Internet Security 1 Int Si 1 14 Network


- Slides: 29

Internet Security 1 (Int. Si 1) 14 Network Access Control Prof. Dr. Andreas Steffen Institute for Internet Technologies and Applications (ITA) Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 1

Internet Security 1 (Int. Si 1) 14. 1 Firewalls The Traditional Way Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 2

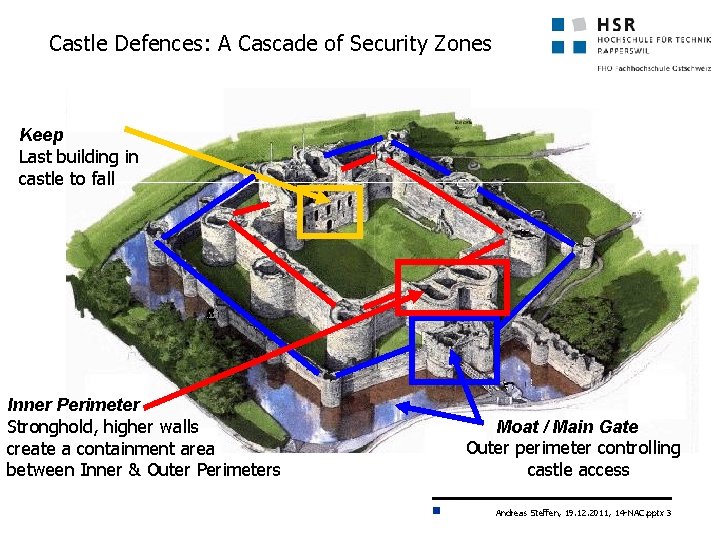
Castle Defences: A Cascade of Security Zones Keep Last building in castle to fall Inner Perimeter Stronghold, higher walls create a containment area between Inner & Outer Perimeters Moat / Main Gate Outer perimeter controlling castle access Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 3

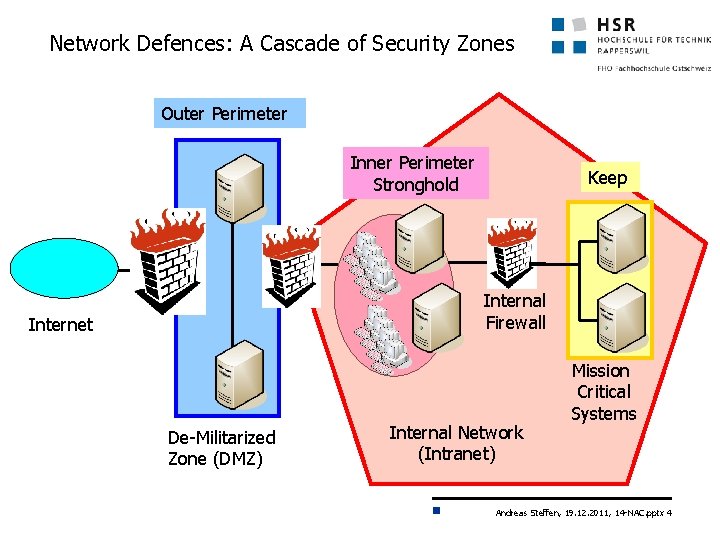
Network Defences: A Cascade of Security Zones Outer Perimeter Inner Perimeter Stronghold Keep Internal Firewall Internet De-Militarized Zone (DMZ) Internal Network (Intranet) Mission Critical Systems Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 4

