How To Spy On Your Kids 101 Trooper

























- Slides: 31

How To Spy On Your Kids 101 Trooper First Class Rachel Grose Internet Crimes Against Children Task Force

Internet safety and your kids • THINK OF HOW MUCH TIME YOUR KIDS SPEND ON • • THE INTERNET. DO YOU KNOW WHO THEY ARE TALKING TO? DO THEY KNOW WHO THEY ARE TALKING TO? DO YOU KNOW ALL THEIR ONLINE ACCOUNTS? SOCIAL MEDIA? E-MAIL? CHATTING? HOW MUCH INFORMATION DO THEY HAVE ON THEIR PROFILES? AGE? ADDRESS? PHONE? CURRENT CITY? IS THERE A REASON THEY ARE IN MIDDLE SCHOOL AND THEY HAVE 1500 FRIENDS? DO THEY KNOW 1500 PEOPLE?

INTERNET SAFETY STATISTICS • Nearly all teenagers (93%) use the internet • 17% of teens say they've been contacted online by • • someone they didn't know in a way that made them feel scared or uncomfortable 39% of teens admitted to lying about their age to gain access to websites 34% of youth online saw sexual materials online that they did not want to see, including pictures of people naked or having sex 1 in 7 kids (ages 12 to 17 -years-old) were sexually solicited or approached online. 45% of youth posted their birth date or age 34% posted their real names, phone numbers, addresses, or schools 18% posted their pictures

INTERNET SAFETY STATISTICS • • • 71% of kids get messages online from someone they don’t know 45% were asked for personal information by someone they didn’t know 30% considered meeting someone they only talked with online 14% actually met a person face-to-face that they only spoke to over the internet 9% of the 13 to 15 -year-olds 22% of the 16 to 17 -year-olds 40% will usually reply when they get messages from strangers, but only 18% will tell an adult � SO AGAIN, HOW MUCH DO YOU KNOW ABOUT WHAT YOUR CHILD DOES ON THE INTERNET?

Children’s online privacy protection act �The Children's Online Privacy Protection Act and Rule apply to individually identifiable information about a child that is collected online, such as full name, home address, email address, telephone number or any other information that would allow someone to identify or contact the child. The Act and Rule also cover other types of information -- for example, hobbies, interests and information collected through cookies or other types of tracking mechanisms -- when they are tied to individually identifiable information.

sexting � Sexting is the act of sending sexually explicit messages and/or photographs, primarily between mobile phones. The term was first popularized in early 21 st century, and is a portmanteau of sex and texting, where the latter is meant in the wide sense of sending a text possibly with images. � Ways to “sext”: • Cell phones (Smart phones, i. Pod touches, etc) • Computers (Instant Messaging) • Tablets (i. Pads/ Androids) • E-Readers (Kindle) • XBox

Things to assist parents � Monitoring your child’s phone and text messaging as well as • • • social media sights may have parental controls in their security settings to assist parents in watching what their child posts. Smartphones now have applications that can conceal pictures and even delete messages that have been sent within a matter of seconds. Know your child’s passwords. Social Media websites such as Facebook, Twitter, Instagram. Watching chat websites that teens use nowadays to chat with random people around the world. (Kik, Meet. Me, etc. ) Get to know the state law Establish rules on using the Internet (etc. passwords, time limits, parental controls)

Sexting law � CHAPTER 61. CRIMES AND THEIR PUNISHMENT. � ARTICLE 8 C. FILMING OF SEXUALLY EXPLICIT CONDUCT OF MINORS. � § 61 -8 C-3 b. Prohibiting juveniles from manufacturing, possessing and distributing nude or � � � � � partially nude images of minors; creating exemptions; declaring a violation to be an act of juvenile delinquency; and providing for the punishment thereof. (a) Any minor who intentionally possesses, creates, produces, distributes, presents, transmits, posts, exchanges, or otherwise disseminates a visual portrayal of another minor posing in an inappropriate sexual manner or who distributes, presents, transmits, posts, exchanges or otherwise disseminates a visual portrayal of himself or herself posing in an inappropriate sexual manner shall be guilty of an act of delinquency and upon adjudication disposition may be made by the circuit court pursuant to the provisions of article five, chapter forty-nine of this code. (b) As used in this section: (1) “Posing in an inappropriate sexual manner” means exhibition of a bare female breast, female or male genitalia, pubic or rectal areas of a minor for purposes of sexual titillation. (2) “Visual portrayal” means: (A) A photograph; (B) A motion picture; (C) A digital image; (D) A digital video recording; or

