HIPAA HITECH Topics In This Module HIPAA and



























- Slides: 33

HIPAA & HITECH

Topics In This Module HIPAA and HITECH Protected Health Information (PHI) Using PHI correctly Breaches Penalties and sanctions for violation What can I do? 2

HIPAA The Health Insurance Portability and Accountability Act of 1996 (HIPAA) was created to: Provide consistent coverage to people changing jobs Give patients greater control over the use of their health information Protect the privacy of health information by: Establishing national standards all healthcare providers must comply with Limiting the use of health information to minimize inappropriate disclosures Investigating inappropriate disclosures and holding violators accountable. 3

HITECH The Health Information Technology for Economic and Clinical Health of 2009 (HITECH) was created to strengthen HIPAA by: Standardizing data transfer methods Encouraging the move to electronic health record systems Imposing stiffer penalties for improper disclosures 4

HIPAA contains Privacy & Security rules to address health care concerns such as: • Fears that once patients’ records are stored electronically on networks, a couple of clicks could transmit those records worldwide • Loss of control over personal information • Potential for undesired marketing 5

HIPAA Privacy & Security Rules Privacy rule: protects all PHI in any form or media, whether electronic, paper, or spoken Security rule: specifically protects PHI in electronic format; addressing confidentiality, integrity, and availability using administrative, physical, and technical safeguards 6

What is PHI? Protected Health Information(PHI) is any information in the medical record or designated record set that can be used to identify an individual and that was created, used, or disclosed in the course of providing a health care service such as diagnosis or treatment. Is created or received by a health care provider, health plan, public health authority, employer, life insurer, school, or health care clearinghouse Relates to the past, present, or future physical or mental health condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual 7

PHI is information that can be used to identify, contact, or locate a single person or can be used with other sources to identify a single individual. There are 18 HIPAA identifiers that are considered personally identifiable information. 8

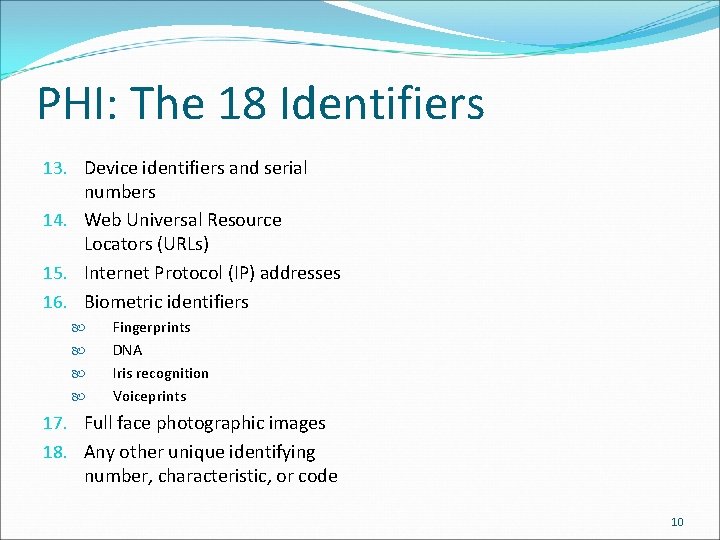
PHI: The 18 Identifiers 1. 2. Names All geographical subdivisions smaller than a state: Street address City County Precinct Zip code 3. Dates directly related to an individual: Birth date (including age if over 89) Admission date Discharge date Date of death Phone numbers Fax numbers Email addresses Social Security Numbers Medical record numbers Health plan beneficiary numbers 10. Account numbers 11. Certificate/license numbers 12. Vehicle identifiers and serial numbers, including license plate numbers 4. 5. 6. 7. 8. 9. 9

PHI: The 18 Identifiers 13. Device identifiers and serial numbers 14. Web Universal Resource Locators (URLs) 15. Internet Protocol (IP) addresses 16. Biometric identifiers Fingerprints DNA Iris recognition Voiceprints 17. Full face photographic images 18. Any other unique identifying number, characteristic, or code 10

