I HAVE MANY CHECKLISTS HOW DO I GET


















- Slides: 21

I HAVE MANY CHECKLISTS: HOW DO I GET STARTED WITH CYBER SECURITY? Calvin Weeks, En. CE, CEDS, CRISC, CISSP, CISM

TRACK 2 – GOVERNANCE, POLICY, AND COMPLIANCE There are many great resources to help any organization to secure their cyber infrastructure. So, how do you know where to get started or if you have already started then is it the right things to be doing and is it enough. The good news is that any well run organization already has the foundation to implement the right cyber security solutions that will be the right fit. The leadership only needs to understand what that foundation is and how to employ it to protect the organization.

LEARNING OBJECTIVES 1. Understanding of available checklists, guides, and best practices for Cyber Security. 2. Define Governance, Cyber Security, Risk, and Compliance. 3. Understand how to apply the proper strategy to simplify cyber security efforts.

DEFINITIONS

CYBER SECURITY https: //niccs. us-cert. gov Definition: The activity or process, ability or capability, or state whereby information and communications systems and the information contained therein are protected from and/or defended against damage, unauthorized use or modification, or exploitation. https: //digitalguardian. com/blog/whatcyber-security Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access.

RISK 'Cyber risk' means any risk of financial loss, disruption or damage to the reputation of an organization from some sort of failure of its information technology systems. Cyber Risk is the potential of loss or harm related to technical infrastructure or the use of technology within an organization. Risk is identifying the threats to your assets that you are vulnerable to. You will either eliminate those threats that you are vulnerable to or mitigate the ones you cannot get rid of.

COMPLIANCE A common definition of the term, compliance is merely meeting the minimum standards as required by a law of industry requirement. Start with your internal policies.

GOVERNANCE Information Governance Reference Model (IGRM) Started by EDRM. net members https: //www. edrm. net/frameworks-and -standards/information-governancereference-model/ Formalized process of organizational wide efforts to manage all information and systems that contain, store, and communicate data.

RESOURCES

STANDARDS National Institute of Standards & Technology (FREE to public, mostly built for government, but applies to all) Everything that you do for cyber security you must reference a standard that you are following. Technical staff will use these, but it is imperative that management know and understand these standards. Management must support and embrace all actions based on a standard. https: //csrc. nist. gov/publications/sp

HARDENING National Checklist Program https: //nvd. nist. gov/ncp/repository Repository of publicly available security checklists (or benchmarks) that provide detailed low level guidance on setting the security configuration of operating systems and applications. Security Technical Implementation Guides (STIG) https: //iase. disa. mil/stigs/Pages/index. aspx STIG Tool https: //iase. disa. mil/stigs/agct/Pages/index. aspx Security Content Automation Protocol (SCAP) https: //csrc. nist. gov/Projects/Security. Content-Automation-Protocol/SCAP-

VULNERABILITIES National Vulnerability Database https: //nvd. nist. gov/vuln/search The NVD includes databases of security checklist references, security-related software flaws, misconfigurations, product names, and impact metrics.

STRATEGY

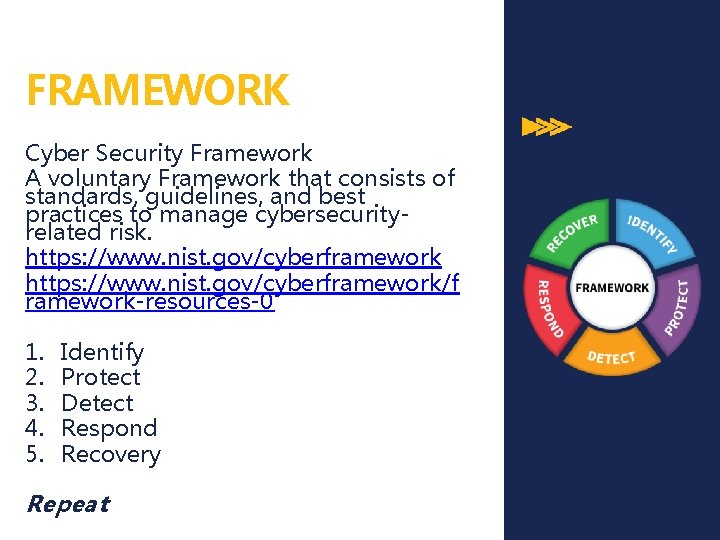
FRAMEWORK Cyber Security Framework A voluntary Framework that consists of standards, guidelines, and best practices to manage cybersecurityrelated risk. https: //www. nist. gov/cyberframework/f ramework-resources-0 1. 2. 3. 4. 5. Identify Protect Detect Respond Recovery Repeat

CYBER SECURITY BEST PRACTICE Cyber Security is a balanced approach of prevention, detection, and response to protect the confidentiality, integrity, and availability of electronic assets.

GOVERNANCE STRATEGY Formalized process of organizational wide efforts to align IT/Security strategy with the business strategy. Realized benefits that are measurable and reportable to executives, management, and board members.

CHECKLIST

BEST PRACTICE CHECKLIST • Begin with writing customized policies, procedures, and protocols covering the following areas: • Acceptable Use • Data Loss Prevention • Data Classifications • Incident Response • Passwords • Personal devices • Others as needed • Perform a risk assessment • Incident Response Plan • Third party Incident Management • Table top and scenario based assessments • Training & Awareness for Executives, IT, and all Users • Social Engineering and Phishing testing • Two-Factor Authentication • Password Management • Centralized logging, retention, and Monitoring • Updated software & hardware • Backups • Patch Management • Malware & threat detection • Encryption at rest, in transmission, and mobile • Managed Firewall and IDS • Third Party Risk Management

CYBER LIABILITY INSURANCE • All insurance coverage is unique. • Make sure you get all that you need to cover your risk. You will know what you are at risk for with a proper risk assessment. • Make sure you have coverage to pay for the third party response to include forensics work. Make sure you are allowed to hire your own third party. The minimum coverage would be $50, 000 per instance, but expect to pay up to $150, 000. • You would also need coverage for the loss or damage as well. • Make sure that you get updated annually on the insurance since this area is very volatile right now.

QUESTIONS? This presentation is presented with the understanding that the information contained does not constitute legal, accounting or other professional advice. It is not intended to be responsive to any individual situation or concerns, as the contents of this presentation are intended for general information purposes only. Viewers are urged not to act upon the information contained in this presentation without first consulting competent legal, accounting or other professional advice regarding implications of a particular factual situation. Questions and additional information can be submitted to your Eide Bailly representative, or to the presenter of this session.

THANK YOU Calvin Weeks, En. CE, CEDS, CRISC, CISSP, CISM 405. 594. 2051 | cweeks@eidebailly. com | forensics. eidebailly. com