Sexting law 2 � (E) Any other mechanical or electronic recording process or device that can preserve, for later viewing, a visual image of a person that includes, but is not limited to, computers, cellphones, personal digital assistance and other digital storage or transmitting devices; � (c) It shall be an affirmative defense to an alleged violation of this section that a minor charged with possession of the prohibited visual depiction did neither solicit its receipt nor distribute, transmit or present it to another person by any means. � (d) Notwithstanding the provisions of article twelve, chapter fifteen of this code, an adjudication of delinquency under the provisions of this section shall not subject the minor to the requirements of said article and chapter.

cyberbullying � Cyberbullying is the use of technology to harass, threaten, embarrass, or target another person. By definition, it occurs among young people. � Some examples of ways kids bully online are • Sending someone mean or threatening emails, instant messages, or text • • • messages Excluding someone from an instant messenger buddy list or blocking their email for no reason Tricking someone into revealing personal or embarrassing information and sending it to others Breaking into someone's email or instant message account to send cruel or untrue messages while posing as that person Creating websites to make fun of another person such as a classmate or teacher Using websites to rate peers as prettiest, ugliest, etc.

Cyberbullying statistics • Nearly 43% of kids have been bullied online. 1 in 4 has had • • • it happen more than once. 70% of students report seeing frequent bullying online. Over 80% of teens use a cell phone regularly, making it the most common medium for cyber bullying. 81% of young people think bullying online is easier to get away with than bullying in person. Only 1 in 10 victims will inform a parent or trusted adult of their abuse. Bullying victims are 2 to 9 times more likely to consider committing suicide. About 75% of students admit they have visited a website bashing another student.

What can be done �§ 61 -3 C-14 a. Obscene, anonymous, harassing and threatening communications by computer, cell phones and electronic communication devices; penalty. (a) It is unlawful for any person, with the intent to harass or abuse another person, to use a computer, mobile phone, personal digital assistant or other electronic communication device to: � (1) Make contact with another without disclosing his or her identity with the intent to harass or abuse; � (2) Make contact with a person after being requested by the person to desist from contacting them; � (3) Threaten to commit a crime against any person or property; or � (4) Cause obscene material to be delivered or transmitted to a specific person after being requested to desist from sending such material. �

What can be done � (3) "obscene material" means material that: � (A) An average person, applying contemporary adult community standards, would find, taken as a whole, appeals to the prurient interest, is intended to appeal to the prurient interest, or is pandered to a prurient interest; � (B) An average person, applying contemporary adult community standards, would find, depicts or describes, in a patently offensive way, sexually explicit conduct consisting of an ultimate sexual act, normal or perverted, actual or simulated, an excretory function, masturbation, lewd exhibition of the genitals, or sadomasochistic sexual abuse; and � (C) A reasonable person would find, taken as a whole, lacks literary, artistic, political or scientific value. � (c) It is unlawful for any person to knowingly permit a computer, mobile phone or personal digital assistant or other electronic communication device under his or her control to be used for any purpose prohibited by this section. �

What can be done � (d) Any offense committed under this section may be determined to have occurred at the place at which the contact originated or the place at which the contact was received or intended to be received. � (e) Any person who violates a provision of this section is guilty of a misdemeanor and, upon conviction thereof, shall be fined not more than $500 or confined in jail not more than six months, or both fined and confined. For a second or subsequent offense, the person is guilty of a misdemeanor and, upon conviction thereof, shall be fined not more than $1, 000 or confined in jail for not more than one year, or both fined and confined.

