Hire or Develop a WorldClass CISO Find a







- Slides: 16

Hire or Develop a World-Class CISO Find a strategic and security-focused champion for your business. Info-Tech Research Group, Inc. is a global leader in providing IT research and advice. Info-Tech’s products and services combine actionable insight and relevant advice with ready-to-use tools and templates that cover the full spectrum of IT concerns. © 1997 -2016 Info-Tech Research Group Inc. Info-Tech Research Group 1

ANALYST PERSPECTIVE Create a plan to become the security leader of tomorrow The days are gone when the security leader can stay at a desk and watch the perimeter. The rapidly increasing sophistication of technology, and of attackers, has changed the landscape so that a successful information security program must be elastic and nimble, and must be tailored to the organization’s specific needs. The CISO is tasked with leading this modern security program, and this individual must truly be a Chief Officer, who has a finger on the pulses of the business and security processes at the same time. The modern, strategic CISO must be a master-of-all-trades. A world-class CISO is a business enabler who finds creative ways for the business to take on innovative processes that provide a competitive advantage, and most importantly: to do so securely. Cameron Smith Consulting Analyst, Security & Risk Practice Info-Tech Research Group 2

Our understanding of the problem This Research is Designed For: This Research Will Help You: ü A C-suite executive who needs to hire or ü Design a framework to identify good CISO develop a security leader ü A Chief Information Security Officer (CISO) who wants to become a strategic partner ü Any senior security leader seeking to build the skills of a top-level CISO candidates ü Provide a development framework for the new CISO ü Engage with stakeholders and executives ü Communicate the value of your information security program This Research Will Also Assist: This Research Will Help Them: ü A CIO/CTO who needs to incorporate security ü Understand how information security provides technology ü A CEO who needs to maintain reputational and corporate value in the face of security risks ü A CFO who wants to develop a businesseffective security manager value and enables progress for the organization ü Work with the CISO in developing security initiatives ü Understand the processes, capabilities, and limitations of information security Info-Tech Research Group 3

Executive Summary Situation • CEOs/CXOs are looking to hire or develop a senior security leader and • • aren’t sure where to start. Conversely, security practitioners are looking to upgrade their skill set and are equally stuck as to an appropriate starting point. Organizations are looking to optimize their security plans, and move from a tactical position to a more strategic one. Complication • It is difficult to find a “unicorn”: a candidate who is already fully • • developed in all areas. The role of the CISO has changed so much in the past three years, it is unclear what competencies are most important. You are a current CISO and are scoping out your areas of future development. Info-Tech Insight • Security without strategy is a hacker’s paradise. • The new security leader must be strategic, where a balance is struck between being tactical and taking a proactive security stance, incorporating security into business practices from day one and enabling secure adoption of new technologies and business practices. Resolution • If you are a CEO / CXO seeking to hire a CISO, clarify the competencies that are important to your organizational needs, • • • and use them to find a candidate with those specific strengths. If you are a current CISO, complete a self-assessment and identify your high-priority competency gaps, so you can actively work to develop those areas. Similarly, take time to evaluate your organization’s security processes and technology from a high level and create an action plan to raise the maturity level of trouble areas. Going forward, have an actionable plan to develop the CISO’s and the security program’s capabilities, and regularly reassess these items to ensure constant improvement. Info-Tech Research Group 4

Developing strategic competencies will benefit both the CISO and the organization Career development should not be seen as an individual effort. By understanding the personal core competencies that Info-Tech has identified, the individual wins by developing relevant new skills and the organization wins because the CISO provides increased value. Organizational Benefits Individual Benefits • Increased alignment between security and business objectives • Increased opportunity, as you become a trusted partner within your organization • Development of information security that is elastic, nimble, and flexible to the business • Improved relationships with peers and stakeholders • Reduction in wasted efforts and resources, and improvement in efficiency of security and the organization as a whole • Less resistance and more support for security initiatives • Opportunity to identify new, secure revenue streams • More involvement and stronger role for security at all levels of the organization • True synergy between security and business stakeholders, where the goals of both groups are being met Info-Tech Research Group 5