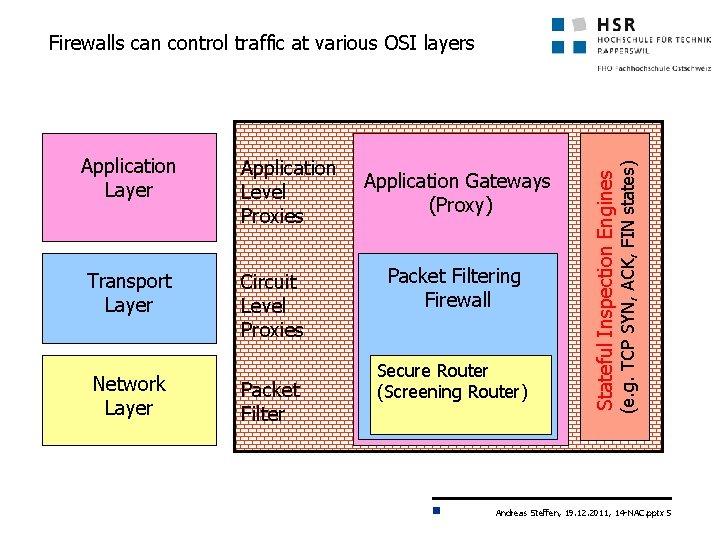
Application Level Proxies Transport Layer Circuit Level Proxies Network Layer Packet Filter Application Gateways (Proxy) Packet Filtering Firewall Secure Router (Screening Router) Stateful Inspection Engines Application Layer (e. g. TCP SYN, ACK, FIN states) Firewalls can control traffic at various OSI layers Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 5

How to Protect against Trojan Horses? Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 6

Internet Security 1 (Int. Si 1) 14. 2 Network Access Control The Modern Way Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 7

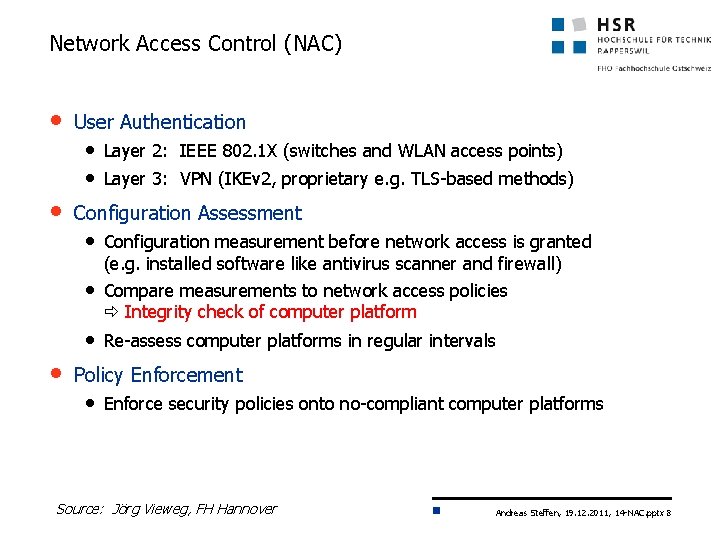
Network Access Control (NAC) • User Authentication • Layer 2: IEEE 802. 1 X (switches and WLAN access points) • Layer 3: VPN (IKEv 2, proprietary e. g. TLS-based methods) • Configuration Assessment • Configuration measurement before network access is granted (e. g. installed software like antivirus scanner and firewall) • Compare measurements to network access policies Integrity check of computer platform • Re-assess computer platforms in regular intervals • Policy Enforcement • Enforce security policies onto no-compliant computer platforms Source: Jörg Vieweg, FH Hannover Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 8

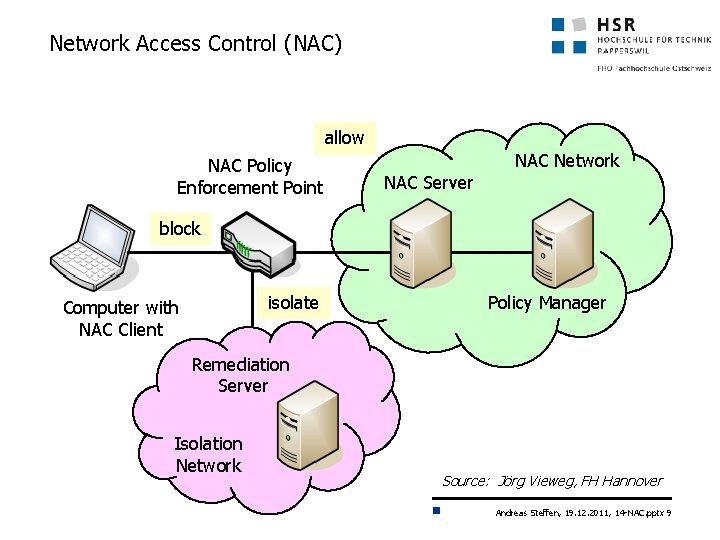
Network Access Control (NAC) allow NAC Policy Enforcement Point NAC Network NAC Server block isolate Computer with NAC Client Policy Manager Remediation Server Isolation Network Source: Jörg Vieweg, FH Hannover Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 9

