Advanced Encryption Standard AES Reasons for AES n








- Slides: 15

Advanced Encryption Standard (AES)

Reasons for AES n Problems with DES n n n key size is small Theoretical attacks Exhaustive key search attacks Triple-DES – pretty safe, but slow AES selected out of 15 candidates Issued as FIPS PUB 197 standard in Nov -2001

AES Features n n n Symmetric key block cipher 128 -bit data, 128/192/256 -bit keys Resistant against known attacks Fast Compact code Simple

AES Cipher n n n Designed by Rijmen-Daemen in Belgium Anticipated life of 20 -30 years NIST have released all submissions & unclassified analyses Fixed data block size : 128 bits Processes a data block in 4 groups of 4 bytes and operates an entire block in every round A data block is termed as “state. ” Original plaintext known as initial state.

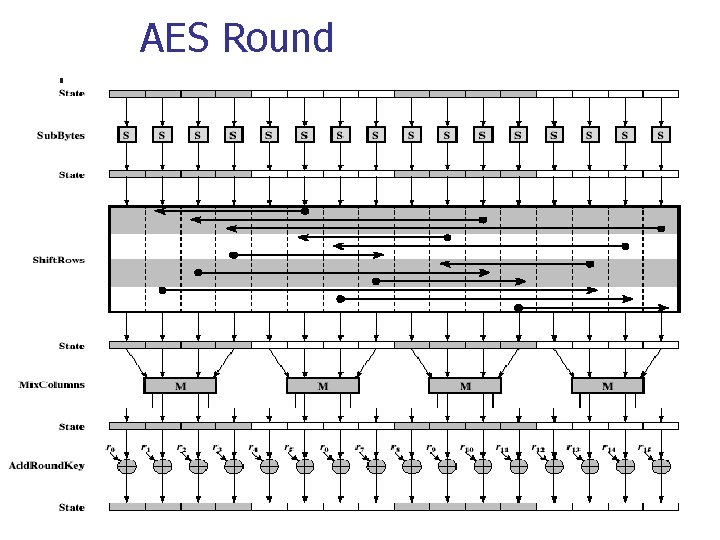
AES n Goes through 9/11/13 rounds. In each round, it does: n n n Byte substitution (Sub. Bytes()) Shift rows (Shift. Rows()) Mix columns (Mix. Colums()) Add round key (Add. Round. Key()) Last round is incomplete

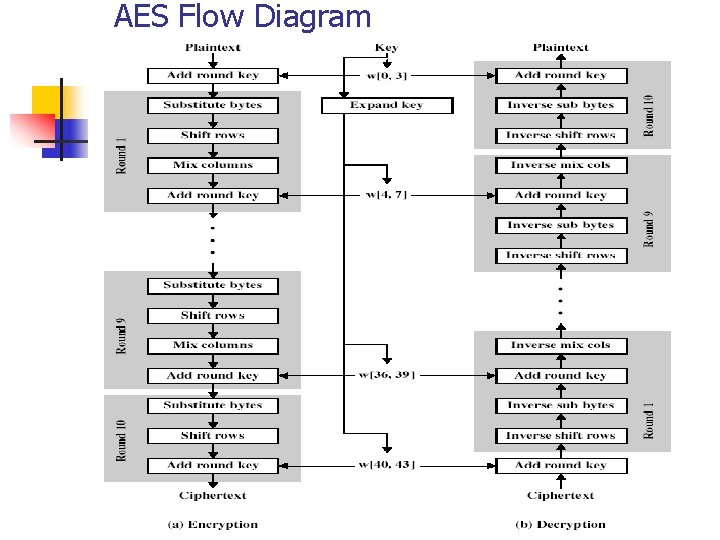
AES Flow Diagram

Byte Substitution n n Uses a 16 x 16 table Each byte of state is replaced by byte in row indexed by left 4 -bits of the byte & column indexed by right 4 -bits n n n Example: byte {95} in hex. is replaced by row 9 col 5 byte, which is the value {2 A} in hex. S-box (substitution box) is constructed using a defined transformation of the values in GF(28) Designed to be resistant to all known attacks