Investing in security, and what you should expect to get back from your investment Yesterday’s CISO Was Tactical Historically, security has been viewed as a kind of wager. The bet being that whatever was spent on security would prevent an even more costly incident from taking place. For information security, the equation was something like this: % Probability of Breach x $ Cost of Breach = $ Risk If the CISO spent less on security than the value of the risk, then security was a positive investment. This is the tactical approach to security, which is reactive, defensive, and focused on guarding the business. The limitation with this view is that it assumes the CISO is only able to prevent loss, and therefore the CISO is excluded from business planning. In reality, an effective CISO will create gains for the business. The World Class CISO Is Strategic The strategic approach is about integrating security with the business and creating a program that is proactive, elastic, and enables the business. The strategic CISO acts to identify opportunities to create new secure ways to do business and provides a competitive advantage to the organization. If involved in business planning, a CISO can become a revenue generator by finding creative ways for the organization to do business and creating revenue streams that are unavailable to organizations with a less savvy CISO. Leveraging your CISO will maximize your ROI in information security, and give your organization an edge over the competition. Info-Tech Research Group 6

MINI CASE STUDY Kyle Kennedy CISO, Cyber. SN. com In the middle of difficulty lies opportunity Challenge The security program has identified vulnerabilities at the database layer that must be addressed. The decision is made to move to a new vendor. There are multiple options, but the best option in the CISO’s opinion is a substantially more expensive service that provides more robust protection and more control features. The CISO faces the challenge of convincing the board to make a financial investment in his IT security initiative to implement this new software. Solution The CISO knows he needs to express this challenge (and his solution!) in a way that is meaningful for the executive stakeholders. He identifies that the business has $100 M in revenue that will move through this data stream. This new software will help to ensure the security of all of these transactions, which they would lose in the event of a breach. Furthermore, the CISO identifies new business plans in the planning stage that could be protected under this initiative. Results The CISO was able to gain support for the new database platform and implement it. The new, upgraded platform was able to protect current assets more securely than before. Furthermore, the CISO allowed new revenue streams to be created securely, which would carry over $60 M in transactions. This approach is the opposite of the cautionary tales that make news headlines, where new revenue streams are created before systems are put in place to secure them. This proactive approach is the core of the world-class CISO. Info-Tech Research Group 7

Measured Value: Having a World-Class CISO • If your organization has no CISO, the simple act of appointing one has been associated with a $12. 20 reduction of cost-per -record in the case of a data breach. 1 • However, we aren’t talking about hiring just any CISO. This blueprint seeks to develop your CISO’s competencies and reach a new level of effectiveness. o Organizations invest a median of ~300 K annually in their CISO 2. The CISO would have to be only 5% more effective to represent 15 K more value from this position. This would offset the cost of an Info-Tech workshop, and this conservative estimate pales in comparison to the tangible and intangible savings as shown below. o Your specific benefits will depend on many factors, but the value of protecting your reputation, adopting new and secure revenue opportunities, and preventing breaches cannot be overstated. There is a reason that investment in information security is on the rise: organizations are realizing that the pay-off is immense and the effort is worthwhile. Tangible cost savings from having a worldclass CISO • Cost savings from incident reduction. • Cost savings achieved through optimizing information security investments, resulting in savings from previously misdiagnosed issues. • Cost savings from ensuring that dollars spent on security initiatives support business strategy. • More opportunities to create new business processes through greater alignment between security and business. Intangible cost savings from having a worldclass CISO • Improved reputation and brand equity achieved through a proper evaluation of the organization’s security posture. • Continuous improvement achieved through a good security assessment and measurement strategy. • Ability to plan for the future since less security time will be spent firefighting, and more time will be spent engaged with key stakeholders. 1 2 2015 Cost of Data Breach Study: United States: Ponemon Institute 2013 Ponemon Cybersecurity Salary Benchmarking Report Info-Tech Research Group 8