NAC Compatibility Issues • Proprietary Solutions • • • Cisco - Network Admission Control (NAC) Microsoft - Network Access Protection (NAP) Juniper - Unified Access Control (UAC) HP - Pro. Curve Access Control Security Solution Still Secure - Safe Access Emerging Standards • Trusted Computing Group (TCG) - Trusted Network Connect (TNC) • IETF - Network Endpoint Assessment (NEA) • Open Source Implementations • • XSupplicant - IEEE 802. 1 X NAC Client/PEP, supports TCG TNC & NEA wpa_supplicant - IEEE 802. 1 X NAC Client/PEP, supports TCG TNC@FHH - Free. RADIUS-based NAC Server, implements TCG TNC strong. Swan - IKEv 2 NAC Client/PEP/Server, supports TCG TNC & NEA Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 10

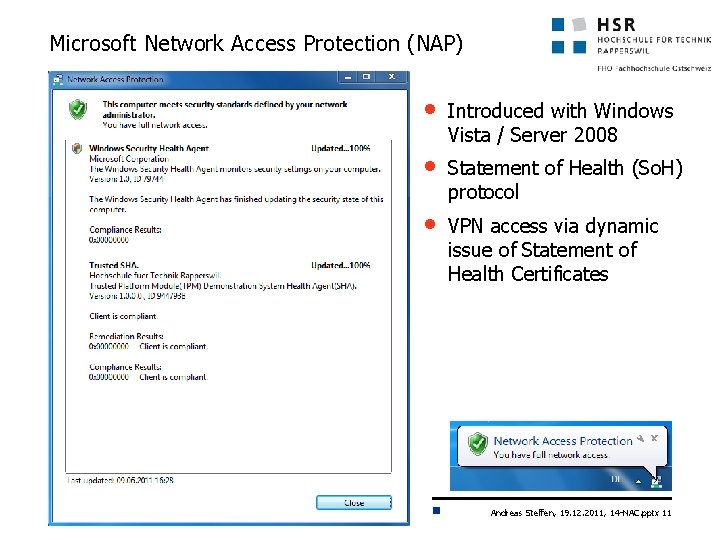
Microsoft Network Access Protection (NAP) • Introduced with Windows Vista / Server 2008 • Statement of Health (So. H) protocol • VPN access via dynamic issue of Statement of Health Certificates Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 11

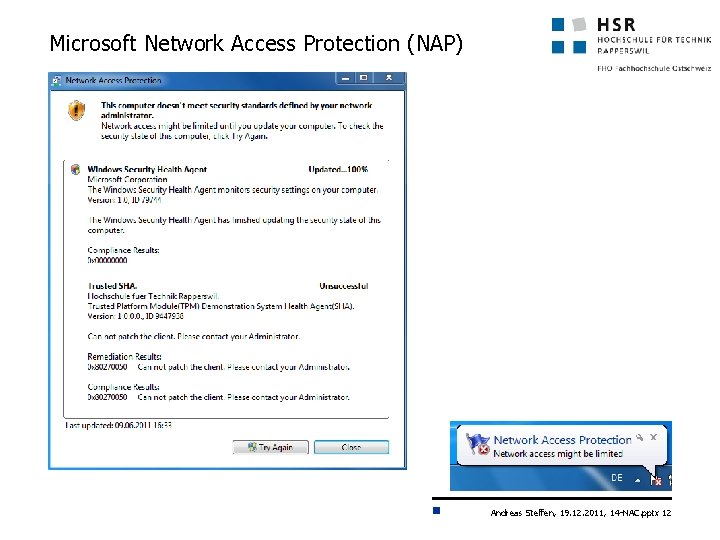
Microsoft Network Access Protection (NAP) Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 12

Internet Security 1 (Int. Si 1) 14. 3 Trusted Network Connect Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 13