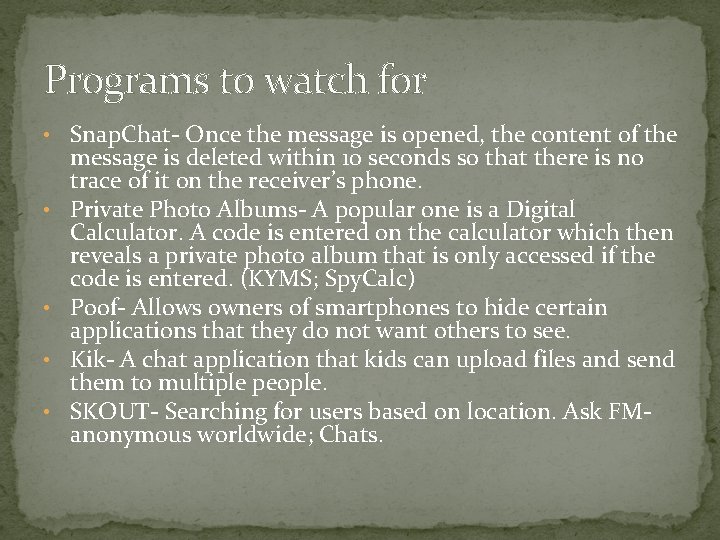
Programs to watch for • Snap. Chat- Once the message is opened, the content of the • • message is deleted within 10 seconds so that there is no trace of it on the receiver’s phone. Private Photo Albums- A popular one is a Digital Calculator. A code is entered on the calculator which then reveals a private photo album that is only accessed if the code is entered. (KYMS; Spy. Calc) Poof- Allows owners of smartphones to hide certain applications that they do not want others to see. Kik- A chat application that kids can upload files and send them to multiple people. SKOUT- Searching for users based on location. Ask FM- anonymous worldwide; Chats.












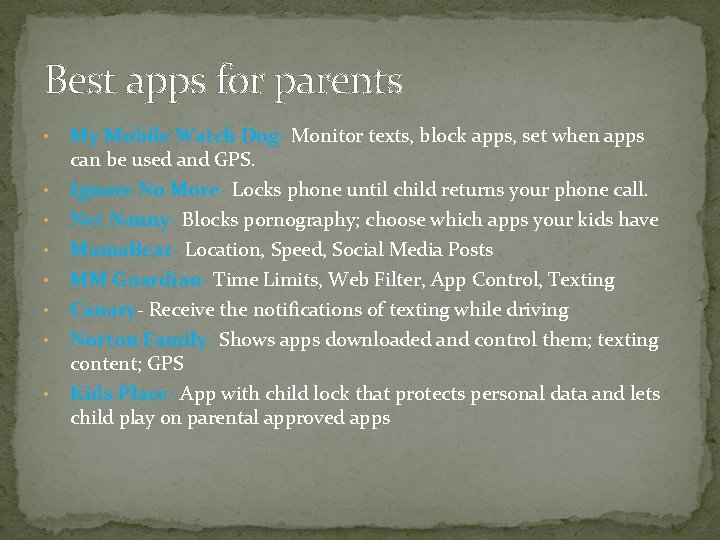
Best apps for parents • • My Mobile Watch Dog- Monitor texts, block apps, set when apps can be used and GPS. Ignore No More- Locks phone until child returns your phone call. Net Nanny- Blocks pornography; choose which apps your kids have Mama. Bear- Location, Speed, Social Media Posts MM Guardian- Time Limits, Web Filter, App Control, Texting Canary- Receive the notifications of texting while driving Norton Family- Shows apps downloaded and control them; texting content; GPS Kids Place- App with child lock that protects personal data and lets child play on parental approved apps