Organizations Bound by HIPAA Covered Entities Health Plans (GCBH) Clearing Houses Providers Business Associates The law refers to Covered Entities (CE) and the work that they perform with PHI as covered functions. Covered functions can be outsourced to business associates. 11

HIPAA Business Associates (BA) Business Associates: Are contracted to perform a covered function on behalf of a CE Use PHI to do their job Are a third party, not direct employees of the Covered Entity they contract with HIPAA requirements and HITECH penalties are extended to Business Associates, and include forming a Business Associate Agreement (BAA) with the Covered Entity. BAs require additional oversight due to HIPAA, and it is not a good practice to have them unless required. 12

Common Business Associates A third party administrator that assists with health plan claims processing Attorneys Independent medical transcriptionists serving physicians Pharmacy benefits managers that manage a health plan’s pharmacist network CPA firms 13

Use and Disclosure of PHI GCBH, as a health plan, is permitted by HIPAA to Use (internally) and Disclose (externally) PHI for the purposes of TPO: Treatment – the provision of health care Payment – the provision of benefits and premium payment Healthcare Operations – normal business activities (reporting, data collection, eligibility checks, etc. ) 14

HIPAA Authorizations Written authorization must be obtained from a patient to use or disclose PHI for specific purposes other than TPO, including employment related inquiries, research, or marketing. An authorization can be revoked at any time in writing. Must include the name of the patient, the purpose of the disclosure, an expiration date or event, as well as a signature, date, and explanation of how to revoke the authorization. Unlike other health records, psychotherapy notes are not subject to disclosure to the patient. 15

The Minimum Necessary Rule The amount of PHI used or disclosed is restricted to the minimum amount of information necessary. Reasonable efforts must be made not to use, disclose, or request more than is necessary to accomplish a task. Exceptions are: Disclosure to a provider for treatment Release to an individual of their own PHI (psychotherapy notes are exempt from requests) Disclosures required by law 16

The Minimum Necessary Rule The “minimum necessary” rule does not restrict the information used or disclosed in treatment. The “minimum necessary” rule does apply to payment and health care operations. 17

Breach According to section 13400(1)(A) of the HITECH Act, a breach is defined as: the unauthorized acquisition, access, use, or disclosure of protected health information which compromises the security or privacy of the protected health information, except where an unauthorized person to whom such information is disclosed would not reasonably have been able to retain such information. 18

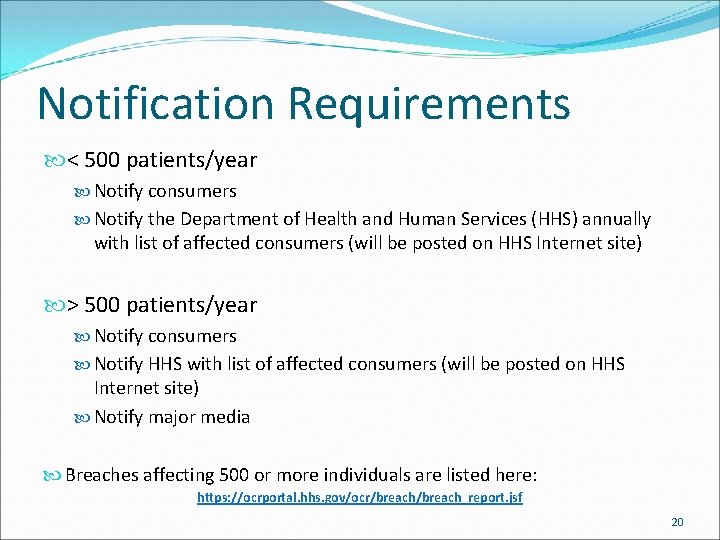
Breach Penalties Breaches are taken very seriously, and are punished accordingly Breaches must be reported to the affected consumers, the Department of Health and Human Services, and, if they affect more than 500 people, the media Civil penalties – four levels, up to $1, 500, 000 Criminal penalties – three levels, up to $250, 000 and up to 10 years imprisonment Fines increase with the number of patients affected and amount of neglect 19