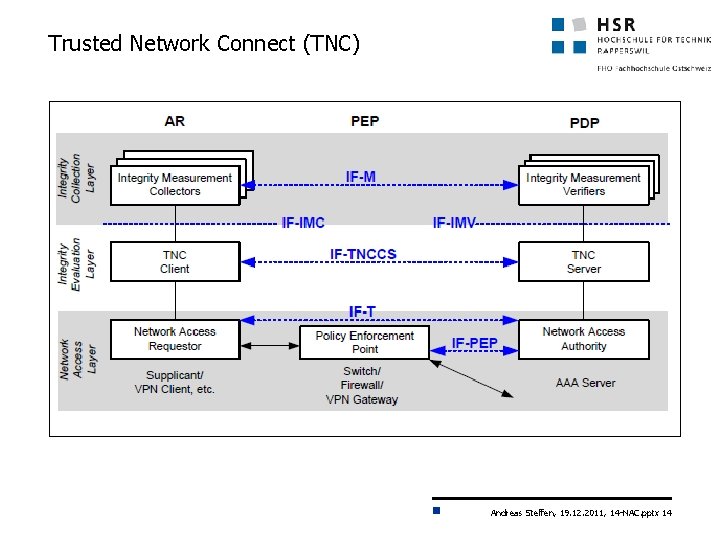
Trusted Network Connect (TNC) Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 14

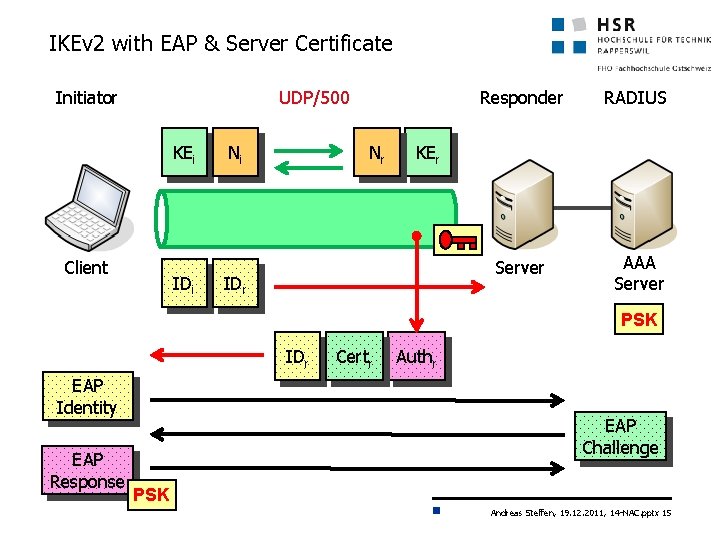
IKEv 2 with EAP & Server Certificate Initiator UDP/500 KEi Client IDi Ni Nr Responder RADIUS Server AAA Server KEr IDr PSK IDr EAP Identity EAP Response Certr Authr EAP Challenge PSK Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 15

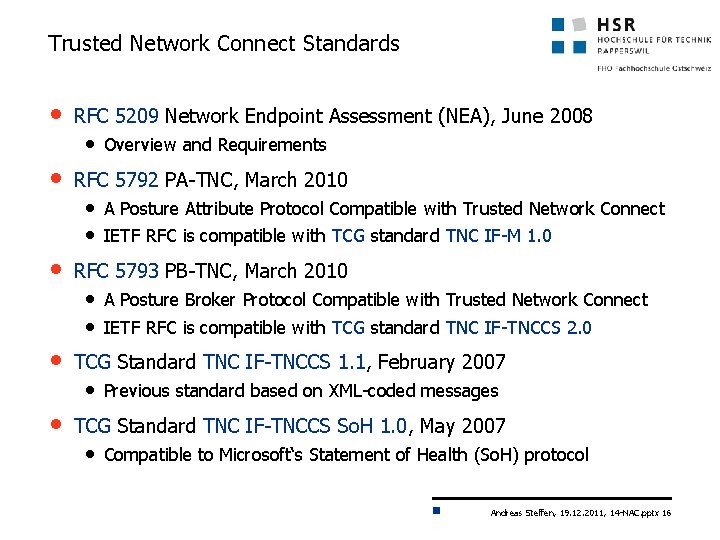
Trusted Network Connect Standards • RFC 5209 Network Endpoint Assessment (NEA), June 2008 • Overview and Requirements • RFC 5792 PA-TNC, March 2010 • A Posture Attribute Protocol Compatible with Trusted Network Connect • IETF RFC is compatible with TCG standard TNC IF-M 1. 0 • RFC 5793 PB-TNC, March 2010 • A Posture Broker Protocol Compatible with Trusted Network Connect • IETF RFC is compatible with TCG standard TNC IF-TNCCS 2. 0 • TCG Standard TNC IF-TNCCS 1. 1, February 2007 • Previous standard based on XML-coded messages • TCG Standard TNC IF-TNCCS So. H 1. 0, May 2007 • Compatible to Microsoft‘s Statement of Health (So. H) protocol Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 16

