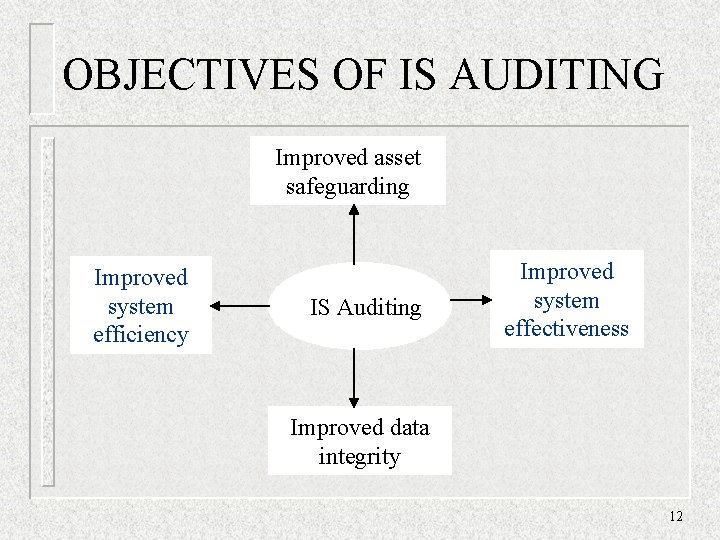
OBJECTIVES OF IS AUDITING Improved asset safeguarding Improved system efficiency IS Auditing Improved system effectiveness Improved data integrity 12

Changes to Evidence Collection v New internal control technology needed v Greater number and diversity of internal controls v Internal controls are more critical v New evidence collection technologies needed v Greater number and diversity of evidence collection techniques 13

Changes to Evidence Evaluation v Computer errors tend to be deterministic rather than stochastic computer – always executes incorrectly v Overall evaluation of the evidence collected is more difficult to undertake 14

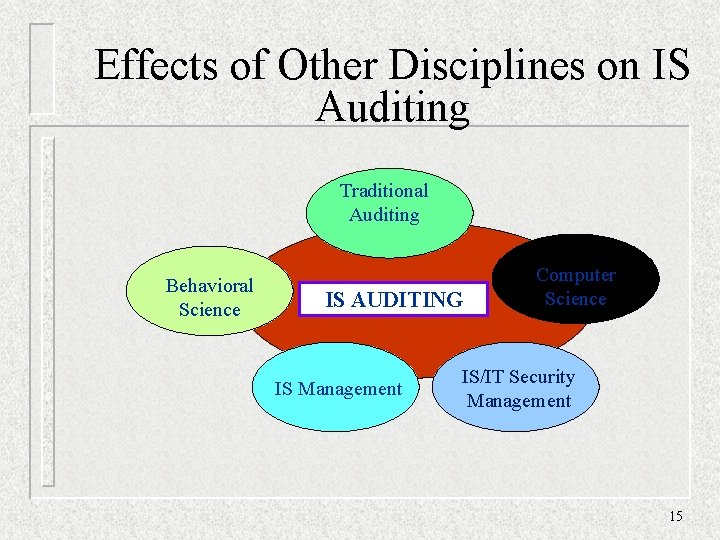
Effects of Other Disciplines on IS Auditing Traditional Auditing Behavioral Science IS AUDITING IS Management Computer Science IS/IT Security Management 15

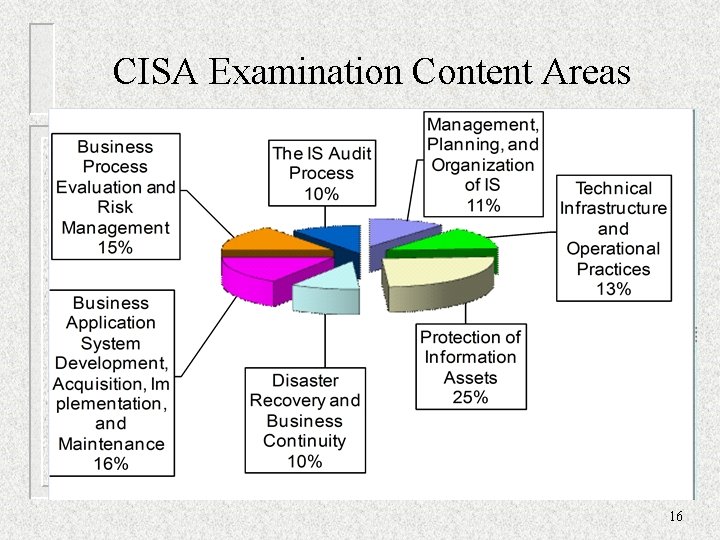
CISA Examination Content Areas 16

17

Impact IT on Audit Profession n n Education programs needed Quality publications needed in IT area IT Chapter needed New methods and fresh approaches required Auditing in real time 18