Notification Requirements < 500 patients/year Notify consumers Notify the Department of Health and Human Services (HHS) annually with list of affected consumers (will be posted on HHS Internet site) > 500 patients/year Notify consumers Notify HHS with list of affected consumers (will be posted on HHS Internet site) Notify major media Breaches affecting 500 or more individuals are listed here: https: //ocrportal. hhs. gov/ocr/breach_report. jsf 20

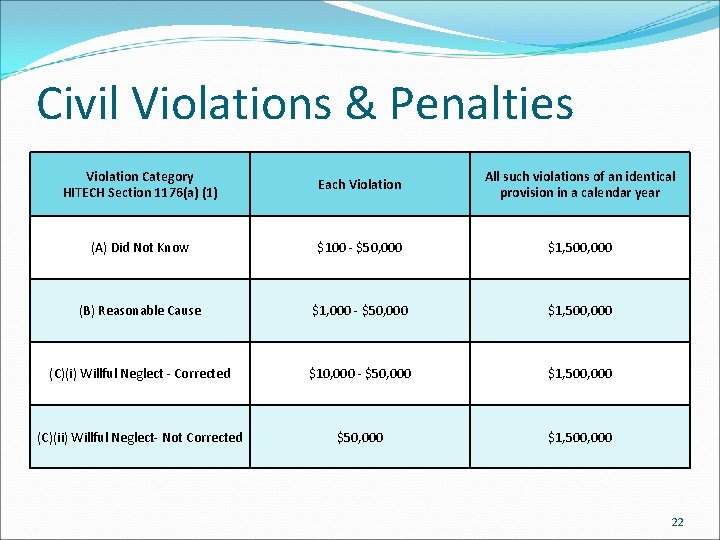
Civil Violation Tiers Did Not Know: The covered entity or business associate did not know, and reasonably should not have known of the violation. Reasonable Cause: The covered entity or business associate knew, or by exercising reasonable diligence would have known, that the act or omission was a violation cut the covered entity or business associate did not act with willful neglect. Willful Neglect – Corrected: The violation was the result of conscious, intentional failure or reckless indifference to fulfill the obligation to comply with HIPAA. However, the covered entity or business associate corrected the violation within 30 days of discovery. Willful Neglect – Uncorrected: The violation was the result of conscious, intentional failure or reckless indifference to fulfill the obligation to comply with HIPAA, and the covered entity or business associate did not correct the violation within 30 days of discovery. 21

Civil Violations & Penalties Violation Category HITECH Section 1176(a) (1) Each Violation All such violations of an identical provision in a calendar year (A) Did Not Know $100 - $50, 000 $1, 500, 000 (B) Reasonable Cause $1, 000 - $50, 000 $1, 500, 000 (C)(i) Willful Neglect - Corrected $10, 000 - $50, 000 $1, 500, 000 (C)(ii) Willful Neglect- Not Corrected $50, 000 $1, 500, 000 22

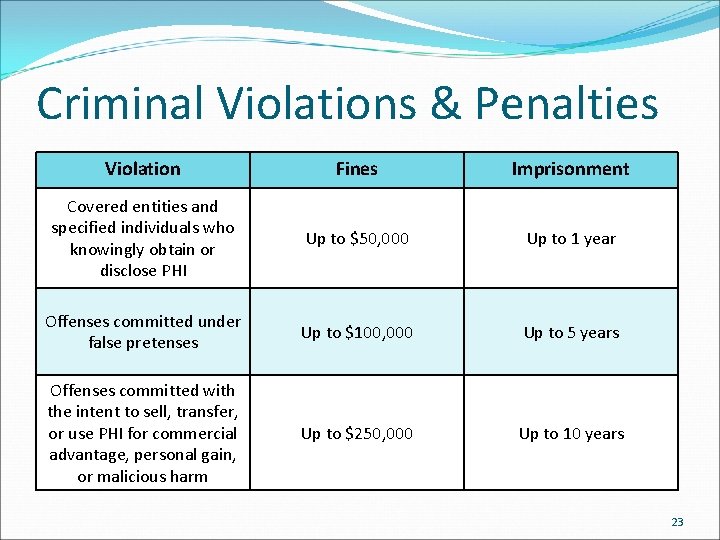
Criminal Violations & Penalties Violation Fines Imprisonment Covered entities and specified individuals who knowingly obtain or disclose PHI Up to $50, 000 Up to 1 year Offenses committed under false pretenses Up to $100, 000 Up to 5 years Offenses committed with the intent to sell, transfer, or use PHI for commercial advantage, personal gain, or malicious harm Up to $250, 000 Up to 10 years 23