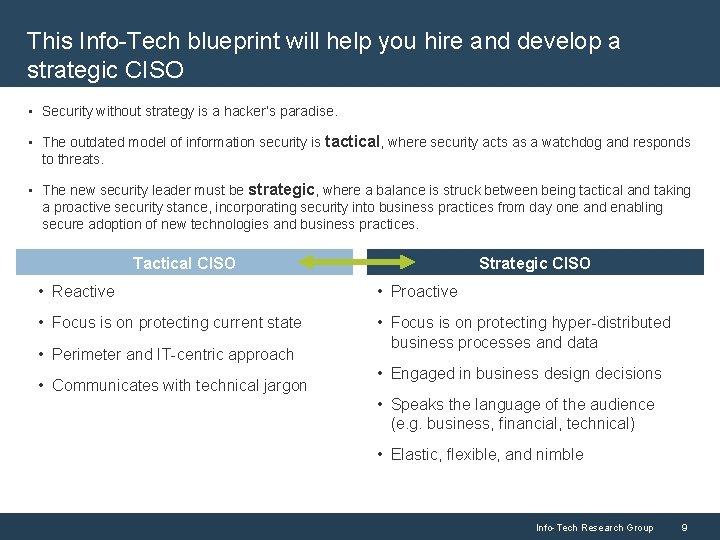
This Info-Tech blueprint will help you hire and develop a strategic CISO • Security without strategy is a hacker’s paradise. • The outdated model of information security is tactical, where security acts as a watchdog and responds to threats. • The new security leader must be strategic, where a balance is struck between being tactical and taking a proactive security stance, incorporating security into business practices from day one and enabling secure adoption of new technologies and business practices. Tactical CISO Strategic CISO • Reactive • Proactive • Focus is on protecting current state • Focus is on protecting hyper-distributed business processes and data • Perimeter and IT-centric approach • Communicates with technical jargon • Engaged in business design decisions • Speaks the language of the audience (e. g. business, financial, technical) • Elastic, flexible, and nimble Info-Tech Research Group 9

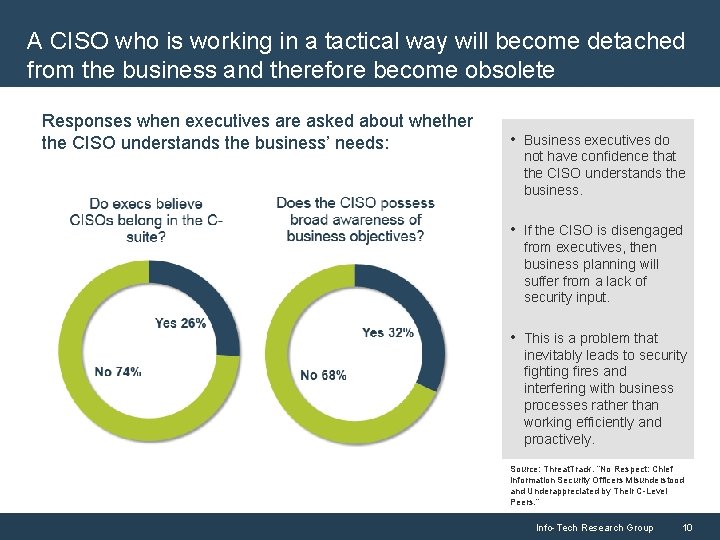
A CISO who is working in a tactical way will become detached from the business and therefore become obsolete Responses when executives are asked about whether the CISO understands the business’ needs: • Business executives do not have confidence that the CISO understands the business. • If the CISO is disengaged from executives, then business planning will suffer from a lack of security input. • This is a problem that inevitably leads to security fighting fires and interfering with business processes rather than working efficiently and proactively. Source: Threat. Track. “No Respect: Chief Information Security Officers Misunderstood and Underappreciated by Their C-Level Peers. ” Info-Tech Research Group 10