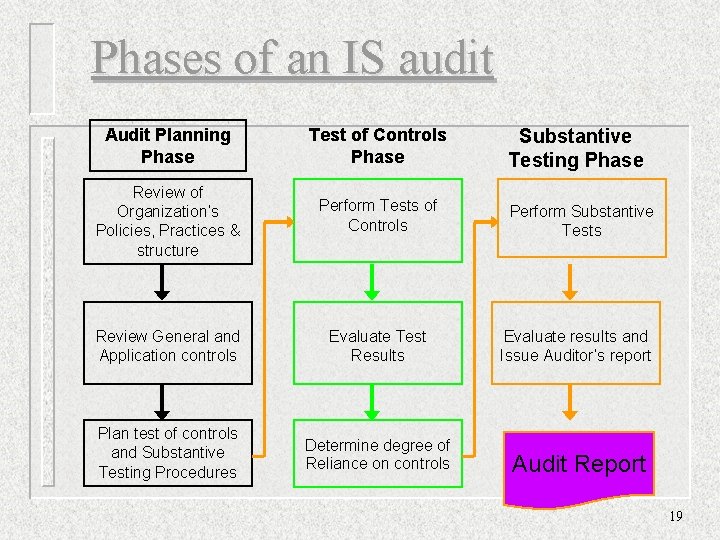
Phases of an IS audit Audit Planning Phase Test of Controls Phase Review of Organization’s Policies, Practices & structure Perform Tests of Controls Review General and Application controls Evaluate Test Results Evaluate results and Issue Auditor’s report Plan test of controls and Substantive Testing Procedures Determine degree of Reliance on controls Audit Report Substantive Testing Phase Perform Substantive Tests 19

THE IT ENVIRONMENT Ø Ø Selalu diperlukan sistem pengendalian internal yang efektif pemanfaatan teknologi informasi. Lingkungan dengan IT menciptakan ‘kerumitan’ baru dari sistem ‘kertas’ sebelumnya: Ø Ø Ø Data digital menjadi utama pentingnya akses dan hubungan dalam jaringan Meningkatnya cara kecurangan atau kejahatan baru yang mungkin sulit dideteksi. (baik manajemen ataupun dari pihak luar)

THE IT ENVIRONMENT Ø Audit planning Ø Tests of controls Ø Substantive tests Ø CAATT (Computer Assisted Audit Tools and Techniques)

INTERNAL CONTROL Ø is … policies, practices, procedures … designed to … Ø safeguard assets Ø ensure accuracy and reliability promote efficiency measure compliance with policies Ø Ø
 Tujuan pemeriksaan subsequent events
Tujuan pemeriksaan subsequent events Komponen laporan audit atas proses right issue
Komponen laporan audit atas proses right issue Macam-macam validasi industri farmasi
Macam-macam validasi industri farmasi Implikasi proses pembelajaran terhadap pdp
Implikasi proses pembelajaran terhadap pdp Proses bisnis pkh
Proses bisnis pkh Ciri-ciri kritik sastra adalah
Ciri-ciri kritik sastra adalah Pantry audit in research methodology
Pantry audit in research methodology Cjis audit
Cjis audit Do-254 audits
Do-254 audits Multimedia compliance audit
Multimedia compliance audit Issai 4000
Issai 4000 Second party audits
Second party audits Infection control audits
Infection control audits Criteria for evaluating performance of channel members
Criteria for evaluating performance of channel members Second party audits
Second party audits Nap 5 infographic
Nap 5 infographic 30-10-2 ocga
30-10-2 ocga Environmental audits
Environmental audits Difference between inspection and audit
Difference between inspection and audit Sas 70 definition
Sas 70 definition Dependent audits
Dependent audits Vraag
Vraag Total resource management
Total resource management











