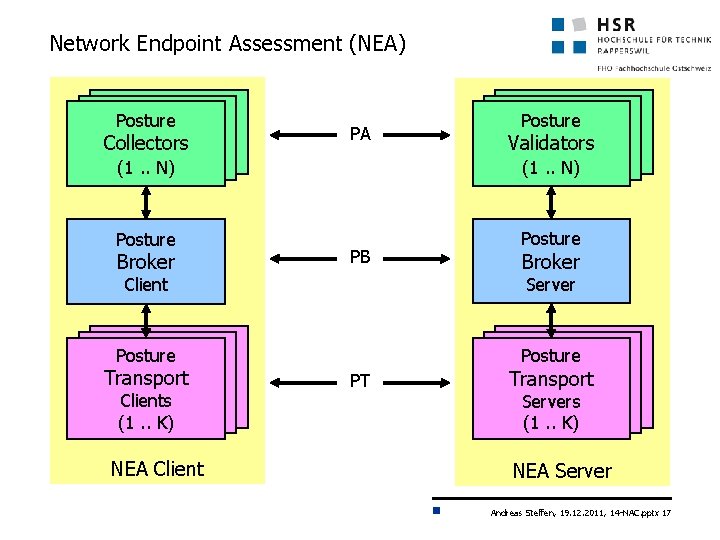
Network Endpoint Assessment (NEA) Posture Collectors PA (1. . N) (1(1. . N)N) Posture Broker PB NEA Client Posture Broker Server Posture Clients (1. . K) (1(1. . K)K) Collectors Validators (1. . N) (1(1. . N)N) Client Transport Posture Posture PT Transport Clients Servers (1. . K) (1(1. . K)K) NEA Server Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 17

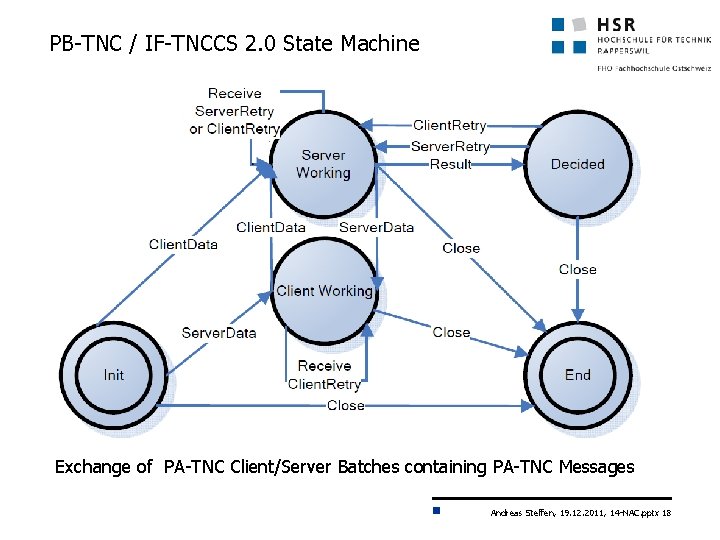
PB-TNC / IF-TNCCS 2. 0 State Machine Exchange of PA-TNC Client/Server Batches containing PA-TNC Messages Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 18

How to Protect against Cyber Attacks? Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 19

Internet Security 1 (Int. Si 1) 14. 4 Metadata Access Point Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 20