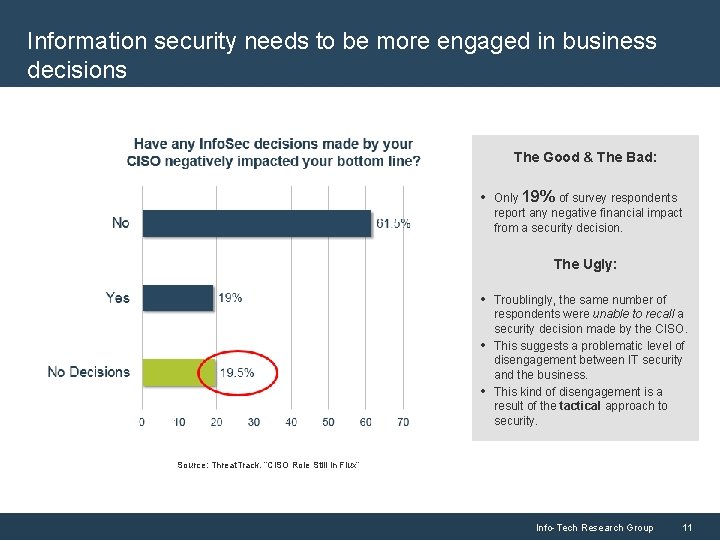
Information security needs to be more engaged in business decisions The Good & The Bad: • Only 19% of survey respondents report any negative financial impact from a security decision. The Ugly: • Troublingly, the same number of • • respondents were unable to recall a security decision made by the CISO. This suggests a problematic level of disengagement between IT security and the business. This kind of disengagement is a result of the tactical approach to security. Source: Threat. Track. “CISO Role Still in Flux” Info-Tech Research Group 11

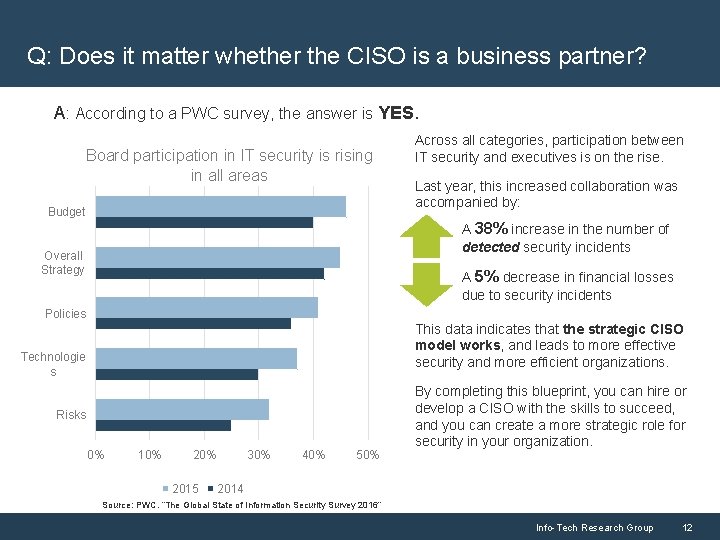
Q: Does it matter whether the CISO is a business partner? A: According to a PWC survey, the answer is YES. Board participation in IT security is rising in all areas Budget Across all categories, participation between IT security and executives is on the rise. Last year, this increased collaboration was accompanied by: A 38% increase in the number of detected security incidents Overall Strategy A 5% decrease in financial losses due to security incidents Policies This data indicates that the strategic CISO model works, and leads to more effective security and more efficient organizations. Technologie s Risks 0% 10% 2015 30% 40% 50% By completing this blueprint, you can hire or develop a CISO with the skills to succeed, and you can create a more strategic role for security in your organization. 2014 Source: PWC. “The Global State of Information Security Survey 2016” Info-Tech Research Group 12

