ICS 454 Cryptography Advanced Encryption Standard AES Sultan





- Slides: 10

ICS 454 Cryptography Advanced Encryption Standard (AES) Sultan Almuhammadi

Outline § Background § AES Encryption and Decryption § Security Issues § Implementation Issues

Background § In 1977, the National Bureau of Standards (NBS) adopted DES. § In 1994, the National Institute of Standards and Technology (NIST), reaffirmed DES for federal use for another 5 years. § In 1999, NIST adopted 3 DES. § Pros: § 168 -bit key overcomes brute-force attack. § Cons: § Triple rounds relatively slow in software. § 64 -bit block size larger is better. § 3 DES is not a good candidate for long-term use.

Background § In 1997, NIST called for a new Advanced Encryption Standard (AES) § AES Requirements: § § Must have equal or better security than 3 DES. Must improve the efficiency. Must be a 128 -bit symmetric block cipher. Must support 128/192/256 bit key lengths. § In 2001, NIST selected Rijndael (by Rijmen and Daemen) as the new AES. § AES will replace 3 DES eventually. Until then, NIST approves 3 DES for US government use.

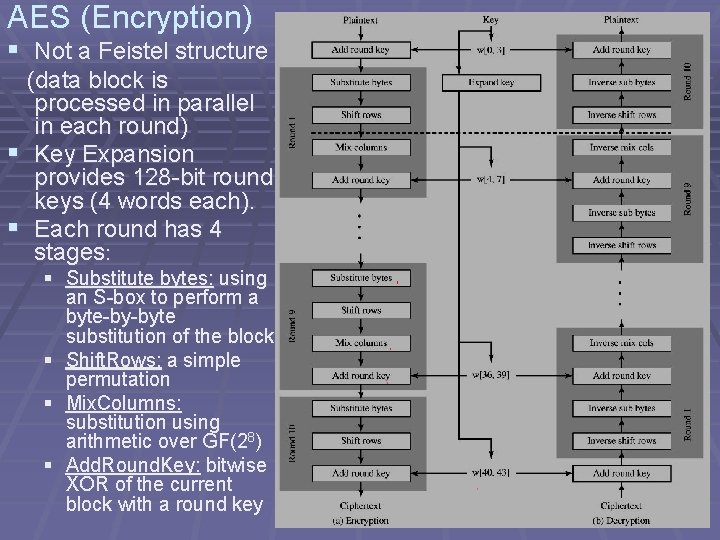
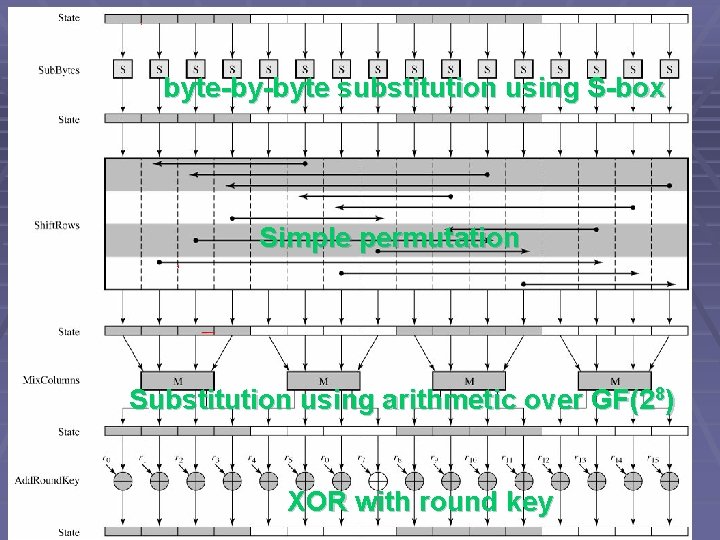
AES (Encryption) § Not a Feistel structure (data block is processed in parallel in each round) § Key Expansion provides 128 -bit round keys (4 words each). § Each round has 4 stages: § Substitute bytes: using an S-box to perform a byte-by-byte substitution of the block § Shift. Rows: a simple permutation § Mix. Columns: substitution using arithmetic over GF(28) § Add. Round. Key: bitwise XOR of the current block with a round key

byte-by-byte substitution using S-box Simple permutation Substitution using arithmetic over GF(28) XOR with round key

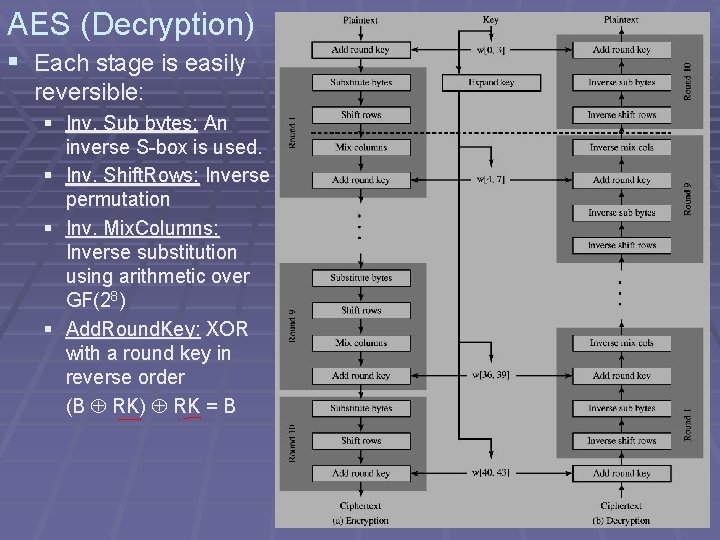
AES (Decryption) § Each stage is easily reversible: § Inv. Sub bytes: An inverse S-box is used. § Inv. Shift. Rows: Inverse permutation § Inv. Mix. Columns: Inverse substitution using arithmetic over GF(28) § Add. Round. Key: XOR with a round key in reverse order (B RK) RK = B

AES Security Issues § Only the Add. Round. Key stage makes use of the key. § Other stages are reversible without the key add no § § security. Add. Round. Key stage by itself is just an XOR scheme attackable. Other three stages provide confusion/diffusion/ nonlinearity (i. e. scrambling the block), but no security. The four stages together in each round make it both efficient and highly secure. The S-box is designed such that: § § § It is resistant to known cryptanalytic attacks It has no fixed point (S-box(n) = n) it is not self-inverse. Eg. S-box(95) = 2 A, but Inv. S-box(95) = AD

AES Implementation Issues § Very efficient on 8 -bit processor: § Add. Round. Key: bytewise XOR operation § Shift. Rows: simple byte shifting § Sub. Bytes: operates at byte-level § Mix. Columns: multiplies matrices in GF(28) § On 32 -bit processor, a more efficient implementation can be achieved with operations defined on 32 -bit words.

AES Demo § Pls visit the link below for a full AES demo: http: //www. cs. bc. edu/~straubin/cs 38105/blockciphers/rijndael_ingles 2004. swf