Employer Sanctions Covered Entities and Business Associates are required to develop and impose sanctions appropriate to the nature of the HIPAA violations. The type of sanction applied should vary depending on factors such as the severity of the violation, whether the violation was intentional or unintentional, and whether the violation indicated a pattern or practice of improper use or disclosure of PHI. Sanctions can range from a warning to termination. 24

Incidental Disclosures Examples of incidental disclosures: • A patient seen in a waiting area • A conversation between a provider and a patient in a semi-private room heard by the other occupant Incidental Disclosures are not violations if the covered entity has safeguards in place and they are observed by the staff. 25

Hypothetically Speaking You work in a setting where you and your colleagues use PHI to do work. You are notified that a visitor has arrived to see you. You are currently busy; however, the visitor has come by several times before and knows where you are located. Should the visitor be allowed to enter on their own? Definitely not! Your visitor may be exposed to PHI. Even if they are familiar with HIPAA, this would be outside of TPO. Follow your company’s rules regarding visitors to protect your patients, your visitor, and yourself. 26

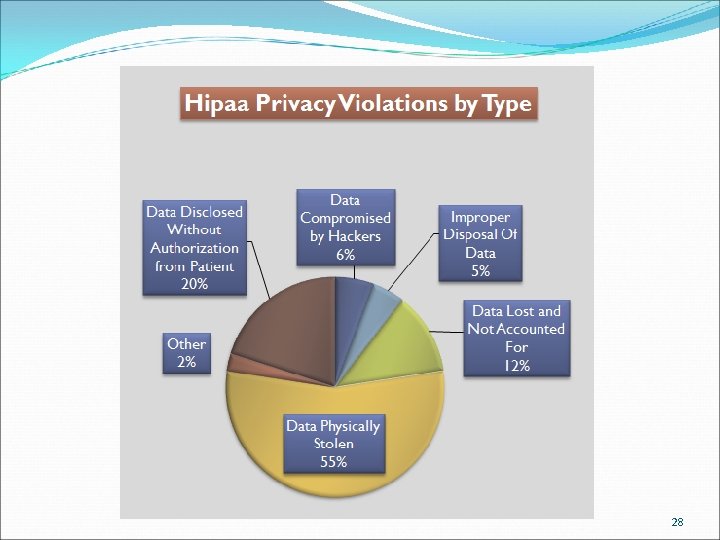
Some HIPAA Breach Trivia Unencrypted portable data storage devices are the leaders for large breaches of PHI Laptops Smart phones USB drives Business associates are a growing problem for breaches Almost two-thirds of data breaches involve a business associate Some of the largest breaches reported to the Department of Health and Human Services (HHS) have involved business associates Smaller breaches usually are results of misdirected faxes, emails, or hard copy communications. 27