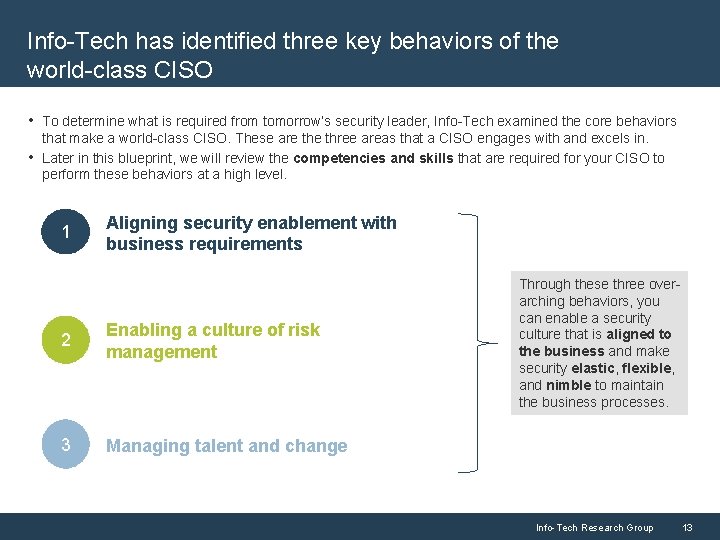
Info-Tech has identified three key behaviors of the world-class CISO • To determine what is required from tomorrow’s security leader, Info-Tech examined the core behaviors • that make a world-class CISO. These are three areas that a CISO engages with and excels in. Later in this blueprint, we will review the competencies and skills that are required for your CISO to perform these behaviors at a high level. 1 Aligning security enablement with business requirements 2 Enabling a culture of risk management 3 Managing talent and change Through these three overarching behaviors, you can enable a security culture that is aligned to the business and make security elastic, flexible, and nimble to maintain the business processes. Info-Tech Research Group 13

Info-Tech offers various levels of support to best suit your needs DIY Toolkit “Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful. ” Guided Implementation Workshop Consulting “Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track. ” “We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place. ” “Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project. ” Diagnostics and consistent frameworks used throughout all four options Info-Tech Research Group 14

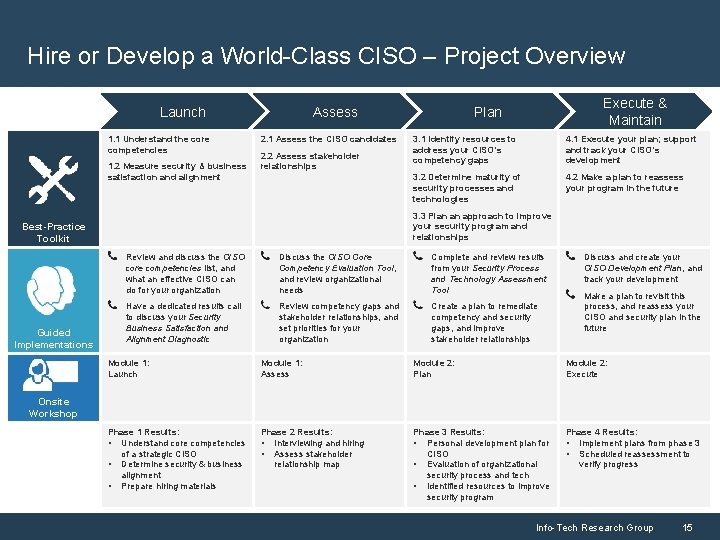
Hire or Develop a World-Class CISO – Project Overview 1. 1 Understand the core competencies 1. 2 Measure security & business satisfaction and alignment 2. 1 Assess the CISO candidates 2. 2 Assess stakeholder relationships 3. 1 Identify resources to address your CISO’s competency gaps 4. 1 Execute your plan; support and track your CISO’s development 3. 2 Determine maturity of security processes and technologies 4. 2 Make a plan to reassess your program in the future 3. 3 Plan an approach to improve your security program and relationships Best-Practice Toolkit Guided Implementations Execute & Maintain Plan Assess Launch Review and discuss the CISO core competencies list, and what an effective CISO can do for your organization Discuss the CISO Core Competency Evaluation Tool, and review organizational needs Complete and review results from your Security Process and Technology Assessment Tool Have a dedicated results call to discuss your Security Business Satisfaction and Alignment Diagnostic Review competency gaps and stakeholder relationships, and set priorities for your organization Create a plan to remediate competency and security gaps, and improve stakeholder relationships Discuss and create your CISO Development Plan, and track your development Make a plan to revisit this process, and reassess your CISO and security plan in the future Module 1: Launch Module 1: Assess Module 2: Plan Module 2: Execute Phase 1 Results: • Understand core competencies of a strategic CISO • Determine security & business alignment • Prepare hiring materials Phase 2 Results: • Interviewing and hiring • Assess stakeholder relationship map Phase 3 Results: • Personal development plan for CISO • Evaluation of organizational security process and tech • Identified resources to improve security program Phase 4 Results: • Implement plans from phase 3 • Scheduled reassessment to verify progress Onsite Workshop Info-Tech Research Group 15