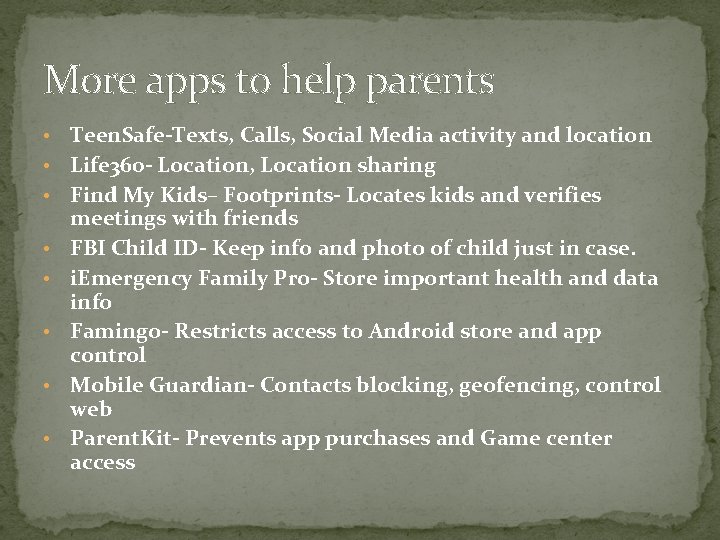
More apps to help parents • • Teen. Safe-Texts, Calls, Social Media activity and location Life 360 - Location, Location sharing Find My Kids– Footprints- Locates kids and verifies meetings with friends FBI Child ID- Keep info and photo of child just in case. i. Emergency Family Pro- Store important health and data info Famingo- Restricts access to Android store and app control Mobile Guardian- Contacts blocking, geofencing, control web Parent. Kit- Prevents app purchases and Game center access

PROCEDURE � IF CHILDREN POSSIBLY HAVE SOMETHING OF CONCERN ON THEIR PHONES, THE SCHOOL CAN TAKE ACTION. � SCHOOLS CAN TAKE ACTION UNTIL IT TURNS CRIMINAL. ONCE A CRIMINAL ACTION TAKES PLACE, THEY NOTIFY LAW ENFORCEMENT. � A CHILD’S PHONE WILL BE TAKEN BY ADMINISTRATION. IF LAW ENFORCEMENT IS NOTIFIED, THE PHONE IS THEN PLACED IN THE CUSTODY OF THE LAW ENFORCEMENT OFFICIAL AND IF EVIDENCE OF A CRIME IS FOUND, THE PHONE WILL NOT BE RETURNED. (THIS ALSO APPLIES TO COMPUTERS)

PROCEDURE • IF FURTHER EVIDENCE OF A CRIME IS FOUND, LAW ENFORCEMENT COULD SEIZE ALL ACCESSIBLE DEVICES IN THE HOUSEHOLD IF DEEMED NECESSARY. • JUVENILE PETITIONS WILL BE FILED AND THE CHILD WILL BE PUT THROUGH JUVENILE COURT. • IF CONVICTED, THE CHILD WILL FACE JUVENILE DETENTION, PROBATION, COMMUNITY SERVICE, AND COULD EVEN BE PROHIBITED FROM OWNING A PHONE WITH TEXTING CAPACITY.

Questions? �TFC. RACHEL GROSE �WEST VIRGINIA STATE POLICE �PHONE: 304 -528 -5555 �EMAIL: RACHEL. N. GROSE@WVSP. GOV
 Spy vs spy font
Spy vs spy font Indentation tool marks
Indentation tool marks Murder of dentist in blairsville pa
Murder of dentist in blairsville pa Kids r kids west cobb
Kids r kids west cobb U-2 incident cartoon
U-2 incident cartoon I spy walter wick
I spy walter wick Spy - card party game взлом
Spy - card party game взлом Spionage tools
Spionage tools Finfisher download
Finfisher download They say he is spy rewrite in the other voice
They say he is spy rewrite in the other voice A stiff bar that moves about a fixed point is a
A stiff bar that moves about a fixed point is a Spy aware
Spy aware Robert townsend spy
Robert townsend spy Spy hansen
Spy hansen Spy addon
Spy addon Si spy net work, big fedjaw iog link kyxogy
Si spy net work, big fedjaw iog link kyxogy Opc data spy
Opc data spy Give us your hungry your tired your poor
Give us your hungry your tired your poor Welcome to kids caf
Welcome to kids caf Transverse waves for kids
Transverse waves for kids Nnn poem
Nnn poem Diskovery kids
Diskovery kids Rock cycle song for kids
Rock cycle song for kids Rainforest producers and consumers
Rainforest producers and consumers Links immunization
Links immunization Children's eatwell guide
Children's eatwell guide When do kids say their first word
When do kids say their first word Poem using similes and metaphors
Poem using similes and metaphors Rota kids
Rota kids Raz kids
Raz kids Example of a blank verse poem
Example of a blank verse poem My brother is not a werewolf poem
My brother is not a werewolf poem