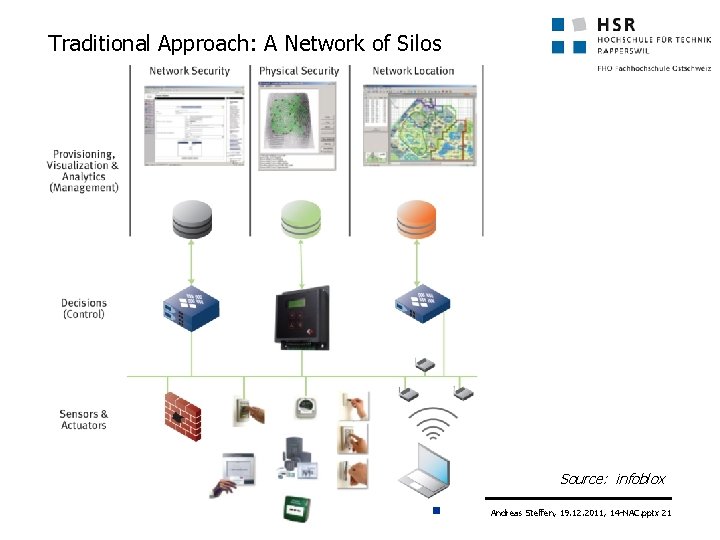
Traditional Approach: A Network of Silos Source: infoblox Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 21

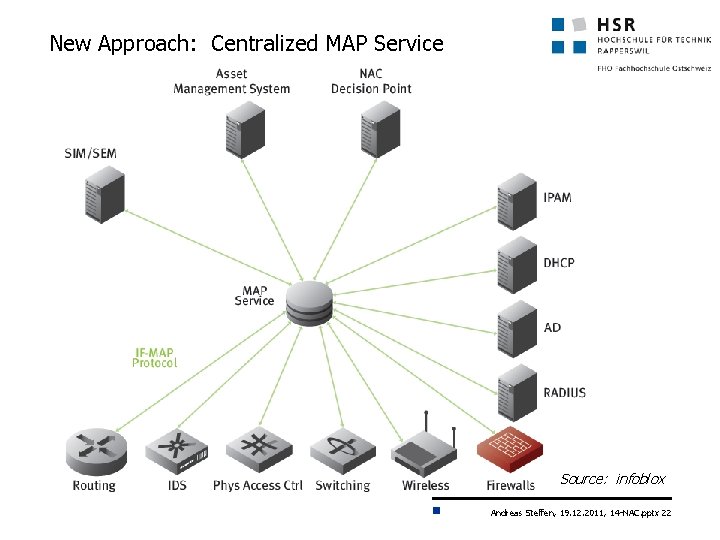
New Approach: Centralized MAP Service Source: infoblox Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 22

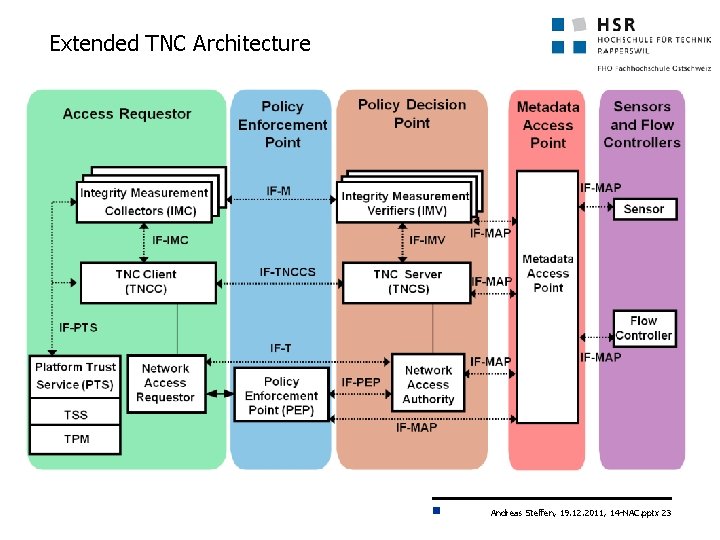
Extended TNC Architecture Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 23