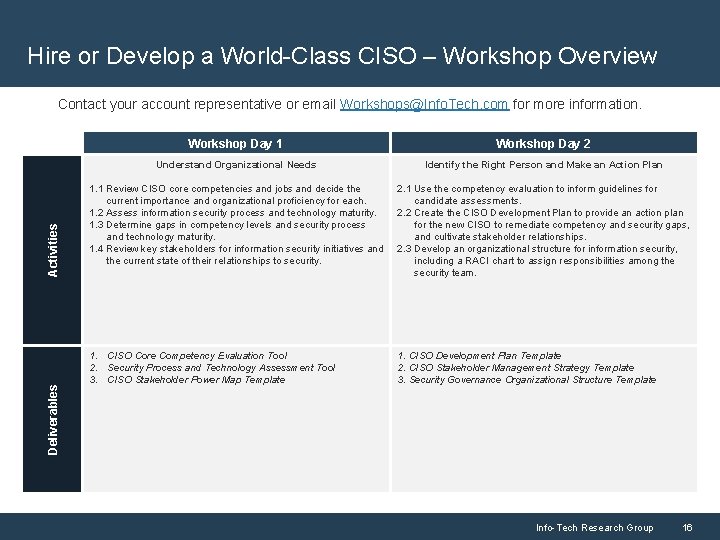
Hire or Develop a World-Class CISO – Workshop Overview Deliverables Activities Contact your account representative or email Workshops@Info. Tech. com for more information. Workshop Day 1 Workshop Day 2 Understand Organizational Needs Identify the Right Person and Make an Action Plan 1. 1 Review CISO core competencies and jobs and decide the current importance and organizational proficiency for each. 1. 2 Assess information security process and technology maturity. 1. 3 Determine gaps in competency levels and security process and technology maturity. 1. 4 Review key stakeholders for information security initiatives and the current state of their relationships to security. 2. 1 Use the competency evaluation to inform guidelines for candidate assessments. 2. 2 Create the CISO Development Plan to provide an action plan for the new CISO to remediate competency and security gaps, and cultivate stakeholder relationships. 2. 3 Develop an organizational structure for information security, including a RACI chart to assign responsibilities among the security team. 1. CISO Core Competency Evaluation Tool 2. Security Process and Technology Assessment Tool 3. CISO Stakeholder Power Map Template 1. CISO Development Plan Template 2. CISO Stakeholder Management Strategy Template 3. Security Governance Organizational Structure Template Info-Tech Research Group 16