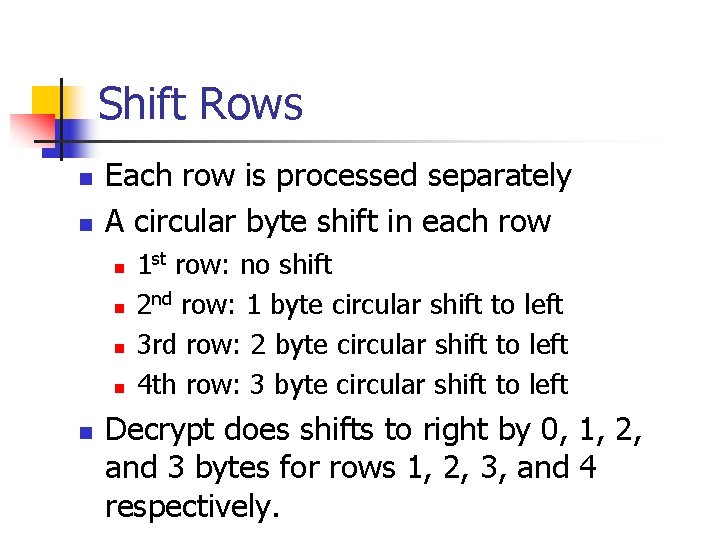
Shift Rows n n Each row is processed separately A circular byte shift in each row n n n 1 st row: no shift 2 nd row: 1 byte circular shift to left 3 rd row: 2 byte circular shift to left 4 th row: 3 byte circular shift to left Decrypt does shifts to right by 0, 1, 2, and 3 bytes for rows 1, 2, 3, and 4 respectively.

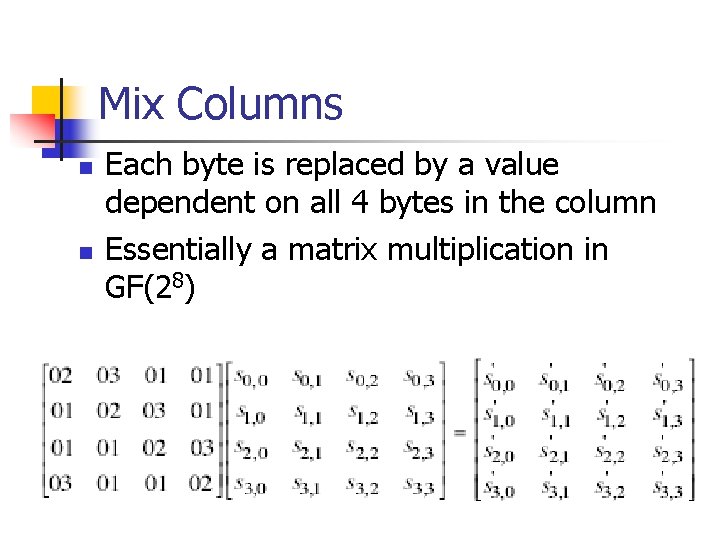
Mix Columns n n Each byte is replaced by a value dependent on all 4 bytes in the column Essentially a matrix multiplication in GF(28)

Add Round Key n n XOR state with 128 -bits of the round key XOR each column of the state with a word from the key schedule

AES Round

AES Key Expansion n n 128 -bit (16 -byte) key expands into array of 44/52/60 32 -bit words See PDF for details

AES Decryption n n n Not identical to encryption since steps done in reverse Uses inverses of each encryption step with a different key schedule Inverse byte substitution Inverse shift rows Inverse mix columns Inverse add (tweaked) round key

Implementation n On 8 -bit CPU n n Byte substitution can be done using a table of 256 entries Shift rows is simple byte shifting Add round key is byte XORs Mix columns is matrix multiplication in GF(28) which works on byte values, can be simplified to use a table lookup

Implementation n On 32 -bit CPU n n Redesign steps to use 32 -bit words Use pre-computed 4 tables of 256 -words Each column in each round can be computed using 4 table lookups + 4 XORs Very efficient implementation was a key factor in its selection as the AES cipher