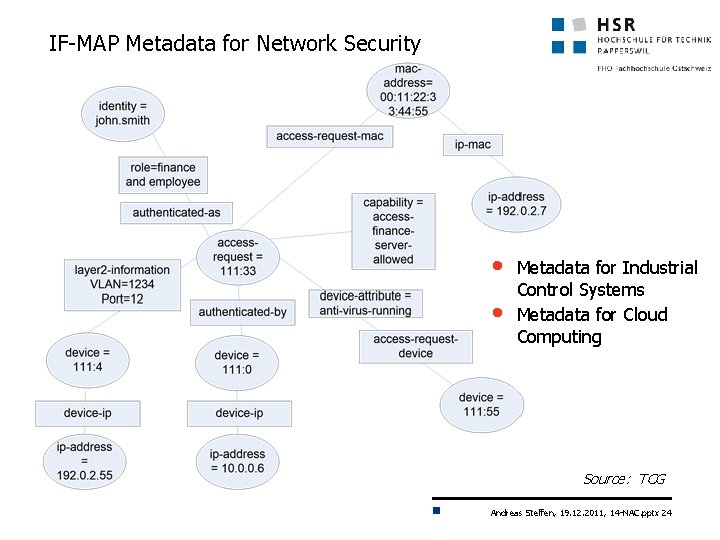
IF-MAP Metadata for Network Security • • Metadata for Industrial Control Systems Metadata for Cloud Computing Source: TCG Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 24

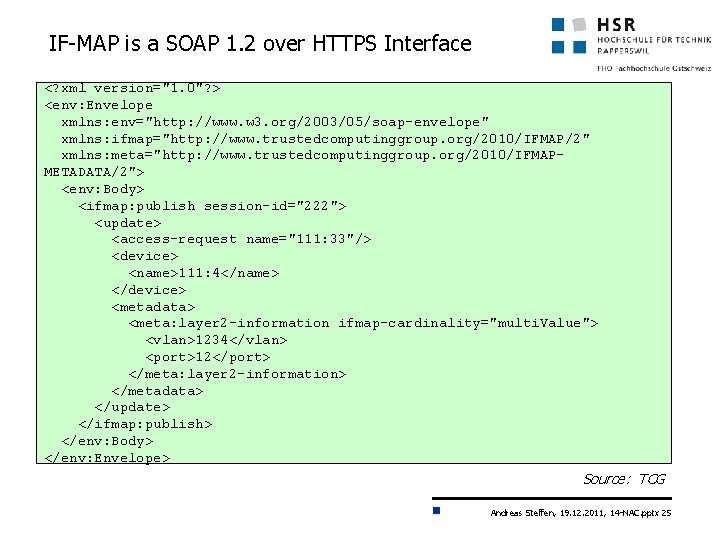
IF-MAP is a SOAP 1. 2 over HTTPS Interface <? xml version="1. 0"? > <env: Envelope xmlns: env="http: //www. w 3. org/2003/05/soap-envelope" xmlns: ifmap="http: //www. trustedcomputinggroup. org/2010/IFMAP/2" xmlns: meta="http: //www. trustedcomputinggroup. org/2010/IFMAPMETADATA/2"> <env: Body> <ifmap: publish session-id="222"> <update> <access-request name="111: 33"/> <device> <name>111: 4</name> </device> <metadata> <meta: layer 2 -information ifmap-cardinality="multi. Value"> <vlan>1234</vlan> <port>12</port> </meta: layer 2 -information> </metadata> </update> </ifmap: publish> </env: Body> </env: Envelope> Source: TCG Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 25

