Federal Desktop Core Configuration FDCC NLIT 2008 May








- Slides: 16

Federal Desktop Core Configuration FDCC NLIT 2008 May 2008 Stan Hall Cyber Technology Development Technical Project Manager Sandia is a multiprogram laboratory operated by Sandia Corporation, a Lockheed Martin Company, for the United States Department of Energy’s National Nuclear Security Administration under contract DE-AC 04 -94 AL 85000.

What is the Federal Desktop Core Configuration (FDCC)? The Federal Desktop Core Configuration (FDCC) is an OMBmandated security configuration. The FDCC currently exists for Microsoft Windows Vista and XP operating system software. While not addressed specifically as the "Federal Desktop Core Configuration, " the FDCC was originally called for in a 22 March 2007 memorandum from OMB to all Federal agencies and department heads and a corresponding memorandum from OMB to all Federal agency and department Chief Information Officers (CIO). Directly from: http: //csrc. nist. gov/fdcc_faqs_20070731. html

How was the FDCC created? The Windows Vista FDCC is based on Do. D customization of the Microsoft Security Guides for both Windows Vista and Internet Explorer 7. 0. Microsoft's Vista Security Guide was produced through a collaborative effort with DISA, NSA, and NIST. The guide reflects the consensus recommended settings from DISA, NSA, and NIST for the Windows Vista platform. The Windows XP FDCC is based on Air Force Customization of the Specialized Security-Limited Functionality (SSLF) recommendations in NIST SP 800 -68 and Do. D customization of the recommendations in Microsoft's Security Guide for Internet Explorer 7. 0. Directly from: http: //csrc. nist. gov/fdcc_faqs_20070731. html

FDCC Changes Coming FDCC User Rights Office 2007 Windows Vista

FDCC Challenges • NTLMV 2 • FIPS Setting • Certificate errors (IE) • User Rights • Active. X Controls • File system ACLs • Unsigned Drivers • Mobile Users • Firewall • Windows XP

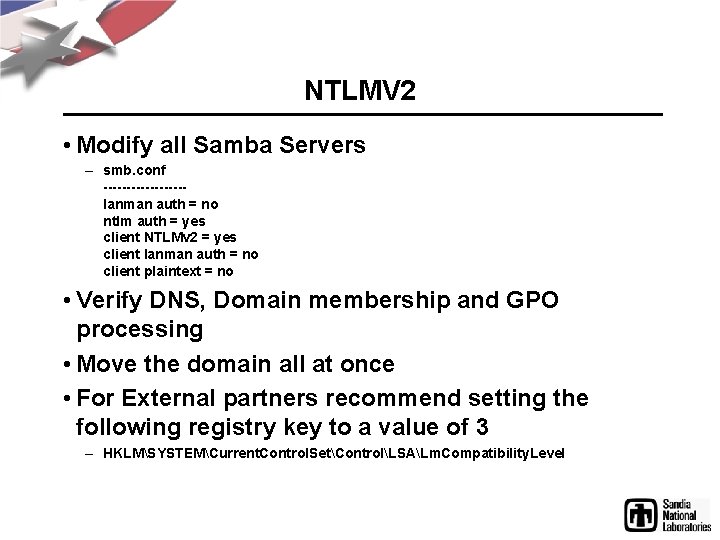
NTLMV 2 • Modify all Samba Servers – smb. conf ---------lanman auth = no ntlm auth = yes client NTLMv 2 = yes client lanman auth = no client plaintext = no • Verify DNS, Domain membership and GPO processing • Move the domain all at once • For External partners recommend setting the following registry key to a value of 3 – HKLMSYSTEMCurrent. Control. SetControlLSALm. Compatibility. Level

Federal Information Processing Standard (FIPS) • Accessing SSL Web sites – Internal – reconfigure to support FIPS (TLS 1. 0) • RDP to XP from Vista is not possible with FIPS • Upgrade RDP to 5. 2 or Higher on Clients • Bit. Locker keys cannot be stored in AD • Windows Server Update Services (WSUS) – Need WSUS 3. 0

Internet Explorer (IE) • Web sites with invalid Certificates will not display – No option to view or trust anyway • Name must match Certificate – Using URL’s in email messages

User Rights • Removing Administrative access is a huge challenge. • Applications must be able to run in User mode. – Application Streaming “Sand. Box” effect. • FDCC Disables File and Printer sharing • Need to have an exception process – FDCC is not applicable to special purpose (e. g. , scientific, medical, process control, and experimental systems) computers. • Users cannot install Printers (local or network)

Active. X Controls • FDCC restricts download of Active. X controls • Active. X controls in Internet and Restricted Sites Zones blocked (unless approved) • Vista: Use Active. X Installer Service (Ax. IS) – Allows users to install Active. X controls from sites that are approved by Group Policy • Use WSUS or SUS in lieu of Windows Update to deploy updates

File system ACLs and Unsigned Drivers • Users do not have access to run the following: – rcp. exe, regedt 32. exe, regedit. exe, arp. exe, attrib. exe, cacls. exe, debug. exe, edlin. exe, eventcreate. exe, eventtriggers. exe, mshta. exe, net 1. exe, netsh. exe, regini. exe, regsvr 32. exe, rexec. exe, route. exe, rsh. exe, sc. exe, secedit. exe, subst. exe, systeminfo. exe, tftp. exe, tlntsvr. exe • Justify exceptions when there is clear impact on supportability and productivity • VBScripts or use of Group Policy Scripts • FDCC recommends all device drivers be signed • Vista Only: – Allows users to install drivers in the Trusted Driver Store – Driver signing not limited to vendor; administrators can sign drivers as well

Mobile Users • FDCC recommends disabling three key services – Remote Access Connection Manager (RACM) – Wireless Zero Configuration (XP) – WLAN Auto. Config (Vista) • Limited to 2 cached logons – Could be issue for shared laptop users when disconnected – Launching an application with “Run-As” is considered a cached logon. • ID subset of mobile users – Create OU and apply policy that allows these services – Develop solution that “intelligently” detects absence of wired connection and then enables wireless

Firewall • FDCC mandates blocking of: – File and print sharing – Includes admin shares (i. e. c$, Admin$) • Central management required • Local admins can’t add exceptions • Alternates to Windows Firewall allowed with consideration to the following: – Centrally managed – No local exceptions allowed

Windows XP • We (Sandia) are currently not considering locking Windows XP down with all the FDCC setting. This is primarily due to the fact that the OS was not designed with the removal of Admin rights in mind. Many applications running on Windows XP require major re-work to run in User mode. • Our current plan it to move XP users to Vista once we have finished testing Vista with the FDCC • XP will require an exception some time in FY 09.

Planning/Testing • I cannot say enough about planning and testing for your environment. • The use of beta testers is a must. • The use of VM systems is a must. • One OU with the FDCC and one OU without. • Application Streaming can overcome compatibility and admin issues. • Installing with a preconfigured image.

Questions? Stan Hall cshall@sandia. gov (505) 284 -4333 Here are some web sites that have additional information. http: //nvd. nist. gov/fdcc/index. cfm http: //blogs. technet. com/fdcc/pages/resources. aspx http: //csrc. nist. gov/fdcc/