Information Warfare Summary Information Security Information Assurance Information

























- Slides: 27

Information Warfare Summary

Information Security Information Assurance Information Warfare Information Dominance

Information Security (INFOSEC) l Protection of information against intentional or unintentional unauthorized – Disclosure (confidentiality) – Modification (integrity) – Destruction (availability) l Concerned CSCE 727 - Farkas mainly with owned resources 3

Security Tradeoffs Security Functionality COST Ease of Use CSCE 727 - Farkas 4

Information Assurance l Information security (prevention) plus – Authenticity and non-repudiation – Detection and reaction capabilities – Additional threats, like perception managements and exploitation of public media l Addresses intentional or unintentional threats CSCE 727 - Farkas 5

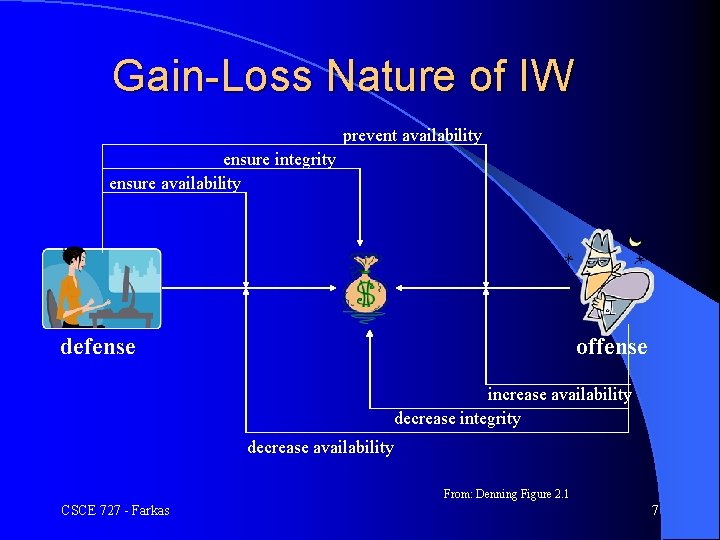
Information Warfare Addresses only intentional attacks l Information in any form and transmitted over any media l Defensive operations: l – Protection against attacks – Concerned with non-owned and owned resources l Offensive operations: – Exploit vulnerabilities in information resources – Motives, means, opportunities WIN-LOSE NATURE OF OPERATIONS CSCE 727 - Farkas 6

Gain-Loss Nature of IW prevent availability ensure integrity ensure availability defense offense increase availability decrease integrity decrease availability From: Denning Figure 2. 1 CSCE 727 - Farkas 7

Activities l Play: hackers vs. owners l Crime: perpetrators vs. victims l Individual rights: individuals vs. individuals/organizations/government l National security: national level activities – State activities – Terrorism CSCE 727 - Farkas 8

Intention of Attackers l Defensive IW l Difficult to guess l Determines response and incident handling CSCE 727 - Farkas 9

Offensive Information Warfare

Win-Lose Activity Alter availability and integrity of resources to benefit the offense l Old vs. new methods l Areas: l 1. 2. 3. 4. 5. 6. Open source and competitive intelligence Psyops and perception management Insiders threat Signal intelligence Computer attacks Malicious software CSCE 727 - Farkas 11

1 Open Source Intelligence l Protected information: readily available in public domain, can be inferred from public data, or deduced from aggregated public data l Goal: answer specific question in support of some mission l Advantages: no risk for collector, provides context, mode of information acquisition, cover for data discovery by secret operations l Disadvantages: may not discover important information, assurance of discovery(? ) CSCE 727 - Farkas 12

1 Privacy and Copyright l Piracy – Copyright Infringement Acquisition of protected work without the owner’s permission l Human perception: not serious crime l Significant loss for marketing/manufacturing/owner l – Trademark Infringement Intellectual property disputes l Domain name disputes l CSCE 727 - Farkas 13

2 Psyops and Perception Management l Information operations that aim to affect perception of others l Goal: influence actions l Means: influence emotions, reasoning, decisions l Target: individuals, groups, nation, World l Censorship – Offensive: denies population access to certain materials – Defensive: protect society from materials that would undermine its culture or governance CSCE 727 - Farkas 14

3 Insider Threat l Employees working for an organization – Generally trusted – Easy access to resources – Know how the system works l Domains – – l State and military espionage Economic espionage Corporate espionage Privacy compromises Motivation of offense – Financial gain, ideology, revenge CSCE 727 - Farkas 15

4 Signal Intelligence l Operations that involves interception and analysis of signals across electromagnetic spectrum l Intelligence report, criminal investigations, employee monitoring l U. S. Federal wiretap restrictions l Foreign intelligence l Privacy rights CSCE 727 - Farkas 16

5 Computer Attacks Passive vs. active attacks l Attack phases: l – Intelligence gathering – Planning – Attack – Inside the system: l l l Hiding Future attacks Types of attacks CSCE 727 - Farkas 17

6 Malicious Software l Genesis of software flaws – How: intentional, unintentional – When: development, operation, maintenance – Where: OS, support system, application l Viruses, worms, bacteria, etc. l Malicious code behavior and detection CSCE 727 - Farkas 18

Defensive Information Warfare

Defensive Information Warfare l Protect information resources from attacks l Preserve the value of resource or recover lost value l Security Policy l Methods l Response CSCE 727 - Farkas 20

Vulnerability Monitoring l Identify security weaknesses l Methods: automated tools, human walkthrough, surveillance, audit, background checks l Red team: organized group of people attempting to penetrate the security safeguards of the system CSCE 727 - Farkas 21

Secure System Development l National Computer Security Center (NCSC): Rainbow Series l Common l National Criteria (with Canada and Europe) Information Assurance Partnership (NIAP) l Security CSCE 727 - Farkas Awareness and Training 22

Secure Software Design l SW reliability l SW security l Systematic SW design with security and reliability – N-versioning – UML misuse cases CSCE 727 - Farkas 23

Incident Handling l Not all incidents can be prevented Incident handling – – l Benefits: – – l Prevention and preparedness Detection and analysis Containment and recovery Post-incident activity Systematic and appropriate response to incidents Quick response reduce loss and damage Strengthen security Satisfy legal requirements Federal agency requirements CSCE 727 - Farkas 24

National Level Information Warfare

National Level Security l Domestic – Posse Commitatus (military involvement for counter terrorism) – Information sharing and intelligence oversight l International – Jus in Pace (law of peace) – Jus ad Bellum (law of conflict management) – Jus in Bello (law of war) CSCE 727 - Farkas 26

Project Information - Review process bring hard copies of reviews scribes: start discussion of projects - Review assignments CSCE 727 - Farkas 27