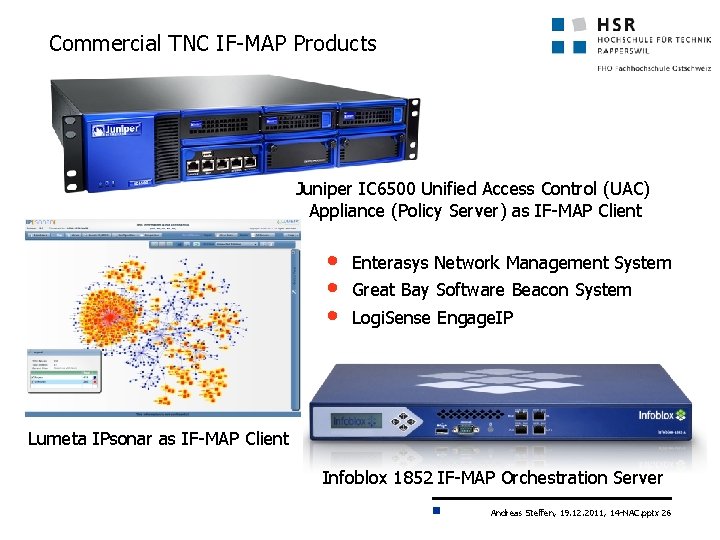
Commercial TNC IF-MAP Products Juniper IC 6500 Unified Access Control (UAC) Appliance (Policy Server) as IF-MAP Client • • • Enterasys Network Management System Great Bay Software Beacon System Logi. Sense Engage. IP Lumeta IPsonar as IF-MAP Client Infoblox 1852 IF-MAP Orchestration Server Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 26

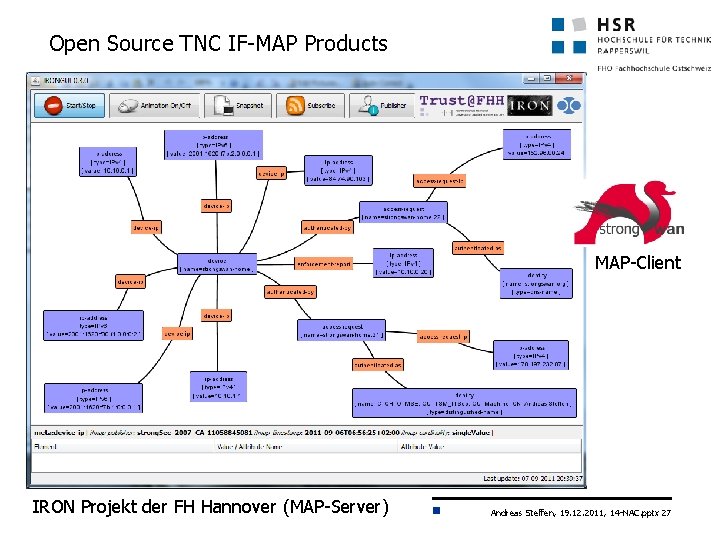
Open Source TNC IF-MAP Products MAP-Client IRON Projekt der FH Hannover (MAP-Server) Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 27

Internet Security 1 (Int. Si 1) What about Lying Endpoints? Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 28

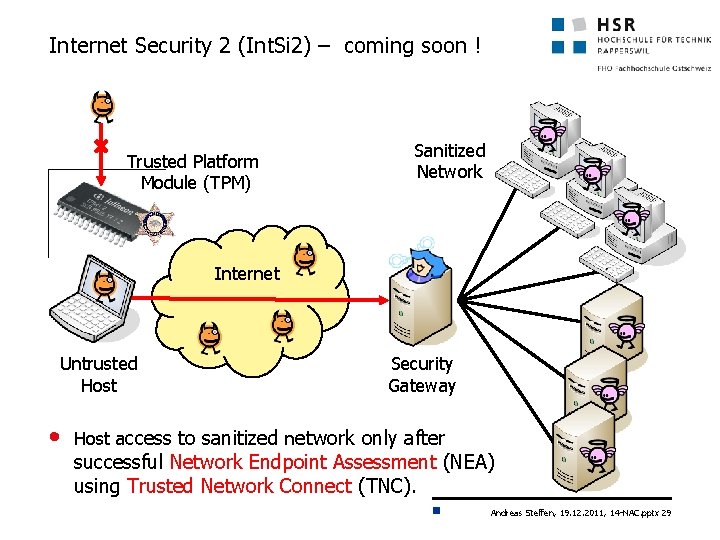
Internet Security 2 (Int. Si 2) – coming soon ! Trusted Platform Module (TPM) Sanitized Network ? Internet Untrusted Host • Security Gateway Host access to sanitized network only after successful Network Endpoint Assessment (NEA) using Trusted Network Connect (TNC). Andreas Steffen, 19. 12. 2011, 14 -NAC. pptx 29