28

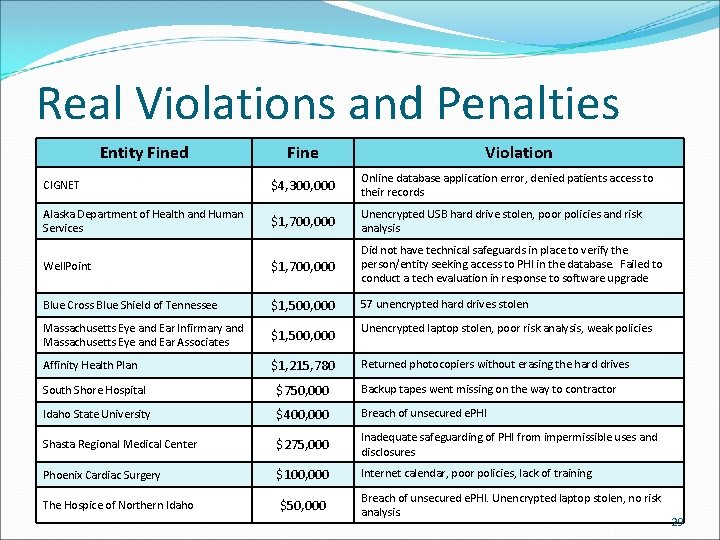
Real Violations and Penalties Entity Fined Fine Violation CIGNET $4, 300, 000 Online database application error, denied patients access to their records Alaska Department of Health and Human Services $1, 700, 000 Unencrypted USB hard drive stolen, poor policies and risk analysis Well. Point $1, 700, 000 Did not have technical safeguards in place to verify the person/entity seeking access to PHI in the database. Failed to conduct a tech evaluation in response to software upgrade Blue Cross Blue Shield of Tennessee $1, 500, 000 57 unencrypted hard drives stolen Massachusetts Eye and Ear Infirmary and Massachusetts Eye and Ear Associates $1, 500, 000 Unencrypted laptop stolen, poor risk analysis, weak policies Affinity Health Plan $1, 215, 780 Returned photocopiers without erasing the hard drives South Shore Hospital $750, 000 Backup tapes went missing on the way to contractor Idaho State University $400, 000 Breach of unsecured e. PHI Shasta Regional Medical Center $275, 000 Inadequate safeguarding of PHI from impermissible uses and disclosures Phoenix Cardiac Surgery $100, 000 Internet calendar, poor policies, lack of training The Hospice of Northern Idaho $50, 000 Breach of unsecured e. PHI. Unencrypted laptop stolen, no risk analysis. 29

Who Protects PHI? Everyone is responsible for protecting PHI Anyone with access to PHI can breach HIPAA, so it is important to understand how to properly use and protect it (and yourself) All healthcare organizations require Privacy Officers who: Educate employees on HIPAA practices Implement policies and procedures to ensure adherence to HIPAA Review and monitor agency practices to ensure HIPAA compliance 30

What Can I Do? • Don’t tell anyone the building code • Escort all visitors – offer to help unescorted individuals • Keep the lobby doors that lead to offices closed during meeting days • Keep your work area free of PHI when you’re not present • If necessary, close your door when discussion involves PHI • Don’t access more PHI than you need to do your job • Do not take removable media offsite that contains PHI • Don’t allow anyone at home to access your work • Report any security incidents immediately 31

What Can I Do? • Lock your computer when you walk away • Don’t share your password • Double check the number you’re dialing and use a cover page with the GCBH confidentiality statement when faxing out • Pick up your incoming faxes A. S. A. P. • Emails containing PHI may only be emailed to GCBH employees’ work email addresses. If transmitting PHI to a provider, you must use the GCBH website. • Dispose of sensitive materials in shredders or locked bins • If sending a CID/P 1 ID, nothing else may be sent – no dates, no initials, etc. 32

Review What is HIPAA, and to whom does it apply? The Health Insurance Privacy and Accountability Act, and it applies to Covered Entities and Business Associates What is PHI? Protected Health Information: Anything that can be used to identify an individual directly or through statistics When are additional authorizations required? For any use or disclosure other than TPO Who is responsible for protecting PHI? Everyone What are the penalties/sanctions for violation? Up to termination of employment, $1, 500, 000 civilly, and $250, 000 and 10 years criminally 33